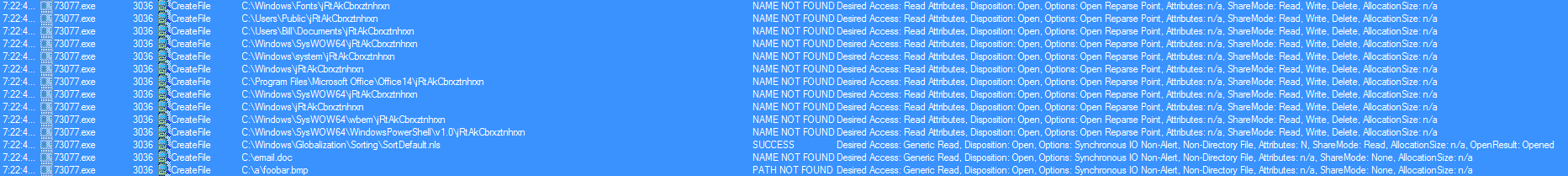
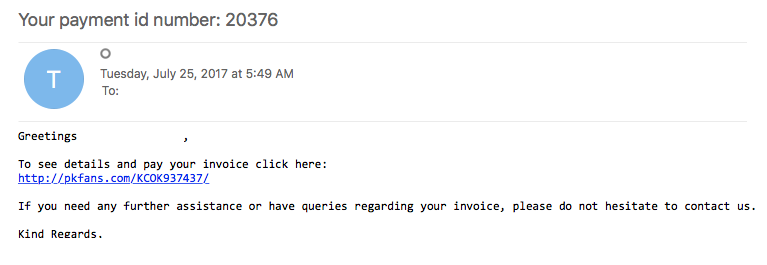
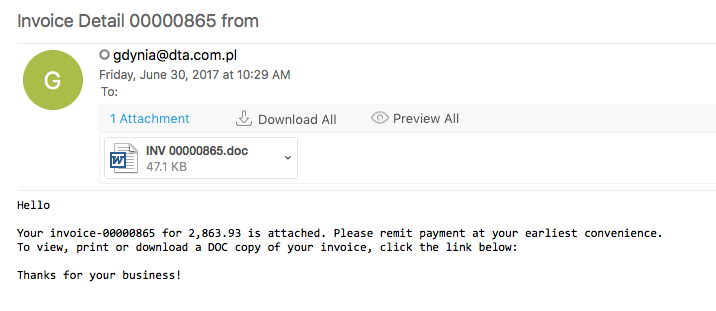
Deobfuscating an Emotet MalDoc Script
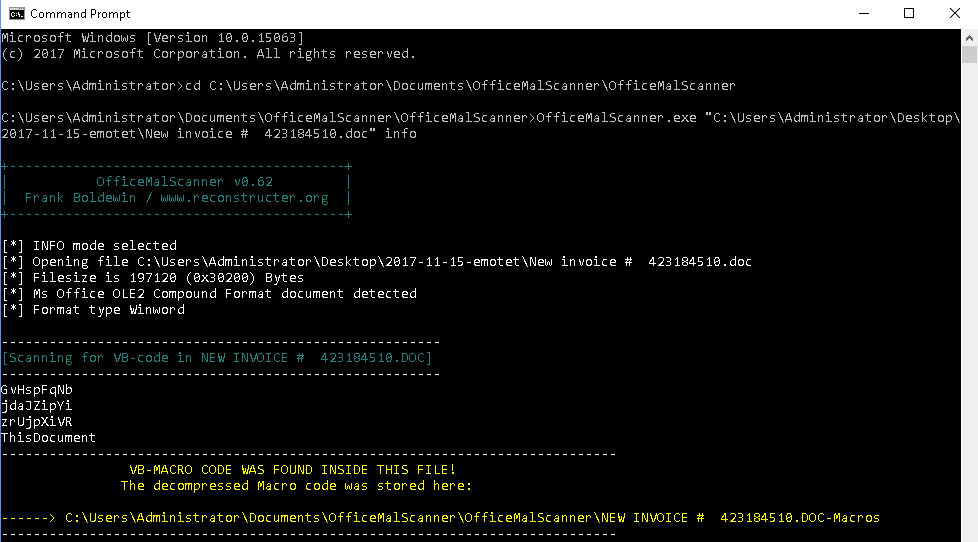
So this post covers the malicious macro script that was found in an older writeup for Emotet which you can find here. While one could develop tools to help deobfuscate the macro script like @David Ledbetter did in his blog post, I wanted to show another way of doing it – manually without any programs or scripts. I wanted to do it this way and document it since I have no talent or skill in the ways of developing programs/scripts to do this kind of work and to show that it is possible to those of us that are “code…