Note: It took me a little longer to get this post written and my VM had crashed on me, so the logs seen from Chrome or Edge may reflect more data than I had initially.
This is going to be slightly off topic from what I usually post about (malware) and is not deep in the weeds for someone that is wanting to do forensics. The lens that I am viewing this from is as a defender/SOC analyst. For a more in-depth look into this topic from a forensics perspective please see these awesome resources below:
- Jai Minton’s Digital Forensics and Incident Response cheat sheet – https://www.jaiminton.com/cheatsheet/DFIR/#
- A Digital Forensic View of Windows 10 Notifications by Patrício Domingues, Luís Andrade, and Miguel Frade – https://www.mdpi.com/2673-6756/2/1/7/pdf
- Microsoft’s Web Push Notifications – https://webpushdemo.azurewebsites.net/
As a defender one of the things that I commonly see is when a user has triggered an alert for either POST or GET requests being blocked at the proxy due to a URL that had been flagged, only to find out that the alert stems from a browser add-on or a push notification for a site. This got me thinking about how EDRs, in general, dealt with this kind of activity since something has to be written to disk. The last time that I played with Crowdstrike (it’s been a while now) it did not flag on any browser add-ons or push notifications unless there was something questionable/malicious about it (i.e.: see this Reddit thread about Wave Browser/WebNavigator alerts) – so I am pretty sure this is the case for most other EDR products as well. With that being said, I wanted to see what would be written to disk, if anything was written to begin with, when a user accepted a push notification for a site on a Windows system. I am not looking at browser extensions for this post since it would be written to disk anyways and could be easily alerted on based on the path for the browser or blocked by GPO. For an excellent resource regarding forensics and the location of different artifacts check out Jai Minton’s site where it is all broken down in an easy to read format.
When I started to look into this I discovered that there are a lot of resources out there that go quite in depth about push notifications and the Windows Notification System in general. One of the first sites that I came across was from Microsoft which explained it well and made it pretty easy to understand from a client-server application perspective. It also has the ability of performing test pushes since it will allow you to subscribe to the site and play with it some. I also came across a well written and in-depth paper talking about the Windows 10 notifications system from a forensic’s perspective. That PDF can be found here. I also found a site (pushalert.co) that would allow someone to create a free limited use account to do push notifications to a website. Leveraging Pushalert and the script that it generated, and a test site that I created on Github with the script from PushAlert, I started to play with things on my test Windows VM.
Like I stated above, initially I started to play with the web push notification site from Microsoft and PushAlert on my test VM and just ran Process Monitor to see what kind of results I would get. With the filtering in ProcMon set as the following:
- Path contains “wpndatabase” (this covers me from the user/system perspective of the Windows push service)
- Path contains “C:\Users\bob\AppData\Local\Google\Chrome\User Data\Notification Resources\”
- Path contains “C:\Users\bob\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications”†
- Path contains “C:\Users\bob\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database”†
† These paths can be swapped out for Edge as well (i.e.: C:\Users\%username%\AppData\Local\Microsoft\Edge\User Data\Default
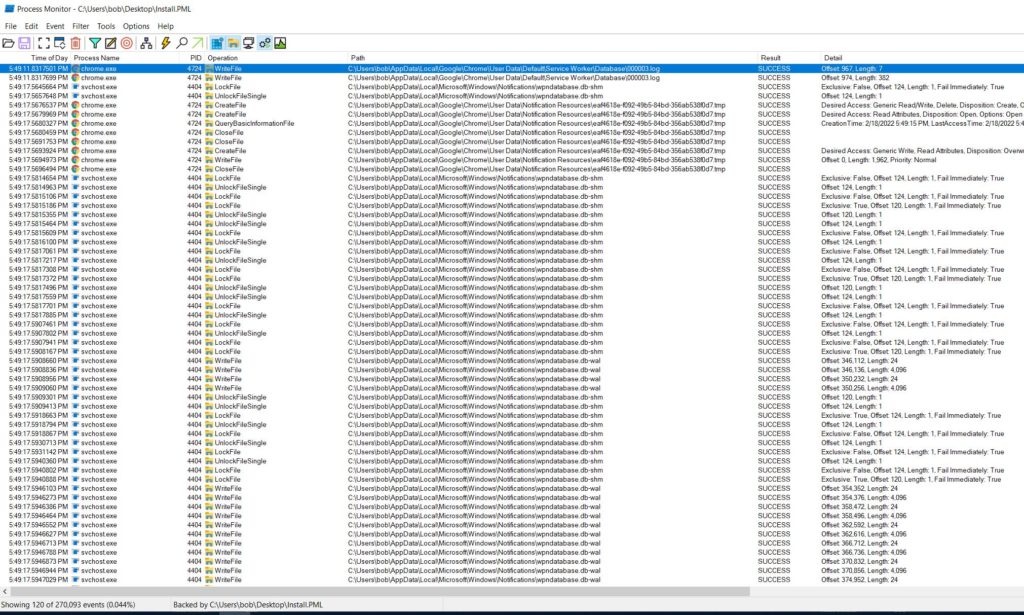
The image below is what I initially saw.
The Chrome process wrote to a file called 000003.log in the “C:\Users\%username%\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database” location. Opening this file up I could see various hits for the push notifications from different sites that I was playing with (i.e.: Reddit, Yahoo, Webpushdemo, and PushAlert.io).
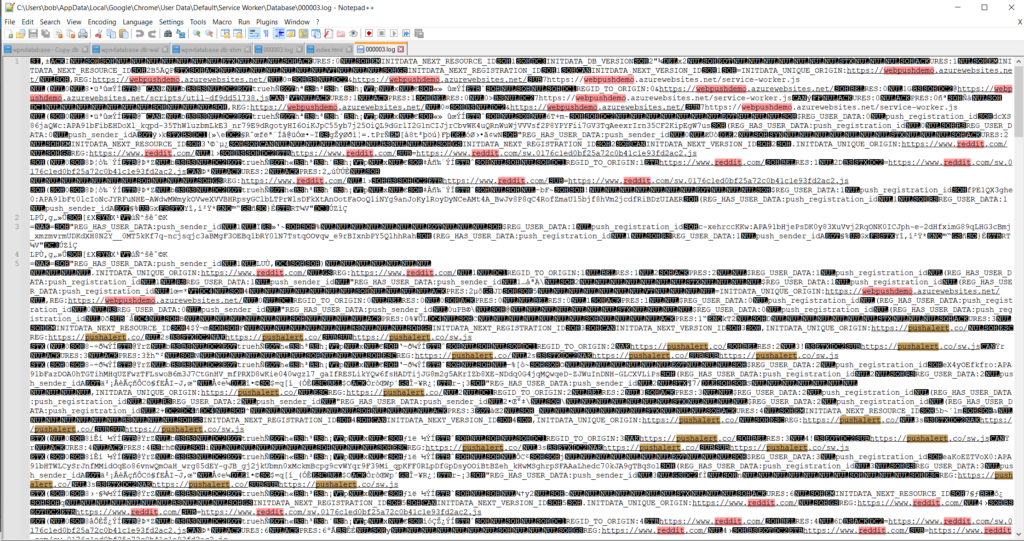 Initially I thought the only thing that was missing here was where the push came from (more on that in a bit). Technically I can see that I had signed up for some push notifications from sites like Yahoo, and Reddit, but the one from PushAlert.io had no reference to the test site setup on Github.io that I could see. Also, I wanted to see what these would look like from a user using Edge, and this file did not have anything stating which browser got the alert. From a defender’s perspective, some bits are definitely missing (initially that is – more in a bit).
Initially I thought the only thing that was missing here was where the push came from (more on that in a bit). Technically I can see that I had signed up for some push notifications from sites like Yahoo, and Reddit, but the one from PushAlert.io had no reference to the test site setup on Github.io that I could see. Also, I wanted to see what these would look like from a user using Edge, and this file did not have anything stating which browser got the alert. From a defender’s perspective, some bits are definitely missing (initially that is – more in a bit).
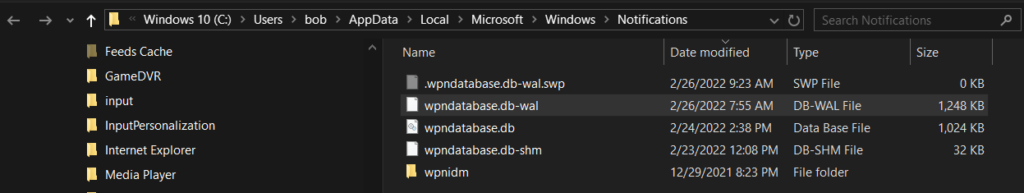
So I bounced over to the path of “C:\Users\bob\AppData\Local\Microsoft\Windows\Notifications” folder location to see what I may be able to find there since the service “svchost.exe” did some file operations on the “wpndatabase.db-shm/wal” files.
Note: This is the user notification location and not the system wide notification location as that is written to another path.
From here, as “A Digital Forensic View of Windows 10 Notifications” described, I found the SQLite file and the other supporting files as well.
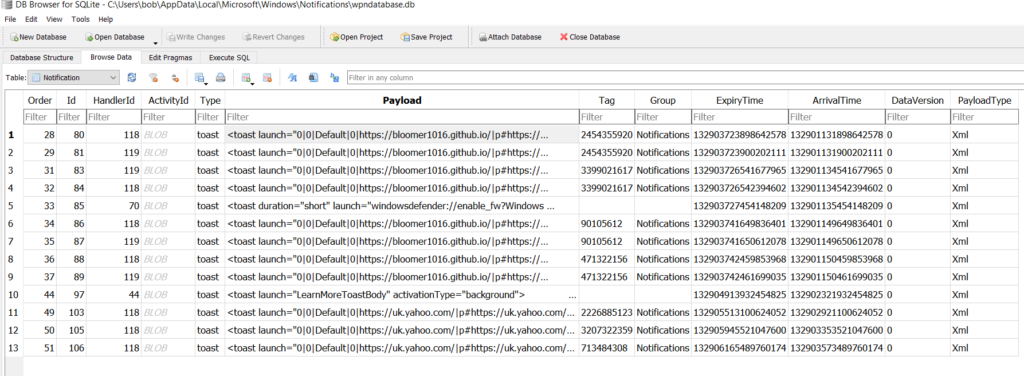
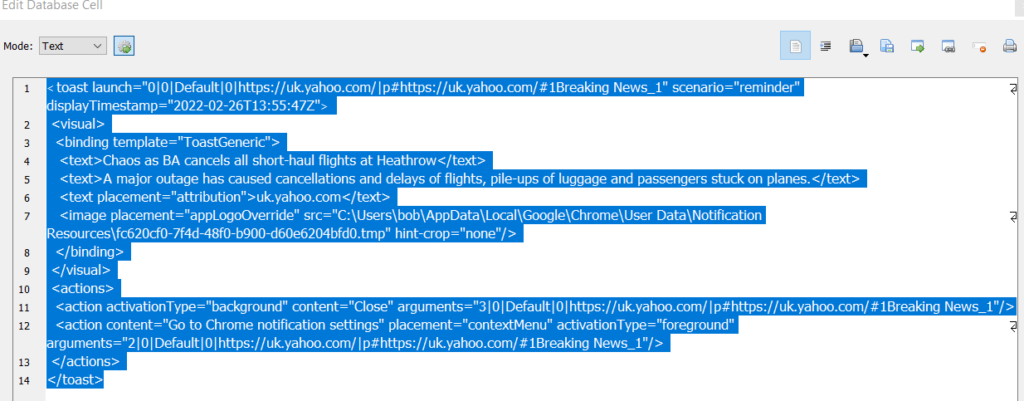
I opened the “wpndatabase.db” file using “DB Browser for SQLite” and low and behold, here is some of the data that I was looking for. As you can see in the XML blobs, this at least tells me 1) where the push is coming from in an easier on the eyes format, and 2) which browser got the push notification since it gives you the path for where the image associated with the push notification is located.
The other nice bit about this is the fact that you can see what kind of message the user got from that push notification since there are some attributes for it as seen above. For example, the one from Github.io has the title of the push notification that I used along with the body of for the push notification (both the same in all cases). If you look at the one from Yahoo, you can see the headline of the news that was pushed to the browser.
Since I was there, I also wanted to see what was in the “wpndatabase.db-wal” file since it does serve as a transaction log and would be more recent then the actual “wpndatabase.db” file based on the documentation from SQLite.org. After reading the doc for the WAL file my testing made more sense since I was seeing the WAL and SHM files updating before the actual db file.
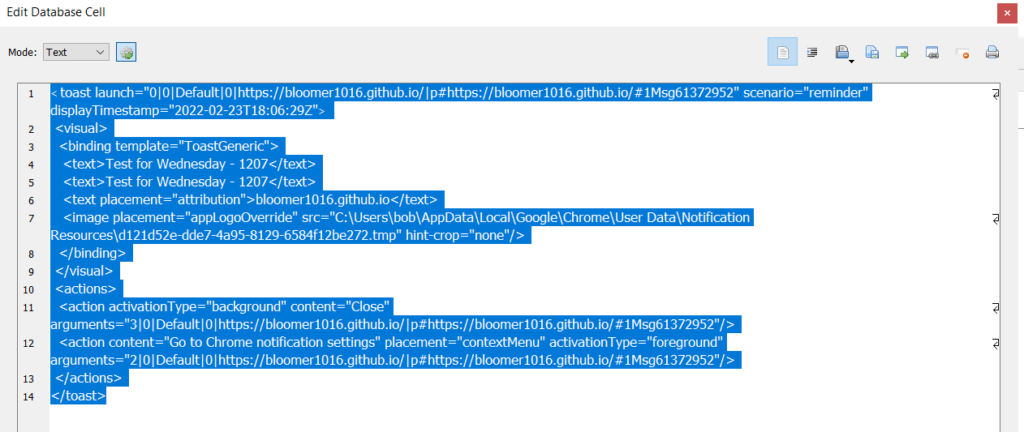
At first I used Notepad++ to open the WAL file up, but it was way to difficult to read. Next I tried Notepad and even then that was slow and clunky. I ended up using GVIM to open the file which made going through it a lot easier. As seen below, the WAL file allowed me to see push notifications that have been aged out of the “wpndatabase.db” file since Windows ages those out after three days. Compare this to the image above where the first date/timestamp is from the 23rd of Feb and not the 21st of Feb.
This still left me with one question left to answer – if someone does get a push notification, can I get information about where it came from possibly? Thinking about it again, I went back to the 000003.log and this time used SysInternals Strings to just look at the strings in the file. Jackpot!
BDATA:https_uk.yahoo.com_0
p#https://uk.yahoo.com/#1Breaking News_1
https://uk.yahoo.com/
BSecond COVID booster jab expected to be offered to most vulnerable
A decision has reportedly been taken by the Joint Committee on Vaccination and Immunisation, with an announcement due in weeks.*
Breaking News_12
https://s.yimg.com/uu/api/res/1.2/JNB6h9aDWHwpbVPBnOPt7A--/cT03NTt3PTgwMDthcHBpZD15dGFjaHlvbjs-/https://media.zenfs.com/en/the_independent_577/a1b49603fd28596e804df7dbc2c4733e8
fallback_"
useNNSF"
title"BSecond COVID booster jab expected to be offered to most vulnerable"
body"
A decision has reportedly been taken by the Joint Committee on Vaccination and Immunisation, with an announcement due in weeks."
url"Jhttps://uk.news.yahoo.com/second-covid-booster-jab-expected-073039251.html"
uuid"$e818a919-915a-377f-aa6e-9ede1e0d0c39"
followId_"
timeline_name"
Breaking News"
msg_id"$78531c1e-f95a-4f43-8a76-1fc23090f9e6"
notification_id_"
publish_time"
1645264860234"
publisher_msg_id"$dfcbc394-d41f-4c4c-b389-fbc3fc03efeb"
pl1I
notification_shownN
wB{
r@https://s.yimg.com/cv/apiv2/notifications/YCon_Badge_90_90_2.pngz
*(p#https://uk.yahoo.com/#1Breaking News_10
k3c
BDATA:https_uk.yahoo.com_0
p#https://uk.yahoo.com/#1Breaking News_2
https://uk.yahoo.com/
4Team GB wins first medal of the 2022 Winter Olympics
"eThe men's curling team had to make do with silver after suffering defeat in the final against Sweden.*
Breaking News_22
https://s.yimg.com/uu/api/res/1.2/bXZOZU8N4FY_l39Mtl_hIQ--/cT03NTt3PTgwMDthcHBpZD15dGFjaHlvbjs-/https://media.zenfs.com/en/evening_standard_239/f42048c283100e0fdfcc4d3916a47fdf8
fallback_"
useNNSF"
title"4Team GB wins first medal of the 2022 Winter Olympics"
body"eThe men's curling team had to make do with silver after suffering defeat in the final against Sweden."
url"Ahttps://uk.news.yahoo.com/team-gb-miss-men-curling-095225138.html"
uuid"$f272d807-c46d-3ccf-af9c-f3f360713dd4"
followId_"
timeline_name"
Breaking News"
msg_id"$a820dd0b-7c40-4a3a-9aed-4e5970b55ca8"
notification_id_"
publish_time"
1645265716129"
publisher_msg_id"$9147640a-5334-44b6-9257-499e0ad01d3f"
pl1I
notification_shownN
wB{
r@https://s.yimg.com/cv/apiv2/notifications/YCon_Badge_90_90_2.pngz
*(p#https://uk.yahoo.com/#1Breaking News_20
PDATA:https_bloomer1016.github.io_0
p#https://bloomer1016.github.io/#1Msg61166680
https://bloomer1016.github.io/
Test 1 - 1411
Test 1 - 1411*
Msg611666802Ahttps://cdn.pushalert.co/img/pushalert-square-icon.png?16454743088
url"
https://bloomer1016.github.io/"
url_id"
61166680"
uidI
eidI
type"
hrz
*-p#https://bloomer1016.github.io/#1Msg611666800
PDATA:https_bloomer1016.github.io_0
p#https://bloomer1016.github.io/#1Msg61167281
https://bloomer1016.github.io/
Test 2 - 1423
Test 2 - 1423*
Msg611672812Ahttps://cdn.pushalert.co/img/pushalert-square-icon.png?16454743328
url"
https://bloomer1016.github.io/"
url_id"
61167281"
uidI
eidI
type"
hrz
*-p#https://bloomer1016.github.io/#1Msg611672810
So looking at the snippet from the log above, the push notifications from Yahoo are pretty clear cut (and one could argue that they were clear cut above as well). The interesting part is the one from my Github test page and how it is associated with the PushAlert URL for the icon file which is what I was looking for since I was thinking in terms of redirects in a push notification or something like that.
So after all of this, what did I learn you may ask? Well, as a defender that is using an EDR within the security stack, I know it will not flag on when a user enables site notifications, or when there is a push notification sent to them from a site, but at least I now know some file paths and files that I can refer to and take a deeper look and that are written to disk. This was the case the other day as there was a user that got flagged on some outbound traffic being blocked by the proxy. Looking at the alert, I could see that the user-agent string was Edge, but when I looked at the extensions directory within Edge, there was nothing there. So knowing the Edge is a fork off of the Chromium project, the folders and logs used would be the same. And while there were no extensions, I could see that there were push notifications that had the flagged URLs for fake anti-virus pop-ups and the like in their 00000x.log.
Till next time.