I figured that I would try and attempt to do the annual SANS Holiday Hack Challenge this year while things were slow at work (knock on wood). So after working on this for 2-3 days, I have managed to knock out the first of the questions:
1) Which commands are sent across the Gnome’s command-and-control channel?
2) What image appears in the photo the Gnome sent across the channel from the Dosis home?
The way I got the answers for this first set of problems was not “creative” by any stretch of the imagination. If anything it was just manually plugging away at things and using the magic 8-ball called Google. Below is a summary of how I went about solving this set of problems.
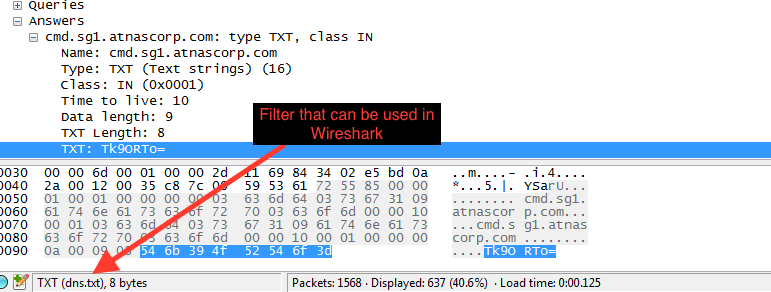
I obtained the PCAP from Josh and also the non-working script as well. Never having played with Scapy or Python, I figured that I would first sink my teeth into the PCAP and see if there was anything that I could figure out from it (since I feel more comfortable with a PCAP). Looking at it via Wireshark and the Protocol Hierarchy option, I could see that most of the traffic was split between 802.11 wireless management frames, and DNS. Filtering on just DNS, I could see all sorts of info in the TXT record of the response.
I remembered that Tim mentioned that BURP could figure out different decoding schemes, and someone else in the town mentioned something about base64 (I think), so I took one line from the TXT response and decoded it. Seeing that it was all in base64, I needed a quick way of getting only the DNS TXT responses. Since I don’t know how to script or work with Python/Scapy, I used ‘tshark’ instead. The filter that I used was ‘tshark -r Downloads/giyh.pcap -T fields -e dns.txt > sans.log’. ***NOTE: When using Wireshark, if you click on something, take a look at the bottom left hand corner. That may give you an idea of what you can use as a filter in the PCAP as you can see below:
That gave me the responses in a text file that I could then decode via Notepad++.
The following is the decoded part of the communication:
NONE: NONE: NONE: NONE: NONE: NONE: NONE: EXEC:iwconfig EXEC:START_STATE EXEC:wlan0 IEEE 802.11abgn ESSID:"DosisHome-Guest" EXEC: Mode:Managed Frequency:2.412 GHz Cell: 7A:B3:B6:5E:A4:3F EXEC: Tx-Power=20 dBm EXEC: Retry short limit:7 RTS thr:off Fragment thr:off EXEC: Encryption key:off EXEC: Power Management:off EXEC: EXEC:lo no wireless extensions. EXEC: EXEC:eth0 no wireless extensions. EXEC:STOP_STATENONE: NONE: NONE: EXEC:cat /tmp/iwlistscan.txt EXEC:START_STATE EXEC:wlan0 Scan completed : EXEC: Cell 01 - Address: 00:7F:28:35:9A:C7 EXEC: Channel:1 EXEC: Frequency:2.412 GHz (Channel 1) EXEC: Quality=29/70 Signal level=-81 dBm EXEC: Encryption key:on EXEC: ESSID:"CHC" EXEC: Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 6 Mb/s EXEC: 9 Mb/s; 12 Mb/s; 18 Mb/s EXEC: Bit Rates:24 Mb/s; 36 Mb/s; 48 Mb/s; 54 Mb/s EXEC: Mode:Master EXEC: Extra:tsf=000000412e67cddf EXEC: Extra: Last beacon: 5408ms ago EXEC: IE: Unknown: 00055837335A36 EXEC: IE: Unknown: 010882848B960C121824 EXEC: IE: Unknown: 030101 EXEC: IE: Unknown: 200100 EXEC: IE: IEEE 802.11i/WPA2 Version 1 EXEC: Group Cipher : CCMP EXEC: Pairwise Ciphers (1) : CCMP EXEC: Authentication Suites (1) : PSK EXEC: IE: Unknown: 2A0100 EXEC: IE: Unknown: 32043048606C EXEC: IE: Unknown: DD180050F2020101040003A4000027A4000042435E0062322F00 EXEC: IE: Unknown: 2D1A8C131BFFFF000000000000000000000000000000000000000000 EXEC: IE: Unknown: 3D1601080800000000000000000000000000000000000000 EXEC: IE: Unknown: DD0900037F01010000FF7F EXEC: IE: Unknown: DD0A00037F04010000000000 EXEC: IE: Unknown: 0706555320010B1B EXEC: Cell 02 - Address: 48:5D:36:08:68:DC EXEC: Channel:6 EXEC: Frequency:2.412 GHz (Channel 1) EXEC: Quality=59/70 Signal level=-51 dBm EXEC: Encryption key:on EXEC: ESSID:"DosisHome" EXEC: Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 18 Mb/s EXEC: 24 Mb/s; 36 Mb/s; 54 Mb/s EXEC: Bit Rates:6 Mb/s; 9 Mb/s; 12 Mb/s; 48 Mb/s EXEC: Mode:Master EXEC: Extra:tsf=00000021701d828b EXEC: Extra: Last beacon: 4532ms ago EXEC: IE: Unknown: 000F736F6D657468696E67636C65766572 EXEC: IE: Unknown: 010882848B962430486C EXEC: IE: Unknown: 030106 EXEC: IE: Unknown: 0706555320010B1E EXEC: IE: Unknown: 2A0100 EXEC: IE: Unknown: 2F0100 EXEC: IE: IEEE 802.11i/WPA2 Version 1 EXEC: Group Cipher : CCMP EXEC: Pairwise Ciphers (1) : CCMP EXEC: Authentication Suites (1) : PSK EXEC: Cell 03 - Address: 48:5D:36:08:68:DD EXEC: Channel:6 EXEC: Frequency:2.412 GHz (Channel 1) EXEC: Quality=62/70 Signal level=-49 dBm EXEC: Encryption key:off EXEC: ESSID:"DosisHome-Guest" EXEC: Bit Rates:1 Mb/s; 2 Mb/s; 5.5 Mb/s; 11 Mb/s; 18 Mb/s EXEC: 24 Mb/s; 36 Mb/s; 54 Mb/s EXEC: Bit Rates:6 Mb/s; 9 Mb/s; 12 Mb/s; 48 Mb/s EXEC: Mode:Master EXEC: Extra:tsf=00000021701d8913 EXEC: Extra: Last beacon: 5936ms ago EXEC: IE: Unknown: 000F736F6D657468696E67636C65766572 EXEC: IE: Unknown: 010882848B962430486C EXEC: IE: Unknown: 030106 EXEC: IE: Unknown: 0706555320010B1E EXEC: IE: Unknown: 2A0100 EXEC: IE: Unknown: 2F0100 EXEC:STOP_STATENONE: NONE: NONE: NONE: FILE:/root/Pictures/snapshot_CURRENT.jpg FILE:START_STATE,NAME=/root/Pictures/snapshot_CURRENT.jpg FILE:STOP_STATE NONE: NONE: NONE:
In the middle of the this log file that I created was a large chunk of base64 encoded text. I took this and created a new file just with it and none of the other data that was decoded above. I tried to decode this but most of it was not decodable, with the exception of the first line which showed “JFIF,” and the occasional “FILE: ” found throughout the file. So not knowing what a normal JPEG would look like in a hex editor I downloaded a regular JPEG from Google and opened it. I then took the new file and opened it in a hex editor as well and compared the two against each other. Josh had made the comment about how the magic-bytes for a JPEG was “0xFFd8.” I looked for that in the new file, and deleted everything before it. I also did a search for the hex string of “46 49 4C 45 3A” (FILE:) and deleted all occurrences of it from the file. Once that was done, I saved the file and gave it the extension of JPG. Once that was done, I was able to see the image that the Gnome had taken (seen below).