So the purpose of this post is because I could not remember how to extract the script from a malicious Word document. Damn old age and lack of coffee!
Like anyone in a SOC role, you most likely get a lot of emails sent to you (or your distro) for odd/weird/humorous emails that people are not sure about. It is up to you and the team in the SOC to figure out if the email is malicious or not. So yesterday someone sent in an email from someone else saying that they would like to work for the company and that they sent over their resume. The email looked something like this:
Sender: orinda_didonatis_1968@rambler.ru Recipient: From: orinda_didonatis_1968@rambler.ru Date: 10 Dec. 2015, 08:56:37 Subject: Job Hiya I saw your website and I'm very interested in applying for a job. Possibily even an unpaid internship. Please see my resume. Sincerely, Orinda Didonatis
The resume.doc file has the following characteristics:
MD5: 3b4914287915f961ccc6e3b6eb2631c8
SHA256: 85e115ed733bc8543b4517a754cd7b8d74381f38d24e41cc25811f545a0d3c9a
File size: 53KB
VirusTotal: http://www.virustotal.com/en/file/85e115ed733bc8543b4517a754cd7b8d74381f38d24e41cc25811f545a0d3c9a/analysis/
First Submission: 2015-12-10 16:22:19 UTC
Detection ratio: 4 / 55
So we know that this is definitely a malicious doc. Now to what lead me to write this blog – remembering how to get the script out of the Word document. Please note that way smarter people have talked about this. An example of one of them can be found here via this Sans post.
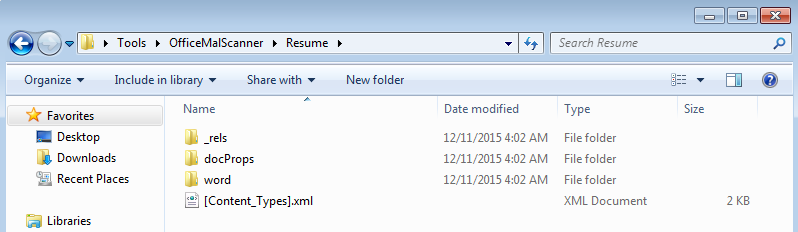
The easiest way for me is to just extract the Word doc since it is kind of like an archive and tools like 7Zip can extract it out. Once you do that, you should be able to see all the different folders:
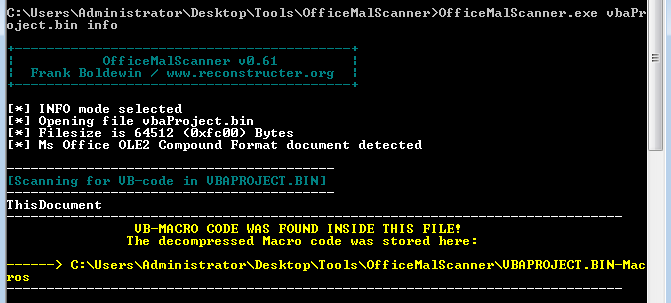
Now just browse to the folder called “word” and you should see the file called “vbaProject.bin.” From here fire up OfficeMalScanner and run the following command:
C:\Users\Administrator\Desktop\Tools\OfficeMalScanner>OfficeMalScanner.exe info
What you should see is the following:
Now that you have extracted out the script, you can start working on it, cleaning it up, and developing your IOCs and such. Since we have already blocked the callbacks from this malicious word doc, I will have to continue this blog post once I get home and can play with it in the lab at home. Till then. Enjoy!