So for today’s update, a change of pace. A couple of weeks ago I came across a Tweet from someone that I follow on Twitter. Unfortunately I can’t find the one that caught my eye, but the link was to Open Analysis Live’s video. The video was covering an “user submission” of a VB script that was attached to a malicious Word doc. I watched it and it made some good sense and was pretty easy to follow. I kept that in the back of my head so when the time came and I got the chance to try this out, I would.
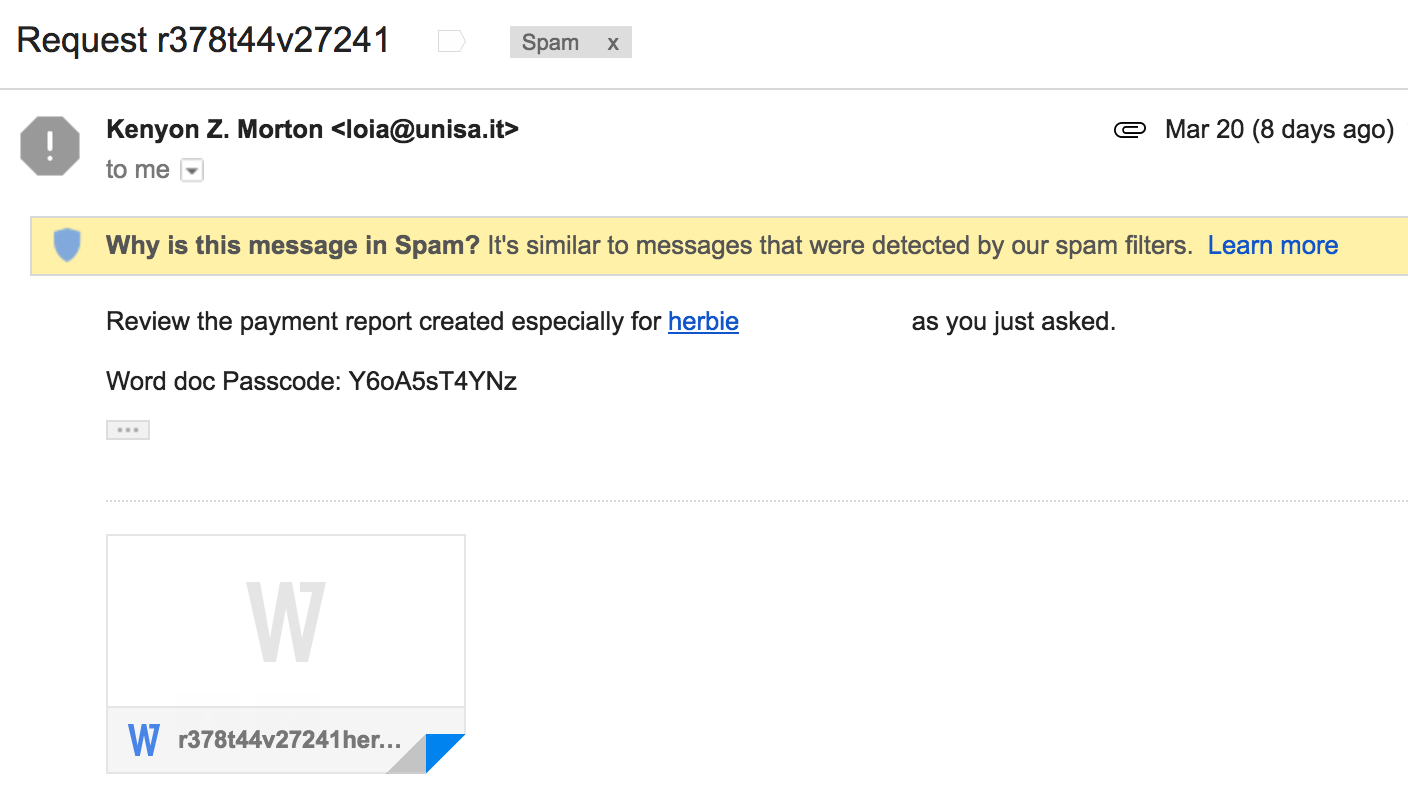
Fast forward to last week and there was this email in my SPAM folder.
For the maldoc, and the code that I was able to deobfuscate and such, check out my repo for this post here.
The email headers from the maldoc.
Delivered-To: herbie@....
Received: by 10.237.51.67 with SMTP id u61csp1294826qtd;
Mon, 20 Mar 2017 07:16:08 -0700 (PDT)
X-Received: by 10.28.14.69 with SMTP id 66mr10312798wmo.27.1490019368589;
Mon, 20 Mar 2017 07:16:08 -0700 (PDT)
Return-Path:
Received: from smtp.unisa.it (mail-out-1.unisa.it. [193.205.165.1])
by mx.google.com with ESMTPS id f21si23226175wrf.78.2017.03.20.07.16.08
for
(version=TLS1_2 cipher=ECDHE-RSA-AES128-GCM-SHA256 bits=128/128);
Mon, 20 Mar 2017 07:16:08 -0700 (PDT)
Received-SPF: pass (google.com: domain of loia@unisa.it designates 193.205.165.1 as permitted sender) client-ip=193.205.165.1;
Authentication-Results: mx.google.com;
spf=pass (google.com: domain of loia@unisa.it designates 193.205.165.1 as permitted sender) smtp.mailfrom=loia@unisa.it
Received: from uuryt (host-58-115-116-4.dynamic.kbtelecom.net [58.115.116.4]) (authenticated bits=0) by smtp.unisa.it (8.14.4/8.14.4) with ESMTP id v2KDp1dC008856 (version=TLSv1/SSLv3 cipher=AES256-SHA bits=256 verify=NO) for ; Mon, 20 Mar 2017 15:15:40 +0100
Date: Mon, 20 Mar 2017 22:15:36 +0800
From: "Kenyon Z. Morton"
Message-Id:
To: herbie@....
Subject: Request r378t44v27241
MIME-Version: 1.0
X-mailer: The Bat Voyager 55.04
Content-type: Multipart/mixed; boundary="------------475786541389322700295399"
Content-Description: Multipart message
X-KLMS-Rule-ID: 1
X-KLMS-Message-Action: skipped, AntiVirus
X-KLMS-AntiSpam-Lua-Profiles: 104832 [Oct 29 2016]
X-KLMS-AntiSpam-Version: 5.6.0.28
X-KLMS-AntiSpam-Envelope-From: loia@unisa.it
X-KLMS-AntiSpam-Rate: 0
X-KLMS-AntiSpam-Status: not_detected
X-KLMS-AntiSpam-Method: none
X-KLMS-AntiSpam-Info: LuaCore: 137 137 5285b9605ed5fe6c3b27b8a035ee01971ae7aa17, Auth:dmarc=none header.from=unisa.it;spf=neutral smtp.mailfrom=unisa.it;dkim=none
X-KLMS-AntiSpam-Interceptor-Info: scan successful
X-KLMS-AntiPhishing: Clean, 2016/10/27 15:29:18
X-KLMS-AntiVirus: Kaspersky Security 8.0 for Linux Mail Server, version 8.0.1.721, bases: 2016/10/28 18:18:00 #8056490
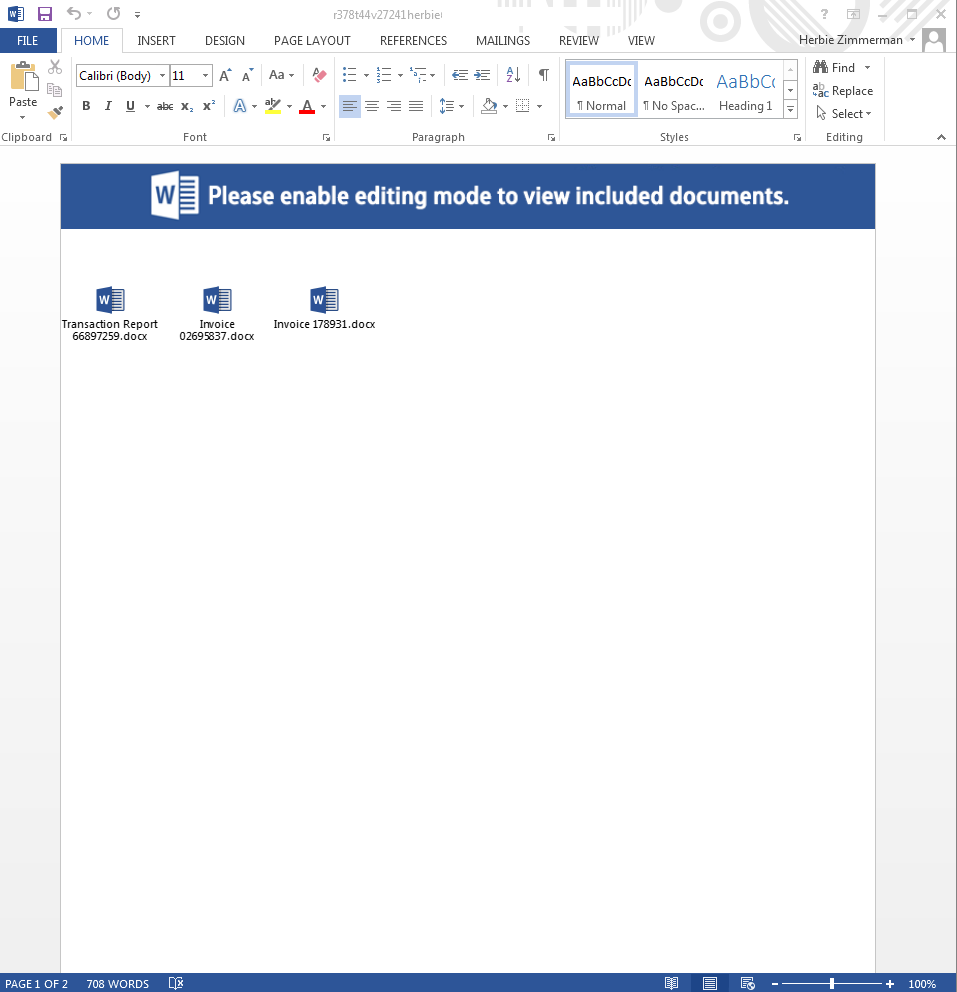
To be honest, I was excited to try my hand at trying to deobfuscate this VB script using the video as a guide. So I started to dig in and needless to say, this one was pretty straight forward. The script that I got was very similar to the one in the video as well which helped. Below are some of the things that I noted when going through this exercise.
– Look for a pattern(s). In this case, most of the time it was 2 lines of garbage with the 3rd line being code.
– CTRL+F was my best friend going through this. If there was any doubt about something, I tried to find it somewhere else where in the code.
– It was easier to remove the junk from the code, and then walk through the code and paste the cleaned up code into another text file that allowed me to see the order/progression from call to call.
– If this is your first time, then make sure you have some time to walk through this. This was the first one that I had ever done and it took some time to walk through.
With that being said, using the video as my guide, I was able to figure out the flow of this and was able to deobfuscate most of the script. Trying to run it on my test VM yielded nothing but an error since the script was cut short.
Over all, this was a great video covering how to do this. I have saved this page and plan on going through some of the other videos as well. Great job Open Analysis!
File details from malspam:
File name: r378t44v2724.docx
File size: 72K
MD5 hash: 6baa49eb4db86758530c08e62e9f6244
VirusTotal: NA
Malwr: NA
Hybrid Analysis: NA