2016-02-06 Network Alerts At Cupid’s Arrow Online
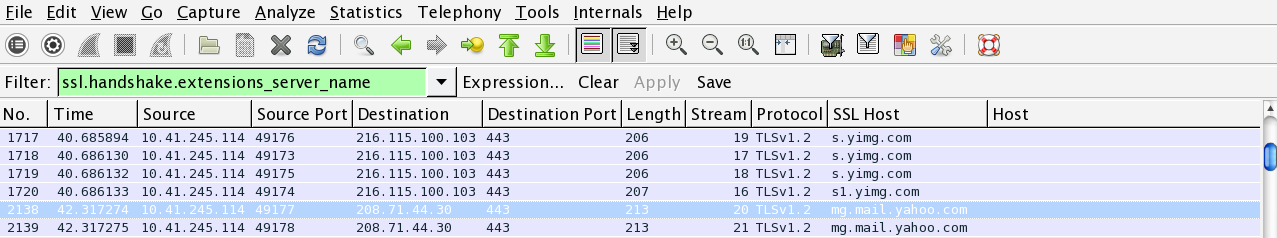
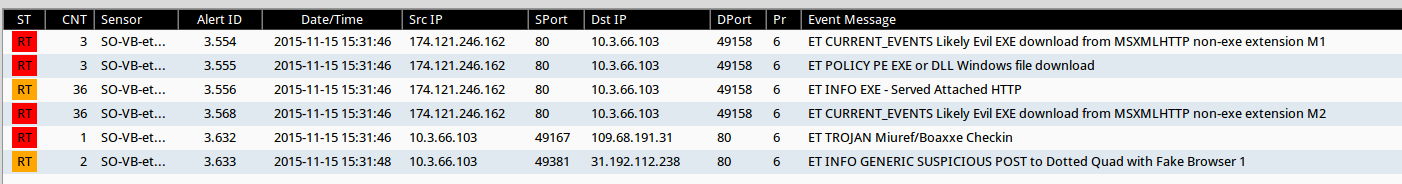
So here is the latest malware exercise from Brad. I will not lie – for some reason this one threw me for a loop. Personally I think it was because I did not have my usual Saturday morning cuppa when I started working on this one. But the emails that Brad included really threw me off for some reason – even after running all the javascript attachments in my VM and seeing that there was no match with the infection traffic in the PCAP or in the Snort rules. With that being said, here are my results for this one….