It has been a long while since I have done any blogging. Since it has been a hot minute since I have done a post I thought that I would take this opportunity to learn something new and expand my tool-belt. So this first step back into the blogging world is going to be about a tool called Brim using the latest malware exercise from Brad found over at his site here and the SANS site here. So let’s start with what Brim is – a tool that helps visualize PCAP data in a different way with WAY faster indexing then Wireshark. It also uses it’s own query language called “Zed” while also using some of the same tools found from the *nix world. The interesting part is how it uses Zeek and it’s nomenclature/syntax as well. There is a great video covering the basics of Brim over on their Github page which you can find here: Brim YouTube.
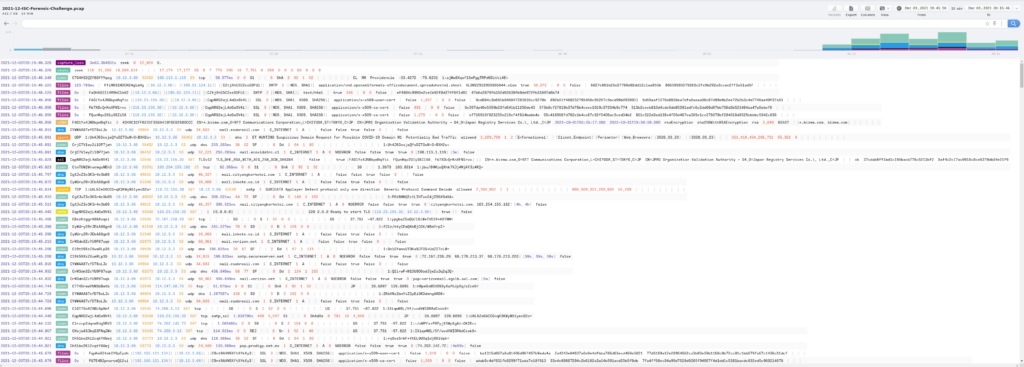
So here is what the PCAP from the exercise looked like when first moving it into Brim.
Looking at this, it immediately reminded me of looking at Bro/Zeek raw logs since it is just a LOT of information all at one (aka: wall of text). Nice thing is that you can toggle the headers in the Brim app (I have it on auto to help save screen real-estate) which makes the data easier to read. The other nice thing is that you can see where a bulk of the activity is and, if needed, focus during that time frame.
With that being said, I focused on the questions that were asked from this exercise while not relying on Wireshark to look/hunt for the answers. The questions asked were:
- What was the IP address of the infected Windows computer?
- What was the host name of the infected Windows computer?
- What was the user account names from the infected Windows computer? (should be "name" not "names")
- What was the date and time the infection activity began?
- What was the family of malware that caused this infection.
With the initial screen up, I wanted to get an idea of what kind of data I was dealing with and where it was. So I started with the following query to help me understand what paths (in my head I think of these like indexes or perhaps sourcetypes from Splunk).
count() by _path | sort -r
This query let me know what the spread looked like from a data perspective and where I may needed to focus my hunt. The other query that I stumbled across stemmed from the Suricata queries built into Brim. The query used here was very much in the same vein of just getting the lay of the land, but from Suricata’s perspective.
count() by event_type
Seeing that Suricata saw “alerts” in the PCAP, I decided to drill down some here. For that I used the generic query of: alert
Here I saw that there were a mix of event-types between “alerts” and “SSL”. After looking at the SSL event-type, I decided that there was nothing there and that I did not need to focus any more there. So I changed the query to:
event_type=="alert"
to help narrow and focus my hunt. Here is where I started really investigating things since I could easily look at the different Suricata alert signatures triggered on while also easily seeing what the timestamp was for said alert. Considering the amount of data presented, I used this query to quickly help summarize what I was seeing from the above query:
event_type=="alert" | count() by alert.severity,alert.category,alert.signature,alert.signature_id,alert.rev | sort -r count
This query allowed me to summarize/count the data for “alert” since I was counting by the sev level, category, signature, and the signature revision.
This helped me answer the question of what type of malware was used in this infection. In this case, it looks to be Emotet/Dridex.
Switching back to the event_type=="alert" query, and scrolling all the way down to the earliest alert, I saw what looks to be the start of the compromise (between 19:42:00 – 19:43:00 timeframe) along with what I saw above – the family of malware associated with this infection.
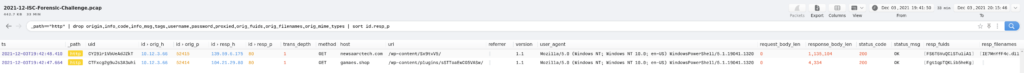
I could also tell what the IP address of the compromised system was (10.12.3.66) and that there was a binary file that was seen in the PCAP as well as PoSH being used via the user-agent right before this binary file. Looking at the log detail for the binary that was downloaded:
I decided to take a quick look at where else these malicious IP addresses was seen in the PCAP. The query used for this was 139.59.6.175 which gave me the following information.
Right clicking on one of the hashes and then clicking on the “Virustotal Lookup” option in the pop-up menu lead me to the Virustotal page where the file was classified as “Dridex/Emotet”. The IP address seen with this binary came up clean on Virustotal and several other OSINT sites via Machinae.
********************************************************************************
* Information for 139.59.6.175
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites</code>
[+] IP Whois Results
[-] ASN Information: ('14061', '139[.]59.0.0/20', '1990-06-27', 'apnic', 'SG')
[-] Network Information: ('139[.]59.0.0/20', 'DOIA2-AP', 'Digital Ocean Inc administrator', '139[.]59.0.0 - 139[.]59.15.255')
[-] Registration Info: ('DigitalOcean, LLC', '2020-05-31')
[-] Registration Locality: IN
[-] Abuse Email: abuse@digitalocean[.]com
abuse@digitalocean[.]com
[+] IPVoid Results
[-] Number of detections: 0
[-] IP Void Detection Rate: 0%
[-] No Malc0de Results
[-] No AbuseIPDB Results
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/139.59.6.175
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/139.59.6.175
[+] Fortinet Category Results
[-] Fortinet URL Category: Not Rated
[-] No VirusTotal pDNS Results
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
One of the only places that I was able to find anything was on URLScan.
Looking at some of the other alerts from this query and drilling in, I wanted to first see what IP addresses were associated with each of the Dridex alerts skipping the SMTP ones as Emotet has, historically, used compromised systems to send out malspam which I suspect this is more of the same. So I will circle back to that later.
ET JA3 Hash - [Abuse.ch] Possible Dridex
ET CNC Feodo Tracker Reported CnC Server group 17
ET CNC Feodo Tracker Reported CnC Server group 18
ET CNC Feodo Tracker Reported CnC Server group 23
Using the following query I was able to pull these with relative ease:
"ET JA3 Hash - [Abuse.ch] Possible Dridex" | count() by dest_ip,dest_port
"ET CNC Feodo Tracker Reported CnC Server group 17" | count() by dest_ip,dest_port
"ET CNC Feodo Tracker Reported CnC Server group 18" | count() by dest_ip,dest_port
"ET CNC Feodo Tracker Reported CnC Server group 23" | count() by dest_ip,dest_port
Leaving me with the following IP addresses (merged for ease of readability):
CNT - IP : Dest_Port
-------------------
26 - 172.104.227.98 : 443
6 - 163.172.50.82 : 443
18 - 91.207.181.106 : 8080
1 - 51.159.35.157 : 443
1 - 51.75.33.120 : 443
1 - 91.207.181.106 : 8080
Machinae gave me back the following details about these IPs:
********************************************************************************
* Information for 172.104.227.98
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites</code>
[+] IP Whois Results
[-] ASN Information: ('63949', '172[.]104.224.0/19', '2015-06-19', 'arin', 'US')
[-] Network Information: ('172[.]104.0.0/15', 'NET-172-104-0-0-1', 'LINODE-US', '172[.]104.0.0 - 172[.]105.255.255')
[-] Registration Info: ('Linode', '2015-06-19', '2016-12-29')
[-] Registration Locality: ('Philadelphia', 'PA', '19106', 'US')
[-] Abuse Email: abuse@linode[.]com
[-] Tech Email: support@linode[.]com
[+] IPVoid Results
[-] Number of detections: 5
[-] IP Void Detection Rate: 6%
[-] Engines: ('CRDF', '(hXXps)://threatcenter[.]crdf[.]fr/check[.]html')
[-] Engines: ('Feodo Tracker', '(hXXps)://feodotracker[.]abuse[.]ch/')
[-] Engines: ('IPsum', 'hXXps://github[.]com/stamparm/ipsum')
[-] Engines: ('JustSpam_org', '(hXXp)://www[.]justspam[.]org/')
[-] Engines: ('Snapt NovaSense', 'hXXps://novasense-threats[.]com/')
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 2
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/172.104.227.98
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/172.104.227.98
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS malicious URLs from VirusTotal: ('2022-01-09', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2022-01-08', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2022-01-07', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2022-01-06', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2022-01-05', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2022-01-05', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2022-01-05', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2022-01-03', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2022-01-02', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-29', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-29', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-29', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-28', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-28', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-26', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-25', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-25', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-25', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-25', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-25', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-25', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-24', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-24', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-24', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-24', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-23', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-20', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-20', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-17', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-17', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-14', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-14', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXp://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-13', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-12', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-12', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-12', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-12', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-12', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-12', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-11', 'hXXps://172[.]104.227.98/')
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 163.172.50.82
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[+] IP Whois Results
[-] ASN Information: ('12876', '163[.]172.0.0/16', '1992-02-14', 'ripencc', 'GB')
[-] Network Information: ('163[.]172.0.0/16', 'ONLINE_NET_DEDICATED_SERVERS', '163[.]172.0.0 - 163[.]172.255.255')
[-] Registration Info: ('Dedicated Servers and cloud assignment, abuse reports : (hXXp)://abuse[.]online[.]net', '2015-09-11', '2015-09-16')
[-] Registration Locality: FR
[+] IPVoid Results
[-] Number of detections: 1
[-] IP Void Detection Rate: 1%
[-] Engines: ('CRDF', '(hXXps)://threatcenter[.]crdf[.]fr/check[.]html')
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 1
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/163.172.50.82
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/163.172.50.82
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS malicious URLs from VirusTotal: ('2021-12-24', 'hXXp://163[.]172.50.82/')
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 91.207.181.106
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[+] IP Whois Results
[-] ASN Information: ('48275', '91[.]207.181.0/24', '2008-10-30', 'ripencc', 'RU')
[-] Network Information: ('91[.]207.180.0/23', 'TSMS-ABKHAZIA-NET', '91[.]207.180.0 - 91[.]207.181.255')
[-] Registration Info: ('Abkhasia, Suhum', '2008-10-30', '2019-04-29')
[-] Registration Locality: RU
[+] IPVoid Results
[-] Number of detections: 5
[-] IP Void Detection Rate: 6%
[-] Engines: ('Barracuda_Reputation_BL', '(hXXp)://www[.]barracudanetworks[.]com/')
[-] Engines: ('CRDF', '(hXXps)://threatcenter[.]crdf[.]fr/check[.]html')
[-] Engines: ('Feodo Tracker', '(hXXps)://feodotracker[.]abuse[.]ch/')
[-] Engines: ('IPsum', 'hXXps://github[.]com/stamparm/ipsum')
[-] Engines: ('Snapt NovaSense', 'hXXps://novasense-threats[.]com/')
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 1
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/91.207.181.106
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/91.207.181.106
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: ('2022-01-06', 'a[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'admi[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'b[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'c[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'd[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'dev[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'dmarc[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'e[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'f[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'g[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'razarizaru[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'suerside[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'tvip[.]am-a[.]su')
[-] pDNS data from VirusTotal: ('2022-01-06', 'www.klient[.]am-a[.]su')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXps://91[.]207.181.106/')
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXp://91[.]207.181.106/')
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 51.159.35.157
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[+] IP Whois Results
[-] ASN Information: ('12876', '51[.]158.0.0/15', '1993-09-01', 'ripencc', 'FR')
[-] Network Information: ('51[.]159.0.0/16', 'ONLINENET_DEDICATED_SERVERS', '51[.]159.0.0 - 51[.]159.255.255')
[-] Registration Info: ('2018-02-09', '2018-02-28')
[-] Registration Locality: FR
[+] IPVoid Results
[-] Number of detections: 3
[-] IP Void Detection Rate: 3%
[-] Engines: ('CRDF', '(hXXps)://threatcenter[.]crdf[.]fr/check[.]html')
[-] Engines: ('IPsum', 'hXXps://github[.]com/stamparm/ipsum')
[-] Engines: ('Snapt NovaSense', 'hXXps://novasense-threats[.]com/')
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 1
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/51.159.35.157
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/51.159.35.157
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS malicious URLs from VirusTotal: ('2021-12-15', 'hXXp://51[.]159.35.157/')
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 51.75.33.120
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[+] IP Whois Results
[-] ASN Information: ('16276', '51[.]75.0.0/16', '1993-09-01', 'ripencc', 'FR')
[-] Network Information: ('51[.]75.33.120/29', 'OVH_251937800', '51[.]75.33.120 - 51[.]75.33.127')
[-] Registration Info: ('Failover Ips', '2019-12-26', '2019-12-26')
[-] Registration Locality: PL
[-] Abuse Email: abuse@ovh[.]net
[+] IPVoid Results
[-] Number of detections: 3
[-] IP Void Detection Rate: 3%
[-] Engines: ('CRDF', '(hXXps)://threatcenter[.]crdf[.]fr/check[.]html')
[-] Engines: ('IPsum', 'hXXps://github[.]com/stamparm/ipsum')
[-] Engines: ('Snapt NovaSense', 'hXXps://novasense-threats[.]com/')
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 1
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/51.75.33.120
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/51.75.33.120
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[!] Error from VirusTotal pDNS: Expecting value: line 1 column 1 (char 0)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
********************************************************************************
* Information for 91.207.181.106
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[+] IP Whois Results
[-] ASN Information: ('48275', '91[.]207.181.0/24', '2008-10-30', 'ripencc', 'RU')
[-] Network Information: ('91[.]207.180.0/23', 'TSMS-ABKHAZIA-NET', '91[.]207.180.0 - 91[.]207.181.255')
[-] Registration Info: ('Abkhasia, Suhum', '2008-10-30', '2019-04-29')
[-] Registration Locality: RU
[+] IPVoid Results
[-] Number of detections: 5
[-] IP Void Detection Rate: 6%
[-] Engines: ('Barracuda_Reputation_BL', '(hXXp)://www[.]barracudanetworks[.]com/')
[-] Engines: ('CRDF', '(hXXps)://threatcenter[.]crdf[.]fr/check[.]html')
[-] Engines: ('Feodo Tracker', '(hXXps)://feodotracker[.]abuse[.]ch/')
[-] Engines: ('IPsum', 'hXXps://github[.]com/stamparm/ipsum')
[-] Engines: ('Snapt NovaSense', 'hXXps://novasense-threats[.]com/')
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 1
[!] Error from RansomwareTracker: 503 Server Error: Backend unavailable, connection timeout for url: https://ransomwaretracker.abuse.ch/host/91.207.181.106
[-] No SANS Results
[!] Error from freegeoip.io: 403 Client Error: Forbidden for url: https://freegeoip.io/json/91.207.181.106
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[!] Error from VirusTotal pDNS: Expecting value: line 1 column 1 (char 0)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
[-] No GreyNoise Results
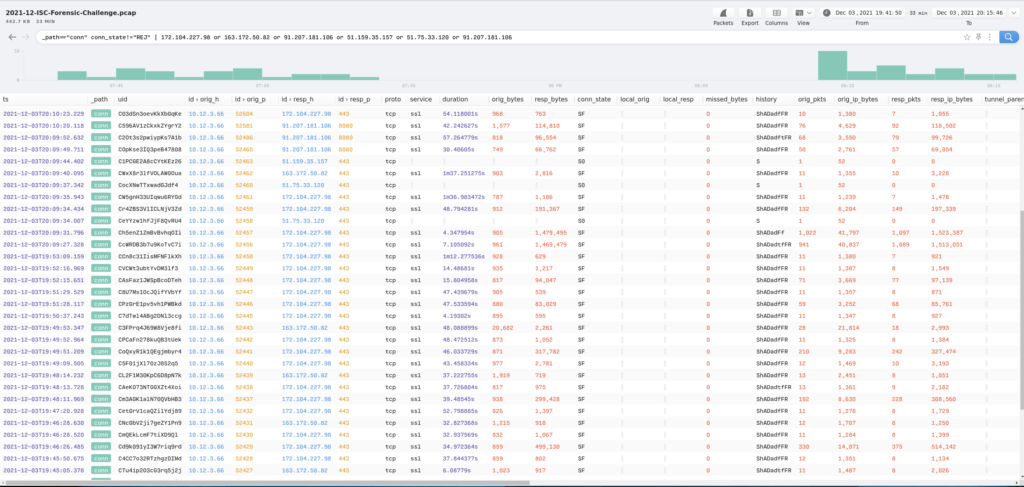
I pivoted to see what kind of connections had been made to these malicious IP addresses. I did this using the following query:
_path=="conn" conn_state!="REJ" | 172.104.227.98 or 163.172.50.82 or 91.207.181.106 or 51.159.35.157 or 51.75.33.120 or 91.207.181.106
where conn_state!="REJ" excluded anything with the REJ status (see this link from the Zeek doc for more information). That gave me the following:
It was here that I could see how frequent the callouts where from the compromised system and how much data was passed. It also looks like the traffic is either encrypted (TCP/443) or encoded (TCP/8080) so unfortunately I could not see what happened there.
I then pivoted from here to see how many malicious JA3/JA3S hashes were seen based on IP address. Using the query:
_path=="ssl" | count() by id.resp_h,ja3,ja3s | sort -r count
gave me the following list of IPs/hashes:
id.resp_h ja3 ja3s count 172.104.227.98 51c64c77e60f3980eea90869b68c58a8 fd4bc6cea4877646ccd62f0792ec0b62 23 91.207.181.106 51c64c77e60f3980eea90869b68c58a8 fd4bc6cea4877646ccd62f0792ec0b62 16 212.227.15.183 37cdab6ff1bd1c195bacb776c5213bf2 265fb1760174263f1728167115d17fe8 10 108.177.122.108 37cdab6ff1bd1c195bacb776c5213bf2 187380bdca925da6fbafacf0d356d2fe 8 81.169.145.133 37cdab6ff1bd1c195bacb776c5213bf2 e54965894d6b45ecb4323c7ea3d6c115 7 194.25.134.114 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 6 173.247.253.179 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 5 202.53.169.50 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 4 108.177.122.108 37cdab6ff1bd1c195bacb776c5213bf2 2b341b88c742e940cfb485ce7d93dde7 4 213.165.67.113 37cdab6ff1bd1c195bacb776c5213bf2 265fb1760174263f1728167115d17fe8 4 172.104.227.98 51c64c77e60f3980eea90869b68c58a8 ec74a5c51106f0419184d0dd08fb05bc 3 163.172.50.82 51c64c77e60f3980eea90869b68c58a8 fd4bc6cea4877646ccd62f0792ec0b62 3 204.79.197.200 6271f898ce5be7dd52b0fc260d0662b3 fbe594b39bb5d9c53aa4f6caf8d2950c 3 80.67.29.4 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 3 64.233.177.16 37cdab6ff1bd1c195bacb776c5213bf2 2b341b88c742e940cfb485ce7d93dde7 3 118.69.221.62 37cdab6ff1bd1c195bacb776c5213bf2 ae4edc6faf64d08308082ad26be60767 3 163.172.50.82 51c64c77e60f3980eea90869b68c58a8 ec74a5c51106f0419184d0dd08fb05bc 3 74.208.5.15 37cdab6ff1bd1c195bacb776c5213bf2 265fb1760174263f1728167115d17fe8 3 212.227.17.168 37cdab6ff1bd1c195bacb776c5213bf2 265fb1760174263f1728167115d17fe8 2 108.167.153.167 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 2 199.79.63.117 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 2 194.25.134.46 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 2 192.185.169.164 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 2 195.4.92.213 37cdab6ff1bd1c195bacb776c5213bf2 7c77dc02a42c4259b2f00e282bf3f89d 2 91.207.181.106 51c64c77e60f3980eea90869b68c58a8 ec74a5c51106f0419184d0dd08fb05bc 2 74.220.199.65 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 2 184.168.200.246 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 2 213.46.255.64 37cdab6ff1bd1c195bacb776c5213bf2 76c691f46143bf86e2d1bb73c6187767 2 2.207.150.234 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 2 213.165.67.124 37cdab6ff1bd1c195bacb776c5213bf2 265fb1760174263f1728167115d17fe8 2 208.91.199.15 37cdab6ff1bd1c195bacb776c5213bf2 649d6810e8392f63dc311eecb6b7098b 1 118.23.155.30 37cdab6ff1bd1c195bacb776c5213bf2 5af4c2c17ac0918c8ce8379db04e21f9 1 194.150.248.156 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 74.220.206.23 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 171.25.222.37 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 86.111.37.33 37cdab6ff1bd1c195bacb776c5213bf2 5af4c2c17ac0918c8ce8379db04e21f9 1 173.201.192.229 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 94.73.163.242 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 204.79.197.203 37f463bf4616ecd445d4a1937da06e19 1ae6020839f37465cc81f5f37480fd1e 1 106.187.245.203 37cdab6ff1bd1c195bacb776c5213bf2 adc06261ef82c2e4688b3cf08c1b2f24 1 103.138.88.100 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 77.55.141.119 37cdab6ff1bd1c195bacb776c5213bf2 1af33e1657631357c73119488045302c 1 195.186.120.54 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 212.77.101.1 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 20.72.205.209 28a2c9bd18a11de089ef85a160da29e4 3ffaa1393a2bf5ecfc7b6b2323452f2d 1 52.109.12.23 28a2c9bd18a11de089ef85a160da29e4 67bfe5d15ae567fb35fd7837f0116eec 1 194.177.200.158 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 1 199.168.117.91 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 211.13.204.5 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 203.211.136.199 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 186.202.161.96 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 23.3.6.28 3b5074b1b5d032e5620f69f9f700ff0e 4b7d5f58af981be54baeda917533e5d8 1 103.20.190.24 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 192.185.121.134 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 52.109.8.24 a0e9f5d64349fb13191bc781f81f42e1 986571066668055ae9481cb84fda634a 1 59.157.128.3 37cdab6ff1bd1c195bacb776c5213bf2 5af4c2c17ac0918c8ce8379db04e21f9 1 186.64.117.195 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 193.70.98.8 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 1 149.126.6.109 37cdab6ff1bd1c195bacb776c5213bf2 303951d4c50efb2e991652225a6f02b1 1 65.99.225.177 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 64.136.52.50 37cdab6ff1bd1c195bacb776c5213bf2 7b6819ed58e8d8415604b7dfcef92d55 1 52.109.12.19 a0e9f5d64349fb13191bc781f81f42e1 986571066668055ae9481cb84fda634a 1 151.80.93.33 37cdab6ff1bd1c195bacb776c5213bf2 b8d072db1f2e5be0acbae44d5808eca0 1 68.178.252.229 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 65.87.230.25 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 77.244.243.66 37cdab6ff1bd1c195bacb776c5213bf2 e54965894d6b45ecb4323c7ea3d6c115 1 93.157.100.35 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 1 89.161.196.12 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 1 192.254.250.163 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 34.68.202.102 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 1 108.179.194.17 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 184.168.200.22 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 89.216.47.170 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 51.81.229.171 37cdab6ff1bd1c195bacb776c5213bf2 853a40879f82a9da4ed2e19c590c05ea 1 206.188.198.65 37cdab6ff1bd1c195bacb776c5213bf2 5af4c2c17ac0918c8ce8379db04e21f9 1 95.110.223.11 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 213.191.128.76 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 89.161.250.151 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 1 108.167.189.110 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 212.227.17.190 37cdab6ff1bd1c195bacb776c5213bf2 265fb1760174263f1728167115d17fe8 1 185.151.28.85 37cdab6ff1bd1c195bacb776c5213bf2 1 203.219.165.58 37cdab6ff1bd1c195bacb776c5213bf2 faa88e75a7471aaa07850841e28f87f1 1 20.50.201.200 28a2c9bd18a11de089ef85a160da29e4 678aeaf909676262acfb913ccb78a126 1 40.83.240.146 3b5074b1b5d032e5620f69f9f700ff0e ae4edc6faf64d08308082ad26be60767 1 96.114.157.81 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 194.25.134.110 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 1 80.249.167.173 37cdab6ff1bd1c195bacb776c5213bf2 5af4c2c17ac0918c8ce8379db04e21f9 1 216.172.184.136 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 166.78.79.129 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 162.241.252.143 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 192.252.149.15 37cdab6ff1bd1c195bacb776c5213bf2 ec74a5c51106f0419184d0dd08fb05bc 1 208.84.244.140 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 66.111.4.52 37cdab6ff1bd1c195bacb776c5213bf2 1af33e1657631357c73119488045302c 1 202.137.236.12 37cdab6ff1bd1c195bacb776c5213bf2 5af4c2c17ac0918c8ce8379db04e21f9 1 207.8.183.5 37cdab6ff1bd1c195bacb776c5213bf2 9706b574e4b03c78a957ef707abe134f 1 200.63.98.23 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 205.178.146.249 37cdab6ff1bd1c195bacb776c5213bf2 5af4c2c17ac0918c8ce8379db04e21f9 1 52.109.8.24 28a2c9bd18a11de089ef85a160da29e4 67bfe5d15ae567fb35fd7837f0116eec 1 68.178.252.101 37cdab6ff1bd1c195bacb776c5213bf2 e35df3e00ca4ef31d42b34bebaa2f86e 1 192.64.117.195 37cdab6ff1bd1c195bacb776c5213bf2 0debd3853f330c574b05e0b6d882dc27 1 52.153.255.201 6271f898ce5be7dd52b0fc260d0662b3 ae4edc6faf64d08308082ad26be60767 1 80.237.132.157 37cdab6ff1bd1c195bacb776c5213bf2 7c77dc02a42c4259b2f00e282bf3f89d 1
Seeing how much data was there, I scaled this back to only give me the hashes that were unique via the the following query:
_path=="ssl" | cut | sort | uniq
Note that I had to use ja3 OR ja3s individually in the above query which was then piped into sort since it would group all the same hashes together which would then be normalized via the “uniq” command.
ja3 28a2c9bd18a11de089ef85a160da29e4 37cdab6ff1bd1c195bacb776c5213bf2 37f463bf4616ecd445d4a1937da06e19 3b5074b1b5d032e5620f69f9f700ff0e 51c64c77e60f3980eea90869b68c58a8 6271f898ce5be7dd52b0fc260d0662b3 a0e9f5d64349fb13191bc781f81f42e1 ja3s 0debd3853f330c574b05e0b6d882dc27 187380bdca925da6fbafacf0d356d2fe 1ae6020839f37465cc81f5f37480fd1e 1af33e1657631357c73119488045302c 265fb1760174263f1728167115d17fe8 2b341b88c742e940cfb485ce7d93dde7 303951d4c50efb2e991652225a6f02b1 3ffaa1393a2bf5ecfc7b6b2323452f2d 4b7d5f58af981be54baeda917533e5d8 5af4c2c17ac0918c8ce8379db04e21f9 649d6810e8392f63dc311eecb6b7098b 678aeaf909676262acfb913ccb78a126 67bfe5d15ae567fb35fd7837f0116eec 76c691f46143bf86e2d1bb73c6187767 7b6819ed58e8d8415604b7dfcef92d55 7c77dc02a42c4259b2f00e282bf3f89d 853a40879f82a9da4ed2e19c590c05ea 9706b574e4b03c78a957ef707abe134f 986571066668055ae9481cb84fda634a adc06261ef82c2e4688b3cf08c1b2f24 ae4edc6faf64d08308082ad26be60767 b8d072db1f2e5be0acbae44d5808eca0 e35df3e00ca4ef31d42b34bebaa2f86e e54965894d6b45ecb4323c7ea3d6c115 ec74a5c51106f0419184d0dd08fb05bc faa88e75a7471aaa07850841e28f87f1 fbe594b39bb5d9c53aa4f6caf8d2950c fd4bc6cea4877646ccd62f0792ec0b62
The only one that was found over on SSLBL Abuse was 51c64c77e60f3980eea90869b68c58a8 which has been seen as early as December 25th and also classified as “Dridex”.
So now knowing the timeframe of the infection, the IP address of the compromised system, and the malware used here in this compromise, the only thing that is left to check are 1) did the compromised system talk to any other systems on the network, 2) what were the HTTP requests like and 3) what are the SMTP messages about. So checking to see what kind of communications happened between this system and any others on the internal network I used this query looking for anything that was more then 4 packets from the source or destination:
id.orig_h==10.12.3.0/24 and id.resp_h==10.12.3.0/24 | cut ts,uid,id.orig_h,id.orig_p,id.resp_h,id.resp_p,proto,service,duration,orig_bytes,resp_bytes,conn_state,history,orig_pkts,orig_ip_bytes,resp_pkts,resp_ip_bytes | orig_pkts >= 4 and resp_pkts >= 4 | sort -r duration
I didn’t see anything that stood out as being malicious and no other systems outside of the DC were found.
For any HTTP communications, I really didn’t see much there outside of what was found already as seen below.
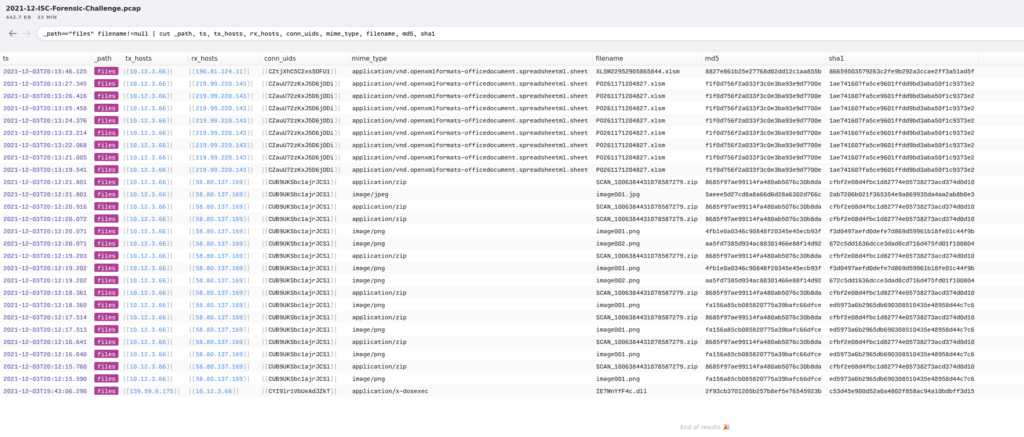
I also remembered that there were other files seen in the PCAP that I forgot about. Using the following query I was able to take a quick look at them. Based on those results, there were some image files, some Excel macro-spreadsheets, and some zip files. Once again knowing that this is related to Emotet, I am pretty sure that this is related to malspam and the SMTP messages that I saw earlier.
_path=="files" filename!=null | cut _path, ts, tx_hosts, rx_hosts, conn_uids, mime_type, filename, md5, sha1
Exporting out the hashes and performing a “uniq” like above, I was able to get the following information.
_path=="files" filename!=null | cut filename, md5, sha1 | sort | uniq
filename md5 sha1 IE7MnYfF4c.dll 2f93cb3701205b257b8ef5e76545923b c53d45e900d52a0a4802f858ac94a10bdbff3d15 PO261171204827.xlsm f1f0d756f2a033f3c0e3ba93e9d7700e 1ae741607fa5ce9601ffdd9bd3aba50f1c9373e2 SCAN_1006384431078587279.zip 8685f97ae99114fa480ab5076c30b8da cfbf2e08d4fbc1d82774e05738273acd374d0d10 XLSM22952905865844.xlsm 8827e861b25e27768d02dd12c1aa855b 86659503579263c2fe9b292a3ccae2ff3a51ad5f image001.jpg 5aeee5d27cd8a8a66d6d28a6302d766c 2ab7206b021f365354e9a869935da4aa2ab8b0e3 image001.png 4fb1e0a0346c90848f20345e45ecb93f f3d0497aefd0defe7d869d59961b18fe01c44f9b image001.png fa156a85cb085820775a39bafc66dfce ed5973a6b2965db690308510435e48958d44c7c6 image002.png aa5fd7385d934ac88301466e88f14d92 672c5dd1636dcce3dad8cd716d475fd01f100804
Looking those hashes up with Machinae gave me back the following hits:
2f93cb3701205b257b8ef5e76545923b
c53d45e900d52a0a4802f858ac94a10bdbff3d15
f1f0d756f2a033f3c0e3ba93e9d7700e
1ae741607fa5ce9601ffdd9bd3aba50f1c9373e2
8827e861b25e27768d02dd12c1aa855b
86659503579263c2fe9b292a3ccae2ff3a51ad5f
********************************************************************************
* Information for 2f93cb3701205b257b8ef5e76545923b
* Observable type: hash (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[-] No Malc0de Results
[+] VirusTotal File Report Results
[-] Date submitted: 2021-12-20 08:06:09
[-] Detected engines: 51
[-] Total engines: 67
[-] Scans: ('Lionic', 'Trojan[.]Win32[.]Emotet.L!c')
[-] Scans: ('MicroWorld-eScan', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('FireEye', 'Generic[.]mg.2f93cb3701205b25')
[-] Scans: ('CAT-QuickHeal', 'Trojan[.]IGENERIC')
[-] Scans: ('McAfee', 'Emotet-FSQ!2F93CB370120')
[-] Scans: ('Cylance', 'Unsafe')
[-] Scans: ('Zillya', 'Trojan[.]Emotet[.]Win32.62068')
[-] Scans: ('K7AntiVirus', 'Trojan ( 0058b4901 )')
[-] Scans: ('Alibaba', 'Trojan:Win32/Emotet.8317975f')
[-] Scans: ('K7GW', 'Trojan ( 0058b4901 )')
[-] Scans: ('CrowdStrike', 'win/malicious_confidence_100% (W)')
[-] Scans: ('VirIT', 'Trojan.Win32[.]Emotet[.]DDW')
[-] Scans: ('Cyren', 'W32/Emotet[.]EDV[.]gen!Eldorado')
[-] Scans: ('Symantec', 'Trojan Horse')
[-] Scans: ('ESET-NOD32', 'a variant of Win32/Kryptik[.]HNNQ')
[-] Scans: ('TrendMicro-HouseCall', 'TrojanSpy.Win32[.]EMOTET[.]YXBLCZ')
[-] Scans: ('Paloalto', 'generic[.]ml')
[-] Scans: ('ClamAV', 'Win[.]Malware[.]Generic-9909860-0')
[-] Scans: ('Kaspersky', 'Trojan-Banker.Win32[.]Emotet[.]ghji')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('Avast', 'Win32:CrypterX-gen [Trj]')
[-] Scans: ('Tencent', 'Malware[.]Win32[.]Gencirc.10cf91d4')
[-] Scans: ('Ad-Aware', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('Sophos', 'Mal/Generic-R + Troj/Emotet-CWR')
[-] Scans: ('Comodo', '.UnclassifiedMalware@0')
[-] Scans: ('DrWeb', 'Trojan[.]Emotet.1124')
[-] Scans: ('TrendMicro', 'TrojanSpy.Win32[.]EMOTET[.]YXBLCZ')
[-] Scans: ('McAfee-GW-Edition', 'Emotet-FSQ!2F93CB370120')
[-] Scans: ('Emsisoft', 'Trojan[.]Crypt (A)')
[-] Scans: ('GData', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('Jiangmin', 'Trojan.Banker[.]Emotet[.]qzt')
[-] Scans: ('Webroot', 'W32[.]Trojan[.]Emotet')
[-] Scans: ('Avira', 'TR/AD[.]Nekark[.]avuwq')
[-] Scans: ('MAX', 'malware (ai score=81)')
[-] Scans: ('Antiy-AVL', 'Trojan/Generic[.]ASMalwS.34E4DB1')
[-] Scans: ('Kingsoft', 'Win32[.]Troj[.]Generic_a.a.(kcloud)')
[-] Scans: ('Gridinsoft', 'Ransom.Win32[.]Sabsik[.]oa')
[-] Scans: ('Microsoft', 'Trojan:Win32/Emotet[.]PAM!MTB')
[-] Scans: ('Cynet', 'Malicious (score: 100)')
[-] Scans: ('AhnLab-V3', 'Trojan/Win[.]Emotet.R456215')
[-] Scans: ('VBA32', 'TrojanBanker[.]Emotet')
[-] Scans: ('ALYac', 'Trojan[.]Agent[.]Emotet')
[-] Scans: ('Malwarebytes', 'Trojan[.]Crypt')
[-] Scans: ('Ikarus', 'Trojan[.]Win32[.]Crypt')
[-] Scans: ('Rising', 'Trojan[.]Kryptik!1.DAEF (CLASSIC)')
[-] Scans: ('Yandex', 'Trojan[.]PWS[.]Emotet!kI3B40T2sck')
[-] Scans: ('SentinelOne', 'Static AI - Suspicious PE')
[-] Scans: ('MaxSecure', 'Trojan[.]Malware.133255221[.]susgen')
[-] Scans: ('Fortinet', 'W32/Mikey.D205!tr')
[-] Scans: ('AVG', 'Win32:CrypterX-gen [Trj]')
[-] Scans: ('Panda', 'Trj/GdSda.A')
[!] Error from ThreatExpert: HTTPConnectionPool(host='www.threatexpert.com', port=80): Max retries exceeded with url: /report.aspx?md5=2f93cb3701205b257b8ef5e76545923b (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[-] No VxVault Results
[!] Error from Cymru MHR: HTTPSConnectionPool(host='hash.cymru.com', port=443): Max retries exceeded with url: /cgi-bin/bulkmhr.cgi (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[+] MetaDefender File Report Results
[-] Date submitted: 2021-12-06T05:35:38.444Z
[-] Detected engines: 12
[-] Total engines: 34
[-] Scans: ('Ahnlab', 'Trojan/Win[.]Emotet')
[-] Scans: ('Avira', 'TR/AD[.]Nekark[.]avuwq')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('ClamAV', 'Win[.]Malware[.]Generic-9909860-0')
[-] Scans: ('Cyren', 'W32/Emotet[.]EDV[.]gen!Eldorado')
[-] Scans: ('ESET', 'a variant of Win32/Kryptik[.]HNNQ trojan')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.47553818 (B)')
[-] Scans: ('Huorong', 'Trojan/Emotet[.]ki')
[-] Scans: ('Ikarus', 'Trojan[.]Win32[.]Crypt')
[-] Scans: ('Jiangmin', 'Unavailable (production)')
[-] Scans: ('K7', 'Trojan ( 0058b4901 )')
[-] Scans: ('Kaspersky', 'Trojan-Banker.Win32[.]Emotet[.]ghji')
[-] Scans: ('Xvirus Personal Guard', 'Hacktool[.]Crypter.40')
********************************************************************************
* Information for c53d45e900d52a0a4802f858ac94a10bdbff3d15
* Observable type: hash.sha1 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2021-12-20 08:06:09
[-] Detected engines: 51
[-] Total engines: 67
[-] Scans: ('Lionic', 'Trojan[.]Win32[.]Emotet.L!c')
[-] Scans: ('MicroWorld-eScan', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('FireEye', 'Generic[.]mg.2f93cb3701205b25')
[-] Scans: ('CAT-QuickHeal', 'Trojan[.]IGENERIC')
[-] Scans: ('McAfee', 'Emotet-FSQ!2F93CB370120')
[-] Scans: ('Cylance', 'Unsafe')
[-] Scans: ('Zillya', 'Trojan[.]Emotet[.]Win32.62068')
[-] Scans: ('K7AntiVirus', 'Trojan ( 0058b4901 )')
[-] Scans: ('Alibaba', 'Trojan:Win32/Emotet.8317975f')
[-] Scans: ('K7GW', 'Trojan ( 0058b4901 )')
[-] Scans: ('CrowdStrike', 'win/malicious_confidence_100% (W)')
[-] Scans: ('VirIT', 'Trojan.Win32[.]Emotet[.]DDW')
[-] Scans: ('Cyren', 'W32/Emotet[.]EDV[.]gen!Eldorado')
[-] Scans: ('Symantec', 'Trojan Horse')
[-] Scans: ('ESET-NOD32', 'a variant of Win32/Kryptik[.]HNNQ')
[-] Scans: ('TrendMicro-HouseCall', 'TrojanSpy.Win32[.]EMOTET[.]YXBLCZ')
[-] Scans: ('Paloalto', 'generic[.]ml')
[-] Scans: ('ClamAV', 'Win[.]Malware[.]Generic-9909860-0')
[-] Scans: ('Kaspersky', 'Trojan-Banker.Win32[.]Emotet[.]ghji')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('Avast', 'Win32:CrypterX-gen [Trj]')
[-] Scans: ('Tencent', 'Malware[.]Win32[.]Gencirc.10cf91d4')
[-] Scans: ('Ad-Aware', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('Sophos', 'Mal/Generic-R + Troj/Emotet-CWR')
[-] Scans: ('Comodo', '.UnclassifiedMalware@0')
[-] Scans: ('DrWeb', 'Trojan[.]Emotet.1124')
[-] Scans: ('TrendMicro', 'TrojanSpy.Win32[.]EMOTET[.]YXBLCZ')
[-] Scans: ('McAfee-GW-Edition', 'Emotet-FSQ!2F93CB370120')
[-] Scans: ('Emsisoft', 'Trojan[.]Crypt (A)')
[-] Scans: ('GData', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('Jiangmin', 'Trojan.Banker[.]Emotet[.]qzt')
[-] Scans: ('Webroot', 'W32[.]Trojan[.]Emotet')
[-] Scans: ('Avira', 'TR/AD[.]Nekark[.]avuwq')
[-] Scans: ('MAX', 'malware (ai score=81)')
[-] Scans: ('Antiy-AVL', 'Trojan/Generic[.]ASMalwS.34E4DB1')
[-] Scans: ('Kingsoft', 'Win32[.]Troj[.]Generic_a.a.(kcloud)')
[-] Scans: ('Gridinsoft', 'Ransom.Win32[.]Sabsik[.]oa')
[-] Scans: ('Microsoft', 'Trojan:Win32/Emotet[.]PAM!MTB')
[-] Scans: ('Cynet', 'Malicious (score: 100)')
[-] Scans: ('AhnLab-V3', 'Trojan/Win[.]Emotet.R456215')
[-] Scans: ('VBA32', 'TrojanBanker[.]Emotet')
[-] Scans: ('ALYac', 'Trojan[.]Agent[.]Emotet')
[-] Scans: ('Malwarebytes', 'Trojan[.]Crypt')
[-] Scans: ('Ikarus', 'Trojan[.]Win32[.]Crypt')
[-] Scans: ('Rising', 'Trojan[.]Kryptik!1.DAEF (CLASSIC)')
[-] Scans: ('Yandex', 'Trojan[.]PWS[.]Emotet!kI3B40T2sck')
[-] Scans: ('SentinelOne', 'Static AI - Suspicious PE')
[-] Scans: ('MaxSecure', 'Trojan[.]Malware.133255221[.]susgen')
[-] Scans: ('Fortinet', 'W32/Mikey.D205!tr')
[-] Scans: ('AVG', 'Win32:CrypterX-gen [Trj]')
[-] Scans: ('Panda', 'Trj/GdSda.A')
[!] Error from Cymru MHR: HTTPSConnectionPool(host='hash.cymru.com', port=443): Max retries exceeded with url: /cgi-bin/bulkmhr.cgi (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[+] MetaDefender File Report Results
[-] Date submitted: 2021-12-06T05:35:38.444Z
[-] Detected engines: 12
[-] Total engines: 34
[-] Scans: ('Ahnlab', 'Trojan/Win[.]Emotet')
[-] Scans: ('Avira', 'TR/AD[.]Nekark[.]avuwq')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.47553818')
[-] Scans: ('ClamAV', 'Win[.]Malware[.]Generic-9909860-0')
[-] Scans: ('Cyren', 'W32/Emotet[.]EDV[.]gen!Eldorado')
[-] Scans: ('ESET', 'a variant of Win32/Kryptik[.]HNNQ trojan')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.47553818 (B)')
[-] Scans: ('Huorong', 'Trojan/Emotet[.]ki')
[-] Scans: ('Ikarus', 'Trojan[.]Win32[.]Crypt')
[-] Scans: ('Jiangmin', 'Unavailable (production)')
[-] Scans: ('K7', 'Trojan ( 0058b4901 )')
[-] Scans: ('Kaspersky', 'Trojan-Banker.Win32[.]Emotet[.]ghji')
[-] Scans: ('Xvirus Personal Guard', 'Hacktool[.]Crypter.40')
********************************************************************************
* Information for f1f0d756f2a033f3c0e3ba93e9d7700e
* Observable type: hash (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[-] No Malc0de Results
[+] VirusTotal File Report Results
[-] Date submitted: 2021-12-10 16:28:17
[-] Detected engines: 29
[-] Total engines: 59
[-] Scans: ('Lionic', 'Trojan[.]MSOffice[.]Emotet.4!c')
[-] Scans: ('ClamAV', 'Xls[.]Downloader[.]EmotetExcel122100-9913103-0')
[-] Scans: ('McAfee', 'Downloader-FCHG!F4546CFAAF78')
[-] Scans: ('K7AntiVirus', 'Trojan ( 0058b5021 )')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('K7GW', 'Trojan ( 0058b5021 )')
[-] Scans: ('Arcabit', 'Trojan[.]Generic.D246B115')
[-] Scans: ('Cyren', 'XML/Agent[.]KD')
[-] Scans: ('ESET-NOD32', 'DOC/TrojanDownloader[.]Agent[.]DOH')
[-] Scans: ('Avast', 'VBS:Malware-gen')
[-] Scans: ('Cynet', 'Malicious (score: 99)')
[-] Scans: ('Kaspersky', 'HEUR:Trojan.MSOffice[.]Emotet[.]gen')
[-] Scans: ('Alibaba', 'TrojanDownloader:Office97/Emotet.3e3309f5')
[-] Scans: ('MicroWorld-eScan', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('Tencent', 'Trojan[.]MsOffice[.]XmlMacroSheet.11017772')
[-] Scans: ('Ad-Aware', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.38187285 (B)')
[-] Scans: ('DrWeb', 'W97M[.]DownLoader.5470')
[-] Scans: ('McAfee-GW-Edition', 'Artemis!Trojan')
[-] Scans: ('FireEye', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('Ikarus', 'Trojan-Downloader[.]XLM[.]Agent')
[-] Scans: ('GData', 'XML.Trojan[.]Agent[.]AOBTAI')
[-] Scans: ('Avira', 'W2000M/YAV[.]Minerva[.]eltuf')
[-] Scans: ('MAX', 'malware (ai score=85)')
[-] Scans: ('Microsoft', 'TrojanDownloader:O97M/Emotet!MTB')
[-] Scans: ('Zoner', 'Probably Heur.W97ShellN')
[-] Scans: ('Rising', 'Downloader[.]Agent/XLM!1.DADA (CLASSIC)')
[-] Scans: ('Fortinet', 'XML/Agent[.]AA!tr[.]dldr')
[-] Scans: ('AVG', 'VBS:Malware-gen')
[!] Error from ThreatExpert: HTTPConnectionPool(host='www.threatexpert.com', port=80): Max retries exceeded with url: /report.aspx?md5=f1f0d756f2a033f3c0e3ba93e9d7700e (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[-] No VxVault Results
[!] Error from Cymru MHR: HTTPSConnectionPool(host='hash.cymru.com', port=443): Max retries exceeded with url: /cgi-bin/bulkmhr.cgi (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[+] MetaDefender File Report Results
[-] Date submitted: 2021-12-06T02:05:47.332Z
[-] Detected engines: 4
[-] Total engines: 34
[-] Scans: ('Avira', 'W2000M/YAV[.]Minerva[.]eltuf')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.38187285 (B)')
[-] Scans: ('Ikarus', 'Trojan-Downloader[.]DOC[.]Agent')
[-] Scans: ('RocketCyber', '')
[-] Scans: ('Webroot SMD', '')
********************************************************************************
* Information for 1ae741607fa5ce9601ffdd9bd3aba50f1c9373e2
* Observable type: hash.sha1 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2021-12-10 16:28:17
[-] Detected engines: 29
[-] Total engines: 59
[-] Scans: ('Lionic', 'Trojan[.]MSOffice[.]Emotet.4!c')
[-] Scans: ('ClamAV', 'Xls[.]Downloader[.]EmotetExcel122100-9913103-0')
[-] Scans: ('McAfee', 'Downloader-FCHG!F4546CFAAF78')
[-] Scans: ('K7AntiVirus', 'Trojan ( 0058b5021 )')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('K7GW', 'Trojan ( 0058b5021 )')
[-] Scans: ('Arcabit', 'Trojan[.]Generic.D246B115')
[-] Scans: ('Cyren', 'XML/Agent[.]KD')
[-] Scans: ('ESET-NOD32', 'DOC/TrojanDownloader[.]Agent[.]DOH')
[-] Scans: ('Avast', 'VBS:Malware-gen')
[-] Scans: ('Cynet', 'Malicious (score: 99)')
[-] Scans: ('Kaspersky', 'HEUR:Trojan.MSOffice[.]Emotet[.]gen')
[-] Scans: ('Alibaba', 'TrojanDownloader:Office97/Emotet.3e3309f5')
[-] Scans: ('MicroWorld-eScan', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('Tencent', 'Trojan[.]MsOffice[.]XmlMacroSheet.11017772')
[-] Scans: ('Ad-Aware', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.38187285 (B)')
[-] Scans: ('DrWeb', 'W97M[.]DownLoader.5470')
[-] Scans: ('McAfee-GW-Edition', 'Artemis!Trojan')
[-] Scans: ('FireEye', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('Ikarus', 'Trojan-Downloader[.]XLM[.]Agent')
[-] Scans: ('GData', 'XML.Trojan[.]Agent[.]AOBTAI')
[-] Scans: ('Avira', 'W2000M/YAV[.]Minerva[.]eltuf')
[-] Scans: ('MAX', 'malware (ai score=85)')
[-] Scans: ('Microsoft', 'TrojanDownloader:O97M/Emotet!MTB')
[-] Scans: ('Zoner', 'Probably Heur.W97ShellN')
[-] Scans: ('Rising', 'Downloader[.]Agent/XLM!1.DADA (CLASSIC)')
[-] Scans: ('Fortinet', 'XML/Agent[.]AA!tr[.]dldr')
[-] Scans: ('AVG', 'VBS:Malware-gen')
[!] Error from Cymru MHR: HTTPSConnectionPool(host='hash.cymru.com', port=443): Max retries exceeded with url: /cgi-bin/bulkmhr.cgi (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[+] MetaDefender File Report Results
[-] Date submitted: 2021-12-06T02:05:47.332Z
[-] Detected engines: 4
[-] Total engines: 34
[-] Scans: ('Avira', 'W2000M/YAV[.]Minerva[.]eltuf')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.38187285')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.38187285 (B)')
[-] Scans: ('Ikarus', 'Trojan-Downloader[.]DOC[.]Agent')
[-] Scans: ('RocketCyber', '')
[-] Scans: ('Webroot SMD', '')
********************************************************************************
* Information for 8827e861b25e27768d02dd12c1aa855b
* Observable type: hash (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[-] No Malc0de Results
[!] Error from VirusTotal File Report: Expecting value: line 1 column 1 (char 0)
[!] Error from ThreatExpert: HTTPConnectionPool(host='www.threatexpert.com', port=80): Max retries exceeded with url: /report.aspx?md5=8827e861b25e27768d02dd12c1aa855b (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[-] No VxVault Results
[!] Error from Cymru MHR: HTTPSConnectionPool(host='hash.cymru.com', port=443): Max retries exceeded with url: /cgi-bin/bulkmhr.cgi (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[+] MetaDefender File Report Results
[-] Date submitted: 2021-12-06T02:07:52.446Z
[-] Detected engines: 4
[-] Total engines: 34
[-] Scans: ('Avira', 'W2000M/YAV[.]Minerva[.]ivjtn')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.47562197')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.47562197 (B)')
[-] Scans: ('Ikarus', 'Trojan-Downloader[.]DOC[.]Agent')
[-] Scans: ('RocketCyber', '')
[-] Scans: ('Webroot SMD', '')
********************************************************************************
* Information for 86659503579263c2fe9b292a3ccae2ff3a51ad5f
* Observable type: hash.sha1 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with --list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2021-12-10 16:32:35
[-] Detected engines: 29
[-] Total engines: 59
[-] Scans: ('Lionic', 'Trojan[.]MSOffice[.]Emotet.4!c')
[-] Scans: ('ClamAV', 'Xls[.]Downloader[.]EmotetExcel122100-9913103-0')
[-] Scans: ('K7AntiVirus', 'Trojan ( 0058b5021 )')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.47562197')
[-] Scans: ('K7GW', 'Trojan ( 0058b5021 )')
[-] Scans: ('Arcabit', 'Trojan[.]Generic.D2D5BDD5')
[-] Scans: ('Cyren', 'XML/Agent[.]KD')
[-] Scans: ('ESET-NOD32', 'DOC/TrojanDownloader[.]Agent[.]DOH')
[-] Scans: ('Avast', 'VBS:Malware-gen')
[-] Scans: ('Cynet', 'Malicious (score: 99)')
[-] Scans: ('Kaspersky', 'HEUR:Trojan.MSOffice[.]Emotet[.]gen')
[-] Scans: ('Alibaba', 'Trojan:Office/Emotet[.]aeb515b2')
[-] Scans: ('MicroWorld-eScan', 'Trojan[.]GenericKD.47562197')
[-] Scans: ('Tencent', 'Trojan[.]MsOffice[.]XmlMacroSheet.11017772')
[-] Scans: ('Ad-Aware', 'Trojan[.]GenericKD.47562197')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.47562197 (B)')
[-] Scans: ('DrWeb', 'W97M[.]DownLoader.5470')
[-] Scans: ('McAfee-GW-Edition', 'Artemis!Trojan')
[-] Scans: ('FireEye', 'Trojan[.]GenericKD.47562197')
[-] Scans: ('Ikarus', 'Trojan-Downloader[.]XLM[.]Agent')
[-] Scans: ('GData', 'XML.Trojan[.]Agent[.]AOBTAI')
[-] Scans: ('Avira', 'W2000M/YAV[.]Minerva[.]ivjtn')
[-] Scans: ('MAX', 'malware (ai score=83)')
[-] Scans: ('Microsoft', 'TrojanDownloader:O97M/Emotet[.]ASQT!MTB')
[-] Scans: ('McAfee', 'Downloader-FCHG!F4546CFAAF78')
[-] Scans: ('Zoner', 'Probably Heur.W97ShellN')
[-] Scans: ('Rising', 'Downloader[.]Agent/XLM!1.DADA (CLASSIC)')
[-] Scans: ('Fortinet', 'XML/Agent[.]AA!tr[.]dldr')
[-] Scans: ('AVG', 'VBS:Malware-gen')
[!] Error from Cymru MHR: HTTPSConnectionPool(host='hash.cymru.com', port=443): Max retries exceeded with url: /cgi-bin/bulkmhr.cgi (Caused by NewConnectionError(': Failed to establish a new connection: [Errno -2] Name or service not known'))
[+] MetaDefender File Report Results
[-] Date submitted: 2021-12-06T02:07:52.446Z
[-] Detected engines: 4
[-] Total engines: 34
[-] Scans: ('Avira', 'W2000M/YAV[.]Minerva[.]ivjtn')
[-] Scans: ('BitDefender', 'Trojan[.]GenericKD.47562197')
[-] Scans: ('Emsisoft', 'Trojan[.]GenericKD.47562197 (B)')
[-] Scans: ('Ikarus', 'Trojan-Downloader[.]DOC[.]Agent')
[-] Scans: ('RocketCyber', '')
[-] Scans: ('Webroot SMD', '')
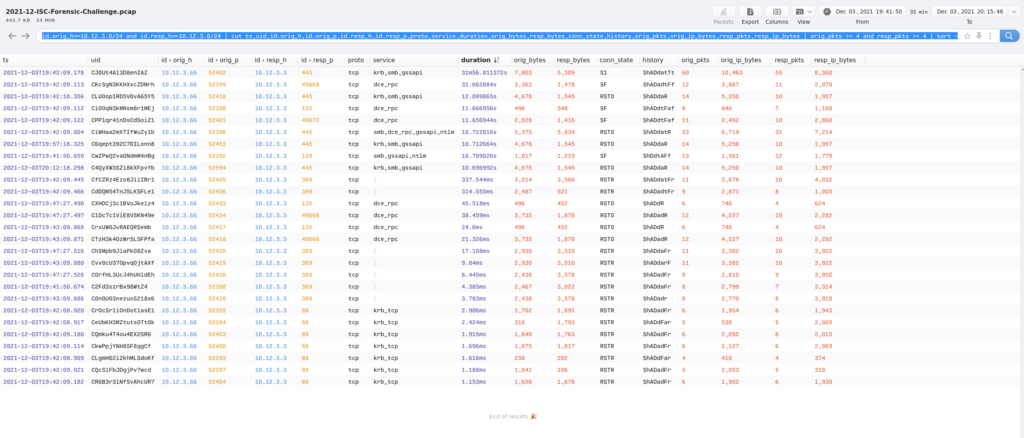
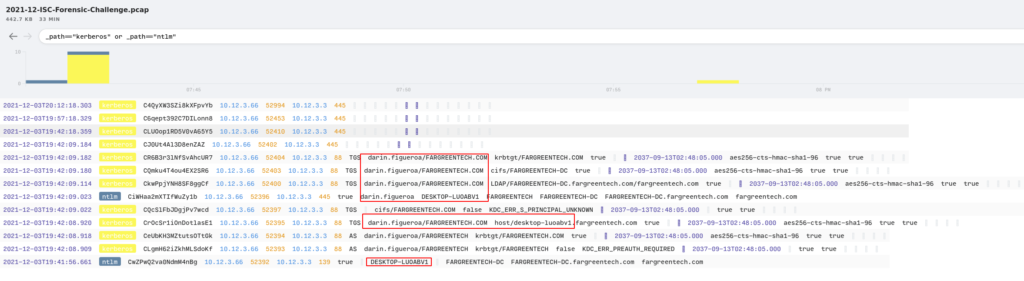
For the last part of this exercise, I needed to find what the name of the user was and the hostname as well. This was pretty straight forward in Brim since you can look at both “NTLM” and “Kerberos” at the same time and see the results.
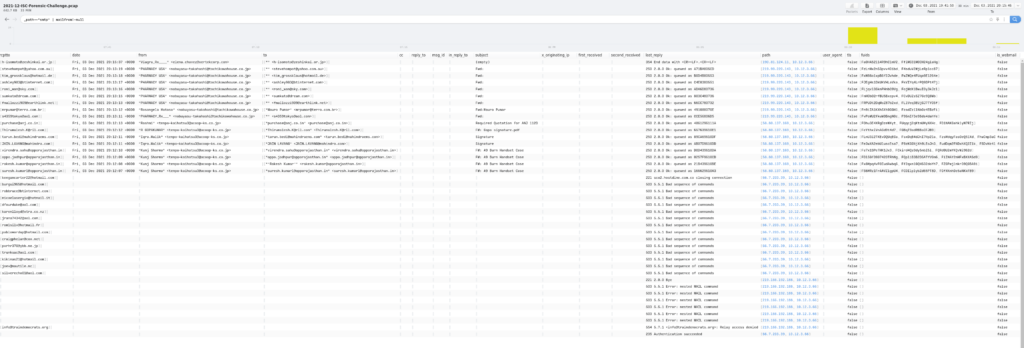
Now for the last part – what the heck is all the SMTP messages? Using the following query I was able to make short work of this.
_path=="smtp" | mailfrom!=null
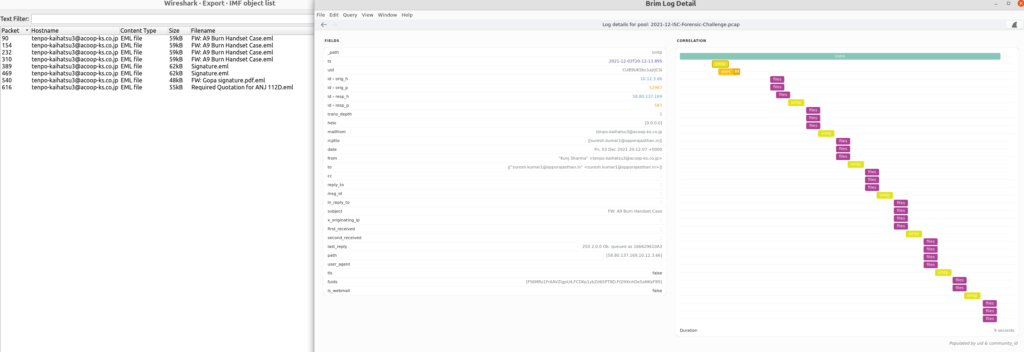
Looks like I was correct about the malspam aspect of this. The other interesting bit to this is when I dug into one of the rows and opened the log detail up. In the following example, I saw that there was the connection, but then a cascading view of three files, and a SMTP communication. This stems from the same connection being used to send several emails that range from two attachments up to four different attachments.
So there we have it – a quick rundown of Brim and the different queries that I used to work on this exercise. As usual, please let me know if I have missed anything. Thanks for stopping by.