Summary
========
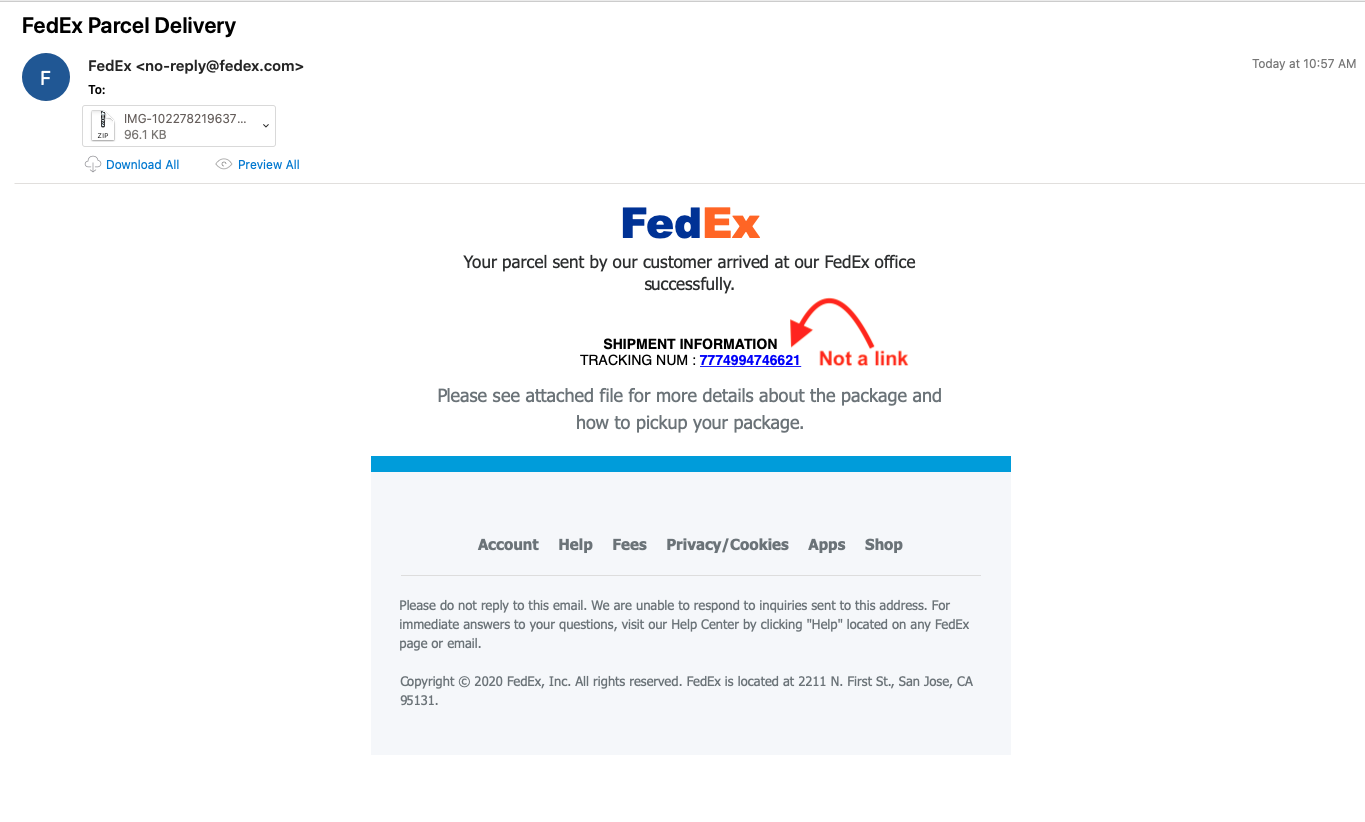
Looking through some of the email filters today looking for anything interesting, I ran into some emails that all had the same characteristics. All the emails were Fedex themed and had an attachment named “IMG-10227821963777100026367819.zip.” Once the file had been unzipped, it was actually a JAR file (IMG-10227821963777100026367819.jar).
Also, since I had not seen any kind of malware like this before, I came across some interesting posts about this that you can review. Trustwave did a great write up about this, along with TrendMicro.
For the PCAPs, ProcMon, and strings2 artifacts from this, please see the Github repo located here. For the actual files that were dropped on the host, please go here. **Note: The reason for 2 PCAP files and 2 ProcMon files is because of running things, and then pausing the Java process to run Strings2 and then starting the process back up again.
Analysis
========
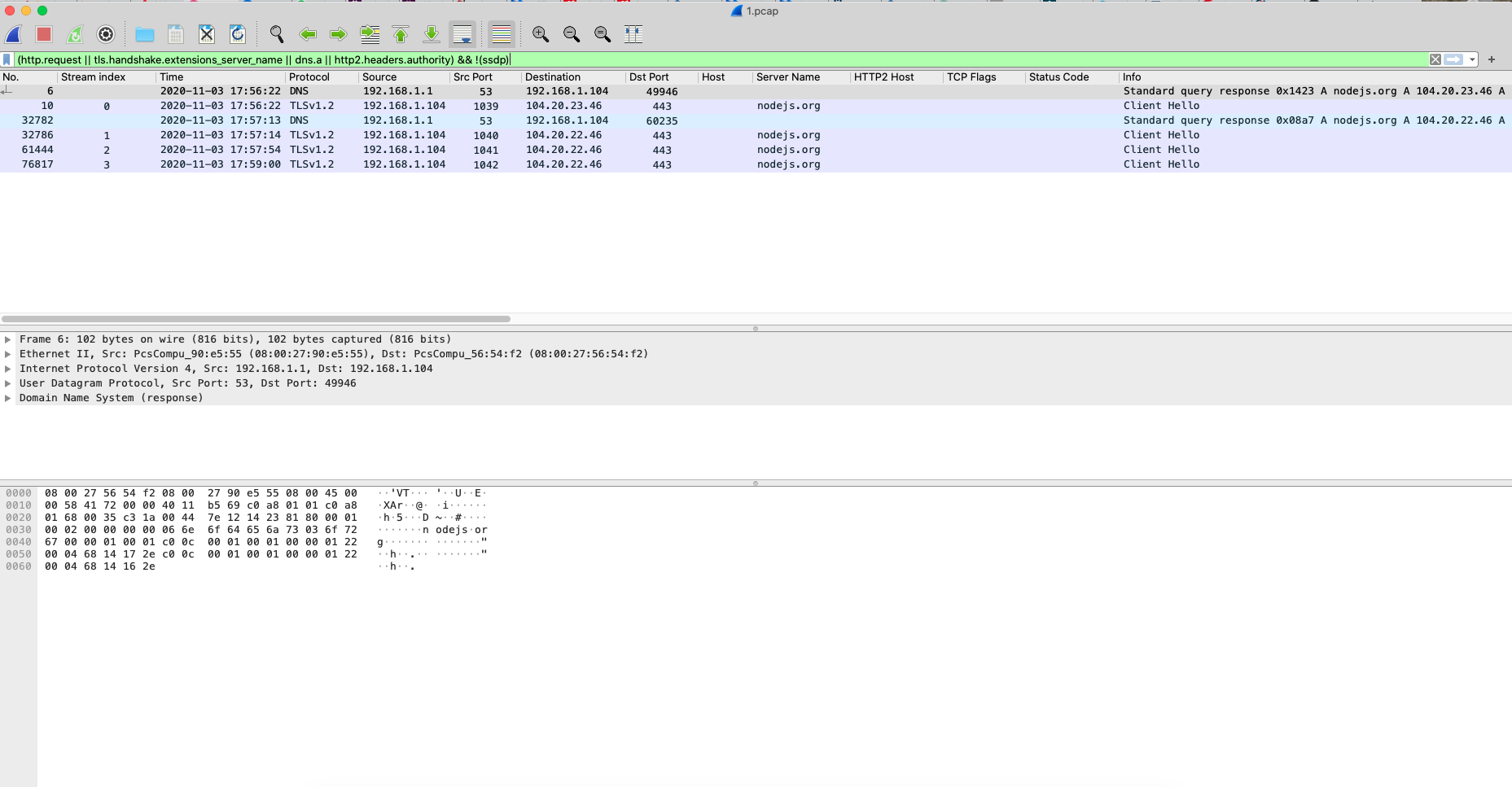
Once I had unzipped the file, I did try to see if I could figure out what was going on using a couple of Java tools to see if it could de-obfuscate it. While there are a few Allatori tools/plugins out there for this, I decided to just run it in my VM to see what happened since I am horrible with Java. Once the JAR file had been run, the initial JAVE.exe process(PID 3012) wrote a file called “6df8c6dc.tmp” to the “C:\Users\%Username%\AppData\Local\Temp” directory. Shortly thereafter, that process spun up another Java.exe process (PID 1564) and started to create what would be several different Node.JS folders (node-v14.12.0-win-x64, node-v14.12.0-win-x64.tmp3688241074700, node-v14.12.0-win-x64.tmp3635979968400, node-v14.12.0-win-x64.tmp3728784032900, and node-v14.12.0-win-x64.tmp3794067098400) under the path of “C:\Users\%Username%\.” This took some time to be honest since it was pulling these down as well based on what I was seeing in the PCAP.
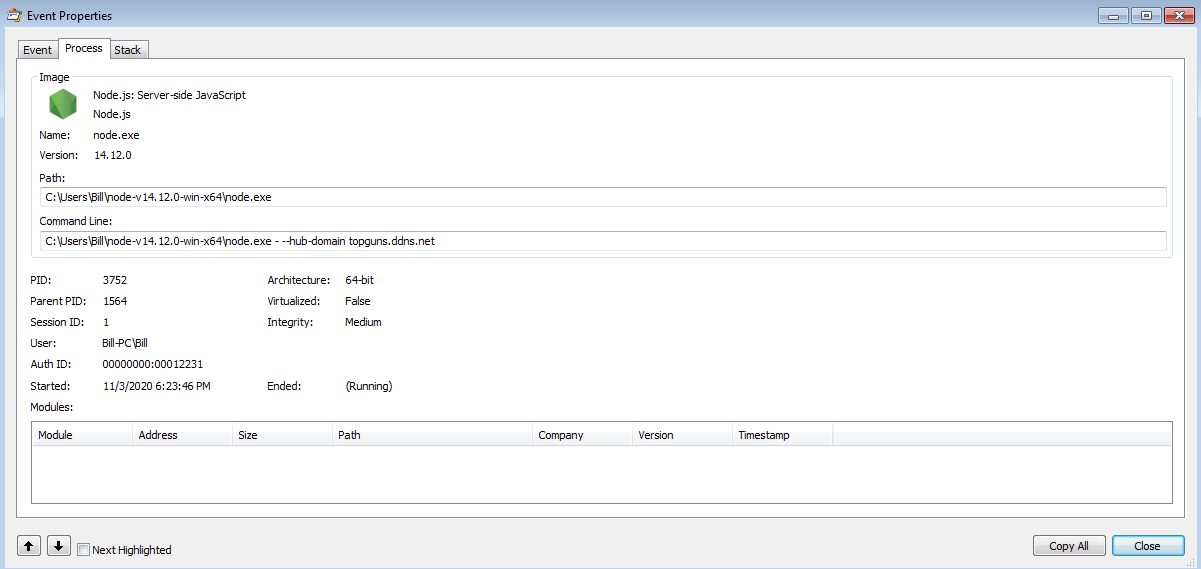
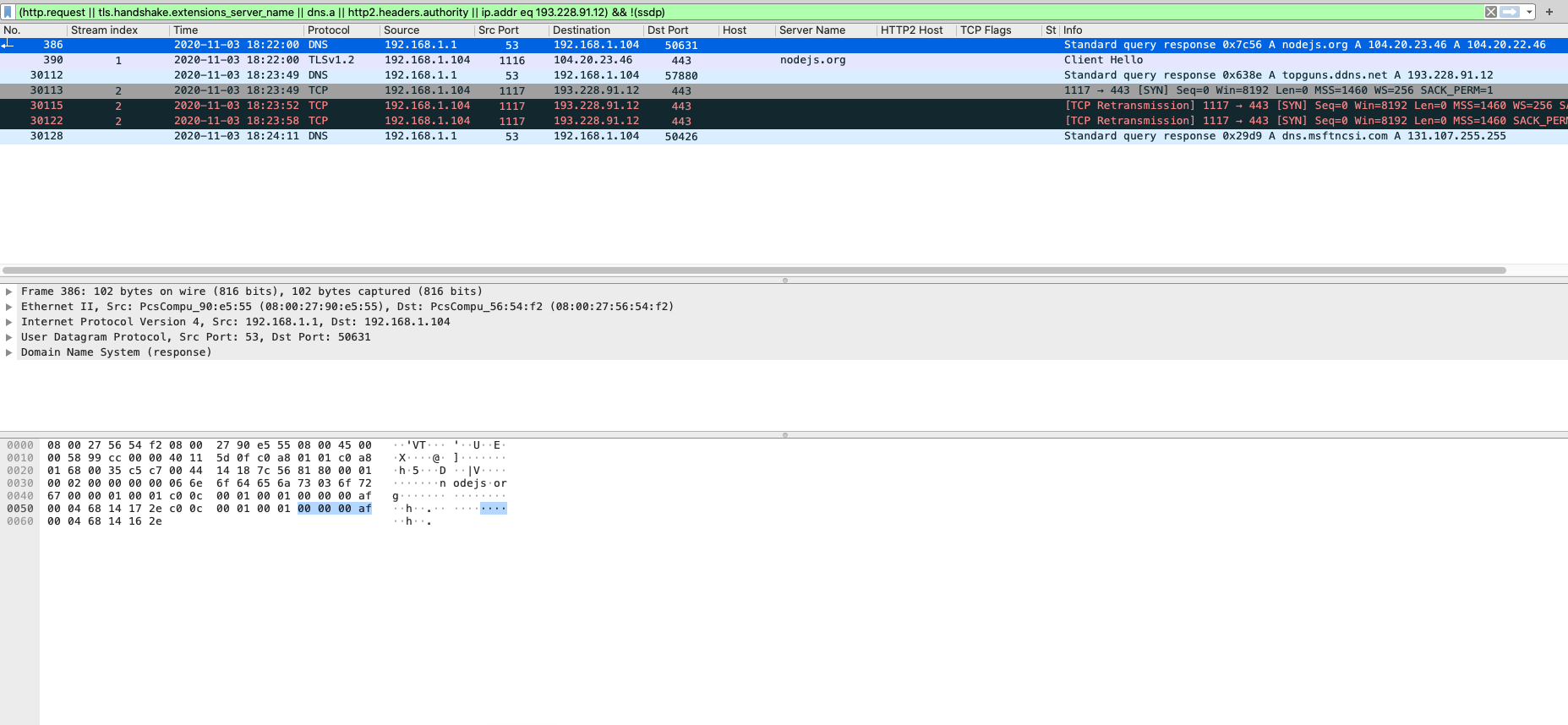
While the Java.exe (PID 1564) process was downloading different Node.JS packages and running them, I paused the process to run strings2 against the Java process to see if I could find anything. Once I had created the log file from that process I started it back up and that is when I noticed that it had finally started the node.exe process (PID 3752) and that it had tried to reach out to the dynamic DNS of “topguns.ddns.net” (193.228.91.12) which was already taken down or cleaned up.
Looking at the strings2 output, I could see things like the firewall settings configured on the VM, and what appeared to be local GPO settings as well. I also did see what @reecdeep found in the attached images from the Tweet but nothing else that stood out to me.
For this sample, I did not see any level of persistence setup or created like what was reported in the Trustwave or TrendMicro articles.
Artifacts
==========
IOCs
—–—
topguns.ddns.net / 193.228.91.12 (TCP/443)
OSINT
———-
http://twitter.com/reecdeep/status/1315560451099504640
http://www.joesandbox.com/analysis/302849/0/html
File hashes
——————–
303c5311de9c5dd4bb49cac5d1efdb4c5cccf03c8bf058d8c87055568712467d – IMG-10227821963777100026367819.jar / 6df8c6dc.tmp
5d96a9a18cbaf65b8b7036d578e0db0fc22314669cb060fc255874bdfc402d18 – IMG-10227821963777100026367819.zip
Machinae results
—————–———–
********************************************************************************
* Information for topguns.ddns.net
* Observable type: fqdn (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No URLVoid Results
[-] No URL Unshorten Results
[-] No Malc0de Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Dynamic DNS
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-10-23’, ‘193[.]228.91.12’)
[-] pDNS data from VirusTotal: (‘2020-10-22’, ‘194[.]180.224.161’)
[+] McAfee Threat Results
[-] McAfee Web Risk: Minimal
[-] McAfee Last Seen: 2020-11-04
********************************************************************************
* Information for 193.228.91.12
* Observable type: ipv4 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[-] No IPVoid Results
[-] No Malc0de Results
[+] AbuseIPDB Results
[-] AbuseIPDB reports: 3
[-] No RansomwareTracker Results
[-] No SANS Results
[+] Fortinet Category Results
[-] Fortinet URL Category: Malicious Websites
[+] VirusTotal pDNS Results
[-] pDNS data from VirusTotal: (‘2020-10-15’, ‘severdops[.]ddns[.]net’)
[-] pDNS data from VirusTotal: (‘2020-10-23’, ‘topguns[.]ddns[.]net’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-11-02’, ‘(hXXp)://topguns[.]ddns[.]net/’)
[-] pDNS malicious URLs from VirusTotal: (‘2020-10-31’, ‘hXXp://ndroga[.]xyz/’)
[-] No McAfee Threat Results
[-] No ThreatCrowd IP Report Results
********************************************************************************
* Information for 303c5311de9c5dd4bb49cac5d1efdb4c5cccf03c8bf058d8c87055568712467d
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2020-11-02 12:36:02
[-] Detected engines: 0
[-] Total engines: 63
********************************************************************************
* Information for 5d96a9a18cbaf65b8b7036d578e0db0fc22314669cb060fc255874bdfc402d18
* Observable type: hash.sha256 (Auto-detected: True)
********************************************************************************
Not seeing what you expect? Likely not a valid site. Try running with –list-sites
[+] VirusTotal File Report Results
[-] Date submitted: 2020-11-02 15:53:17
[-] Detected engines: 2
[-] Total engines: 63
[-] Scans: (‘Invincea’, ‘Mal/DrodZp-A’)
[-] Scans: (‘Sophos’, ‘Mal/DrodZp-A’)