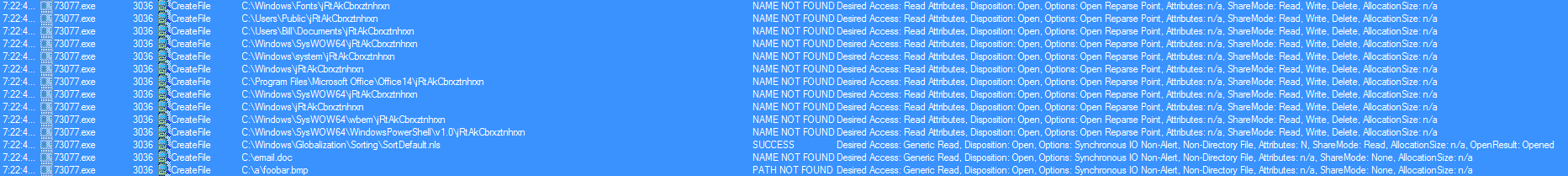
2017-11-17 Maldoc Using CVE 2017-0199
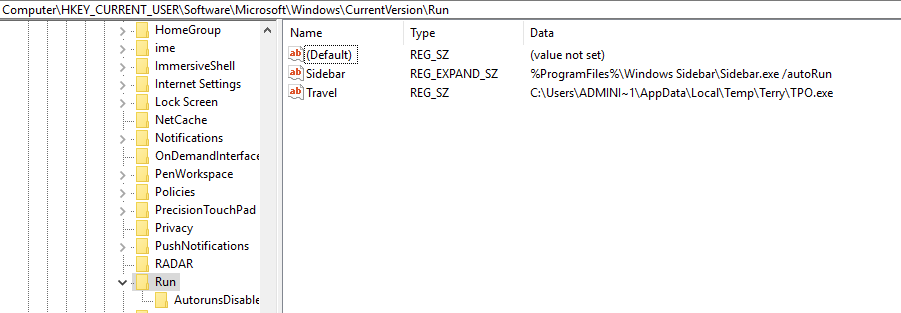
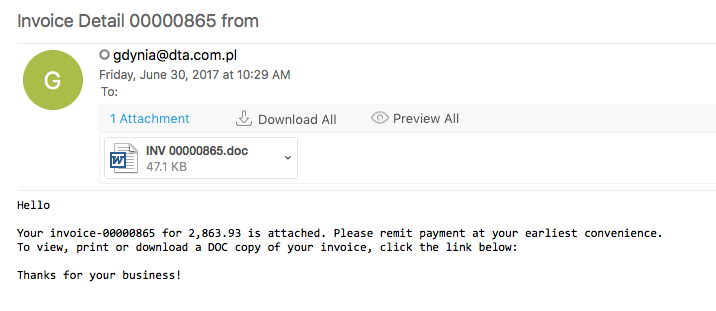
This is a quick writeup on some maldocs that I was able to find in our email filters that used the CVE2017-0199 in them. The emails had the same attachments in them (from a hash perspective) which was a Word document and an Excel spreadsheet. The Word document had a hidden OLE object while the Excel spreadsheet had the hidden OLE object on the 3rd tab in the spreadsheet. Both these Office documents would reach out to a malicious domain and grab the HTA file which would then have code in it to go and doiwnload the actual malicious binary…